Contents:
Virus vs. worm – is there any difference? Short answer: yes, definitely, and you should never confuse one with the other. In this article, I’m going to introduce you to the distinctions and similarities between worms and viruses and provide you with a protection guide from which you and your organization can benefit from.
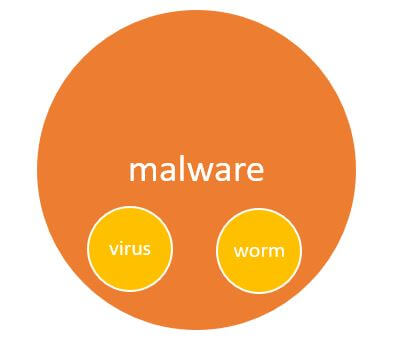
Malware vs. virus vs. worm
Malware depicts any type of malicious software or code implanted on a device with the purpose of causing damage. It includes ransomware, spyware, adware, and other types of harmful programs. Here is how the National Institute of Standards and Technology (NIST) defines it:
“Malware, also known as malicious code and malicious software, refers to a program that is inserted into a system, usually covertly, with the intent of compromising the confidentiality, integrity, or availability of the victim’s data, applications, or operating system or otherwise annoying or disrupting the victim.” – NIST Special Publication 800-83
Viruses and worms are other types of malware created to execute malicious functions. In the early days of cyber threats, they were more of a nuisance for organizations and individuals rather than a potential hazard.
However, today’s malware landscape portrays a never-ending battle between cyber defense specialists and cyber intruders, with the global threat environment changing year after year. Now, malicious software has become a serious threat, with over 350,000 new malware strains and potentially unwanted applications (PUA) being created every day, according to the AVTest.
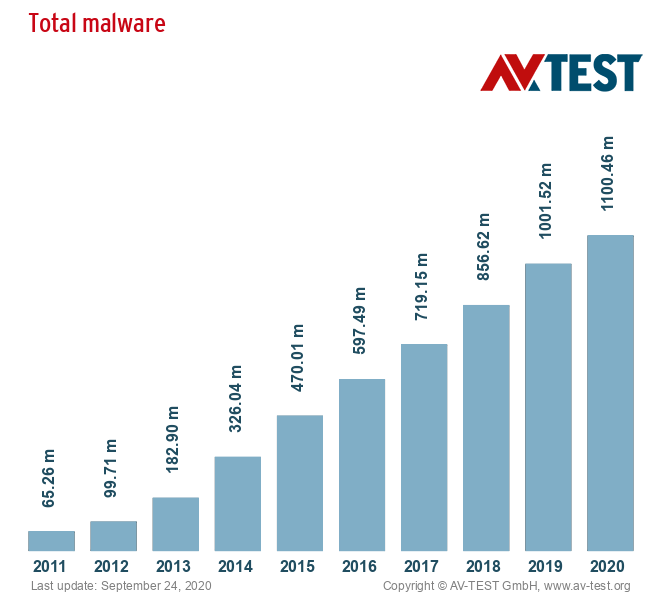
At the current trajectory, it’s no wonder that organizations and consumers are struggling to keep up their defenses. But naturally, not all malware types are created equal, and in this article, I’m going to look at two very specific types of malware: viruses and worms.
What is a Computer Virus?
With reference to cybersecurity, “virus” is perhaps the most widely recognized term and oftentimes used interchangeably with “malware”. However, as I’ve already stated above, “malware” and “viruses” are not synonyms – malware is the all-encompassing term for all types of malicious software, including viruses.
A brief history of computer viruses
The concept of “computer viruses” was first hypothesized by John von Neumann in the late 1940s and further elaborated in a paper published in 1966 (Theory of Self Reproducing Automata) after his death. The piece speculated that it would be possible for a technological organism to behave just like a biological virus, damaging machines through self-replication and having the ability to move from device to device. The early 1970s marked the beginning of the actual computer viruses – well, sort of. The first virus named Creeper had no malicious purpose and only displayed “I’M THE CREEPER. CATCH ME IF YOU CAN!” message on the screen. In practice, it was an experimental computer program written by Bob Thomas in 1971, in the attempt to find out if a self-replicating program was actually viable. Its first version was designed to move between DEC PDP-10 mainframe computers running the TENEX operating system through the ARPANET (the network that became the technical foundation of today’s Internet).

A short time later, Ray Tomlinson wrote an enhanced version which did not just move – now it was also capable of self-replicating. Afterward, another program (called Reaper) was created by Tomlinson which was meant to go through the ARPANET and removed Creeper. If you are curious to find out more and about the history of computer viruses and go through their timeline, I suggest you check out this resource. Now, let’s go back to what a computer virus is and what it does. In our HeimdalTM Security glossary, we define viruses as follows:
“A computer virus is a type of malicious software capable of self-replication. A virus needs human intervention to run and it can copy itself into other computer programs, data files, or in certain sections of your computer, such as the boot sector of the hard drive. Once this happens, these elements will become infected. Computer viruses are designed to harm computers and information systems and can spread through the Internet, through malicious downloads, infected email attachments, malicious programs, files, or documents. Viruses can steal data, destroy information, log keystrokes and more.” – Heimdal Security Glossary, “Virus” Definition
Various types of viruses act differently. For instance, some may begin replicating and causing damage on a machine as soon as they enter a host, while others may lie dormant and remain undetected until a specific stimulus triggers the execution of the malicious code on the computer system.
Types of viruses
According to TechTarget, there are seven categories of computer viruses.
File infectors
File infector viruses usually attach themselves to program files – typically .com or .exe files. They may infect programs that require execution (including .sys, .ovl, .prg, and .mnu files). In this case, whenever a program is run, the virus runs along as well. Some viruses that infect files come as totally contained programs or scripts sent to email notes as an attachment.
Macro viruses
In applications like Microsoft Word and other programs, these viruses target macro language commands directly. In Word, macros are sequences that are stored for commands or keystrokes inserted in documents. Macro viruses in a Word file will apply their malicious code to the valid macro sequences. In more recent versions of Word, Microsoft removed macros by default; as a result, hackers used social engineering schemes to persuade targeted users to allow macros and trigger the virus. Microsoft introduced a new function in Office 2016 that enables security managers to selectively permit macro usage only for trustworthy workflows, as well as ban macros within an enterprise, as macro viruses have seen a revival in recent years.
Overwrite viruses
These are specially designed to delete the data of a file or program. An overwrite Virus starts replacing files with its own code after infecting a system. These viruses may corrupt particular files or applications or destroy all files on an affected computer. New code can be inserted in files and apps through an overwrite virus, which allows it to propagate to additional files, software, and systems.
Polymorphic viruses
A polymorphic virus is a malware type that, without modifying its basic functions or functionality, is able to modify itself or morph its underlying code. This approach enables it to avoid being detected by antimalware software that relies on signature recognition. When a security tool detects the signature of a polymorphic virus, it will then change itself in such a way that it can no longer be identified by its initial signature.
Resident viruses
They embed themselves in a system’s memory. To infect new files or programs the original virus program is not necessary – even if the original virus is removed, when the operating system loads a particular application or operation, the version stored in memory will be enabled. Resident viruses are troublesome because, by residing in the RAM of the device, they can bypass anti-virus and antimalware tools.
Rootkit viruses
A rootkit virus is a form of malware that installs an unwanted rootkit on an infected device with the ability to radically alter or disable features and programs, allowing cyber attackers total control over the system. Rootkit viruses were designed to circumvent antivirus software, which only scanned apps and files.
System or boot-record infectors
These viruses corrupt executable code discovered on a disk in some system locations. They connect to the DOS boot sector on USB thumb drives or the Master Boot Record on hard disks. In a standard attack case, storage devices containing a boot disk virus are received by the user. Files on the external storage unit will corrupt the system while the victims’ operating system is running. The boot disk virus will be triggered by rebooting the system. An infected computer-connected storage device will change or even replace the original boot code on the infected system so that the virus is automatically loaded and executed as part of the Master Boot Log when the system is next booted. Boot viruses are now less prevalent as physical storage media are less reliant on today’s devices.
Notorious computer viruses
Below you can see some examples of the most devastating computer viruses in history:
ILOVEYOU
ILOVEYOU is thought to be one of the worst viruses ever created. With about $10 billion worth of damage, it has managed to destroy 10% of computers around the world. Its severity had been so high that large companies and governments were forced to close their mailing systems to avoid contamination. Being developed by two Filipino programmers, Reonel Ramones and Onel de Guzman, it was based on social engineering and fooled individuals into opening an email attachment, that posed as a harmless TXT file. At that time (the year 2000), Windows did not show the extension of files. When the victim clicked on the file, the virus would send itself to everyone in the mailing list and overwrote files with itself, which made the device unbootable. At that time, the two malicious hackers were not charged, as no laws existed when the cyber crimes took place.
Melissa
In late March 1999, the Melissa virus started spreading like wildfire on the Internet. Although it was not meant to steal money or the users’ data, it did produce a lot of damage. The email servers of over 300 companies and governments become affected and some of them had to be closed completely – even Microsoft was one of the victims. Around 1 million accounts had been infected. The virus emerged by corrupting the victims’ Microsoft Word software, using a macro to attack their Outlook email system and send emails to the first 50 contacts in the target’s list. The messages tricked people into opening attachments titled “sexxxy.jpg” or “naked wife” or by deceitfully asserting, “Here is the document you requested … don’t show anyone else ;-).” Being based on social engineering, many people fell prey.
Shamoon
The Shamoon virus was created for cyber-warfare, being designed by cybercriminals to fight against oil companies of Saudi Arabia and Qatar. It transferred malicious content from an infected computer to other network-attached computers. The actions of the virus and the result of the infection of the malware differs from other malware types. What this specific virus did is it took files from an infected computer, uploaded them to the attacker’s device, and then deleted them. Then, it overwrote the infected system’s master boot record, rendering it impossible to use.
What is a Computer Worm?
Unlike viruses, worms don’t rely on users’ intervention to be able to propagate. In short, a worm is a malware type that can move and copy itself from device to device as a self-contained program. The capability to function independently is what separates worms from other types of malware without the need for a host file or to infiltrate code on the host machine, which makes them superior to viruses and consequently, more dangerous. Worms rely on vulnerabilities found in a system. While viruses may trick you into activating them or attempt to exploit holes in applications using social engineering tactics, a worm finds flaws in the OS that allow it to install and make copies of itself. The Morris Worm is widely known as the first major malware of any type and the first computer worm that actually had a real-life impact. Set loose in November 1988, the worm was designed by Robert Morris, a graduate student at Cornell University at that time. He launched the attacks from the MIT servers, allegedly to conceal its action.
A shortlist of famous computer worms
The spread of computer Worms resulted in some of the most devastating malware attacks of all time. Below I’ve listed some of the most dangerous ones in history.
Stuxnet
The Stuxnet Worm was first seen during the summer of 2010, being originally aimed towards Iran’s nuclear facilities. It managed to destroy multiple centrifuges in the country’s Natanz uranium enrichment facility by causing them to burn themselves out. According to Stuxnet’s log files, a company called Foolad Technic appeared to be the first victim. A random worker’s USB drive is thought to have initially launched the worm, which then spread to Microsoft Windows computers.
MyDoom
On January 26, 2004, MyDoom emerged and distributed through email and via a P2P network. The virus was written in the C++ programming language and emerged from Russia, producing a backdoor in the operating system of the victims’ computer. The virus launched a denial of service (DDoS) attack on Feb 1, 2004, and it stopped spreading itself on Feb 12. The backdoors produced during the initial infections remained active, even after the infection spread.
Sasser
A 17-year-old German named Sven Jaschan developed the Sasser worm. What this malware did is it once it corrupted a device, it started looking for other vulnerable computers, scanning for random IP addresses to find its next victims. Even though it did not cause any physical damage, it was the root cause of DDoS attacks. For instance, it stopped one-third of the post offices in Taiwan, closed 130 branches of a bank in Finland, and lead to the cancellation of several rail and transatlantic flights.
Computer Worm vs. Virus
As I’ve already mentioned before, both viruses and worms can cause major damage to your organization and spread quickly. What sets them apart is the way in which they self-replicate, with viruses requiring the aid of users, while worms are able to act on their own.
|
Virus |
Worm |
| A virus requires a user to either purposely or inadvertently spread the infection, without the knowledge or permission of a system administrator. | A computer worm is a stand-alone malware that self-replicates and does not require any form of human intervention to propagate – for instance, it can rely on security vulnerabilities. |
How do viruses and worms spread?
Viruses need human activity (such as the execution of an infected program) to propagate, as described above. Worms, however, can spontaneously spread, without the user doing anything. Yet, how do devices become infected with a virus or worm, in the first place? The most common methods of infection are:
- Email. Social engineering tactics and infected email attachments or malicious links go hand in hand. Email is one of the most widely used methods for delivering viruses and worms.
- Infected websites. Viruses and worms can be delivered in the form of infected banners or pop-ups on webpages, sometimes even on legitimate sites.
- Security flaws. Oftentimes, vulnerabilities found in systems allow ill-intentioned actors to exploit them and inject malware into an organization’s systems. Worms are able to scan networks, identify vulnerabilities, and then exploit them.
- P2P downloads: Pirated games or TV shows illegally downloaded from unauthorized sources may also bring along unwanted malicious software, including worms and viruses.
How to protect your business against viruses and worms
While viruses and worms have an enormous capacity for destruction, if you follow some best practices you will be able to prevent them. Always staying vigilant and carefully examining the email attachments you receive (especially from unknown senders), not clicking on suspicious links, and updating your software are a few essential steps you and your colleagues can take to prevent cyber incidents. We strongly believe cybersecurity awareness is one of the best defenses against malware and thus, we advocate for continuous cybersecurity education. However, as human errors are oftentimes inevitable and can have dire consequences, organizations must undertake additional protection measures. Although running enterprise antivirus software is a vital first step, it won’t keep your company safe from certain employee behavior such as clicking malicious links or using outdated versions of your software. Endpoint Security Software integrates state-of-the-practice capabilities that support secure systems and strengthen an organizations’ security, privacy, and uphold cyber resiliency based on the latest threat intelligence and cyber-attack data. More precisely, our complete endpoint security solution covers Threat Hunting, Prevention, and Mitigation thanks to its DNS filtering technology (which proactively blocks known and yet unknown malware infections, phishing attacks, and data exfiltration), a next-gen Antivirus, and a vulnerability management tool (for software deployment, inventory, and automatic patching).

- Next-gen Antivirus & Firewall which stops known threats;
- DNS traffic filter which stops unknown threats;
- Automatic patches for your software and apps with no interruptions;
- Privileged Access Management and Application Control, all in one unified dashboard
Bottom Line
In conclusion, both viruses and worms can spread rapidly and cause damage – from mild to catastrophic. The main difference between them is how they self-propagate, with viruses requiring a host’s intervention and worms working independently. The consequences of virus or worm infections may lead to issues related to the performance of devices, money and data loss, and even reputational damage or even extensive, nation-wide attacks.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security