Contents:
Conti Ransomware operation is known as a ransomware-as-a-service (RaaS).
As thoroughly explained by Vladimir, Ransomware-as-a-Service is an illicit ‘parent-affiliate(s)’ business infrastructure, in which operators give tools to affiliates with the goal of carrying out ransomware attacks.
A security researcher recently shared a forum post that was created by an angry Conti affiliate.
In the forum post, the affiliate publicly leaked important information about Conti’s ransomware operation, like IP addresses of Cobalt Strike C2 servers and a 113 MB archive that contains numerous tools and training materials for conducting ransomware attacks.
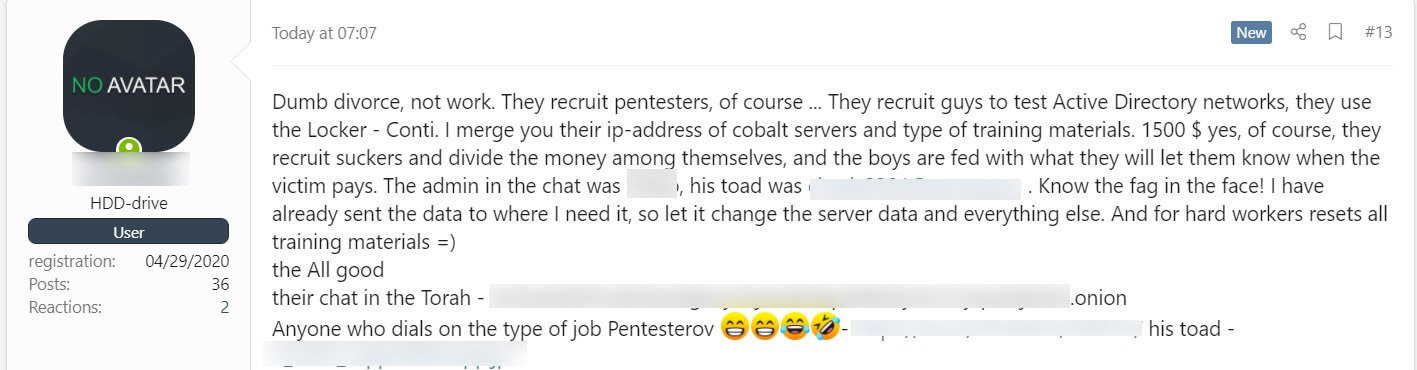
The materials were posted as the affiliate was seeking revenge after he only was paid $1,500 as part of an attack.
I merge you their IP-address of cobalt servers and type of training materials. 1500 $ yes, of course, they recruit suckers and divide the money among themselves, and the boys are fed with what they will let them know when the victim pays.
Security researcher Pancak3 advises that everyone should block the leaked IP addresses in order to prevent attacks from the group.
? go block these ?
162.244.80.235
85.93.88.165
185.141.63.120
82.118.21.1— pancak3 (@pancak3lullz) August 5, 2021
The data leak did not stop here, as the affiliate continued to share information online. The affiliate leaked also an archive containing 111 MB of files, that included hacking tools, manuals written in Russian, training material, and help documents allegedly given to affiliates when performing Conti ransomware attacks.
Vitali Kremez had analyzed the archive as well and declared for BleepingComputer that the training material is a match for any Conti active cases.
We can confirm based on our active cases. This playbook matches the active cases for Conti as we see right now.
By and large, it is the holy grail of the pentester operation behind the Conti ransomware “pentester” team from A-Z. The implications are huge and allow new pentester ransomware operators to level up their pentester skills for ransomware step by step.
The leak also shows the maturity of their ransomware organization and how sophisticated, meticulous and experienced they are while targeting corporations worldwide.
It also provides a plethora detection opportunity including the group focus on AnyDesk persistence and Atera security software agent persistence to survive detections.
Ransomware-as-a-Service Operations Are Becoming Vulnerable
This shows that ransomware-as-a-service operations are exposed to vulnerabilities as well, as the existence of a single unhappy affiliate could lead to the exposure of carefully cultivated information and resources used in attacks.
It’s important to understand the security landscape in which this leak took place, as recently the United States government said that its Rewards for Justice program is accepting tips on foreign malicious cyberactivity against U.S. critical infrastructure.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










