Contents:
In the fast-evolving landscape of cybersecurity threats, ransomware has consistently remained a top concern for individuals and organizations. Among the myriad ransomware strains, the notorious Locky Ransomware has struck fear into the hearts of victims.
Initially appearing in 2016, Locky garnered significant attention due to its sophisticated encryption techniques and devastating impact on victims’ data. Though efforts were made to quell its spread, Locky has resurfaced, and its return poses an alarming risk to cybersecurity worldwide.
What Is Locky Ransomware?
Locky Ransomware is a piece of malware that encrypts important files on your computer, rendering them inaccessible and unusable. It holds them ‘hostage’, and in the meanwhile, demanding a ransom payment, in exchange for the encrypted files. It gained infamy for its aggressive distribution methods and was among the first ransomware strains to utilize email campaigns as a primary infection vector. Cybercriminals leveraged phishing emails containing malicious attachments, typically disguised as invoices, resumes, or delivery notifications. Once unsuspecting users opened the infected attachments, Locky was unleashed to encrypt files on the victim’s system and demand a ransom for decryption keys.
How Does Locky Ransomware Work
Locky ransomware is usually distributed via email, using social engineering techniques to spread the malicious code. The massive email campaigns were spearheaded by the so-called Necurs Botnet, which was considered one of the largest botnets before it went dormant. Necurs primarily distributed the Locky ransomware and the Dridex banking Trojan in its spam emails.
The most commonly reported infectious mechanism of Locky involves receiving an email with a Microsoft Word document attachment that contains the code. The document is gibberish and prompts the user to enable macros to view the document. to prime Locky’s payload. Once the virus is deployed, it will get loaded into the system’s memory. After that, it will begin encrypting documents, renaming them as hash.locky files. In addition, Locky installs .bmp and .txt files, and will encrypt network files that the user has access to.
This has been a different route than most ransomware since it uses macros and attachments to spread rather than being installed by a Trojan or using a previous exploit.
Locky variants have used a number of different file types in order to trigger the infectious process including:
- Microsoft Office (“.doc”, “.docx”, “.xls” etc.) utilizing Visual Basic for Applications (VBA)
- JScript (“.js”)
- JScript Encoded (“.jse”)
- VBScript (“.vbs”)
- Windows Script File (“.wsf”)
- Compiled HTML (“.chm”)
- HTML Application (“.hta”)
- Link Shortcut (“.lnk”)
- Windows Executable (“.exe”)
- Windows Dynamic Link Library (“.dll”)
- Windows Powershell
When the computer gets infected, you would typically see a ransom note displayed either as a desktop wallpaper or a text file, just as seen on the picture below.
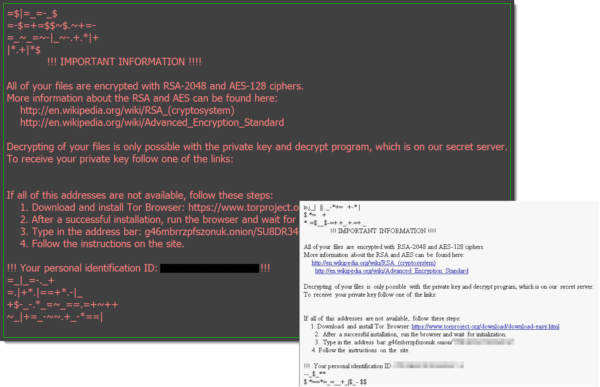
The owner of the computer or company would have to act on the following note, to get their valuable files back.
History of Locky Ransomware and Known Variants
Locky ransomware was first discovered in 2016, and quickly became one of the most significant malware threats on the Internet. Locky is currently out of commission, but other variants of the Locky ransomware have emerged.
There have been numerous variants released that used different extensions for file encryption. Many of these extensions are named after mythological figures. When first released, the extension used for encrypted files was .locky. Other versions utilized the .zepto, .odin, .shit, .thor, .aesir, and .zzzzz extensions for encrypted files.
What is also interesting to mention is its ability to locate and encrypt personal files residing on mapped and unmapped network shares, local drives, and removable drives, if available. This meant that even network paths without a designated drive letter were susceptible to infection. Locky combined the symmetric AES-128 and asymmetric RSA-2048 ciphers to render the victims’ crucial files inaccessible.
In the initial version of Locky (1.0), a significant change was the complete scrambling of victims’ filenames. Each filename was transformed into a string of 32 hexadecimal characters, followed by the “.locky” extension. For instance, “8469F0FE8432F4F84DCC48462F435454.locky” exemplifies this dramatic alteration. Additionally, the ransomware placed ransom notes named “_Locky_recover_instructions.txt” on the desktop, providing victims with links to their personalized decryptor page. The demanded ransom amount was 0.5 Bitcoin.
More about Known Variants of the Locky Ransomware Family
#1. PowerLocky Ransomware
Security analysts have detected a new threat from the Locky family. The PowerLocky Ransomware combines the powers of PowerWare and Locky, two well-known ransomware that have been responsible for numerous attacks around the world. The PowerLocky Ransomware uses the extension ‘.locky’ to recognize the files that have been encrypted with its encryption algorithm. The PowerLocky Ransomware also uses a ransom note message that had been previously associated with the Locky ransomware.
#2. Lukitus Ransomware
Locky’s Lukitus strain was first spotted in august 2017, by the Malware researcher Rommel Joven. He warned that the Lukitus was being distributed via e-mail attachments, as a part of a huge spam campaign, run by the Necurs botnet, also used by Locky ransomware. Lukitus means “locking” in Finnish very close to Locky, and the two of them definitely have their similarities. As with previously seen versions of Locky, “the spam emails distributed in this campaign include an attached archive file (.zip or .rar) that contains a malicious JavaScript or VBS script.
Favorite Targets of Locky Ransomware
Locky Ransomware has been used to target all sorts of businesses, but Healthcare has been the no. 1 target. The hackers send out an e-mail campaign targeting all the computers that they can find at the hospitals, hoping that just one person will open up the malicious attachment. Hospitals are usually targeted by hackers because of their less secure patient data storage practices. On top of that, it puts them in a very critical position if they don’t retrieve patient data. The graph below shows what industries got hit the most by Lucky ransomware in August 2016.
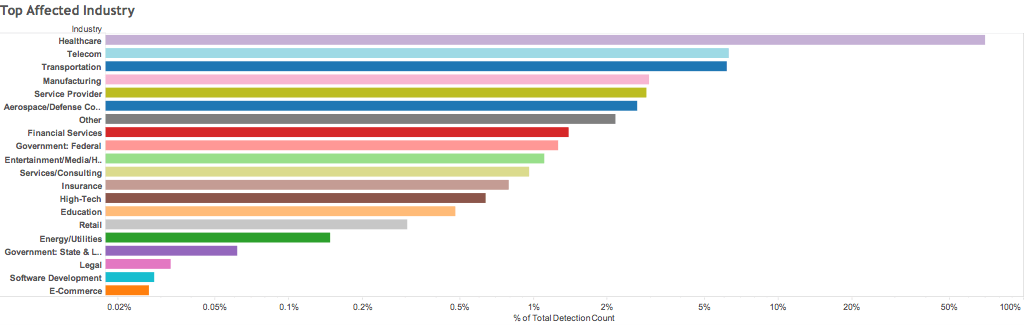
Locky Ransomware Related Incidents
On February 18, 2016, the acute-care facility Hollywood Presbyterian Medical Center paid a $17,000 ransom in the form of bitcoins for the decryption key to get their patient data back. The Hospital’s network was compromised by an email attachment disguised as a Microsoft Word invoice. The disruption caused emergency rooms and treatments to be affected, as the patient data is crucial for treating patients.
How to Stay Safe from Locky Ransomware
#1. Protecting Your Enterprise from Locky Ransomware
The best way to protect your organization from the devastating effects of Locky ransomware attacks is to prevent malware from entering your system in the first place. A broad approach to security is what we recommend.
A good antivirus is essential for the cybersecurity of any company, but not enough. To be fully protected, we recommend you choose a powerful tool that can offer DNS filtering, real-time scanning, traffic-based malware blocking, and multi-layered AI-powered protection. You can also consider our Endpoint Prevention, Detection and Response (EPDR) platform – a multi-layered security suite that brings together threat hunting, prevention, and mitigation in one package, for the best endpoint protection.
Email security
Many hackers rely on you not paying attention to what your emails actually contain and hope you’ll get infected by opening a malicious attachment or clicking on a fake link (see Locky’s MO). Pay attention to the links you want to access to make sure they lead where they’re supposed to and never open attachments or access links received from unknown, unexpected, or unwanted sources. You should also think about an email protection solution, like our Heimdal™ Email Security.
#2. Protecting Your Personal Accounts from Locky Ransomware
When protecting your home from attacks like those from the Locky family, it’s important to know that your firewall alone can’t protect your devices. You need to protect your digital life thoroughly. It’s just as important to have an all-around security solution at home as you do at your workplace, especially in this pandemic, where most of us are working from home. We recommend Heimdal™ Premium Security Home to take care of this task, as it brings the unique threat prevention layer of Heimdal™ Threat Prevention Home on top of flawless, market-leading detection. Heimdal™ Next-Gen Antivirus Home stops ransomware, data leakage, viruses, APTs, exploits & other advanced online threats.
How to act if encrypted by The Locky ransomware family?
Though this seems like a good idea, when you are desperate to get back control of your machine by paying the ransom, we never encourage people to do so. There are no promises that you actually will get your files back from the cybercriminals and giving them money only motivates them to go forward and keep on doing what they do. Take a look at what the FBI says about the matter.
“The FBI does not advocate paying a ransom, in part because it does not guarantee an organization will regain access to its data. In some cases, victims who paid a ransom were never provided with decryption keys. In addition, due to flaws in the encryption algorithms of certain malware variants, victims may not be able to recover some or all of their data even with a valid decryption key.
Paying ransoms emboldens criminals to target other organizations and provides an alluring and lucrative enterprise to other criminals. However, the FBI understands that when businesses are faced with an inability to function, executives will evaluate all options to protect their shareholders, employees, and customers.”
The Locky Ransomware family Decryption keys
#1 The Locky ransomware
The Locky uses RSA-2048 + AES-128 cipher with ECB mode to encrypt files. Keys are generated on the server-side, making manual decryption impossible, and Locky ransomware can encrypt files on all fixed drives, removable drives, network, and RAM drives. But the original Locky ransomware is obsolete, therefore you must look into what kind of Locky variant you are dealing with, and find the decryption key that works for that.
For more info on how to find out the type of ransomware you’re dealing with, and if there is a decryptor available, check this Ransomware Decryption tools article.
#2 PowerLocky Decryption
There is a free decryption key for the PowerLocky ransomware made by Michael Gillespie.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Conclusion
In the world we live in today, it is crucial to know the threats that live among us. We can no longer sit back and wait until something happens, because that may be too late. We need to be proactive and learn more about it, else hackers will forever be able to compromise our devices and steal our information. And when it comes to ransomware like the Locky, it is no different, make sure that you and your company have taken the right precautions, to stay ahead of the hackers, and stay safe!
Make sure to leave a comment below and tell us how you secure your company and home from the threatscape out there.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










