Contents:
The PrintNightmare saga goes on, but now in a different way. The well-known class of bugs has become a target currently in the hands of threat actors specialized in ransomware attacks. Hackers have started to abuse PrintNightmare vulnerabilities in order to breach Windows servers. Their goal is to distribute Magniber ransomware.
Magniber Ransomware: the Malware That Takes Advantage of PrintNightmare
Crowdstrike researcher’s investigation has brought to light that PrintNightmare class of vulnerabilities is now exploited by the Magniber ransomware group. The cyberattacks point to South Korean victims.
There were reported 600 entries on the ID Ransomware platform, this proving that Magniber ransomware has increased its malicious activity during the last month.
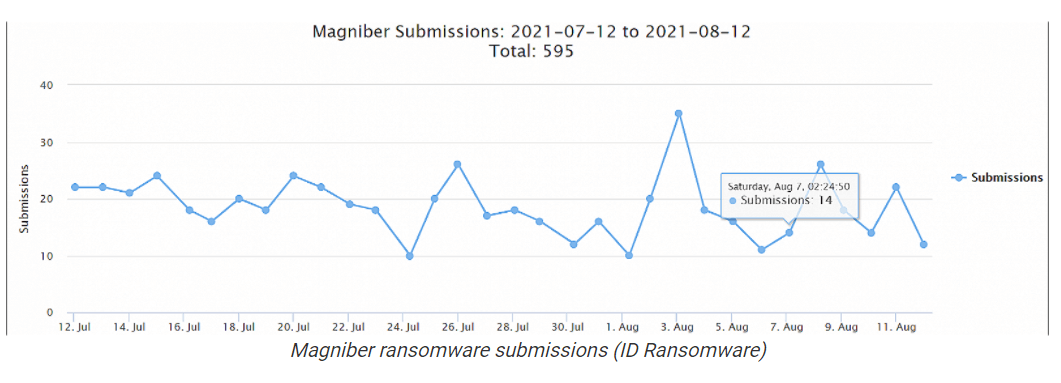
Here is how it works:
- Hackers choose servers that are not patched against PrintNightmare.
- An obfuscated DLL loader is then dropped by Magniber.
- The malware’s first step is to emerge itself into a process.
- Then, on the compromised machine, it is later deployed.
- This way local file traversal and encryption can be achieved.
What Is PrintNightmare?
PrintNightmare stands for a class or a group of bugs that have been detected in Windows Print Spooler. It usually affects the Windows Point and Print capability and also print drivers: CVE-2021-1675, CVE-2021-34527, and CVE-2021-36958. Microsoft has addressed this threat over time, the latest update being a security advisory that provides mitigation measures against CVE-2021-36958 until security patches are released for this specific vulnerability.
Patches for CVE-2021-1675 and CVE-2021-34527 were provided in June, respectively in July and August. We also wrote about them in our previous articles.
The main danger of PrintNightmare is that it lets hackers perform 2 major malicious activities: remote code execution when they pretend to be the sysadmins when logging into Windows domains and also the abuse of local privilege escalation.
Magniber: Some Background
According to the same researchers, the first sign of Magniber ransomware’s existence was reported back in 2017. He came into sight after Cerber ransomware, being his successor. At that time, it was making use of the Magnitude Exploit Kit (EK) in the malvertising campaigns and having as victims people from South Korea. Then, in the middle of 2018, it was observed that the malware expanded to target other regions too, focusing on other countries and areas from Asia, for example, China, Taiwan, Hong Kong, Singapore, or Malaysia.
More recent investigations from February 2021 showed that Magniber ransomware targeted devices from South Korea that use the Internet Explorer browser. It was delivered in the same way: through Magnitude EK and its targets were machines that were not secured against the new CVE-2020-0968 bug.
Magniber Ransomware Sets a Precedent
According to the BleepingComputer publication, there is no proof at the moment that other cybercriminals are following the Mangniber Ransomware group’s path, the latter being the only one known as exploiting PrintNightmare vulnerabilities currently. But this will not remain without a precedent, since the door is left open now.
CrowdStrike estimates that the PrintNightmare vulnerability coupled with the deployment of ransomware will likely continue to be exploited by other threat actors.
The mitigation measures that hang together, for now, are the usual ones: to closely follow the release of the security patches and right off apply them and also to implement the mitigation measure Microsoft has provided until now. Disabling Print Spooler is the most recommended mitigation measure against PrintNightmare bugs.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










