Contents:
Every day, cybersecurity specialists detect over 200,000 new ransomware strains. This means that each minute brings no less than 140 strains capable of avoiding detection and inflicting irreparable damage. But what is ransomware in the end? Briefly, ransomware is one of the most common and most dangerous cyber threats of today, with damaging consequences for individuals and businesses alike.
In this article, I will explain what ransomware is, how it works, how to prevent it, and what to do if attacked. Besides, recent statistics and ransomware examples will show you real facts to make you understand how ransomware attacks really happen.
What Is Ransomware?
Ransomware is a type of malware that blocks users from accessing their operating system or files until a ransom is paid. It does so by locking the system’s screen or encrypting the users’ files.
The victims receive a ransom note informing them that they must pay a certain amount of money (usually in Cryptocurrencies) to regain access to their system or data. There is generally a time restriction for completing the payment, else the files may be lost permanently or made public by attackers. It should be reminded that even if the victim pays the ransom, there is no assurance that the decryption key will be delivered.
How Does Ransomware Work?
Every ransomware has different behavior. There are 2 types of ransomware: locker ransomware and encrypting ransomware. The first locks the victim out of the operating system making it impossible to access the desktop and any apps or files and the latter is the most common which incorporates advanced encryption algorithms and it’s designed to block system files.
However, the result is always the same. Locking files or systems and demanding a ransom for their recovery. Here are some common steps on how ransomware works:
1. Ransomware Delivery and Deployment
Cybercriminals simply look for the easiest way to infect a system or network and use that backdoor to spread the malicious content. Nevertheless, these are the most common infection methods used by cybercriminals:
- Phishing email campaigns that contain malicious links or attachments (there are plenty of forms that malware can use for disguise on the web);
- Security exploits in vulnerable software;
- Internet traffic redirects to malicious websites;
- Legitimate websites that have malicious code injected into their web pages;
- Drive-by downloads;
- Malvertising campaigns;
- SMS messages (when targeting mobile devices);
- vulnerable Remote Desktop Protocol exploitation.
2. Lateral Movement
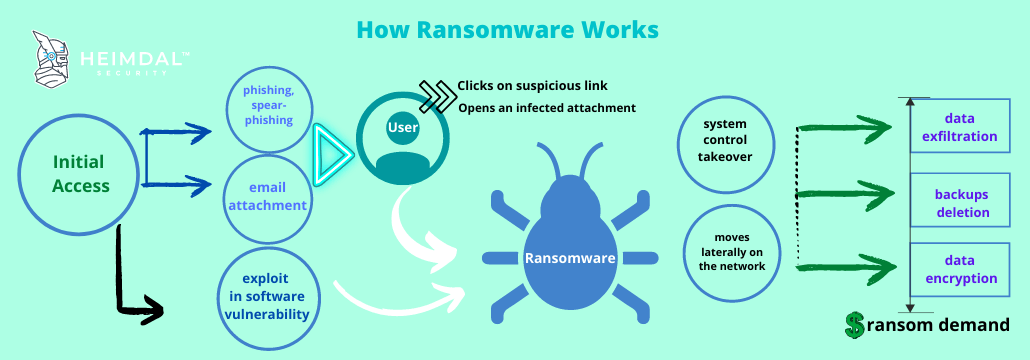
After the initial access, ransomware spreads via lateral movement tactics to all devices in your network and tries to get full access. If no micro-segmentation or network segmentation is put in place, the ransomware will move laterally on the network, this meaning that the threat spreads to other endpoints and servers in the entire IT environment, therefore engaging in self-propagation. This way, hackers can use detection evasion techniques to build persistent ransomware attacks.
3. Attack Execution
Data exfiltration
If in the past ransomware used tactics like weak symmetric encryption, now ransomware operators leverage more advanced methods like data exfiltration. Basically, hackers can exfiltrate sensitive business data before making the encryption leading to double extortion: this way, cybercriminals can threaten organizations to make their private information public if the ransom is not paid. Keeping data hostage is no longer the only method.
Destroy backups
Ransomware will look for backups in order to destroy them before encrypting data. This type of malware can recognize backups by file extension and documents stored in the cloud could be at risk too. Offline backup storage or read-only features on backup files might prevent backups recognition and deletion.
Data Encryption
Ransomware is practically the combination of cryptography with malware. Ransomware operators use asymmetric encryption, a.k.a. public-key cryptography, a process that employs a set of keys (one public key and one private key) to encrypt and decrypt a file and protect it from unauthorized access or use. The keys are uniquely generated for the victim and only made available after the ransom is paid.
It is almost impossible to decrypt the files that are being held for ransom without access to a private key. However, certain types of ransomware can be decrypted using specific ransomware decryptors.
Demand Ransom
After encryption, a warning pops up on the screen with instructions on how to pay for the decryption key. Everything happens in just a few seconds, so victims are completely dumbstruck as they stare at the ransom note in disbelief.
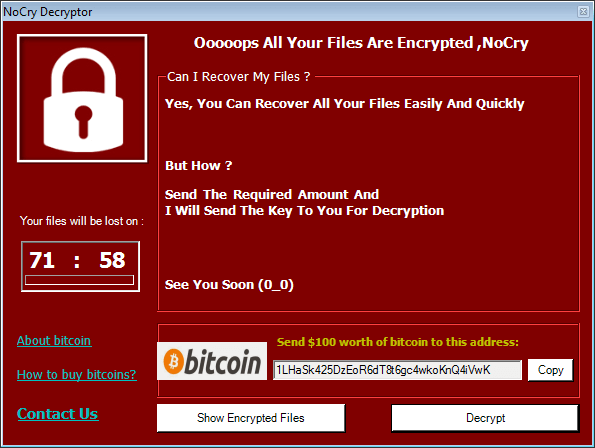
The appearance of Bitcoin and the evolution of encryption algorithms helped turn ransomware from a minor threat used in cyber vandalism, to a full-fledged money-making machine. Usually, threat actors request payment in Bitcoins because this cryptocurrency cannot be tracked by cybersecurity researchers or law enforcement agencies.
Top Targets for Ransomware
Cybercriminals soon realized that companies and organizations were far more profitable than users, so they went after the bigger targets: police departments, city councils, and even schools and hospitals. If the percentage of businesses that paid the ransom raised to 26% in 2020 and has increased to 32% in 2021, the $170,404 is the average value of the ransom paid this year. But for now, let’s find out what are the top targets for ransomware.
Public institutions
Public institutions, such as government agencies, manage huge databases of personal and confidential information that cybercriminals can sell, making them favorites among ransomware operators. Because the staff is not trained to spot and avoid cyberattacks and public institutions often use outdated software and equipment, means that their computer systems are packed with security holes just begging to be exploited.
Unfortunately, a successful infection has a big impact on conducting usual activities, causing huge disruptions. Under such circumstances, ransomware victims experience financial damage either by owning up to large ransomware payouts or by bearing the price of recovering from these attacks.
Businesses
In short, because that’s where the money is. Threat actors know that a successful infection can cause major business disruptions, which will increase their chances of getting paid. Since computer systems in companies are often complex and prone to vulnerabilities, they can easily be exploited through technical means. Additionally, the human factor is still a huge liability that can also be exploited through social engineering tactics. It is worth mentioning that ransomware can affect not only computers but also servers and cloud-based file-sharing systems, going deep into a business’s core.
Cybercriminals know that businesses would rather not report an infection for fear of legal consequences and brand damage.
Home users
Since they usually don’t have data backups, home users are the number one target for ransomware operators. They have little or no cybersecurity education at all, which means they’ll click on almost anything, making them prone to manipulation by cyber attackers. They also fail to invest in need-to-have cybersecurity solutions and don’t keep their software up to date (even if specialists always nag them to). Lastly, due to the sheer volume of Internet users that can become potential victims, more infected PCs mean more money for ransomware gangs.
Ransomware Examples
By now you know that there’s plenty of versions out there. With names such as CryptXXX, Troldesh, or Chimera, these strains sound like the stuff hacker movies are made of. So while newcomers may want to get a share of the cash, a handful of families have established their domination.
Conti Ransomware
Conti ransomware has become famous after targeting healthcare institutions. Its usual methods leverage phishing attacks to achieve remote access to a machine and further spread laterally onto the network, meanwhile performing credentials theft and unencrypted data gathering.
A famous attack was that on Ireland’s Health Service Executive (HSE) on the 14th of May 2021 when the gang requested $20 million not to release the exfiltrated data.
DarkSide Ransomware
DarkSide is a ransomware program that operates as a ransomware-as-a-service (RaaS) group. It began attacking organizations worldwide in August 2020 and, like other similar threats utilized in targeted cyberattacks, DarkSide not only encrypts the victim’s data but also exfiltrates it from the impacted servers.
In just 9 months of operations, at least $90 million in Bitcoin ransom payments were made to DarkSide, coming from 47 different wallets. The ransomware gang gained around $10 million from that profit attacking chemical distribution organization Brenntag, which paid a $4.4 million ransom, and Colonial Pipeline, which also paid $5 million in cryptocurrency.
It’s a good example of ransomware that uses double extortion as hackers normally ask for a ransom to return the data they exfiltrated, so the paying pressure is higher.
REvil Ransomware
REvil Ransomware aka Sodinokibi first spotted in April 2019 and working as a ransomware-as-a-service model, is famous for its attacks on JBS in June 2021 and Kaseya in July 2021.
Due to a Kaseya software vulnerability to SQL injection attacks, REvil Ransomware managed to encrypt Kaeya’s servers. This resulted in a supply chain attack as its customers were infected.
JBS, the biggest meatpacking enterprise worldwide, was hit by REvil on May 30, 2021, and had to pay an $11 million ransom to prevent hackers from leaking their data online.
Avaddon Ransomware
Avaddon Ransomware was distributed via phishing emails with malicious JAVA script files and is famous for its attack on the French enterprise AXA in May 2021. Its operators use normally data leak websites to publish there the information of the victims who do not pay the ransom.
QLocker Ransomware
As its name says, QLocker ransomware operates as a locker, compromising users’ storage devices. Therefore victims are locked out until they provide the password. Its targets are QNAP devices. The files in these network-attached storage devices are encrypted in a 7-zip archive format that requires a password.
Ryuk Ransomware
Ryuk is a ransomware-as-a-service (RaaS) group that’s been active since August 2018. It is widely known for running a private affiliate program in which affiliates can submit applications and resumes to apply for membership. In the last months of 2020, the gang’s affiliates were attacking approximately 20 companies every week, and, starting November 2020, they coordinated a massive wave of attacks on the US healthcare system.
WannaCry Ransomware
Even if this is not recent, of course, we cannot skip mentioning this famous one. On Friday, May 12, 2017, around 11 AM ET/3 PM GMT, a ransomware attack of “unprecedented level” (Europol) started spreading WannaCry around the world. It used a vulnerability in Windows that allowed it to infect victims’ PC’s without them taking any action. Until May 24, 2017, the infection has affected over 200,000 victims in 150 countries.
Ransomware Statistics
From 1989’s first ransomware distributed via floppy disks and with a ransom price of $189 to today’s million dollars ransom, here are some statistics that will help you further understand the threat of ransomware.
- The first half of 2021 recorded a doubling in ransomware attacks compared to 2020.
- Data exfiltration and data leakage were common practices that allowed double extortion.
- Conti, Avaddon, and REvil are the authors of 60% of the attacks.
- The U.S. registered 54.9 % of the victims, being a top target for ransomware attacks.
Top Ransomware Targets by Industry
#1. Government
According to SonicWall’s 2021 Cyber Threat Report, there have been far more hits on government customers than any other industry. By June, government customers “were getting hit with roughly 10 times more ransomware attempts than average”.
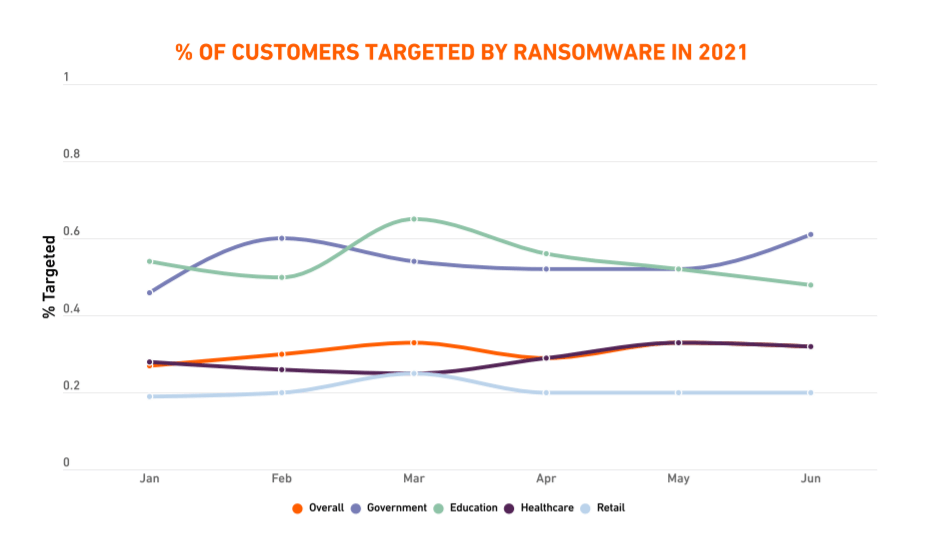
#2. Education
During the first half of 2021, the education field saw even more ransomware attempts than the government sector. In March, the FBI’s Cyber Division has issued a flash alert to warn of an increase in ransomware attacks targeting government entities, educational institutions, private companies, and the healthcare sector. A month later, the Conti ransomware gang encrypted the systems at Broward County Public Schools, threatening to release sensitive personal data of students and staff unless the district paid an enormous $40 million ransom.
#3. Healthcare
Healthcare organizations are the new favorite targets of ransomware attacks. Hospitals have become perennial targets of cyberattacks, including UC San Diego Health, Scripps Health, SalusCare, New Hampshire Hospital, and Atascadero State Hospital. As previously stated, healthcare providers lose an average of 7% of their customers after a data breach or ransomware attack, which is the highest when compared to other industries.
#4. Retail
Ransomware operators seem to often target retail enterprises because “they are rarely secured well and the benefits are easily monetized.” SonicWall security specialists discovered startling ransomware spikes across retail entities (264%). In July, the Coop Supermarket chain had to close 500 of its stores following the Kaseya ransomware attack.
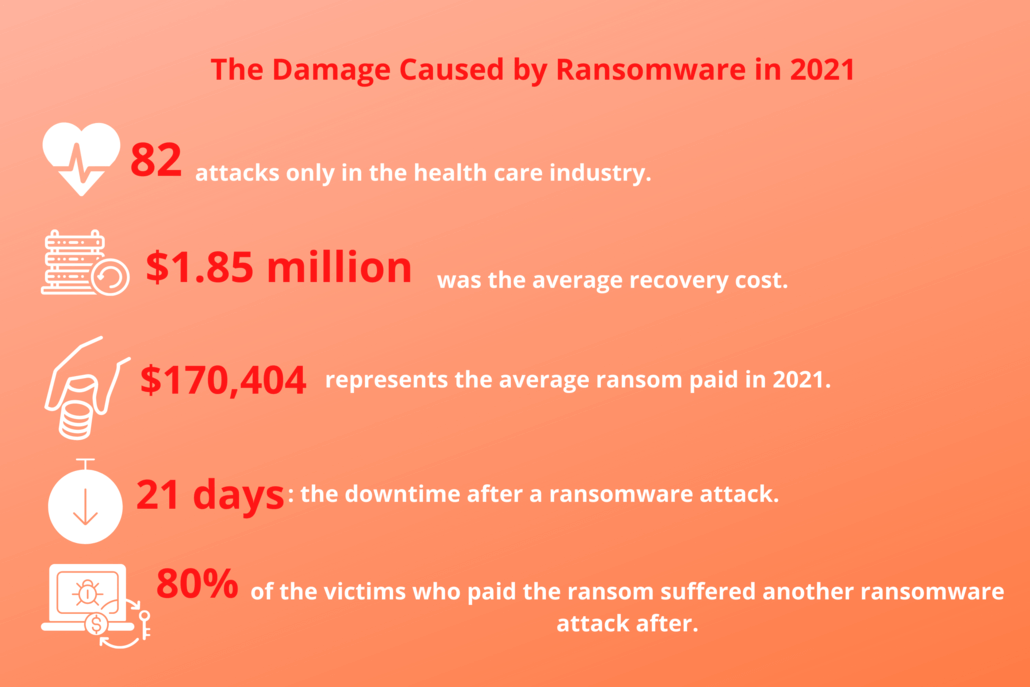
Image data sources: here and here.
Conclusion
Ransomware brought extortion to a global scale, and it’s up to all of us, users, business owners, and decision-makers, to disrupt it.
We now know that:
- creating malware or ransomware threats is now a business and it should be treated as such;
- the “lonely hacker in the basement” stereotype died a long time ago;
- the present threat landscape is dominated by well defined and well-funded groups that employ advanced technical tools and social engineering skills to access computer systems and networks;
- even more, cyber criminal groups are hired by large states to target not only financial objectives but political and strategic interests.
We also know that we’re not powerless and there’s a handful of simple things we can do to avoid ransomware. Cybercriminals have as much impact on your data and your security as you give them.
Check this article for more information on how to prevent ransomware.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Do you work for an NHS Trust? Heimdal is giving you free ransomware licenses to combat growing cyber attacks.
Get your free ransomware protection here.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










