Contents:
Make it the rule of thumb to never open an email attachment from an unknown sender! Here’s why: The Heimdal team has collected data about a spam run that is currently rolling out, targeting random email addresses. The spam email pretends to include a scanned document. However, the included .doc contains macros, which, once accessed, will attempt to download the online bank and information thief Dridex. Here are the contents of the unsolicited email: From: [spoofed / fake return address] Subject Line: Scanned from a Xerox Multifunction Printer Contents: Please open the attached document. It was scanned and sent to you Using a Xerox Multifunction Printer. Attachment File Type: DOC, Multi-Page Multifunction Printer Location: Device Name: XRX9C934E5EEC46 For more information on Xerox products and solutions, please visit http://www.xerox.com Attached: Scanned from a Xerox Multifunction Printer.doc
How the infection happens
If the document in question is opened, it will use macros to retrieve Dridex malware from the following locations (sanitized by Heimdal Security): hxxp: // tgequestriancentre [.] co.uk/708/346.exe hxxp: // sudburyhive [.] org / 708 / 346.exe hxxp: // werktuigmachines [.] be / 708 / 346.exe hxxp: // colchester-institute [.] com / 708 / 346.exe These are compromised webpages which return Dridex. The Dridex malware is run in the memory, never dropping a single file onto the hard-drive. This reduces the payload’s footprint on the user’s system and it provides a very low detection rate for traditional security products, such as antivirus. As we can see from the VirusTotal page, the detection rates for this infostealer is extremely low: 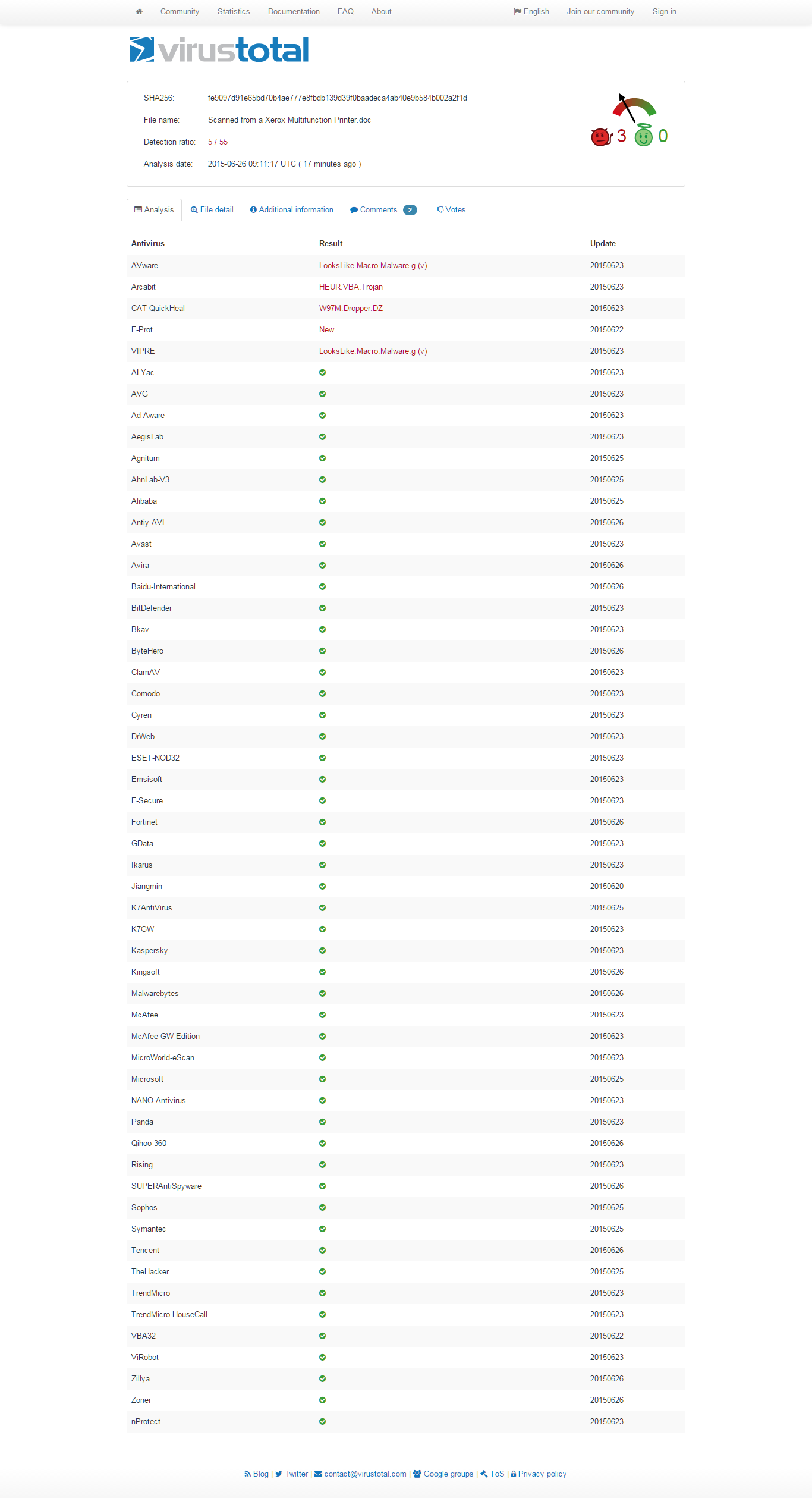 In the next step, Dridex will contact a series of C&C servers to deliver the data banking harvested from the victim’s system. Our team has blocked a large number of these domains in the Heimdal Secure DNS, so our users can be protected from data leakage and data loss. Dridex then writes the following datablobs (Binary Large OBjects) to the registry: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\CLSID\{91179CCE-14A2-1D89-01D5-125992394513}\ShellFolder 01D3A3627F1088934 “= hex:90,77,a9,7c,3c,f2,f0,e5,46,1c,c3,7b,fd,97,c1,19,aa,ce,1f,c5,2f,51,80,82,3a,7f,ec, 26,a9,83,df,19,aa,d7,12,cd,2f,51,83,cc,6e,38,e3,09,ea,d9,44,13,5c,57,81,ce,ec,89,a1, 9b,d1,dc,ab,58,05,37,8b,62,0c,50,0e,bd [..] The above data is split into two data sets, where both are XOR’d and contain configuration and web injects. In the configuration step, we have observed various features that Dridex uses: http shots form-grabber, httpinjblock, http block, click shots httpinjects, etc. For example, the “http shots” is activated by visiting the following URI: https://www \ .bankline \. (NatWest \ .com | rbs \ .com | ulsterbank \. (ie | co \ .uk)) / From analyzing the configuration and communication with C&C super nodes, we can see that this campaign is marked with BOTid: 120. There are numerous other targets and many sub-functions that make Dridex a dangerous infection for most businesses and individual users with access to online banking.
In the next step, Dridex will contact a series of C&C servers to deliver the data banking harvested from the victim’s system. Our team has blocked a large number of these domains in the Heimdal Secure DNS, so our users can be protected from data leakage and data loss. Dridex then writes the following datablobs (Binary Large OBjects) to the registry: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\CLSID\{91179CCE-14A2-1D89-01D5-125992394513}\ShellFolder 01D3A3627F1088934 “= hex:90,77,a9,7c,3c,f2,f0,e5,46,1c,c3,7b,fd,97,c1,19,aa,ce,1f,c5,2f,51,80,82,3a,7f,ec, 26,a9,83,df,19,aa,d7,12,cd,2f,51,83,cc,6e,38,e3,09,ea,d9,44,13,5c,57,81,ce,ec,89,a1, 9b,d1,dc,ab,58,05,37,8b,62,0c,50,0e,bd [..] The above data is split into two data sets, where both are XOR’d and contain configuration and web injects. In the configuration step, we have observed various features that Dridex uses: http shots form-grabber, httpinjblock, http block, click shots httpinjects, etc. For example, the “http shots” is activated by visiting the following URI: https://www \ .bankline \. (NatWest \ .com | rbs \ .com | ulsterbank \. (ie | co \ .uk)) / From analyzing the configuration and communication with C&C super nodes, we can see that this campaign is marked with BOTid: 120. There are numerous other targets and many sub-functions that make Dridex a dangerous infection for most businesses and individual users with access to online banking.
What is Dridex?
According to Webopedia:
Dridex is a strain of banking malware that leverages macros in Microsoft Office to infect systems. Once a computer has been infected, Dridex attackers can steal banking credentials and other personal information on the system to gain access to the financial records of a user. Dridex is an evolution of the Cridex malware, which itself is based on the ZeuS Trojan Horse malware. According to security firm Trustwave, the Dridex banking malware initially spread in late 2014 via a spam campaign that generated upwards of 15,000 emails each day. The attacks primarily focused on systems located in the United Kingdom.
UPDATE [August 20 2015]: A few days ago, the group behind the Dridex botnet launched several spam “spray & pray” campaigns against arbitrary email addresses. The unsolicited email arrives with the following contents: From: [spoofed / fake return address] Subject Line: Notification [random numbers and letters] Attached: 72O99GWS9.doc The attached document contains macros, which, if activated by an unsuspecting user when received, will enable the payload. The payload will connect to the following URLs from which it will download Dridex (sanitized by Heimdal Security): http://www.glamourstylistas [.] com / administrator / components / com_joomlaupdate / 777763172631572.txt http://www.glamourstylistas [.] com / administrator / components / com_joomlaupdate / rara.txt -> https://www.dropbox [.] Com / s / 7elbruw7mwn8oj4 / sfa3xaf.exe? Dl = 1 It’s important not to forget that Dridex is a sophisticated infostealer that systematically harvests data from infected machines. The compromised machines are then bound into a P2P based botnet, where they continue to transmit the collected data. Anti-virus detection for this campaign is low.
UPDATE [October 2 2015]: Dridex is active again
After about one month of downtime, the gang behind Dridex (the notoriously refined banking malware) resumed its operations with a new spam campaign which was launched yesterday, late at night. The unwanted e-mail arrives with an attached document that, once opened and its contents clicked by a careless recipient, will drop Dridex onto the machine. The spam e-mail is delivered with the following contents: From: [spoofed / fake return address] Subject Line: Please print Contents: [pretends to come from an English company named “Ucblinds”]. Attached: Order-SO00653333-1.doc If the attached document is opened and the content is activated, Dridex will become active in memory and it will connect to the following domains from which the main component of the infection will be downloaded and run (sanitized by Heimdal Security): http://hobby-hangar [.] net / 123 / 1111.exe http://miastolomza [.] pl / 123 / 1111.exe http://www.ifdcsanluis [.] edu.ar/123/1111.exe http://www.norlabs [.] de / 123 / 1111.exe http://www.schmidks [.] de / 123 / 1111.exe http://zahnrad-ruger [.] de / 123 / 1111.exe The main component binds the machine into a botnet, but it also captures and delivers various sensitive information to the malicious server. The active C & C and MITM servers are reproduced below and can serve as the Indicators of Compromise (sanitized by Heimdal Security): 195.251 [.] 250.37: 444 195.251 [.] 250.37: 444 136.243 [.] 237 218: 443 136.243 [.] 237 218: 443 66,171 [.] 247 166: 443 88,151 [.] 246.80: 443 66,171 [.] 247 166: 443 https://136.243 [.] 237 218 / https://82.118.24 [.] 167: 4483 / https://85.214.196 [.] 227: 4483 / orderability From the configuration file, it is clear that, in the case of BOTid # 220, the attack’s primary target is the UK. Antivirus detection is still unsatisfactory: 21/56 on VirusTotal. 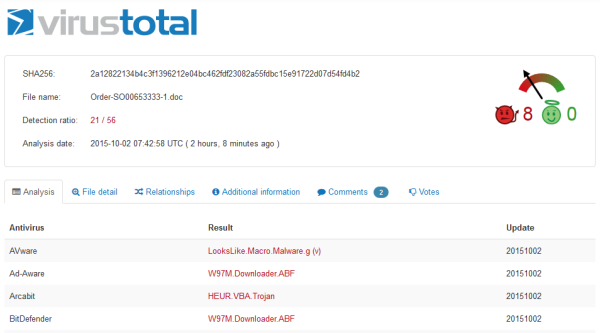 Click here for the full VirusTotal page detection rates at the moment when the campaign was discovered.
Click here for the full VirusTotal page detection rates at the moment when the campaign was discovered.
UPDATE [October 8 2015]: New spam campaign drops Dridex
Heimdal Security has collected data regarding a recent “spray & pray” spam campaign. Victims are lured to click because of the subject line which indicated that a scanned document is attached. The attachment is a XLS file with macros, which, if activated, will download Dridex from multiple servers and infect the victim’s PC. The unwanted e-mail arrives with the following contents: From: [spoofed / forged sender] Subject Line: Scanned document from the MX-2600N Contents: Device Name: Not Set Device Model: MX-2600N Location: Not Set File Format: XLS MMR (G4) Resolution: 200dpi x 200dpi Attached: xerox @ [% domain of the receiver%]. tld_20151007_160214.xls If the attachment is opened and the receiver activates the included macros, the machine will connect to the following malicious URLs to download Dridex from a cyber criminal controlled server (sanitized by Heimdal Security): http://tyleos [.] com / fw43t2d / 98kj6.exe http://frozenfoods2004 [.] com / fw43t2d / 98kj6.exe http://alarmtechcentral [.] com / fw43t2d / 98kj6.exe http://performatic [.] xf.cz/fw43t2d/98kj6.exe http://boda-link [.] com / fw43t2d / 98kj6.exe The binary code reveals that the Dridex code is part of Dridex botnet # 220: 220 </ botnet> 196 710 </ version> Command and control servers: 198.61.187 [.] 234: 4483 84246226 [.] 211: 448 92.51.129 [.] 33: 4483 Peers: 113.53.234 [.] 218: 448 134184.39 [.] 171: 443 136243237 [.] 218: 443 66171247 [.] 166: 448 83101.5 [.] 105: 444 88151246 [.] 80: 443 164.15.82 [.] 22: 443 164.15.86 [.] 19: 443 195251250 [.] 37: 448 37128132 [.] 96: 443 The attached malicious XLS document achieves only very limited antivirus detection, which makes the infection very effective on PCs who are not adequately protected.
Financial safety precautions
We advise online banking users to take all necessary security measures to ensure the protection of the confidential data and financial resources. Keep in mind to:
- Use secure websites when running financial transactions
- Never download email attachments from unknown senders
- Set strong passwords for online banking accounts and use 2-step authentication when possible.
Read and apply the 15 Steps to Maximize your Financial Data Protection.
Dridex was first spotted in November 2014, followed by spam campaigns in March, April and May this year. An article on the evolution of Dridex was recently published on the FireEye blog.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










