Contents:
Ransomware has become one of the main cyber threats that can have devastating effects on organizations, resulting in financial damage, corporate instability, and reputational harm. This type of malware uses complex encryption algorithms which lock up all files on a machine unless a decryption key is used to retrieve the data. A ransom message appears on the device’s screen, demanding the victim to pay a certain amount of money (usually in the Bitcoin cryptocurrency) in exchange for the passkey (with no certainty of the malicious hackers keeping their promise).
This sequence of events occurred one too many times during the past three decades since the first strain of ransomware was created.
Back in 2017, the WannaCry ransomware became one of the most devastating cyber-attacks ever seen. It swept the entire world, locking up critical systems all over the globe and infecting over 230,000 computers in more than 150 countries in just one day.
The UK’s National Health Service (NHS), FedEx, Spain’s Telefónica, or Renault-Nissan are merely a few names that became high-profile victims of crippling WannaCry ransomware attacks.
In this article, I will dissect the WannaCry outbreak and provide tips for organizations to defend themselves against ransomware attacks, so stay tuned until the end.
What is the WannaCry ransomware attack?
WannaCry is a crypto-ransomware type, a malicious type of software used by attackers in the attempt to extort money from their victims. Unlike locker ransomware (which locks targets out of their device so they are unable to use it), crypto-ransomware only encrypts the data on a machine, making it impossible for the affected user to access it.
Just like any type of crypto-ransomware, this is exactly what WannaCry does: it takes the victims’ files hostage, claiming to restore them only if they paid a ransom.
Who was affected by WannaCry?
WannaCry targeted devices running Microsoft Windows OS, encrypting the data and requesting payment in Bitcoin in exchange for their return.
WannaCry behaved like a worm-type attack vector, being able to self-propagate on Windows devices. However, the fact that it was a worm was not the most significant thing about it. Instead, the methods it used to distribute itself were a concern, as they leveraged some critical Windows bugs that had been fixed by Microsoft two months before the outbreak.
WannaCry used an exploit dubbed “EternalBlue”, which took advantage of a security vulnerability that allowed malicious code to propagate without the user’s consent across systems set up for file-sharing.
What is EternalBlue?
EternalBlue is the vulnerability exploit name for the Service Message Block (SMB) protocol (CVE-2017-0144) implementation in Windows. The weakness originated from a bug that made it possible for a remote attacker to execute arbitrary code on a targeted machine and transmit specially designed data packets.
EternalBlue was created by the United States National Security Agency (NSA) as part of a questionable initiative of stockpiling and weaponizing software vulnerabilities rather than reporting them to the relevant provider, according to denouncing comments made by Microsoft.
The malicious hacker group Shadow Brokers leaked the cyberweapon in April 2017 and posted it online.
EternalBlue was one of the most useful tools in the NSA’s cyber arsenal until it got stolen. Security experts spent nearly a year discovering a flaw in Microsoft’s program and writing the code to target it, according to three former NSA insiders. They referred to it originally as EternalBluescreen because it frequently crashed machines. Yet, it became a reliable instrument used in numerous missions of intelligence collection and counter-terrorism.
On March 13, 2017, a month before EternalBlue was leaked, Microsoft patched the flaw. A large number of unpatched servers, however, still existed and were vulnerable to the exploit.
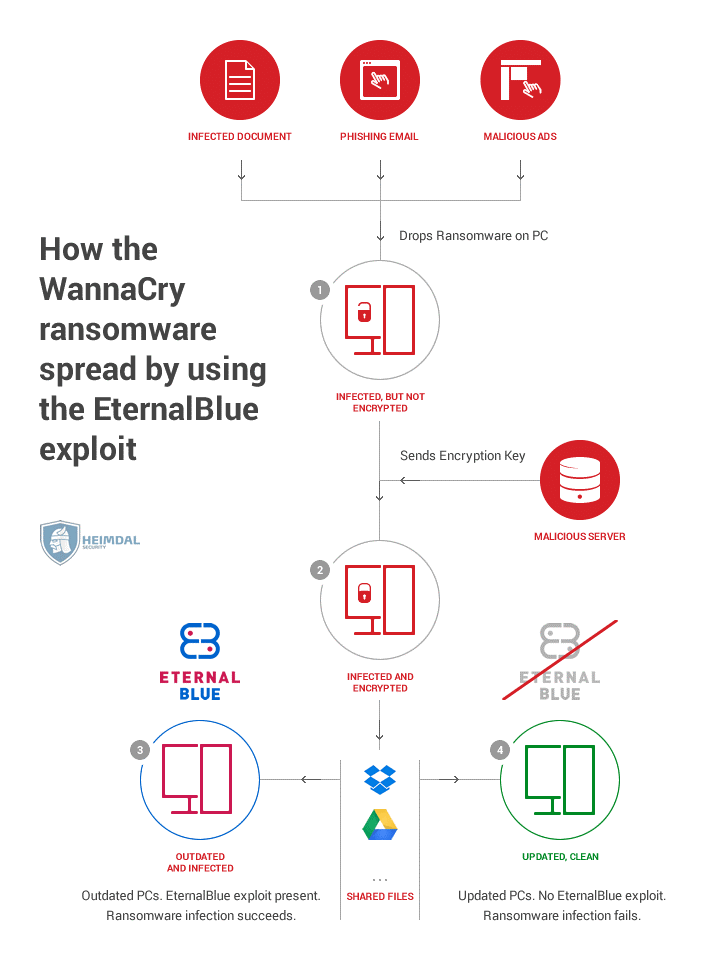
How does WannaCry ransomware spread?
WannaCry’s variant that incorporated the EternalBlue exploit first appeared at about 6 a.m. UTC on May 12, 2017, and quickly started circulating. Due to its ability to self-propagate and push itself through the network of an organization and then on to other entities via the Web, it was a novel and incredibly dangerous type of e-threat.
The ransomware used EternalBlue to spread to other machines on the local network until it placed itself on a computer. Besides, in an effort to locate other vulnerable devices, it tried to self-propagate throughout the Internet by analyzing random public IP addresses.
This aggressive dissemination process shows how certain organizations were highly influenced by WannaCry and how it managed to easily leap from one entity to another.
The malware also downloaded the DoublePulsar backdoor (part of the Shadow Brokers leak) following an infection. It was also stated that the malicious code aimed to use the DoublePulsar backdoor, which may have been mounted in a previous attack, even though the EternalBlue exploit failed. The vulnerability would enable the intruder to obtain remote access to the compromised device in order to flood the victim with additional malware or allow for data exfiltration.
WannaCry sought to contact a certain domain while it was activated on a machine. If the domain was inaccessible, it could continue to encrypt the files and try to distribute itself to other devices. Nonetheless, if the domain was reachable, the ransomware would not be downloaded.
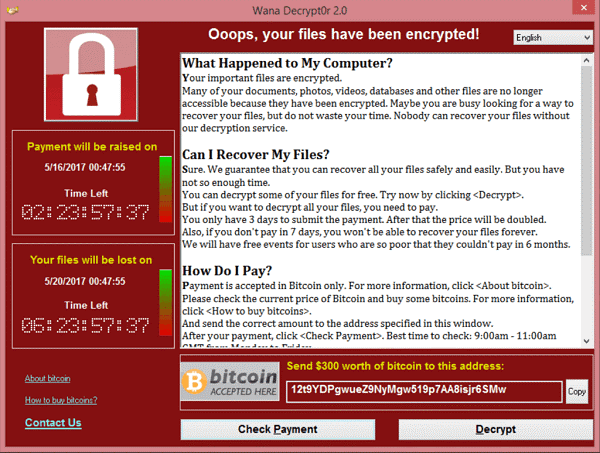
The WannaCry kill switch
The WannaCry kill switch functionality was soon accidentally discovered by security researcher Marcus Hutchins, who on May 12, registered a domain found in the ransomware’s binary code. Activating this kill-switch led to a rapid decline in attacks.
However, this practice did not permanently stop the attacks. As the malware could ignore proxy settings, the kill switch was not completely effective, as many affected devices were not directly connected to the Internet. Furthermore, additional variants with other kill switches had already been released, and thus the expansion of the outbreak continued.
Who was responsible for WannaCry?
Although average attacker groups typically release most ransomware, WannaCry allegedly originated from somewhere else. The investigation of an earlier version of WannaCry, which was used in a limited number of targeted attacks, indicated some crucial facts. The former variant was somewhat similar to the one used in May 2017, the only difference being that EternalBlue was not used as a tool for spreading, but rather relied on compromised credentials to propagate through networks.
Specifically, the techniques used in those early attacks have been shown to have close ties to the Lazarus Group, an organization that was engaged in numerous high-profile attacks, including the November 2014 devastating cyber assault on Sony Pictures.
Is WannaCry still a threat?
Almost three and a half years later, WannaCry still remains a threat. As per the ESET Threat Report of Q1 2020, WannaCryptor accounts for 40.5% of ransomware detections.
A timeline of key events in the WannaCry cyberattacks
To put things into perspective, below you can see how the WannaCry events unfolded, in a nutshell.
January 16, 2017
March 2017
- Microsoft publishes the patch for CVE-2017-0144 as part of their usual Patch Tuesday updates almost two months before the outbreak emerged.
April 14, 2017
- The Shadow Brokers cyber attackers group stole the EternalBlue toolkit from the NSA and leaked it on the Dark Web. The exploit targeted machines running the Windows OS and encrypted all files on an infected device, requesting a payment to be made in exchange for the data.
May 12, 2017
- Spanish telecom operator Telefónica was among the first major companies to confirm infection with WannaCry on Friday morning.
- Hospitals and clinics around the UK started reporting concerns to the national cyber incident response center by late morning.
- French carmaker Renault was struck, while Deutsche Bahn became another victim in Germany.
- The Ministry of the Interior, cell phone operator MegaFon, and Sberbank became compromised in Russia.
- The US was not spared either, with the highest-profile victim being FedEx.
- The WannaCry kill switch – by late afternoon, malware analyst Marcus Hutchins finds a kill switch and slows down its spread, becoming “an accidental hero for inadvertently stopping the cyberattack by registering a web domain found in the malware’s code”.
May 14, 2017
- Organizations start releasing free decryptors for WannaCry.
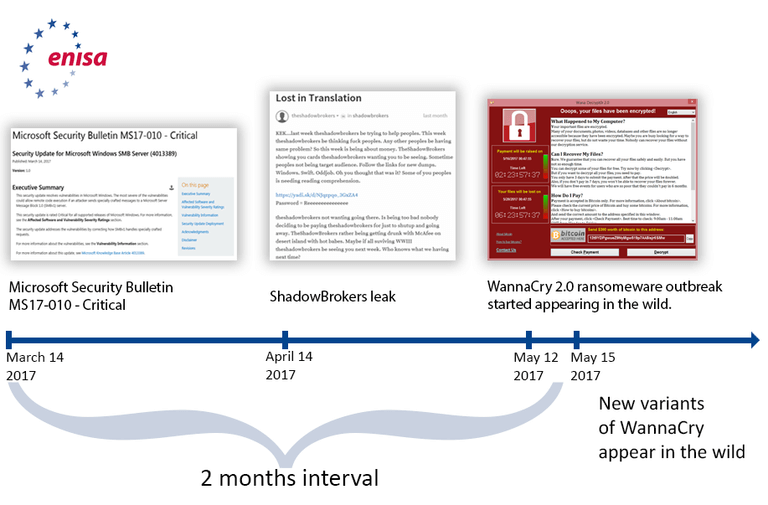
Image source: ENISA, WannaCry Ransomware Outburst
Lessons learned: The importance of a good cybersecurity posture
Following the WannaCry outbreak, pressing cybersecurity matters were brought to light. Namely, the importance of setting up secure and regular backups, using proactive cybersecurity software, staying up to date with the latest security patches, and isolating sensitive systems.
What’s more, the flawed patching practices of public and private sector organizations were proved to be an issue. They were (and in some cases still are) an inconsistent, irregular process, not based on a proper patch management policy.
WannaCry’s arrival showed how disruptive cyber incidents can quickly ambush unprepared organizations. The impact of these malicious events on institutions is never overlooked by cybercriminals. In fact, they only set the stage for more attackers who try to pursue similar attack techniques.
Therefore, businesses need to prepare themselves and make sure they have protections in place against all vectors of attack.
To better ensure that attack entry points are covered, organizations need to follow a multi-layered defense approach. This should entail not only periodically patching software flaws and ensuring the backup of sensitive systems, but also the use of interconnected protection technologies. These solutions include essential threat prevention and remediation mechanisms, such as Next-Gen Antivirus & Firewall, DNS Filtering at the endpoint and perimeter level, Email Security, and Privileged Access Management (PAM).
Ransomware can be distributed through various methods, with email remaining one of the main channels. Self-propagation (when it comes to “ransomworms”) can also be used.
Nevertheless, a crucial element in building an organization’s protection against ransomware is knowing where it comes from.
One of the most powerful means of defense is to stop attacks at their root until they get a chance to transfer themselves to multiple devices on a network. Thus, employee cybersecurity awareness, as well as having the most appropriate defenses against ransomware in place is crucial.
How Heimdal Security blocked WannaCry ransomware
Heimdal Security is always on the lookout to combat the most sophisticated cyber threats.
Our DNS filtering technology proactively blocked all efforts to exploit the vulnerability that WannaCry used, ensuring that our users were safe even before the outburst emerged.
Heimdal’s advanced DNS solution blocks network communication to mitigate Zero Hour exploits, Ransomware C&C’s, next-gen attacks, and data exfiltration. Using our ground-breaking Threat-to-Process-Correlation technology, we identify attack processes and provide HIPS capabilities.
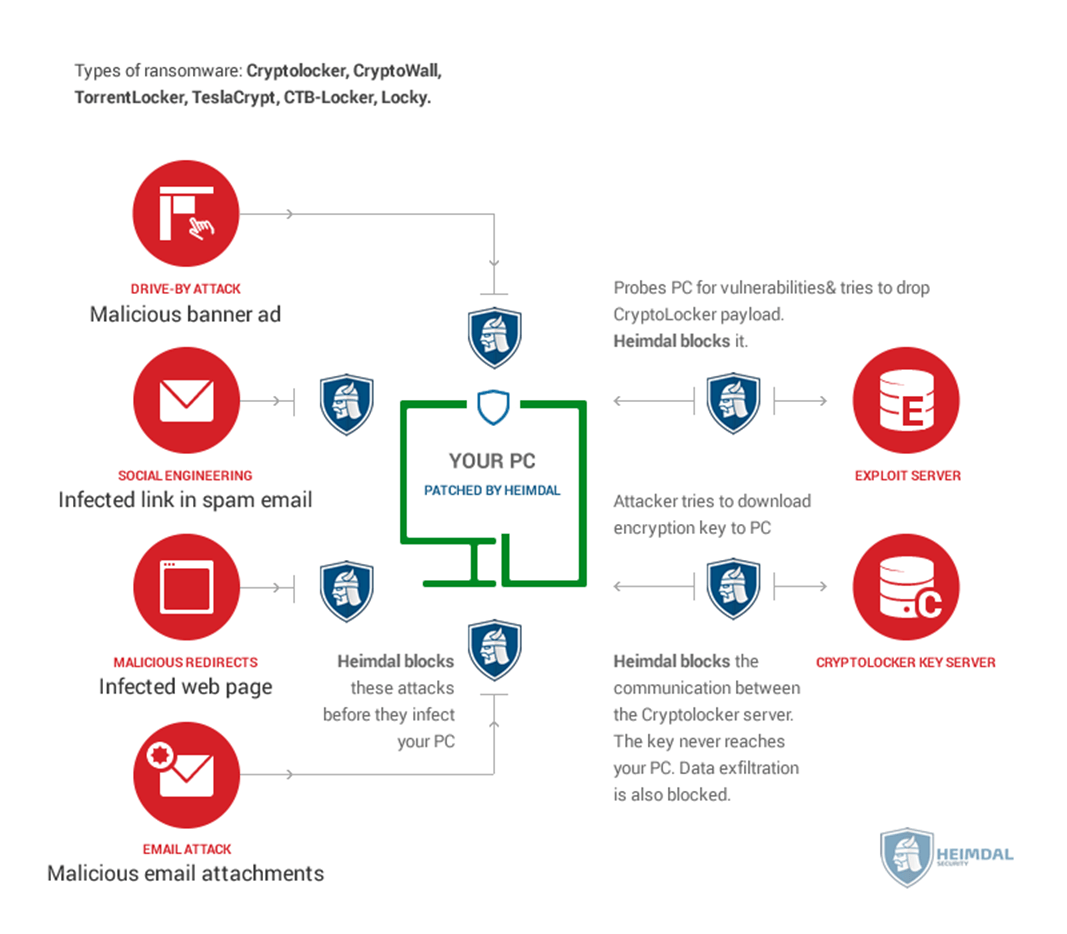
Heimdal offers protection where traditional cybersecurity products like antiquated Antivirus solutions give up. We provide attack blocking, patching, exploit blocking, dropper protection, and use five layers of protection to stop ransomware attacks at different levels.

- Next-gen Antivirus & Firewall which stops known threats;
- DNS traffic filter which stops unknown threats;
- Automatic patches for your software and apps with no interruptions;
- Privileged Access Management and Application Control, all in one unified dashboard
Bottom Line
Ransomware attacks can cause major damage, resulting in business delays and huge recovery costs. They can also lead to brand damage and customer losses, especially if cyber incidents become public. However, what you need to keep in mind is that paying the ransom may not work and your files may still remain encrypted, even if you did pay. Thus, your safest bet against ransomware is to be prepared before it strikes. Build your cyber resilience to battle ransomware and stay away from stressful scenarios, costly losses, and unplanned downtime.
Have you or your company been affected by WannaCry? How do you protect your organization against ransomware? We’re waiting for your comments in the section below!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










