Contents:
Ransomware could be considered the most prevalent threat in this cybersecurity landscape.
As hackers discover new ways to profit from ransomware assaults, the frequency of these attacks is increasing.
Hackers will plan their attacks with care and patience, and will strike when the conditions are appropriate as the ability to conduct effective reconnaissance could be critical to the success of any cybercrime operation.
One example of such diligence when it comes to the in-depth research used to target a potential victim is the DarkSide group.
What Is Darkside Ransomware?
DarkSide is a ransomware group that was first noticed in July 2020, targeting companies all around the world.
Darkside’s assaults indicate a thorough understanding of the victims’ architecture, security systems, and vulnerabilities. It’s worth noting that the ransomware operation has indicated that they prefer not to target hospitals, schools, non-profits, or governments, instead preferring to target major companies that can afford to pay hefty ransoms.
Darkside group is operating under the form of a Ransomware-as-a-Service (RaaS). In this way the gains are shared between its holders and partners, or affiliates, who allow entry to companies and execute the ransomware. The DarkSide ransomware gang gets around 25% of a ransom payment, and the rest is taken by the affiliate who organized the assault.
How Does DarkSide Ransomware Work?
The gang conducts reconnaissance and takes precise efforts to guarantee that its attack tools and tactics will not be detected on monitored devices and endpoints.
Initial Access
Usually, Darkside ransomware gains initial entry through weak links as remotely exploitable accounts and systems.
They are able to access the Virtual Desktop Infrastructure (VDI) that had been put in place to facilitate remote access during the pandemic.
Command and Control
Darkside ransomware attackers establish command and control by utilizing an RDP client operating on port 443, which is routed over TOR.
It’s worth noting that once the Tor browser is installed, its settings are changed to operate as a permanent service, routing traffic delivered to a local (dynamic) port via TOR over HTTPS over port 443.
Cobalt Strike was used as a backup command and control system by deploying stagers (named file.exe) remotely on certain targeted computers through WinRM, each with a unique configuration. Cobalt Strike stagers linked to a specific C2 server to obtain the Cobalt Strike Beacon.
Reconnaissance and Credential Harvesting
Darkside ransomware is notorious for its ability to live off the land (LOtL), but it can also scan networks, conduct commands, dump processes, and steal passwords.
Data Collection and Staging
The active Windows server also acted as a hub for data storage prior to exfiltration. Data was mined from hundreds of servers using a batch program (dump.bat) in the Desktop folder. Dumping files to the same directory and compressing them into 7zip archives using the naming scheme *.7z.[001]-[999].
Encryption
Darkside does not launch ransomware until they have mapped the environment, extracted valuable data, taken control of privileged accounts, and discovered all backup systems, servers, and apps. Several connections to primary backup repositories were identified using compromised service accounts soon before encryption. By postponing the encryption phase of the assault, they position themselves to maximum harm and profit.
The ransomware code is distributed using well-known backdoors (TOR-RDP or Cobalt Strike) and is tailored to each victim. The payload contains the executable, a one-of-a-kind extension, and a one-of-a-kind victim ID that allows the victim to enter Darkside’s website and make a payment.
The malware avoids signature-based detection systems by employing distinct executables and extensions. Darkside also sells customized ransomware to other threat actors (Ransomware as a Service) and profits from successful attacks.
Exploited Vulnerabilities
CVE-2019-5544
If a malicious actor gains network access to port 427 on an ESXi host or on any Horizon DaaS management appliance, the malicious actor may be able to rewrite the heap of the OpenSLP service, resulting in the execution of remote code.
CVE-2020-3992
It is possible for a malicious actor living on the management network and having access to port 427 on an ESXi system to trigger a use-after-free in the OpenSLP service, which might result in remote code execution.
How to Prevent Darkside Ransomware?
DarkSide ransomware is a very dangerous malware created to encrypt files such as photos, audios, videos, documents, etc, and make them impossible to access.
Following the encryption process, it spreads the ransom note in every folder of your device that claims the decryption is possible only when you use its data recovery service.
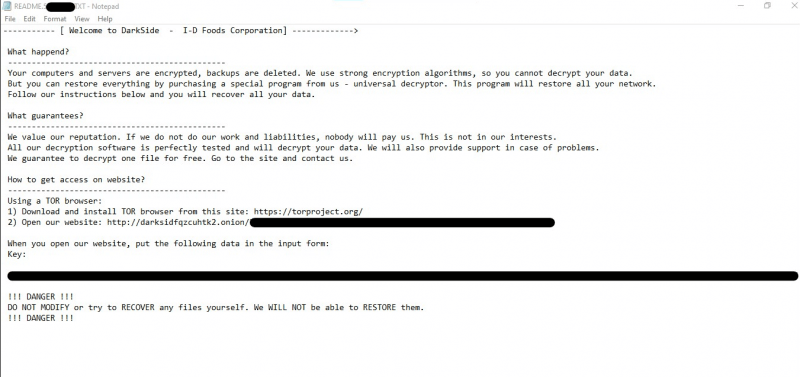
This is the moment when you need to remove DarkSide ransomware and all the linked components from PCs immediately and then execute data recovery actions. Some ransomware prevention methods that might be helpful are listed below:
- Require multi-factor authentication for remote access to operational and information technology networks.
- Enable powerful spam filters to keep phishing emails out of the hands of end-users. Keep executable-file-containing emails from reaching end users.
- Implement a spearphishing user training program and simulated assaults to dissuade users from accessing dangerous websites or opening harmful attachments, as well as to reinforce acceptable user responses to spearphishing emails.
- Filter network traffic to prevent communications with known malicious IP addresses from entering or leaving the network. Implement URL blocklists and/or allowlists to prevent users from visiting harmful websites.
- Ensure that software, such as operating systems, applications, and firmware, on IT network assets, is updated on a regular basis. Consider implementing a centralized patch management system; using a risk-based assessment technique to identify which OT network assets and zones should be included in the patch management program.
- Restriction of network access to resources, particularly RDP. If RDP is found operationally required after risk assessment, limit the originating sources and demand multi-factor authentication.
- Configure antivirus/antimalware software to do frequent scans of IT network assets with up-to-date signatures. To define how OT network assets are discovered and analyzed for the existence of malware, use a risk-based asset inventory technique.
If an organization is impacted by a ransomware incident, CISA and FBI recommend powering off and segregating (i.e., remove from the network) the infected computer(s), removing the infected system from all networks, and disabling the computer’s wireless, Bluetooth, and other potential networking capabilities.
Most Important Attacks
Colonial Pipeline
Colonial Pipeline is the largest fuel pipeline operator in the U.S. that carries refined gasoline and jet fuel all the way from Texas to New York.
Back in 2021, the company was forced to shut down after being hit by ransomware in a clear demonstration of the vulnerability of energy infrastructure to this type of cyberattacks.
After learning it was “the victim of a cybersecurity attack,” the pipeline operator took some systems offline, temporarily halting pipeline operations and several IT systems. It also contacted an outside cybersecurity firm to investigate.
The company released an official statement saying that in an effort to contain the breach, it had to shut down its 5,500 miles of pipeline, which carries 45% of the East Coast’s fuel supplies.
On May 7, Colonial Pipeline Company learned it was the victim of a cybersecurity attack and has since determined that the incident involved ransomware. Quickly after learning of the attack, Colonial proactively took certain systems offline to contain the threat. These actions temporarily halted all pipeline operations and affected some of our IT systems, which we are actively in the process of restoring.
Since pipelines play a central role in so many parts of the U.S. economy, they are a specific concern.
Toshiba
Toshiba is a Japanese multinational conglomerate that provides products and services such as power, industrial and social infrastructure systems, elevators and escalators, printers, as well as IT solutions.
According to the organization, the ransomware attack was limited to part of Europe and only a small amount of work data had been lost, hackers not being able to get access to customer information.
Following the cyberattack, the company closed down networks between Europe, Japan, and branches in order to avert the damage escalating as they were implementing recovery protocols and data backups.
According to the Japanese company, an inquiry has been launched in order to analyze the damage that has been done and a third-party cyber forensics specialist has been pulled in to help.
We have not yet confirmed that customer-related information was leaked externally.
Nevertheless, Toshiba Corporation is aware of the fact that it might be possible that at least some private information may have been exposed.
Brenntag SE
German chemical distribution companies operating in more than 77 countries around the world, suffered a DarkSide Ransomware attack that led to the organization paying a $4.4 million ransom in Bitcoin.
Following the ransom payment, Brenntag obtained a decryptor for encrypted files and successfully stopped the cybercriminals from making the company’s stolen information public.
DarkSide Ransomware operates under the form of a Ransomware-as-a-Service (RaaS), in which the gains are shared between its holders and partners, or affiliates, who allow entry to companies and execute the ransomware. The DarkSide ransomware gang gets around 25% of a ransom payment, and the rest is taken by the affiliate who organized the assault.
Usually, in a ransomware negotiation, the affiliate has to reveal how they acquired access to the victim’s data. This can be done in the form of a multi-page security audit report or just a paragraph in the Tor chat screen describing how they obtained access.
In Brenntag’s case, the DarkSide affiliate said they have obtained access to the network after purchasing stolen information, but didn’t know how the credentials were obtained, to begin with.
Wrapping Up
Prevention is still the best medicine for ransomware. With patented DNS security technology that detects and blocks attacks at the DNS, HTTP, and HTTPs levels, Heimdal™ Threat Prevention protects your endpoints and network from ransomware and data exfiltration. Ransomware operators will be defeated when combined with Heimdal’s Ransomware Encryption Protection.
Heimdal™ Ransomware Encryption Protection
Heimdal’s Ransomware Encryption Protection module is a revolutionary, 100% signature-free component. A novel and proactive approach, it benefits from market-leading detection and remediation that combats any type of ransomware, be it file-based or fileless.
*This article was initially drafted by Antonia Din in May 2021 and updated by Dora Tudor in January 2022.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











