Contents:
As ransomware attacks have gained ground recently, researchers decided to start making out a list of vulnerabilities abused by ransomware groups that is easy-to-follow in order for organizations to be aware of which security flaws ransomware gangs exploited or exploit in order to gain initial access when breaching a network.
The initiative came into existence at Allan Liska’s urge. He is a Recorded Future’s CSIRT member and announced his idea over the weekend on Twitter.
Lots of contributors have started to support Allan Liska in his initiative and the detailed in-progress list now includes vulnerabilities exploited in the past or that are still at the present moment targeted.
The list follows a diagram pattern with a concise mentioning of different vulnerabilities.
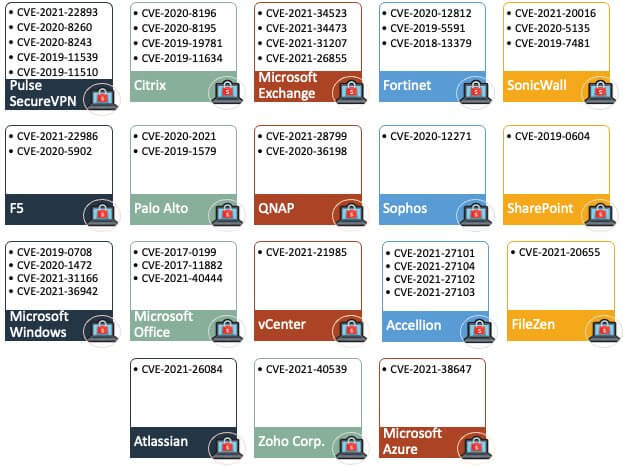
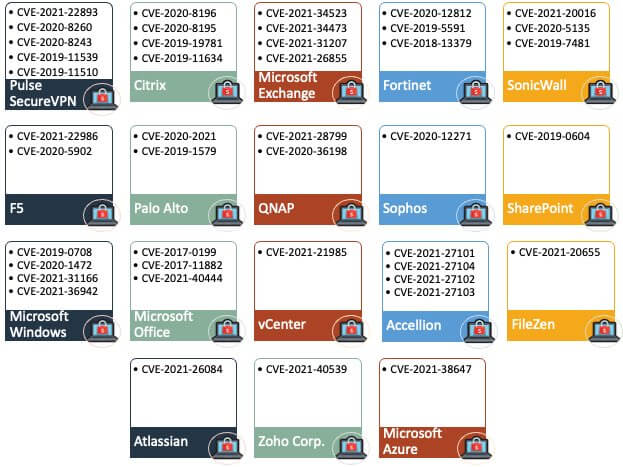
Short Overview of the Security Vulnerabilities Exploited by Ransomware Groups
Actively exploited vulnerabilities have become a trend in 2021. According to BleepingComputer, here are the most exploited security flaws:
CVE-2021-40444
This is a Windows MSHTML flaw that has been recently patched. However, last week it was exploited by ransomware-as-a-service affiliates through RCE exploits.
CVE-2021-34473, CVE-2021-34523, CVE-2021-31207
These are associated with Conti ransomware, which made use of the above-mentioned ProxyShell exploits at the beginning of September to attack Microsoft Exchange servers.
CVE-2021-36942
Through this, LockFile took over Windows domains by using the PetitPotam NTLM relay attack method.
CVE-2021-34527
The so-known PrintNightmare was exploited eventually by Magniber ransomware too.
CVE-2021-28799
The security flaw in QNAP and Synology NAS devices made way for eCh0raix ransomware.
This vulnerability was also exploited by the popular Qlocker ransomware.
CVE-2019-7481
This is the vulnerability found in SonicWall devices and exploited by HelloKitty ransomware during the month of July.
CVE-2021-30116, CVE-2021-30119, and CVE-2021-30120
These are the vulnerabilities that let Kaseya’s network to be breached by Revil Ransomware.
CVE-2021-20016
It was a vulnerability in SonicWall that received its patch back in Feb. 2021 but has not escaped being targeted by FiveHands ransomware.
CVE-2018-13379
Fortinet VPN devices were encrypted in April by Cring ransomware targeting the above-mentioned unpatched vulnerability. This followed the FBI and CISA’s warning of Fortinet devices being scanned by cybercriminals to find the vulnerable ones.
CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065
Systems that were unpatched against ProxyLogon vulnerabilities were the target of Black Kingdom ransomware and DearCry ransomware back in March, affecting Microsoft Exchange servers.
CVE-2021-27101, CVE-2021-27102, CVE-2021-27103, CVE-2021-27104
The vulnerabilities that allowed the attack started in the middle of December 2020 and were carried out to January 2021, when Clop ransomware affected Accellion servers.
The Fight Against the Threat of Ransomware
Ransomware has become a real and ceaseless threat nowadays and organizations have started to act against it.
This way, Joint Cyber Defense Collaborative (JCDC) emerged. This is a partnership between several names like, for instance, CISA, Microsoft, Amazon Web Services, Lumen, Google Cloud, AT&T, FireEye Mandiant, Verizon, and Palo Alto Networks. It’s a project whose goal is to mitigate ransomware by defending the US critical infrastructure.
The key to preventing and solving an issue is determining its cause. This is what the June ransomware self-assessment security audit tool released by CISA lets enterprises do. Through this tool, organizations can evaluate their level of risks when it comes to ransomware and find out if they are really prepared to recover if attacked. The same federal agency makes available the Ransomware Response Checklist that helps firms part of the second scenario described before with advice and ransomware-related information.
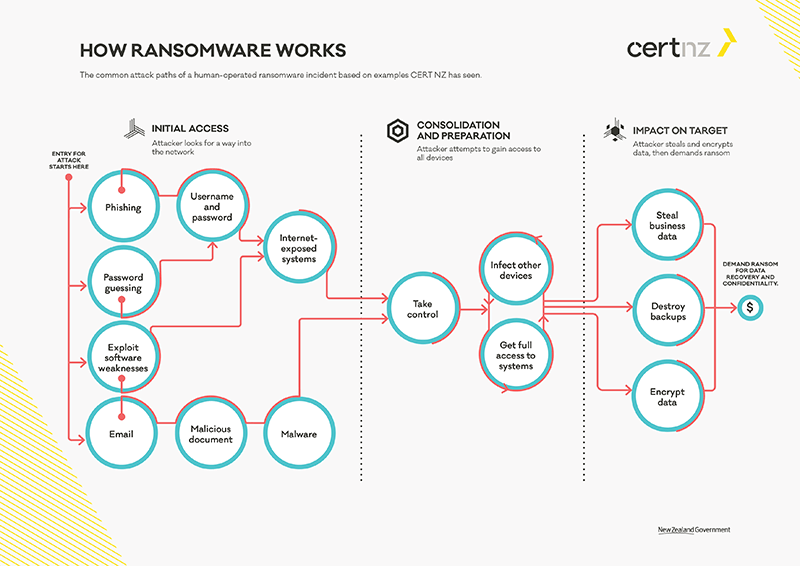
A ransomware protection guide comes also from CERT NZ (The New Zealand Computer Emergency Response Team). Below is an illustration of this guide.

Heimdal® Patch & Asset Management
- Create policies that meet your exact needs;
- Full compliance and CVE/CVSS audit trail;
- Gain extensive vulnerability intelligence;
- And much more than we can fit in here...


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










