Contents:
The imagination of cyber criminals seems to be unlimited when it comes to developing new methods to obtain what they want from their victims. We often hear about new ransomware strains that make victims every other week all across the globe – and they are all getting more and more dangerous. One such ransomware strain is Avaddon ransomware. Let’s find out more about how it works and what you can do to prevent an infection!
What is Avaddon Ransomware
In the cybersecurity landscape, we’ve first learned about the Avaddon ransomware in 2019; it has been offered with a Ransomware-as-a-Service model since June 2020, where ransomware fees for affiliates were negotiable.
Similar to how other ransomware groups proceeded, the Avaddon ransomware operators used a double extortion technique. They had a data leak site where they could expose the data of those who do not pay the ransom. Another significant aspect of Avaddon ransomware is that, apart from exposing the encrypted data, its operators also threaten to carry out DDoS attacks.
After a free decryptor was developed in February 2021 and made publicly available, the ransomware’s creators updated their code to make sure they still succeed with their criminal activities.
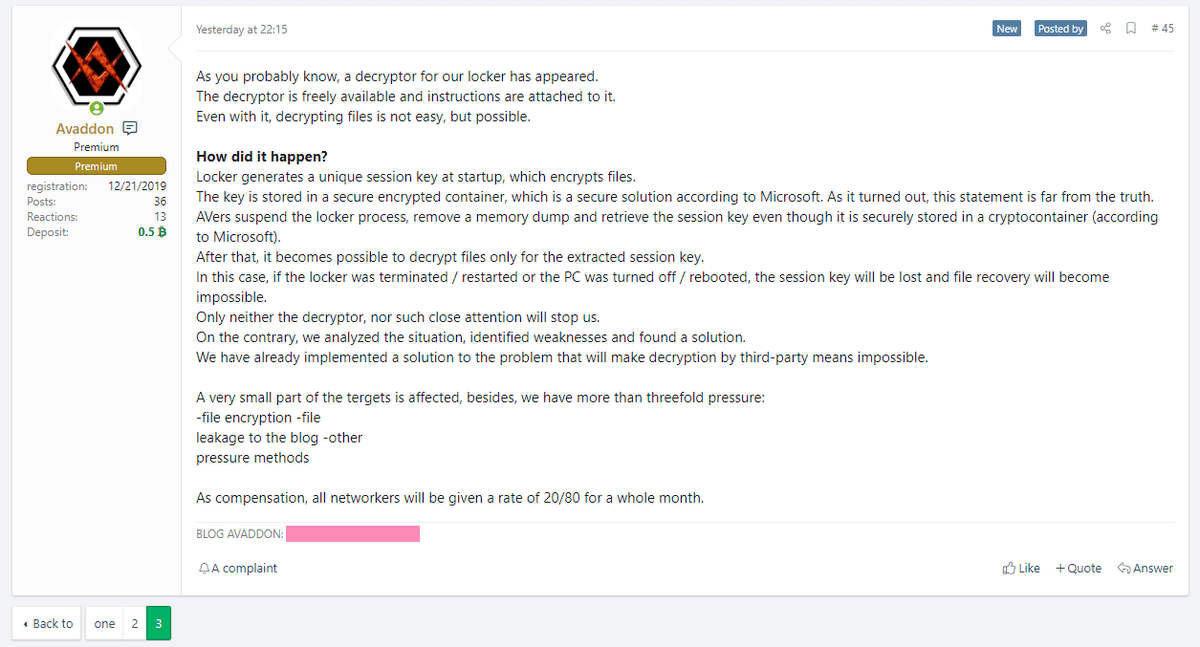
In June 2021 the ransomware group sent to Bleeping Computer a ZIP file with the decryption keys for all victims affected. It seems that the Avaddon group is shutting down its operation.
How Avaddon ransomware works
Avaddon is spread via phishing and malicious spam campaigns that deliver malicious JavaScript files, the ACSC says.
“These are often low in sophistication, containing a threat suggesting the attached file contains a compromising photo of the victim,” the Australian agency says. “‘Double extortion’ techniques are used, such as coercion and further pressure to pay a ransom, including threatening to publish the victim’s data … and threatening the use of DDoS attacks against the victims.”
Written in C++, Avaddon encrypts data using a unique AES256 encryption key, the agency reports. During the infection process, Avaddon checks the operating system language and keyboard layouts. If a potential victim’s operating system language is set to specific languages normally used in the Commonwealth of Independent States – formerly part of the Soviet Union – the malware ceases operation without harming the system.
In addition, the operators behind Avaddon apply the GetUserDefaultLCID() function to identify the default geolocation and system language of the user’s device to determine whether the user will be targeted for attack. This technique has also been observed in ransomware campaigns using the MedusaLocker variant, ACSC states.
BankInfoSecurity also adds:
“After Avaddon actors gain access to a victim’s network, they map the network and identify backups for deletion and/or encryption,” the FBI says. “The malware escalates privileges, contains anti-analysis protection code, enables persistence on a victim system and verifies the victim is not located in the Commonwealth of Independent States.”
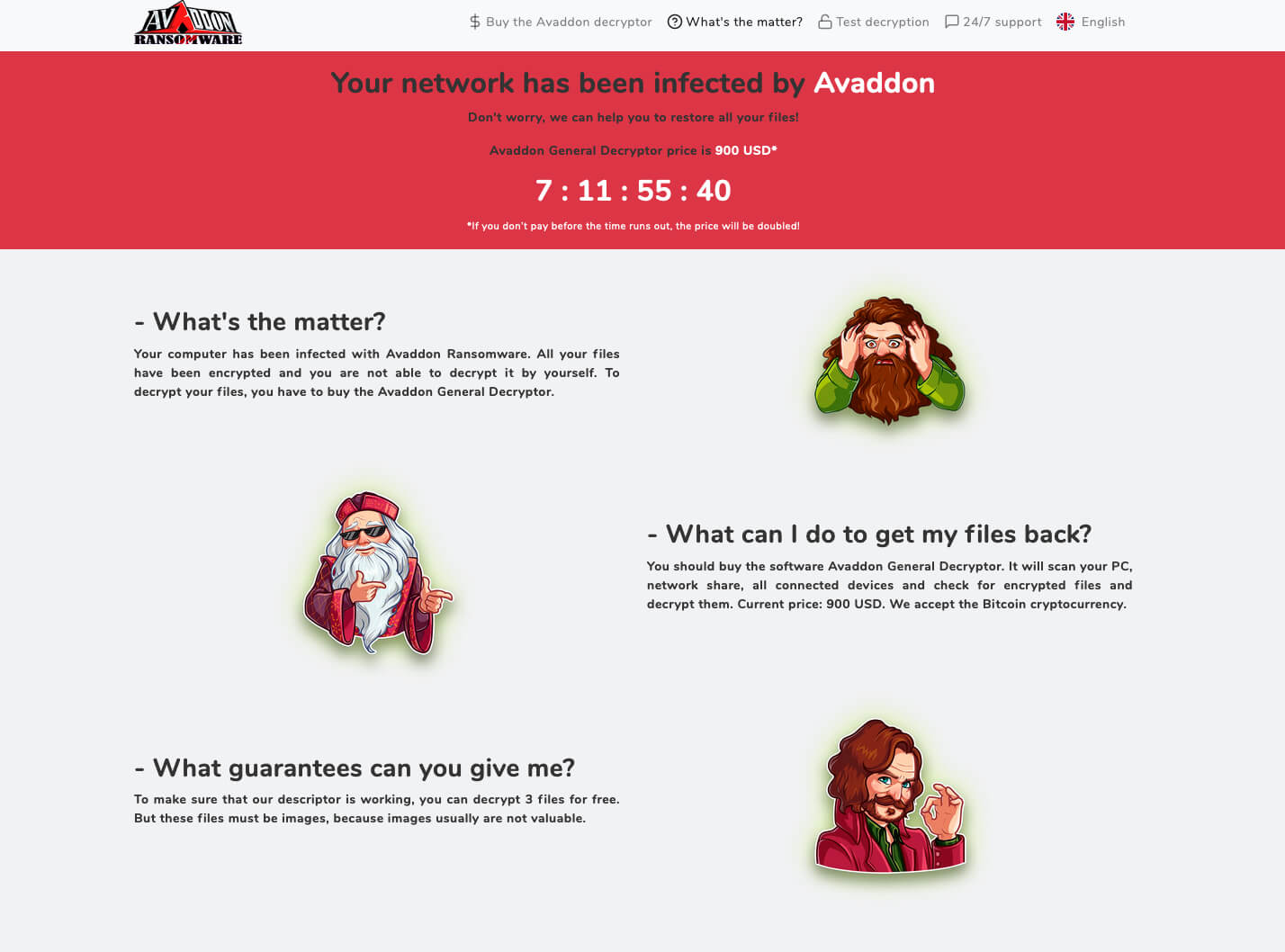
The Avaddon attackers use data leak site avaddongun7rngel[.]onion to identify victims who do not pay ransoms, ACSC says. They demand ransom payment via bitcoin, with an average demand of about $40,000 in exchange for a decryption tool, the Australian agency says.
Victims of Avaddon Ransomware
One of the victims of the Avaddon Ransomware is the French insurance company AXA. The incident took place last month and it affected the company’s Asia Assistance division and the IT operations in Thailand, Malaysia, Hong Kong, and the Philippines.
The data that Avaddon operators claimed to have stolen includes customer IDs, customer claims, contracts and reports, and more.
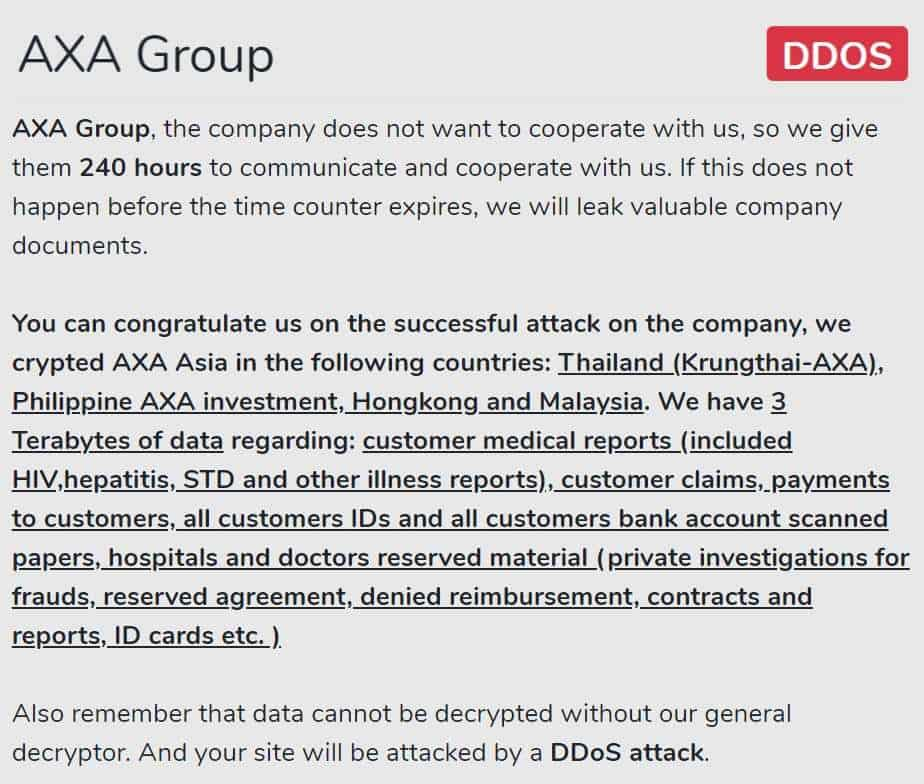
The ransomware attack may be viewed as retribution for AXA’s decision to “stop writing cyber-insurance policies in France that reimburse customers for extortion payments made to ransomware criminals.”
Another recent victim of the Avaddon ransomware operators is a Melbourne-based service provider called Communication – a platinum partner of the telecom giant Telstra. The company’s website went offline for several days.
What to Do If You’re Infected with Avaddon Ransomware
When an Avaddon ransomware infection occurs, the first thing you need to do is contain and neutralize:
- Identify what devices have been infected and isolate them immediately by unplugging the network cable or turning off the Wi-Fi adapter. Unless you can’t disconnect the network, don’t shut down the affected devices.
- Try to assess the damage: what has been affected? What has been lost? Are your backups safe? If so, you should make an offline copy as soon as possible.
- Return to your incident response plan, which is a “documented, written plan with 6 distinct phases that help IT professionals and staff recognize and deal with a cybersecurity incident like a data breach or cyber attack.” The six phases of an incident response plan include preparation, identification, containment, eradication, recovery, lessons learned.
- Search for existing Avaddon ransomware decryption keys.
After these steps, you should focus on investigation:
- You may discover that the attackers got access to your network days or even weeks before the attack.
- Avaddon ransomware operators may target both Windows and Linux systems and they might succeed by securing access to domain admin accounts or other privileged accounts.
- Check for any backdoors that the attackers might have installed that allowed them to get into your network undetected. You need to find them in order to avoid becoming a victim again.
- Your security solutions might have been disabled.
To Pay or Not to Pay, This Is the Question
Well, according to the FBI,
In some cases, victims who paid a ransom were never provided with decryption keys. In addition, due to flaws in the encryption algorithms of certain malware variants, victims may not be able to recover some or all of their data even with a valid decryption key. Paying ransoms emboldens criminals to target other organizations and provides an alluring and lucrative enterprise to other criminals. However, the FBI understands that when businesses are faced with an inability to function, executives will evaluate all options to protect their shareholders, employees, and customers. Regardless of whether you or your organization have decided to pay the ransom, the FBI urges you to report ransomware incidents to law enforcement. Doing so provides investigators with the critical information they need to track ransomware attackers, hold them accountable […], and prevent future attacks.
How to Stay Safe from Avaddon Ransomware
So, if paying the ransom should not be an option, what can you do to avoid an attack in the first place? Think about your company’s cybersecurity from a holistic point of view and apply a “defense in depth strategy”, that should absolutely include:
- patch management.
- email security.
- ransomware encryption protection.
- provide cybersecurity training to all your employees
If you’re interested, you can find cybersecurity solutions that deal with all these aspects in the Heimdal™ Security offer.
Our Heimdal Patch & Asset Management will help you close vulnerabilities by allowing you to update software and operating systems from a unified dashboard and deploying Windows, 3rd party, and custom software to your endpoints anywhere in the world.
Heimdal Email Security’s analysis vectors will keep all malicious emails out of your inbox, automatically removing malware-laced attachments, filtering emails coming from malicious IPs or domains, or those containing malicious URLs. You’ll have no more worries about elaborate phishing attempts and malware hiding in your emails.
Ransomware Encryption Protection is a solution designed to adapt and counter both zero-day threats and altered malicious code, universally compatible with any antivirus.
Heimdal™ Ransomware Encryption Protection
Wrapping Up
Avaddon is a ransomware strain that can come with an unpleasant twist, but one that can still be prevented by adopting a good cybersecurity posture and making sure that all your employees have basic cybersecurity knowledge.
However you choose to proceed, please remember that Heimdal™ Security always has your back and that our team is here to help you protect your home and your company and to create a cybersecurity culture to the benefit of anyone who wants to learn more about it.
Drop a line below if you have any comments, questions, or suggestions related to the topic of the Avaddon ransomware – we are all ears and can’t wait to hear your opinion!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











