Contents:
Ransomware infiltrates and hinders everything from healthcare organizations to energy distribution pipelines. This is why knowing what is the main vector of ransomware attacks can be hugely beneficial, not to say imperative for your organization’s safety.
Did you know that in the first half of 2022, there were 236.1 million ransomware attacks worldwide? And that it is a prevalent form of malware due to its ability to extort large sums of money while posing a low risk to criminals?
Before we get into all the ways threat actors could access your organization, let’s get one thing straight:
What Is an Attack Vector?
An attack vector in cyber security is a hacker’s path to exploit cybersecurity vulnerabilities.
Cybercriminals make money by targeting software systems, but they don’t always aim to steal credit card data or banking information. Some hackers have developed more sophisticated ways of monetizing their attacks, such as:
- Use an off-site command-and-control server to remotely access and control hundreds or thousands of computers to send spam, conduct cyberattacks, steal data, or mine cryptocurrency.
- Steal customer data from companies that collect and store large amounts of customer information.
- Make use of DDoS attacks that overload IT systems and cause unplanned service interruptions.
The thing is, a variety of infection vectors are used in these ransomware attacks.
The key to preventing ransomware is knowing how it makes its way in the first place.
In this article, you will see the main vector of ransomware attacks. By understanding the three top ransomware attack vectors, you can put in place controls and ransomware mitigations that will make your organization more resistant to infection.
Top 3 Ransomware Attack Vectors
Let’s examine the top three ways ransomware gets onto victims’ systems: phishing, Remote Desktop Protocol (RDP) and credential abuse, and vulnerabilities.
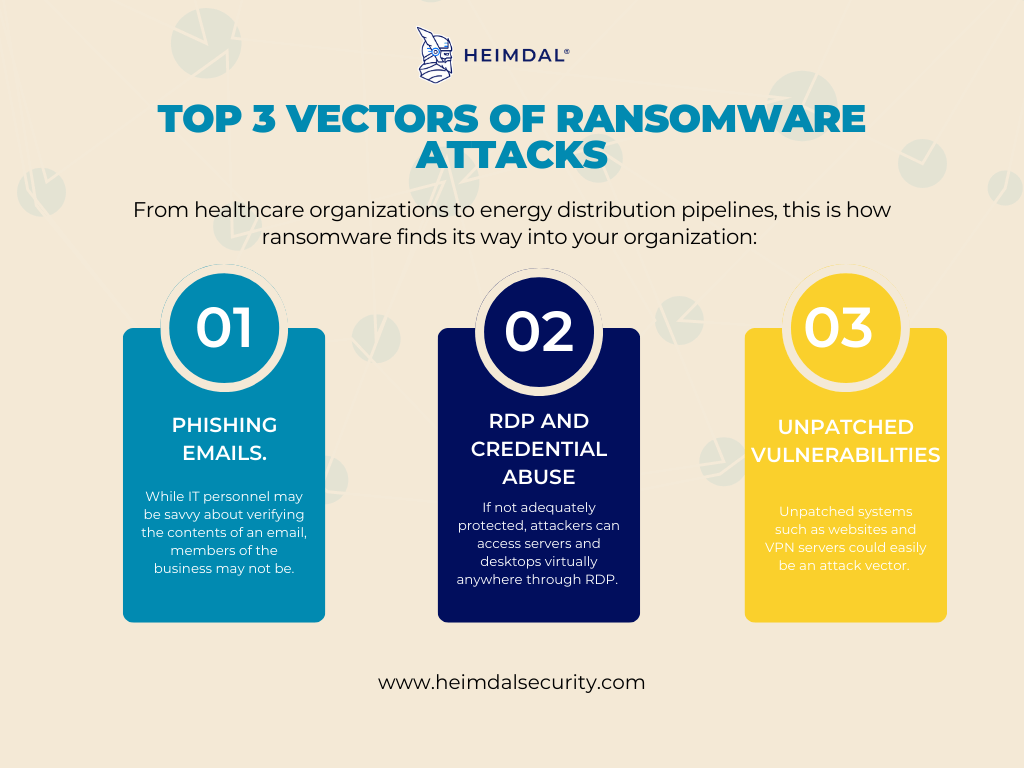
1. Phishing
Without a doubt, the main vector of ransomware attacks is phishing. Phishing remains the most popular attack vector for all malware, including ransomware, because it never fails. In addition, attackers often target emails, a technique called spear phishing, because it arrives in employees’ inboxes, usually located on corporate endpoints. The attacker, therefore, has high confidence that email-borne malware — if opened– has reached a valuable target.
A typical attack attempt begins when a user receives a malicious email that instructs them to open a tainted file attachment. It can arrive as a PDF document, a ZIP archive, or a Microsoft Office document that tricks a recipient into enabling macros. The attacker can trick the recipient into running a ransomware-downloading executable in any of those file formats.
It is not always attachments that infect recipients with malware in phishing emails. Instead, suppose victims click on the malicious link. In that case, the campaign may redirect them to a website that contains fake software downloads or other ruses designed to distribute ransomware or exploit kits.
There are a variety of ways in which phishing emails can be disguised to keep up with the topics users are most likely to be interested in.
For example, a great deal on electronics ahead of Black Friday or Cyber Monday or the promise of a faster tax refund in April will get clicks. A simple click of an attachment or malicious link will install dropper malware and download ransomware payloads as soon as the email is received.
How to Prevent Phishing
Email security systems, particularly those that operate in the cloud, can reduce the load on your mail server and lighten employee inboxes by filtering out low-hanging, easy-to-spot phishing emails before they reach your organization.
Endpoint detection and response systems, particularly those that detect abnormal behavior, are a last line of defense that can see ransomware activity that has passed email filters and users.
Read more about Phishing-as-a-Service and how to avoid it in our in-depth article.
2. Remote Desktop Protocol and Credential Abuse
Because it allows administrators to access servers and desktops from virtually anywhere, Microsoft’s proprietary Remote Desktop Protocol is extremely valuable to modern enterprises. However, it can also let attackers do the same if not adequately protected.
To exploit RDP, attackers typically require legitimate credentials. Ransomware operators and other criminal gangs use various techniques to obtain these credentials, including brute force attacks, purchasing them from illegal sites, and credential stuffing.
How to Keep RDP Safe and Prevent Credential Abuse
There are a couple of things you could do, such as:
- Add multi factor authentication and make it mandatory for remote access. Even with valid credentials, an attacker will be unable to access the system unless a secondary authentication factor is used, such as a one-time code, dongle, or text message.
- Use VPNs to restrict remote system access further and limit admin access to a single-purpose device, such as a jump server or privileged access workstation. This means attackers must first infiltrate the jump server or workstation before attempting to connect to the remote server via RDP.
- Consider closing the admin ports and only allowing access when a legitimate, verified user requests it. This way, administrators can continue to do their jobs while keeping systems secure around the clock.
3. Exploitable Vulnerabilities
The “other” category, which includes the exploitability of unpatched systems and software, is our list’s final ransomware attack vector. Any internet-facing system that isn’t patched and protected could be a vector for attack.
Due to the complexity of modern software supply chains, websites frequently include plugins and libraries. Furthermore, many low-code/no-code workflows connect to various services and functions. A flaw in these could be used as a ransomware attack vector.
How to Find and Fix Vulnerabilities?
If you haven’t already, update your patch management software:
- Implement an application lifecycle management (ALM) program for software and workflows to inventory and track applications and services in the organization.
- Implement automated vulnerability management tools that enable you to continuously monitor your infrastructure and assess the status of your environment in real time.
- Implement automated patch management software. For example, Heimdal’s Patch and Asset Management solution allows you to automate your software patching process, achieve compliance, solve vulnerabilities, and creates an IT asset inventory in minutes.
How to Avoid Becoming a Ransomware Victim
Consider the following measures to protect your organization from ransomware attacks:
1. Start with a thorough cyber awareness.
Your employees should view themselves as cyber foot soldiers and change perceptions in your organization that security is the sole responsibility of the Security Operations Center (SOC). Cyber-attacks can significantly impact the entire organization, causing downtime, loss of productivity, financial loss, and significant disruption.
Reinforce lessons learned through regular cyber awareness training, tabletop exercises, and security drills. Walking through a hypothetical ransomware incident, you can explain how these attacks happen, what employees should do if they find themselves attacked, and who to contact. Security teams can also conduct mock phishing or smishing attacks to determine the effectiveness of these awareness efforts.
2. Maintain a solid patching schedule.
Cyber hygiene, such as patching your system frequently, is an effective tool against ransomware. Organizations that fail to apply patches are at an increased risk of being ransomware victims. Over seven times more likely than organizations with an A grade to experience a ransomware event were those with a patching cadence grade of D or F.
3. Establish security protocols for email and instant messaging.
To reduce spoofing and authenticate the origin of emails, consider implementing email security protocols such as DKIM, SPF, and DMARC.
Antivirus software that scans instant messages for suspicious links and attachments effectively prevents instant messenger ransomware attacks. For instance, Heimdal’s Next Gen Antivirus, can detect sophisticated online threats such as ransomware, hidden backdoors, rootkits, brute-force attacks, and even undetectable malware. Moreover, it detects and mitigates even the most complex threats by utilizing four layers of impeccable detection.
How Can Heimdal Help Protect Against Ransomware?
Heimdal offers a comprehensive cybersecurity suite to protect businesses from ransomware and other threats. The range of products includes endpoint and network protection solutions that work together to provide a layered defense against ransomware and other cyberattacks, covering the most common attack vectors and preventing data loss and downtime. Heimdal’s products are easy to deploy and manage through a single agent and a unified platform. Moreover, specifically for ransomware, Heimdal employs a revolutionary 100% signature-free module called Ransomware Encryption Protection that can detect any encryption attempts.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Final Thoughts
Fortunately, ransomware attacks are preventable, and the risks of this threat are reduced if you understand how they happen. We hope this blog article has given you a better understanding of the common ransomware attack vectors and provided you with tips to protect your business from them.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










