Contents:
An important cybersecurity company has discovered that the banking trojan Bizarre is now stealing financial data and crypto wallets from 70 banks in Europe and South Africa.
The banking trojan Bizarre, a malware originating from Brazil is usually dispersed through MSI downloads in spam messages. When clicked, it activates a ZIP download from a harmful website that matches the user’s processor design.
The malware circulates via phishing emails that are commonly camouflaged as certified tax-related messages notifying of neglected obligations.
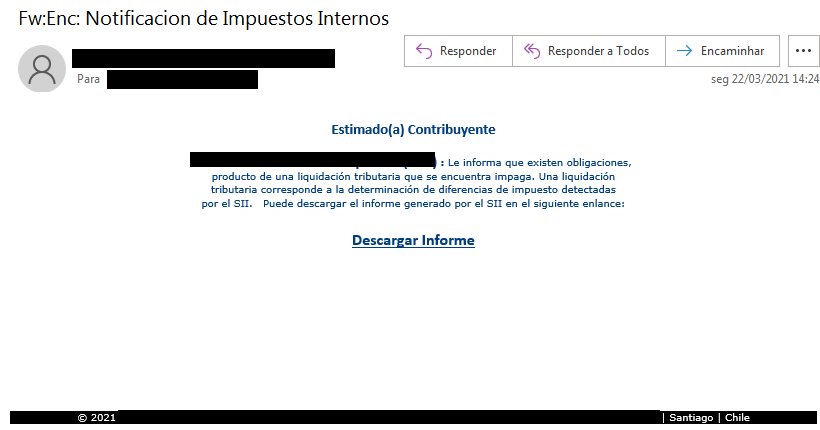
Following the installation, will begin to surveil the computer’s activity including cryptocurrency transfers and online banking sessions.
The minute it infects a Windows system, the malware can compel victims into entering banking credentials and utilizes social engineering to steal two-factor authentication codes and to convince victims to download a smartphone app.
According to the security researchers, the trojan is already spreading in countries such as Brazil, Argentina, Chile, Germany, Spain, Portugal, France, and Italy.
Users should also be worried about other characteristics of the malware. Once operative, the banking trojan can end all browser processes and even shut off online banking sessions. Once the session ended, victims will have no other choice but to re-enter banking credentials to log in again. This is the threat actors’ chance to steal the information.
The malware also catches the contents of each screen and monitors the clipboard. In consequence, when a crypto wallet is accessed, Bizarro substitutes it with a distinct one belonging to the attacker. The banking trojan even attempts to lure the victims into installing a different malicious app on their devices.
Cybersecurity researchers say that the banking trojan’s central element is its backdoor utility, which supports over 100 orders, most of them “used to display fake pop-up messages to users.”
The backdoor offers a lot of options to the attacker, including:
- Collecting data about the compromised system and sending them to the C&C server.
- Searching for and stealing files from the affected computer.
- Dropping files on the affected system.
- Remote control of the mouse and keyboard.
- Keylogging.
- Creating fake popup windows and messages. The messages are meant to slow down the user’s response time and include progress bars.
- Impersonating banking websites while operating.
Users can be deceived into providing their private data when they see custom message boxes or windows sent by Bizarro’s operators who use specific instructions for the backdoor component.
These messages can be either fake notifications asking for the credentials again or requesting to enter a confirmation code to a false error notifying that the system needs a restart to complete a security-related operation.
operation.
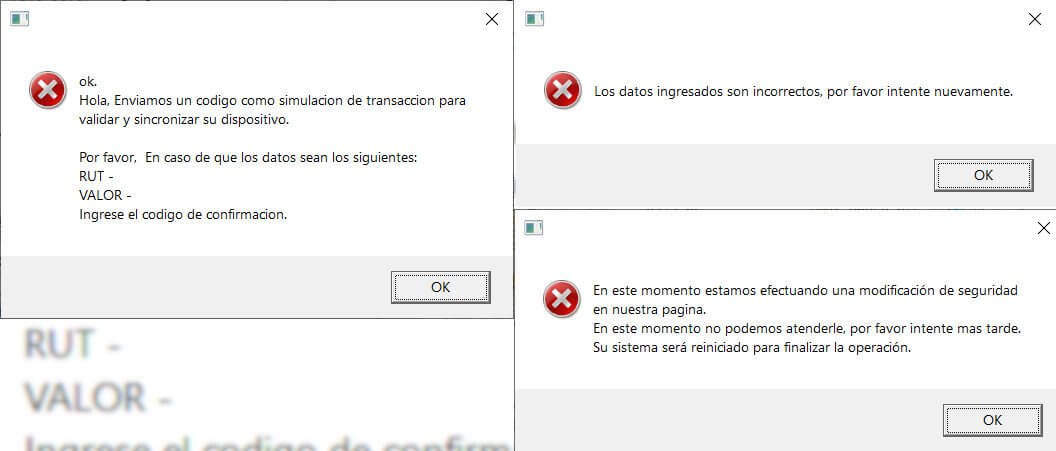
Another trick consists of showing jpeg pictures holding a target financial institution’s logo and directives for the victim. Some of these messages may obstruct access to the entire screen and conceal the taskbar, making it more difficult to start Task Manager.
The purpose of these pictures is to persuade the victims into thinking that their systems need an update or got infected.
The cybersecurity organizations declare that the banking trojan Bizarro is not the only malware in South America that expands to Europe, mentioning others that have been designed, developed, and spread in Brazil and have expanded outside Latin America: Guildma, Amalvado, Javali, Melcoz, and Grandoreiro.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










