Contents:
The first step in protecting any computer against WannaCry, Uiwix and other ransomware campaigns is to apply the critical patch that Microsoft released in March 2017 (Microsoft Security Bulletin MS17-010).
Step 1: Check this list to see if your system is exposed
This is the list of Windows software which need the update in order to close the vulnerabilities in SMBv1 and SMBv2:
- Microsoft Windows Vista SP2
- Microsoft Windows Server 2008 SP2 and R2 SP1
- Microsoft Windows 7
- Microsoft Windows 10
- Microsoft Windows 8.1
- Microsoft Windows RT 8.1
- Microsoft Windows Server 2012 și R2
- Microsoft Windows Server 2016
- Microsoft Windows XP
- Microsoft Windows Server 2003.
You can also use the Microsoft Baseline Security Analyzer 2.3 to scan your PC or your environment and discover which updates are missing on your endpoints. The tool also lists the missing updates by severity and potential impact. Here is a helpful guide on how to use it (text version):
Step 2: Download and install the update
Once you’ve identified the vulnerabilities in your environment, the next step is to find and apply the necessary updates. Fast.
In order to counteract the limit the widespread threat that WannaCry and Uiwix are posing, Microsoft released new Security Updates packages so that all systems will be protected against the exploit, including unsupported systems, such as Windows XP or Windows Vista.
We’ve chosen to illustrate each step by using the update for Windows 7, since it’s the operating system with the highest number of users at the moment.
-
- Go to the Microsoft Security bulletin where you’ll find links to all the links for the security update packages.
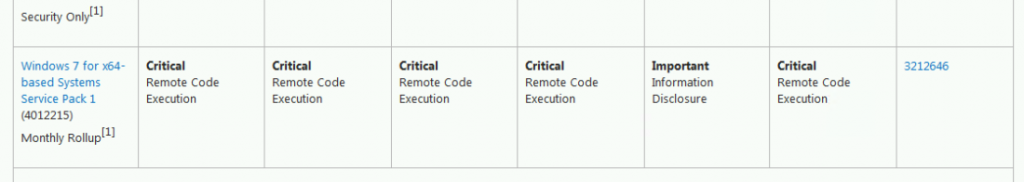
- Scroll down to the operating system that you are using. In our example, it was Windows 7 64bits.
- Click on the package you need. In our example, we used Windows 7 for x64-based Systems Service Pack 1 (4012215) Monthly Rollup. Make sure it’s the Monthly Rollup link that you choose!
-
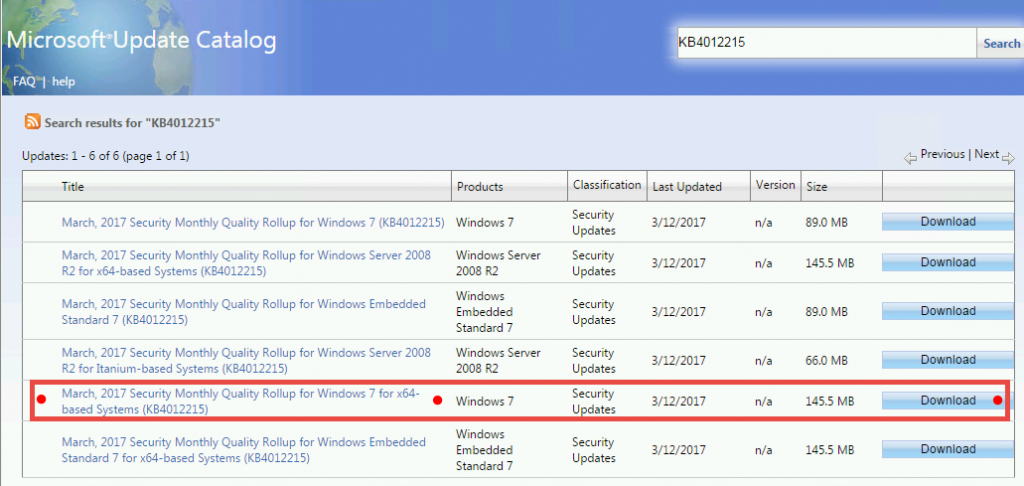
- A new window will open. Select the update for the windows version that you have and press Download.
-
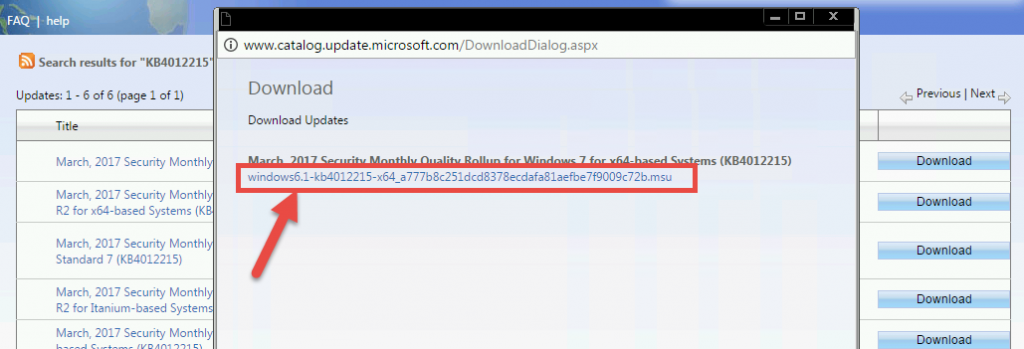
- Click on the link that will appear after you press the Download button:
-
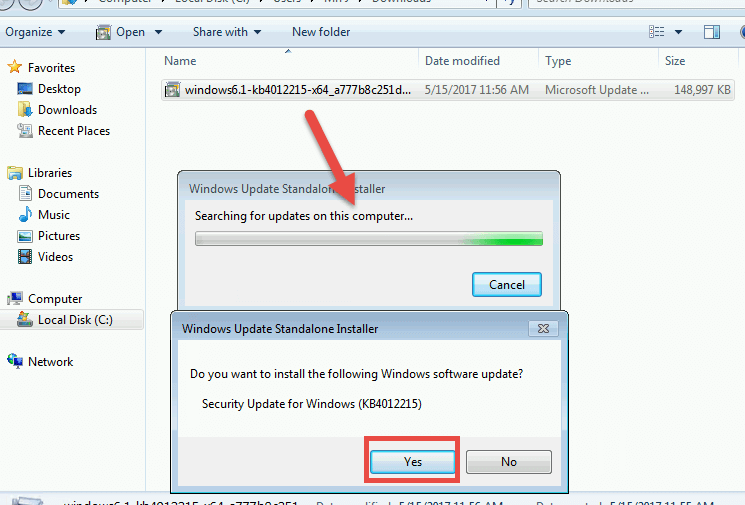
- After the download is complete, run it as you would run any other setup.
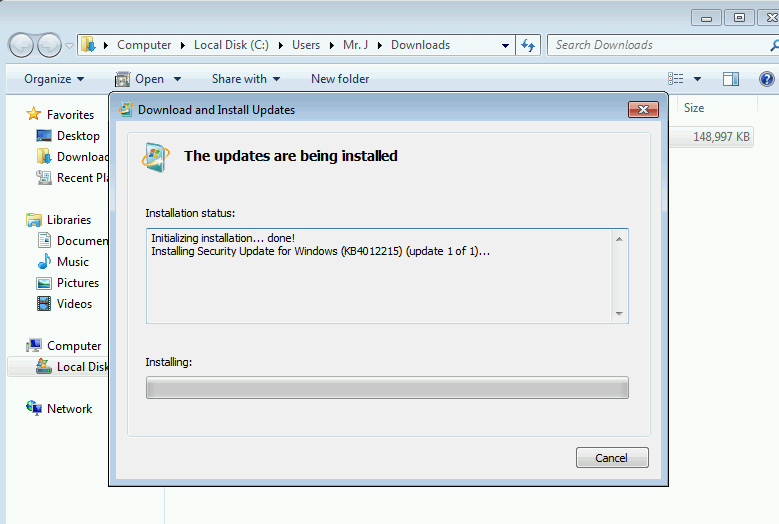
- It will ask you if you want to install the Windows software update. Press Yes and this will initialize the installation setup:
- At the end of the installation it will ask you to restart the computer. Restart it.
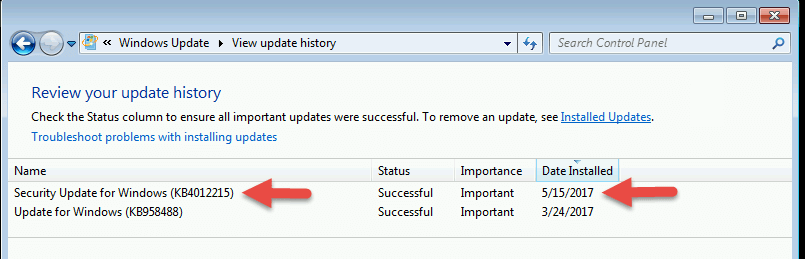
- To check if the installation was successful, you can go to Control Panel > Windows Updates > View update History (on the left side) and see if the Security Update for Windows is installed. It should have the current date in the Date Installed column.
IMPORTANT!
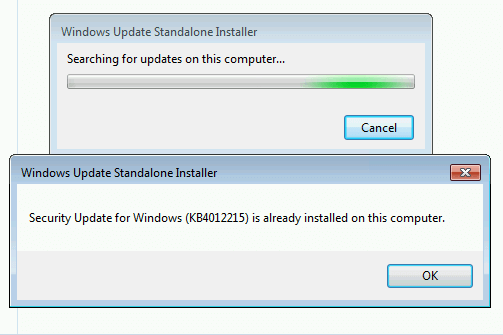
If the update has already been applied or installed, then you will receive a message informing you about it.
Also, make sure you follow the security alerts for WannaCry ransomware attacks and the Uiwix ransomware threat. We will keep these alerts updated at all times.

INSTALL IT, FORGET IT AND BE PROTECTED
Download Heimdal™ FREE

 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security