Contents:
Microsoft recently released a security update to fix the PrintNightmare zero-day vulnerabilities that allowed attackers to gain administrative privileges on Windows devices.
A zero-day Windows print spooler vulnerability called PrintNightmare (CVE-2021-34527) was accidentally disclosed.
This flaw makes use of the Windows Point and Print functionality in order to allow remote code execution and the acquisition of local SYSTEM privileges.
Regardless of the fact that Microsoft published two security patches to address different PrintNightmare flaws, another vulnerability publicly disclosed by security researcher Benjamin Delpy still enabled threat actors to swiftly obtain SYSTEM access by connecting to a remote print server.
The vulnerability discovered by Delpy was able to abuse the CopyFiles directive in order to copy and execute malicious DLL using SYSTEM privileges when a user installed a remote printer.
Once the DLL was launched by the exploit, a console Window where all commands are executed with SYSTEM privileges would be opened.
Unfortunately, ransomware gangs, like Vice Society, Magniber, and Conti, started to use the bug in order to gain privileges on the compromised devices.
This PrintNightmare vulnerability is tracked as CVE-2021-36958 and was attributed to Victor Mata from FusionX, Accenture Security. The researcher privately disclosed the bug to Microsoft back in December of last year.
PrintNightmare Vulnerability Fixed
In the most recent Patch Tuesday update, Microsoft released a security update for the CVE-2021-36958. The update deals with the remaining PrintNightmare vulnerability.
The journalists at BleepingComputer got in touch with Delpy, who tested his exploit against the new security update as he confirmed that the bug is now fixed.
Apparently, in addition to fixing the vulnerability, Delpy also noticed the fact that Microsoft disabled the CopyFiles feature by default and added an undocumented group policy that allows admins to enable it again.
This policy can be configured in the Windows Registry under:
HKLM\Software\Policies\Microsoft\Windows NT\Printers key and by adding a value named CopyFilesPolicy. When set to ‘1’, CopyFiles will be enabled again.
It’s worth noting that even when enabled it would only allow Microsoft’s C:\Windows\System32\mscms.dll file to be used with this feature.
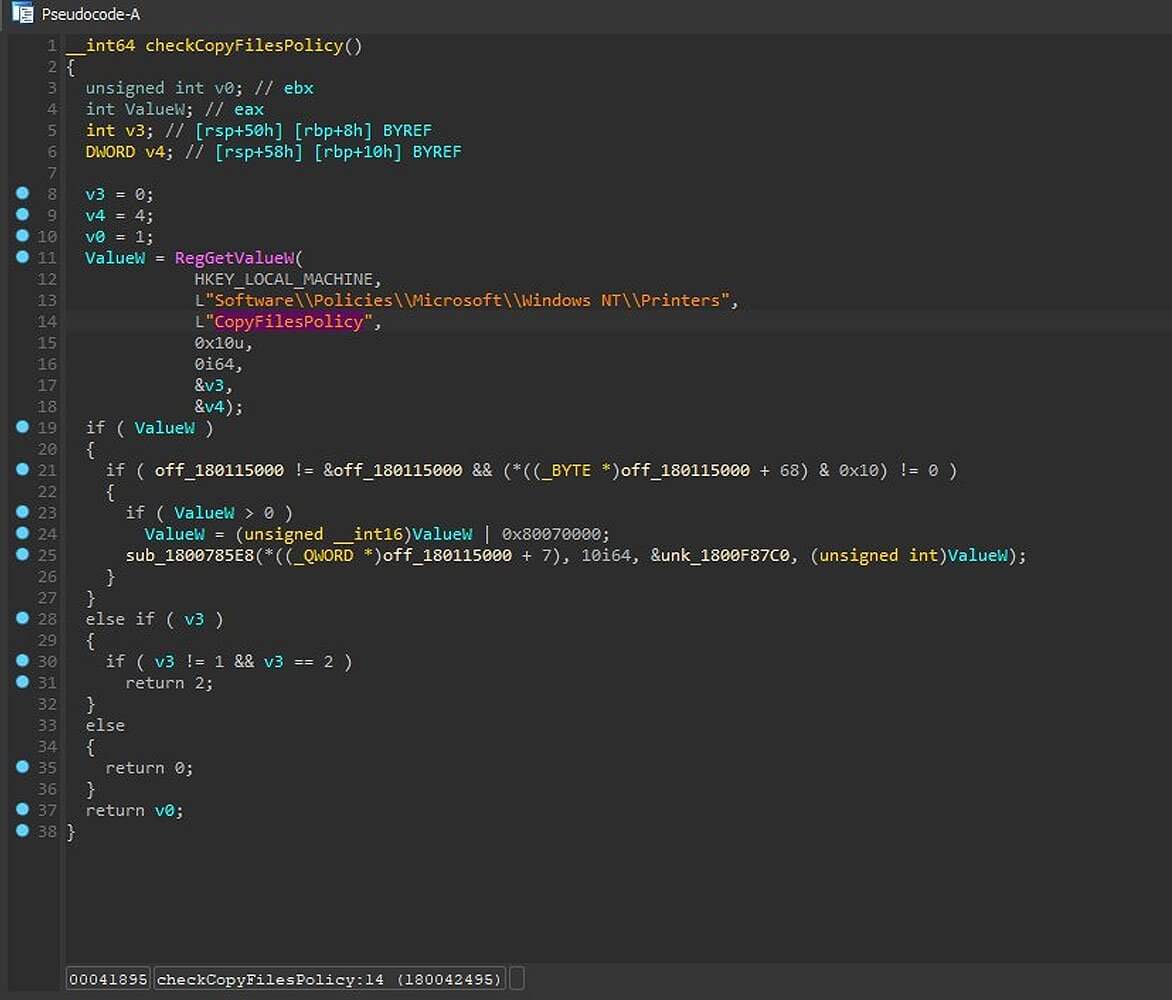
Because this modification affects the default behavior of Windows, it’s unknown what issues it will cause when printing in the future.
At this time, Microsoft has not provided any information about this new group policy, as it is not accessible through the Group Policy Editor.
In addition to the PrintNightmare bug, today’s patches also address a widely exploited Windows MSHTML zero-day flaw.
Both of these vulnerabilities have been known to be used by threat actors in attacks, therefore installing today’s security patches as soon as possible is critical.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










