Contents:
A new banking Trojan called “Bizarro” is now targeting European banking customers through a spear-phishing campaign in an attempt to steal credentials.
This week, Securelist researchers released a report saying the Brazil-originating Trojan is striking users in Brazil, Argentina, Chile, Spain, Portugal, France, and Italy, with bank customers being manipulated into handing over their account credentials for the purposes of financial theft.
The attackers reportedly use affiliates for cashing out or to help transfer the exfiltrated money. The researchers added that besides spear-phishing, the threat actors are spreading the malware as a malicious app.
Bizarro has x64 modules and is able to trick users into entering two-factor authentication codes in fake pop-ups. It may also use social engineering to convince victims to download a smartphone app. The group behind Bizzaro uses servers hosted on Azure and Amazon (AWS) and compromised WordPress servers to store the malware and collect telemetry.
The spear-phishing emails use a variety of lures, including a fake tax notification that contains an attachment with malicious Microsoft installer packets. When the victims click on the link within the Microsoft installer, they download a ZIP file.
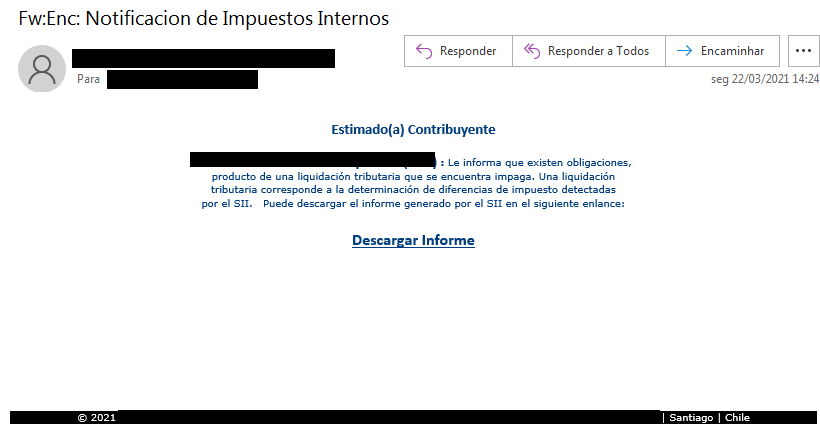
Image Source: Securelist
The ZIP file contains a Dynamic Link Library (DLL) file, written in Delphi, which executes the malware, an AutoHotkey script runner, and a small script that calls an exported function from the malicious DLL.
To exfiltrate banking credentials, the Trojan follows two steps. The first involves killing the browser processes and forcing the victims to reenter their banking credentials, which are then captured by the malware.
The second step involves disabling autocomplete in a browser to steal as many credentials as possible.
While it runs on the system, Bizarro gathers information including computer name, operating system version, default browser name, installed antivirus software name.
The malware gathers banking credentials by calling for an LMAimwc command, which displays an error message that appears to come from legitimate banks. The message requests that the victims enter their credentials. When this message is displayed, the victim’s computer freezes, allowing the attackers to steal banking credentials and device information.
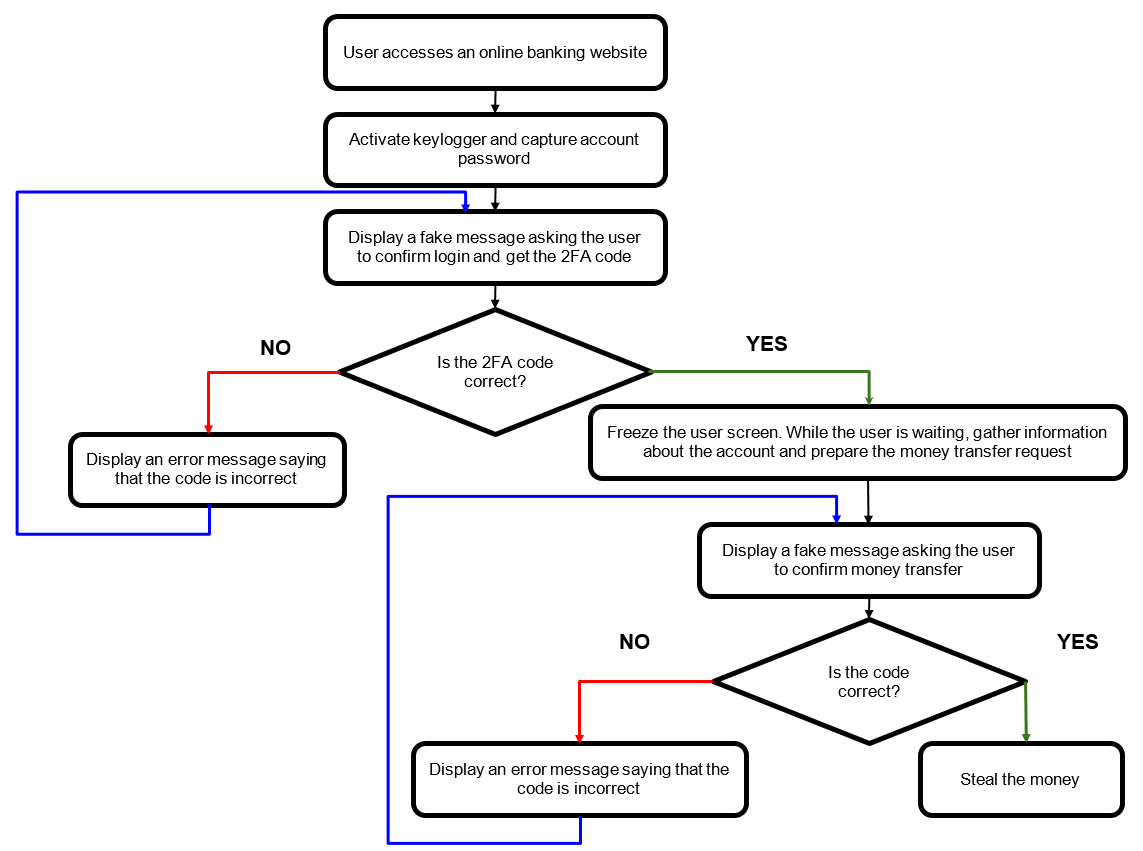
Image Source: Securelist
What’s more, the victim is manipulated into believing that the device is frozen due to a security update. And if the malware identifies a bitcoin wallet address on the targeted device, “it is replaced with a wallet belonging to the malware developers.”
According to the researchers, Bizarro’s C&C server contains more than 100 commands, including those that allow attackers to control the compromised device connections, files, the mouse, and the keyboard.
In an attempt to convince the victim to install a malicious app on their smartphone, hackers also make use of legitimate-looking messages:

Image Source: Securelist
“If the victim chooses Android, the C2 server will send a link with a malicious application to the client. The client will make a QR code out of it with the help of the Google Charts API”, the researchers added.
Unfortunately, Bizarro is not the only banking Trojan from Brazil that has expanded to other countries. Melcoz, Guildma, Javali, and Grandoreiro are just a few of the operators that are expected to continue their attacks, and it’s just a matter of time until they improve their malware as well.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










