Contents:
What privacy and security concerns should Coinbase users have? Is Coinbase safe to use? What should you keep in mind before you dive? In this guide, I will walk you through all that and more. As a cybersecurity company, we understand how important money is – for people like us, trying to get more digitally-savvy, for cybercriminals, whose only goal, disregarding whatever method they use for hacking, is to make a profit and get something valuable from their victims, but also for pretty much everyone else who wants to have a nice and decent life. This is why we think that financial education is as important as a good cybersecurity culture – and cryptocurrency is the part in which the two intertwine.
Is Coinbase safe? A Brief Description of Cryptocurrency and Bitcoin
As Cointelegraph says, a cryptocurrency is “a digital or virtual currency designed to work as a medium of exchange. It uses cryptography to secure and verify transactions as well as to control the creation of new units of a particular cryptocurrency. Essentially, cryptocurrencies are limited entries in a database that no one can change unless specific conditions are fulfilled.”
Although there have been many attempts of creating a digital currency during the 90s, only in 2009 an anonymous programmer or group of programmers known as Satoshi Nakamoto introduced Bitcoin, which is “completely decentralized, meaning there are no servers involved and no central controlling authority. The concept closely resembles peer-to-peer networks for file sharing.” With Bitcoin, there is no server or central authority to control your funds or avoid the fraudulent technique of double-spending (spending the same amount of money twice) – every single participant does this job, via the Blockchain. Blockchain is, thus, a key component of cryptocurrency, representing “a public ledger of all transaction that ever happened within the network, available to everyone. […] Every transaction is a file that consists of the sender’s and recipient’s public keys (wallet addresses) and the amount of coins transferred.”
The Bitcoin wallets’ private key “is used to sign transactions, providing a mathematical proof that they have come from the owner of the wallet. The signature also prevents the transaction from being altered by anybody once it has been issued. All transactions are broadcast to the network and usually begin to be confirmed within 10-20 minutes, through a process called mining.”
Mining refers to a “distributed consensus system that is used to confirm pending transactions by including them in the blockchain. It enforces a chronological order in the blockchain, protects the neutrality of the network, and allows different computers to agree on the state of the system.” In the mining process, computer hardware does difficult “mathematical calculations for the Bitcoin network to confirm transactions and increase security.
As a reward for their services, Bitcoin miners can collect transaction fees for the transactions they confirm, along with newly created bitcoins. Mining is a specialized and competitive market where the rewards are divided up according to how much calculation is done. Not all Bitcoin users do Bitcoin mining, and it is not an easy way to make money.” New information can be added to the Blockchain, but the previous information cannot be edited, adjusted, or changed. You can better understand how Blockchain works from the image below:
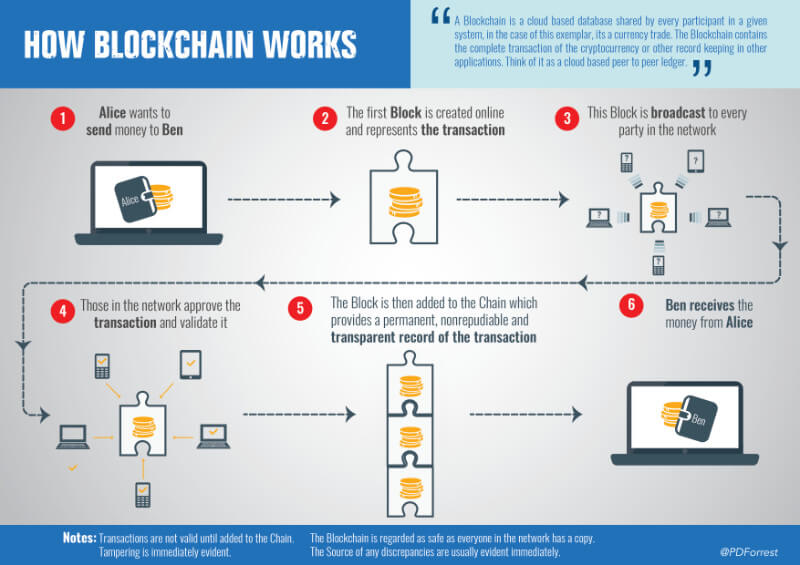
Source: SupplyChainGameChanger
Cryptocurrencies like Bitcoin can be used for buying goods both online and offline or even services, or for investments – although we have to warn you that these investments come with their fair share of risks: “Their market value fluctuates like no other asset’s.
Moreover, it is partly unregulated, there is always a risk of them getting outlawed in certain jurisdictions and any cryptocurrency exchange can potentially get hacked.” If you decide to buy cryptocurrency, you can either store it in an electronic wallet service or in an offline wallet on your hard drive. A hardware wallet is believed to be the most secure method, though, because it gives you full control over your assets.
And now, before finding out the final answer to the Is Coinbase Safe question, let’s see what the term refers to: BitDegree defines it at “a digital currency broker exchange where you can buy and trade Bitcoin and a few other cryptos. It is different from traditional cryptocurrency exchanges because it allows you to buy crypto using fiat currencies.”
Coinbase has two core products, a broker exchange and a professional trading platform called GDAX, which can be used independently from one another, while also having a built-in wallet (cryptocurrency wallets can be a software program, an online platform or a hardware device where all the crypto keys are stored. As BitDegree describes them, wallets are “a bit like a vending machine in a public place – anyone can insert money into the vending machine, but only those with the keys to the vending machine can remove the money.”)
Is Coinbase Safe?
As most sources say, yes. – it has 40 different licenses to operate in 30 states of the US alone and can be used in many countries to send, receive or store funds. To buy and sell features, though, Coinbase can be used only in 32 countries – you can consult the list here. – when talking about how safe is Coinbase, we must also mention that Coinbase stores the vast majority of the digital assets in secure offline storage and the cryptocurrency stored in their servers is covered by their insurance policy: “Coinbase prioritizes the security of our customer’s funds, all digital currency that Coinbase holds online is insured. If Coinbase were to suffer a breach of its online storage, the insurance policy would payout to cover any customer funds lost as a result.” – another important aspect is that Coinbase adheres to strict KYC (Know Your Customer) rules and closely respects them. It also cannot be used anonymously – “due to the KYC rules, users must submit a government-issued piece of ID and, in some cases, address verification in order to use the platforms BUY and SELL features.”
Here are some other nice features of Coinbase:
a. Trusted Cryptos only
You can only buy Bitcoin, Litecoin, Ether and Bitcoin Cash if you want to use Coinbase as an entry point into the crypto market. As BitDegree explains, “This is because Coinbase will only offer coins that are guaranteed currencies or commodities, and it does not open up to tokens that could potentially be securities or equities. It is very rare that they add new coins.”
b. Friendly interface
Coinbase is very beginners-friendly, since it has an easy-to-use interface, with clean design and clear tools, as you can see in the image below:
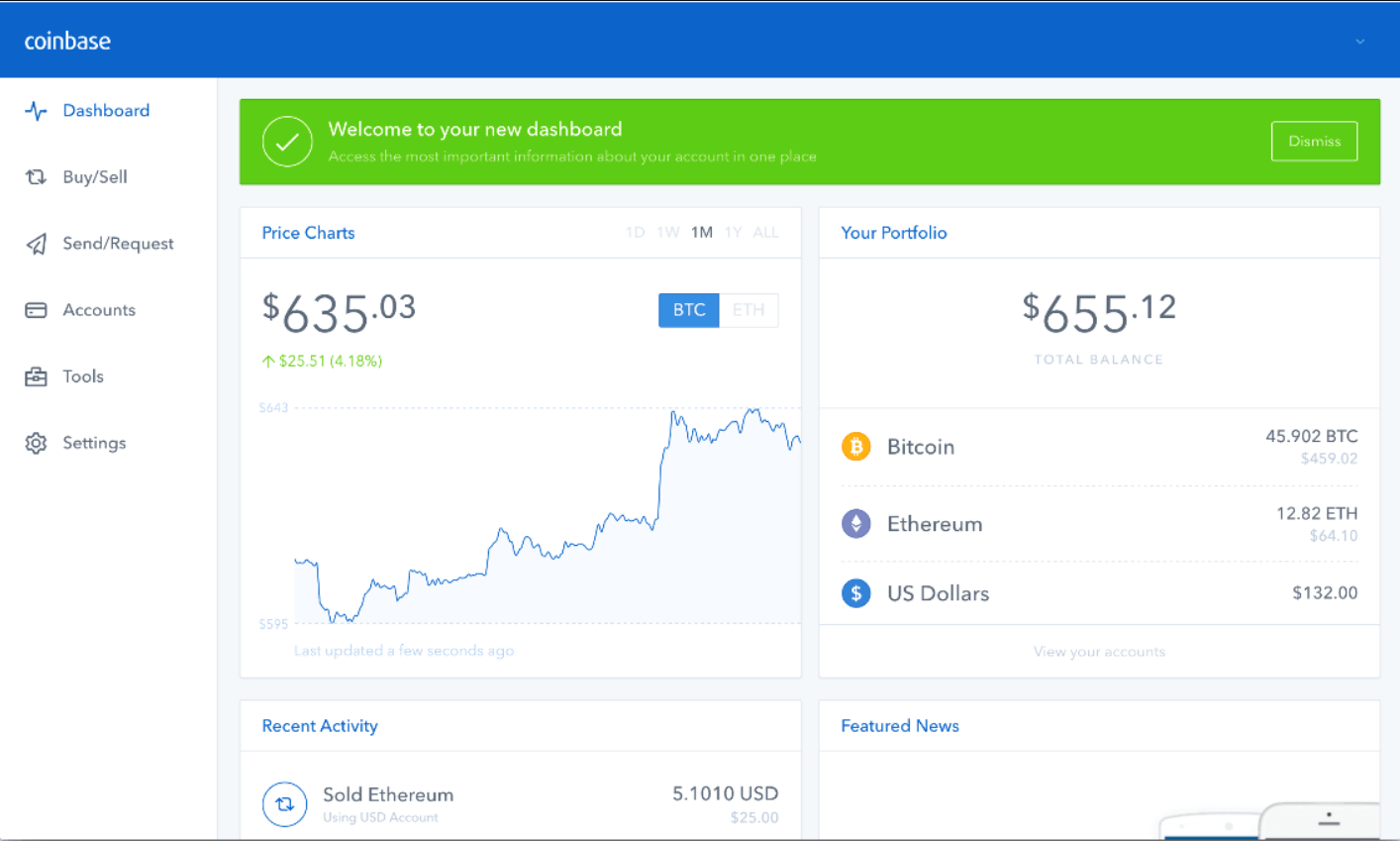
Source: BitDegree
c. Great variety of payment methods
Coinbase accepts a variety of fiat and offers a great variety of payment methods when it comes to getting the fiat money onto the platform to buy crypto – bank transfers, debit/credit cards, PayPal are a few examples.
Is Coinbase Wallet Safe?
Coinbase Wallet, first known as Toshi, is owned by the same company that owns Coinbase Exchange, but you don’t need to have a Coinbase Exchange account to use it. Everyone can use it for free, and it can be downloaded for both iOS and Android. As a standalone wallet, it stores the private keys on the device it is installed on, which makes it just as secure as the device it is on. It does use Secure Element Technology to lock down the private keys on your smartphone, though – a state-of-the-art security technology. Blockonomi adds:
“By using your fingerprint to guard the private keys on your smartphone, a hack of your wallet is nearly impossible. It is almost inconceivable that a hacker could create a duplicate fingerprint, or otherwise trick the device to let them into your Coinbase Wallet. You are also able to set up an auto-lock timeout for the wallet from one minute to one hour. By making it painfully slow to try multiple breaches, you make your wallet a very frustrating target for hackers.”
You only have to remember/copy the recovery passphrase that you are given at the account’s configuration moment, since that is the only way you can regain access to your wallet if something happens to your phone. Moreover, as it is mentioned on Wallet.Coinbase.com, “Coinbase Wallet is a user-controlled, non-custodial product. The app generates a 12-word recovery phrase which is what gives you, and only you, access to your account to move received funds. Coinbase will never have access to this seed, meaning that we cannot move funds on your behalf even if you lose access to your recovery phrase.” Coinbase also has different levels of verification that determine the amount of money you can invest and how much you can receive or send.
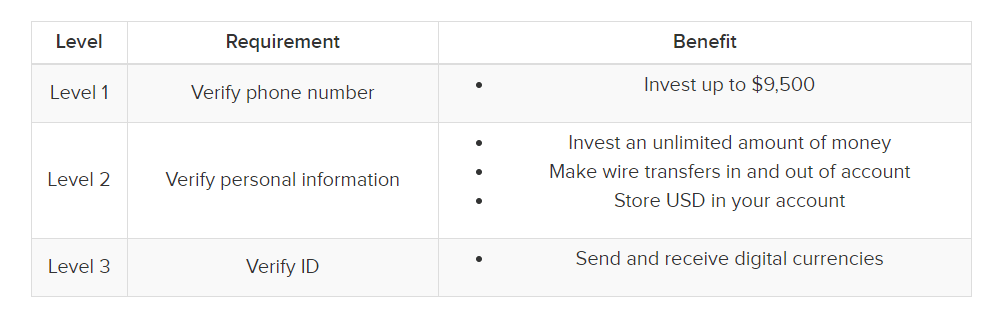
Source: BuyBitcoinWorldWide
After the ID verification, you can also opt for enabling 2-Factor Authentication, thus making your account even more secure. Coinbase can be used by cryptocurrency beginners or by anyone who already uses another wallet – since every wallet has a private key to secure its assets, it is possible to use the 12-word recovery phrase to sign into Coinbase Wallet.
Is Coinbase Safe? How to use Coinbase safely
Although, as we have discussed so far, Coinbase is a pretty safe application, there are dangers lurking in this part of the Internet that regards cryptocurrency too – we have already written about them here and here. When talking about how to use Coinbase safely, their team put it very nicely: “Coinbase takes extensive security measures to ensure your account and cryptocurrency investment remains as safe as possible, but ultimately, security is a shared responsibility.” Let’s see what you can do to secure your investments and keeping your accounts private:
1. Use a strong password
Your Coinbase account’s password should be long, random and unique. Don’t forget that this applies to all your online accounts – you can use a password manager if you’re afraid you won’t remember them all.
2. Use 2-step verification
Coinbase recommends using a security key or Time-based One Time Password (TOTP) with a mobile authenticator app, because these drastically reduce the chances of having your account compromised. You can enable both the security key and the TOTP from the account’s security settings.
3. Secure your email
Coinbase stresses the importance of a secure email account: “Your email is one of the most important connections between you and your Coinbase account. We use your email to confirm new devices, send you important alerts about your account, and to communicate with you if you need support. Please make sure it is secure!” They recommend checking if your email address has ever been compromised (you can do that on https://haveibeenpwned.com/ ), and then taking a few basic precautions, like checking for unauthorized recovery emails or phone numbers, for authorized devices you don’t recognize or for suspect rules, filters of forwarding addresses.
4. Protect your mobile account
As we were trying to answer the Is Coinbase Safe question, we said that it is, ultimately, as secure as your mobile device is. For this reason, you must protect your phone against SIM-swap or phone port attack (this happens “when an attacker has their target’s phone number transferred to a mobile device under the attacker’s control. Fraudsters are able to do this through a variety of means, including identity theft and socially engineering mobile carrier customer support representatives. This type of attack is a threat to all accounts using SMS-based 2-step verification and any account that can be recovered using phone-based authentication.”) Apart from the basic enabling of a screen lock for your phone, Coinbase advises us to:
“Call your mobile service provider and tell them that you’d like to place a port freeze and SIM lock on your account; Ask them to create an account note requiring you to be in-store with a valid photo ID in order to port or transfer your phone number to a new device; Ask them to add or enable a PIN number to be used when making changes to your account.”
5. Update and clean your devices
Keyloggers, remote access trojans and cookie-stealing malware are some of the biggest threats to mobile cybersecurity. To protect your mobile devices against them you should: – use anti-virus protection and scan your device often. You can try Heimdal™ Premium Security Home – our next-gen threat prevention tool can secure your digital life by stopping even the most sophisticated malware, ransomware, and online scams. 
6. Beware of phishing
Phishing is a malicious technique used by cybercriminals to gather sensitive information (credit card data, usernames, and passwords, etc.) from users. The attackers pretend to be a trustworthy entity to bait the victims into trusting them and revealing their confidential data, which can then be used for financial theft, identity theft, to gain unauthorized access to the victim’s accounts or to accounts they have access to, to blackmail the victim, etc. If you receive an email that seems suspicious, you can always forward it to Coinbase at security@coinbase.com to verify its authenticity. It is also important to always take basic safety measures against phishing – we have described them in-depth here.
7. Remember to verify your recent activity
Coinbase allows you to check all of your active sessions in terms of authorized mobile applications, web sessions or confirmed devices. Remember to regularly verify this information to see if something unusual or suspicious catches your eye.
Is Coinbase Safe? Wrapping Up
As we have seen, although relatively new on the market, cryptocurrency is a complex subject and, like any technological innovation, it can be used for good or to make a profit, even though someone might get harmed in the process. Whether you decide to invest in cryptocurrency and how you choose to protect your assets is entirely up to you, but please remember that Heimdal™ Security always has your back and that our team is here to help you protect your home and your company and to create a cybersecurity culture to the benefit of anyone who wants to learn more about it. Drop a line below if you have any comments, questions or suggestions – we are all ears and can’t wait to hear your opinion!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










