Contents:
On April 11, Vista will reach end of life. And Microsoft Office 2007 will share the same fate.
Don’t worry, you can keep using your Vista PC if you want. Microsoft won’t press a kill switch to turn off all Vista computers out there.
Microsoft operating system support periods
Microsoft generally stops supporting their older operating systems in order to push users to adopt the latest technologies in newer versions.
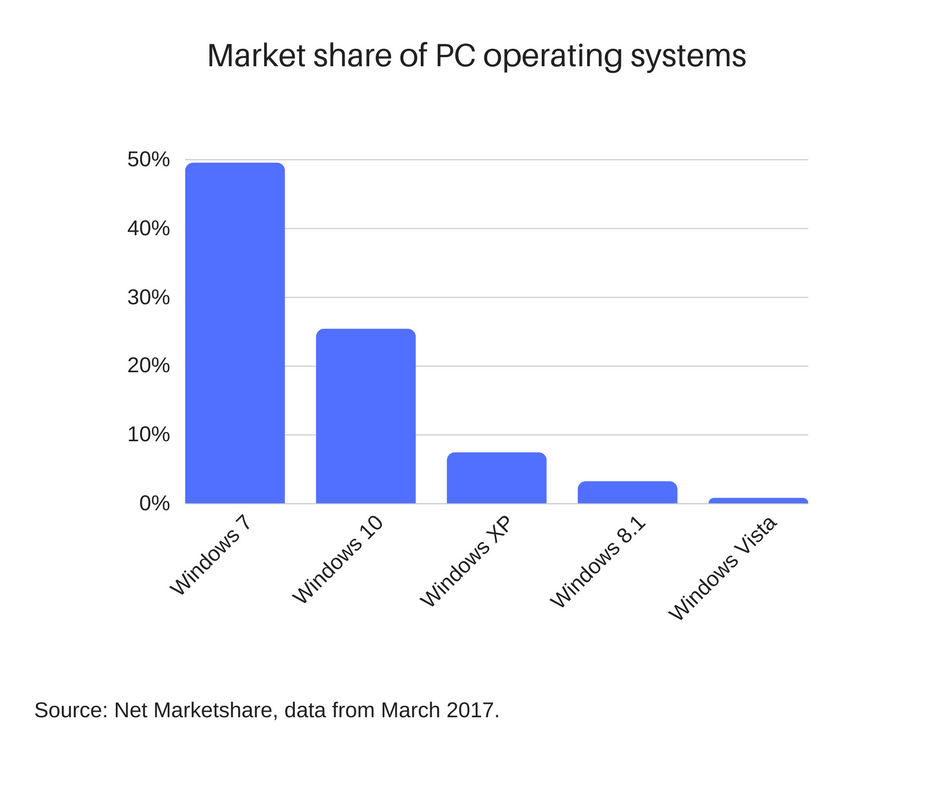
Right now, Vista has only 0.78% of the global PC operating system market share.
To put that into hard numbers, that means nearly 11.7 million devices of the estimated 1.5 billion active PCs worldwide.
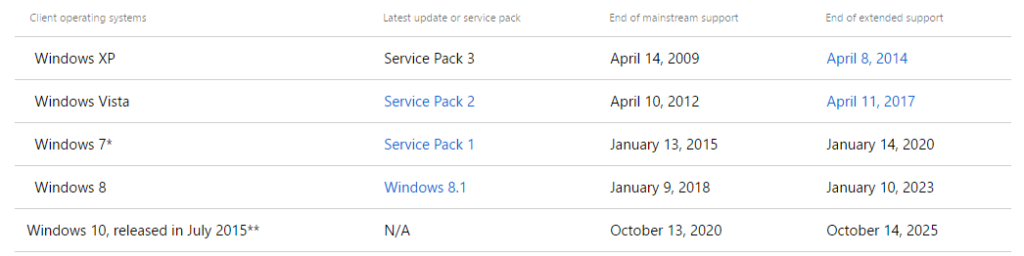
As a policy, Microsoft offers mainstream support for a minimum of 5 years after a product launch. Mainstream support means that Microsoft will continuously add new features over this interval, improve the design, offer free support and patch any security issues.
Windows Vista launched in January 2007, and its mainstream support ended April 2012.
After the mainstream support period is over, the product enters the extended support phase, which also lasts a minimum of 5 years. This means that no new features or redesigns will take place. The only thing that Microsoft does do in this interval is to update and patch any security issues and bugs it might find along the way.
For Vista, the extended support period started on April 2012, and ends on April 11 2017.
What does this mean for your cybersecurity?
Here’s what you need to know now that your Vista OS has nearly reached its end of life support.
Many new products will not be backwards compatible with your PC
Newer devices, such as printers or webcams, might not be compatible with your Vista operating system. This can be for a variety of reasons, such as the absence of a critical OS feature, or the developer didn’t consider it cost-effective to provide backwards compatibility for software with only 0.78% market share.
And since Vista also passed its end of mainstream support, there are zero chances for it to acquire the missing features that might attract developers and hardware makers.
The same logic applies to software programs. Given how small Vista’s market share is at the moment, a developer has next-to-no incentive to even consider making his program or game backwards compatible with the OS.
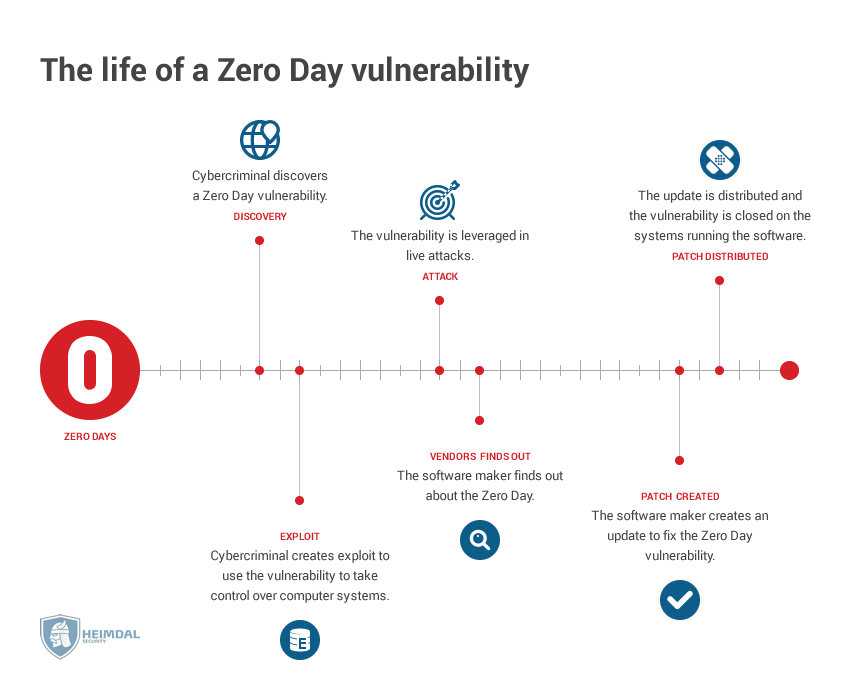
No more security updates, meaning Zero Day attacks forever!
A Zero Day vulnerability is a weakness or bug in the software which the developer hasn’t yet patched. These are particularly dangerous, since there’s not much an OS (or any other software for that matter) can do to defend itself.
Depending on type of vulnerability he exploits, a Zero Day attacker can intercept the data your PC sends and receives, deactivate certain programs or functions, simplify a malware infection process, or even take full control of your device with a buffer overflow or code injection exploit.
Since no more security updates will be released for Vista, then every vulnerability discovered after April 11, will be a Zero Day, forever.
But you see, this problem becomes even more acute if you need to use programs that are not backwards compatible with Vista. As a workaround, you end up using older versions of software apps that still work with your OS. But those versions are also outdated and vulnerable to exploitation. One clear such example is Internet Explorer 9, which went out of support on January 12, 2016. Combining two outdated software won’t take you anywhere, security wise.
What happened to previous operating systems?
Vista’s predecessor, Windows XP, reached end of life in April 2014, three years ago. That’s sufficient time to gather some conclusions, and see how it has aged from a cybersecurity perspective.
Number of vulnerabilities
According to CVEdetails, Windows XP has nearly 620 vulnerabilities with a severity score between 5 and 10.
Chances are there are many more than that however, but neither Microsoft nor other software developers have any reason to make them public, given that they will never be patched.
As a comparison, nearly 650 vulnerabilities have been found for Windows Vista but in a much shorter time frame.
These are vulnerabilities are here to stay, and cybercriminals aren’t shy of using them.
In one of the more recent examples, malicious hackers were able to bypass the strong defenses of three US hospitals by exploiting vulnerabilities found in a few left-over XP devices. The malware and exploits used were so old, the hospital’s defenses weren’t able to pick them up. As a result, a few of their medical devices such as X-ray machines and fluoroscopy devices were broken into and compromised.
Exploitable ATMs and other devices
95% of ATMs around the globe were powered by Windows XP as recently as 2014. The number has certainly declined, but not by much, given that their life spans can average out to as high as 7 years.
[Tweet “Did you know 95% of ATMs ran on Windows XP as late as 2014?”]Kaspersky did an interesting run down explaining why it can be fairly easy for a cybercriminal to hack into an ATM and clean it of money.
Since ATMs are basically PCs, it is possible for a hacker to infect them with a USB stick or another external device that can connect to it.
But even if all of the physical ports of an ATM are properly secured and inaccessible, it’s still possible to break into one by intercepting the internet traffic it sends and receives.
Combine all those vulnerabilities with an outdated software like Windows XP, and you start to realize how big of a risk it is to use an unsupported operating system.
Windows XP computers are vulnerable to botnets
Botnets are extensive networks of infected PCs controlled by a command and control center, and used for various criminal activities, such as DDoS, click fraud or Bitcoin mining.
A PC gets enslaved into a botnet through the way of rootkits, Trojans and other malware. Windows XP was particularly prone to this, but the lack of security only makes it more vulnerable.
Practical steps to avoid Vista vulnerabilities
The easiest way to avoid the end-of-life security limbo is to upgrade from Vista to any of the more modern Windows OS versions.
In most cases, switching to a new operating system requires that you do a clean install, meaning a complete wipe of your computer and start again fresh.
However, you may have files and other programs on your PC which you aren’t willing to lose. Fortunately, Microsoft has provided you with a way around this, called “in-place updates.”
We’ll quickly go over both of these options.
Do an in-place upgrade to Windows 7
If you don’t want to lose all your files and programs, you can upgrade to Windows 7. Within one or two hours, you’ll have a completely new OS, and keep your original files and folders.
Unfortunately, this works only for Windows 7. So if you want to upgrade to Windows 8/10, you’ll need to use Windows 7 as a stepping stone.
If you’re interested in upgrading to Windows 7, then you can use this guide.
Do a clean Windows 8/10 upgrade
It’s not possible to upgrade to Windows 8/10 without doing a clean install and wipe of your system. However, you can (and should) backup many of your files and applications before doing the installation.
Here’s an in-depth guide on how to properly back up your PC and preserve your data.
Next, you should decide on whether to upgrade to Windows 10 or Windows 8. Generally speaking, it’s best to upgrade to the latest version since it provides newer technologies, longer support and in the case of Windows 10, wider adoption.
If you’re still undecided, then check out this comparison between Windows 8 and 10.
If you opt for Windows 10, we recommend you check out our Windows 10 Security Guide to help you in your task of securing the operating system.
Use a virtual machine for older programs
You might be reluctant to switch to a new operating system because you already use old software for work or play that isn’t compatible with a new operating system. For these cases, we suggest you upgrade to a new OS and use an emulator for the old software.
A virtual machine is basically a software program that emulates another device or operating system. Think of it as a Matrioshka doll, where the big doll is your main Windows 7 PC, and the small doll is an emulated Windows XP/Vista.
For instance, you can use a virtual machine on your Windows 7 OS, to create a separate environment that runs a Windows XP/Vista operating system. In this case, the old program you use isn’t compatible with Windows 7, but you can run it using the Windows XP virtual machine.
Here’s an article for beginners on how to install and use virtual machines.
Switching from Windows Vista if you are a business
Switching from Vista gets complicated in case you are business.
One way is to manually upgrade each and every PC to your desired version of Windows, and apply the tips we talked about above to every device.
Another upgrade method is to use image cloning software such as Acronis or other similar programs to “feed” a certain Windows image from the main source to the other PCs connected to the network.
Some businesses however are subject to regulations that compel them to have their software constantly updated, such as the GDPR legislation in Europe. This becomes even more important for businesses and professions that handle sensitive, legal or private data. For these companies, not using an up-to-date OS isn’t just a cyber threat, but also a legal problem.
Switching from pirated Vista
Using a pirated version of Vista exposes you to even more potential avenues of attack. These installations of Windows might be buggy and malware-infested from the get go.
Another thing going against pirated Windows is that they don’t always receive updates, meaning that they already have serious security flaws.
Fortunately, upgrading from a pirated to a genuine Windows version doesn’t cost more than an upgrade between two genuine ones. Just follow the steps we’ve outlined above and you’re good to go.
Conclusion
“Update your software” is usually the top security advice shared by experts, alongside the use of strong passwords and security software. And of all the software that you do have, updating your OS should be a top priority.
“The end user who hasn’t found out the hard way that failing to patch and update both operating systems and third party products only leads to data loss or financial crime.”
Peter Kruse, from our “Is Internet Security A Losing Battle” Round Up

INSTALL IT, FORGET IT AND BE PROTECTED
Download Heimdal™ FREE

 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security