Contents:
According to cybersecurity researchers, the Conti ransomware threat actor has been used recently disclosed ProxyShell vulnerability exploits to hack into Microsoft Exchange servers and compromise corporate networks.
ProxyShell is an exploit of vulnerabilities in Microsoft Exchange that have been the subject of multiple critical updates over the past several months. The three Microsoft Exchange vulnerabilities used by the exploit are CVE-2021-34473, CVE-2021-34523, CVE-2021-31207.
ProxyShell is an attack chain that can be used to execute arbitrary commands remotely on unpatched Exchange Servers without requiring authentication.
Microsoft issued fixes to mitigate the vulnerabilities in April and May 2021, but technical details on how to take advantage of them were recently published, enabling hackers to begin using them in cyberattacks.
Up to this point, cybercriminals have used ProxyShell flaws to deliver web shells, backdoors, and the LockFile ransomware.
ProxyShell Used By Conti Ransomware Gang to Breach Networks
Security firm Sophos noticed that Conti affiliates seem to have accelerated their attacks considerably, deploying ransomware in just a few hours instead of weeks or months.
Sophos was involved in an incident response case last week in which the Conti ransomware threat actor encrypted a customer. Sophos specialists analyzed the incident and saw that at first, the hackers compromised the network employing the Microsoft Exchange ProxyShell vulnerabilities that were recently disclosed.
In this case, minutes after installing a first web shell, a second one was installed. Within half an hour, the Conti threat actors had compiled a comprehensive list of all network computers, domain controllers, and domain administrators.
After 4 hours, the cybercriminals had gained domain administrator accounts credentials and started carrying out commands.
Within 48 hours of acquiring access, the cybercriminals had stolen about 1 terabyte of unencrypted data and uploaded it to the MEGA file sharing server. Within five days, they deployed the Conti ransomware to every machine on the network, specifically targeting individual network shares on each computer.
During the attack seven back doors have been installed on the network:
- two web shells (used for initial access);
- Cobalt Strike (used for the remainder of the attack);
- four commercial remote access tools (AnyDesk, Atera, Splashtop, and Remote Utilities).
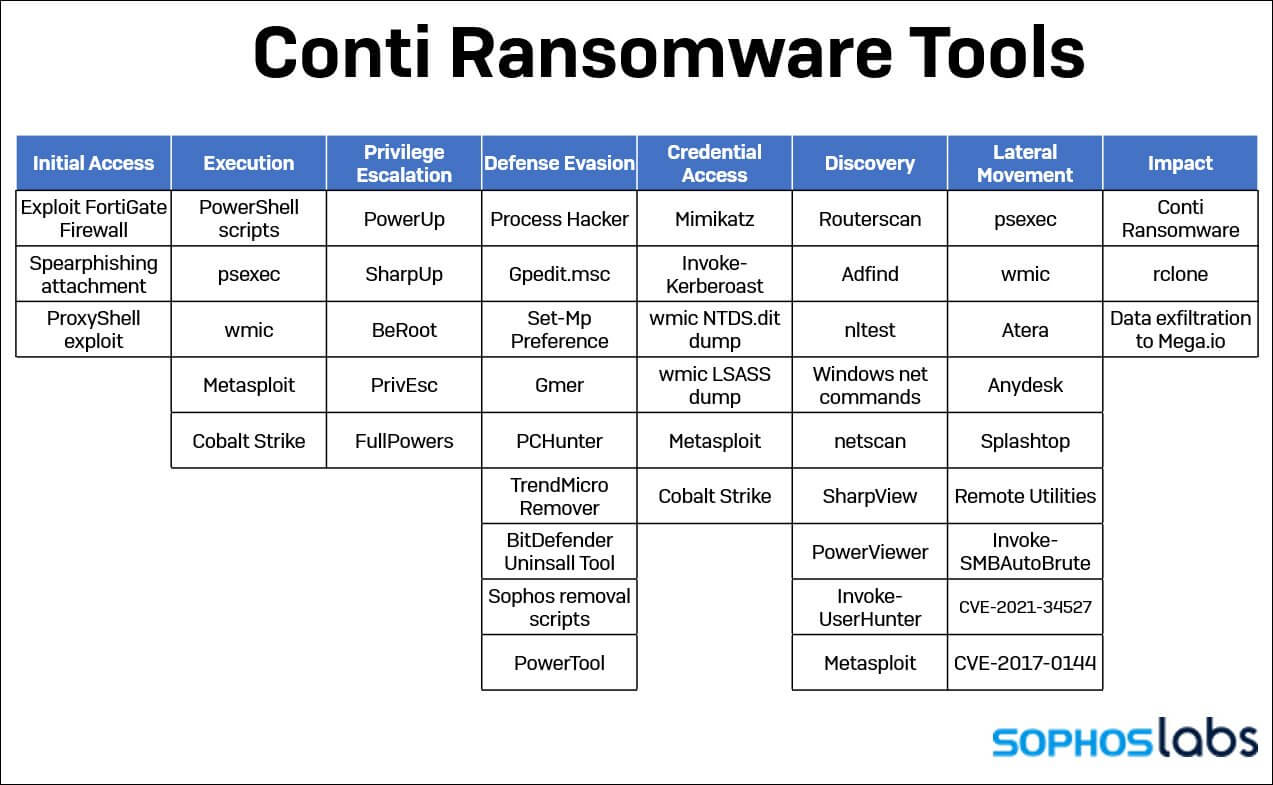
ProxyShell and other attacks on known Microsoft Exchange vulnerabilities pose a significant risk. Companies that use on-premises Exchange Server should update and patch their servers as quickly as possible.
Furthermore, these kinds of attacks highlight the importance of enabling malware protection on both servers and endpoints.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










