Contents:
Following the invasion of Ukraine, a member of the Conti ransomware group believed to be of Ukrainian origin, leaked the gang’s internal communications after the group’s leaders posted an aggressive pro-Russian message on their official website on Friday, in the aftermath of the Russian invasion of the country.
Internal records were disclosed via an email that was provided to a number of journalists and security experts, among other people.
What Is Happening?
Conti continues to suffer terrible blows thanks to the efforts of a Ukrainian researcher, who has leaked further internal chats, as well as the source of their ransomware, administration panels, and other information.
A Ukrainian researcher going by the name of “ContiLeaks” published 393 JSON files that included over 60,000 internal conversations seized from the Conti and Ryuk ransomware gang’s secret, encrypted XMPP chat server.
The conversations took place between January 21st, 2021, and February 27th, 2022, and they provided an invaluable amount of on-the-spot information on the cybercrime organization, including bitcoin addresses, how the organization is organized as a business, evading law enforcement, how they conduct their attacks, and much more.
The researcher continued to reveal more devastating Conti material, including an additional 148 JSON files with 107,000 internal communications since June 2020.
Following that, ContiLeaks continued publishing further information, including the gang’s administration panel source code as well as the BazarBackdoor API, images of storage servers, and other materials.
https://t.co/fndSSAY9Bs – conti source without locker src.
— conti leaks (@ContiLeaks) March 1, 2022
However, one aspect of the release that drew attention was a password-protected ZIP containing the source code for the Conti ransomware encryptor, decryptor, and constructor, all of which could be downloaded for free.
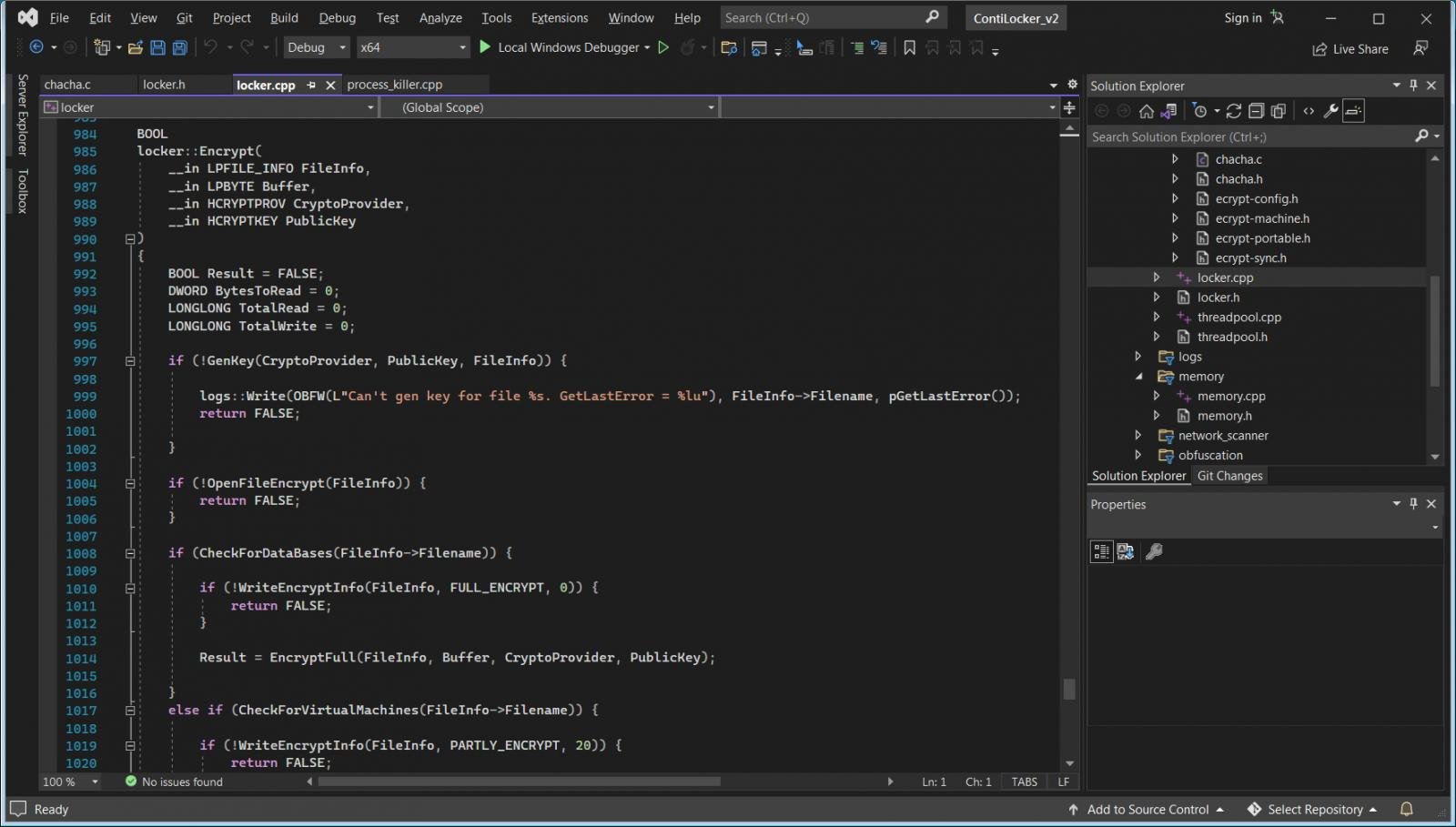
As BleepingComputer reports, despite the fact that the leaker did not disclose the password, another researcher was able to break it within minutes, giving everyone access to the source code for the Conti ransomware malware files.
The Hidden Dangers of This Leak
While making this code available to the public is beneficial for security research, some threat actors could as well use it to establish their own criminal operations based on it in the future.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security