Contents:
Every once in a while, you may find yourself thinking back to simpler times. Maybe you’ll ponder that too much technology has your life both easier and more complex. Or maybe you preferred your car not to be connected to the Internet and, consequently, un-hackable.
Even cyber security specialists experience such reflective moments. Especially when they’re confronted with fileless malware infections.
Although the term sounds self-explanatory, we know that not everyone speaks the lingo. And you don’t have to be a specialist to understand and use this guide for your own online safety.
Here’s a sneak peek of what you can learn right now:
- What are fileless infections?
- Why cyber criminals use fileless malware
- How fileless infections work
- Exploit kits – a must-have for fileless infections
- How to protect your computer against fileless infections
- Fileless malware technical analyses resources
WHAT ARE FILELESS MALWARE INFECTIONS?
Fileless infections are exactly what they seem to be: malware or virus infections that don’t use any files in the process.
To understand their name, all we need is a very quick recap of how traditional antivirus products work:
- The infection places files on the hard drive
- The antivirus analyzes the malicious files (aka the payload)
- If identified, the antivirus quarantines and/or removes the malicious files, keeping your computer safe.
These infections were called fileless because no files are dropped onto the system.
The consequences? You guessed them:
A. Traditional antivirus products can’t identify this infection.
B. Without additional protection, attackers can cause all sorts of damage.
We’re going to explain exactly what type of damage fileless infections can cause and how you can protect yourself from then. Let’s start with:
WHY CYBER CRIMINALS USE FILELESS MALWARE
Cyber criminals are resourceful and creative and this fileless infections are proof.
In their attacks, malicious hackers aim for:
- Stealth – the ability to avoid being detected by security products for as long as possible
- Privilege escalation– the capacity to exploit a vulnerability that will give them administrator access to the system, so they can do whatever they want
- Information gathering – to harvest as much data about the victim and from the victim’s computer as possible (to be later used in other attacks);
- Persistence – the ability to keep the malware in system, undetected, for longest time possible.
What malware creators have done with fileless infections is trade persistence for stealth. Keeping the malware infection concealed while it triggers the intended actions is key here.
When the exploit kit carrying the fileless infection finds its way into the system (explanation coming soon), the malware can fulfill its purpose directly.
This is definitely not your typical malware!
Cyber criminals can also program fileless malware to gain persistence after it was written directly to RAM. That’s because it can hide in locations that are difficult to scan or detect by traditional antivirus products. These type of persistent and masked infections can be a real pain for your computer and data:
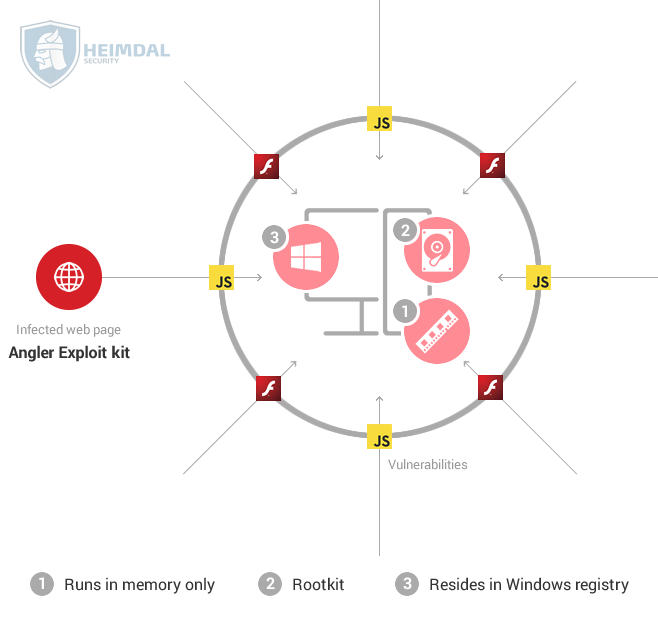
1. Memory-resident malware – this type of quasi-fileless malware makes use of the memory space of a process or an authentic Windows file. It loads its malicious code into that memory space and stays there until it’s triggered. This may not be a completely fileless malware type, but we can safely include it in this category.
2. Rootkits – this kind of malware masks its existence behind a computer user to gain administrator access. Rootkits often reside in the kernel, thus persisting in spite of restarts and usual antivirus scans. Its cloaking abilities are uncanny and removal can be almost impossible. While this isn’t an 100% fileless infection either, it fits here.
3. Windows registry malware – newer types of fileless malware are capable of residing in Windows’ registry. The Windows Registry is a database that stores low-level settings for the operating system and certain apps. It’s a difficult place to navigate as a normal user. But malware authors have even exploited the OS’s thumbnail cache to gain persistence. It’s true that this type of fileless malware executes code in a file in the registry, but the file is set to self-destruct once it carried out its malicious task.
[Tweet “Did you know that traditional AV can’t detect/stop fileless #malware?”]But wait! It gets even more interesting!
Fileless malware infections appeared in August 2014, when the Poweliks Trojan made its debut. It was initially engineered to perform click-fraud, but it evolved to do much more.
This new type of infection brought new prospects for malware makers. They now could:
- create new malware that could infect systems without triggering traditional detection mechanism;
- profit from wildly successful fileless malware infections by spreading new malware;
- run one-time info-stealing malware to gather information about an infected PC before infecting it with additional malware;
- move the payload, after the exploitation, to the Windows registry to achieve persistence;
- employ sophisticated, flexible and even modular exploit kits to find and manipulate vulnerabilities faster;
- use the high number of Zero- Day vulnerabilities to compromise a huge number of computers;
- make fast and easy money by infecting machines with ransomware.
At this point, you may ask:
Are there any drawbacks to using fileless malware?
There are, in fact.
Because fileless malware is ran in your computer’s RAM memory, it can only work while you keep your PC on. This means that attackers have a smaller windows of opportunity to execute the attack and infiltrate your operating system.
It’s true that we keep our computers on for much longer times than we used to, so cyber criminals will have more time to make the infection stick.
HOW FILELESS INFECTIONS WORK
Here’s a real-life scenario of how a fileless infection could compromise your computer.
>> You use Chrome that has the Flash plugin installed. It can also be any other browser that supports this plugin or Javascript.
>> Your Flash plugin is outdated, because you haven’t had time to install the updates.
>> You end up on a website that hosts the Angler exploit kit.
>> The exploit kit scans for vulnerabilities and finds one in your Flash plugin. It immediately starts running the payload it in the memory of your Chrome process.
>> If, for example, the payload is a ransomware strain, it will connect to the Command & Control servers controlled by the attackers and get the encryption key.
>> The last step is to encrypt the data on your PC, locking you out and asking for a hefty ransom to give you access to it once again.
As you can see, the payload (the part of malware which performs a malicious action) is injected directly into the process used for the exploitation and run in your computer’s RAM memory.
In order to avoid detection by traditional antivirus products, attackers chose not to install a malware program on a disk drive, which could be detected through signature scanning.
While traditional antivirus solutions can detect malicious payloads if they’re dropped on the disk or perhaps ran in memory (rarely), but only after the exploitation has happened.
Let’s see how Poweliks, one of the first fileless malware to be discovered, can infect a computer with ransomware, while also performing click-fraud:
Poweliks comes with a default list of keywords that it uses to generate requests for ads. The threat pretends that the victim legitimately searched for these keywords and then contacts an ad network so it knows where to direct the victim. Poweliks sends a request to the URL returned by the ad network and then receives payment for downloading the advertisement. […]
Some of the ad requests that Poweliks receives may result in malicious web pages being displayed on the affected computer. This opens the door for other malware to enter the already compromised computer. For example, one of the websites visited by Poweliks resulted in Trojan.Cryptowall being installed on the computer.
In other cases, click-fraud comes bundled with malvertising:
While the ads are not shown to victims, the downloading and processing of ads consume processing and network bandwidth and could potentially expose victims to secondary infections from malvertisement. This can lead to numerous threats ending up on a victim’s computer, or even with the victim being completely locked out of their computer because the secondary threats could include ransomware.
Source: The evolution of the fileless click-fraud malware Poweliks
[Tweet “I just learnt how fileless #malware infections work. You should too:”]
EXPLOIT KITS – A MUST-HAVE FOR FILELESS INFECTIONS
In any successful fileless malware infection, exploit kits play an important part. Exploit kits are software programs designed to find flaws, weaknesses or mistakes in apps and use them to gain access into your computer or any other system.
We’ve already mentioned the Angler exploit kit and there’s a reason we did. This particular exploit kit can deliver these fileless infections, it’s very flexible and has a low detection rate too. This means it can deliver a wide range of malware, from banking Trojans to ransomware, without being spotted by traditional antivirus solutions.
Two core factors are driving the rise in fileless malware infections:
- The fact that exploits kits-as-a-service has become a reality and cyber criminals of all kinds are trying their hand at using them;
- The fact that malware makers are producing as many as 230,000 new malware samples per day offers attackers an endless array of attack vectors.
And Angler is not the only exploit kit that cyber criminals use, even though it’s definitely a favourite.
In late December 2015, our team analyzed a campaign using Kovter, a fileless Trojan, which managed to achieve both stealthiness and persistence. It was actively used in an IRS spam campaign that delivered malware to unsuspecting victims.
As it often happens, Kovter also opened the door for other malware, such as CoreBOT, which had rapidly evolved from data-stealing malware to financial malware.
Cyber criminals are moving fast, because their objective, most of the time, is to make money. A lot of it and as fast as possible.
That’s why, when commercially available exploit kits started including the fileless infection technique, it even surprised cyber security specialists. It seemed difficult to believe that cyber criminals would give up on persistence to make their attacks as difficult to spot as possible. In order to steal a lot of data or empty a bank account, they needed time. They used that time to bypass users’ defenses and collect and exfiltrate as much data as they could.
But the truth is that things have changed a lot in the past year, and we might see fileless malware a lot more often in 2016.
How to protect your computer against fileless infections
When it first surfaced, fileless malware caused computers to run veeeeeeery slooooooowly, because it used their RAM memory to carry on the attack. As you’d imagine, that made them very easy to spot.
But cyber criminals rapidly enhanced their tactics and code to make the fileless infection go unnoticed.
The best way to protect yourself from fileless malware infections is to stop them before they happen.
Sounds just about right, but how do I actually do it?
Level 1: apply security updates for your applications and operating system.
Most users disregard software updates because of preconceived notions such as:
“It will take up more of my computer’s memory.”
OR
“It might make my computer run slower.”
Or even:
“It may cause compatibility issues with my operating system or other apps.”
But we’re not in ‘90s anymore. Security updates are crucial for your security!
Keeping your apps and OS updated at all times can rule out as many as 85% of targeted attacks (cyber attacks that target a specific vulnerability on your PC).
And if you loathe the idea of running updates, you can always automate the task with a free solution.
Level 2: blocking the pages hosting the exploit kit.
The infection starts when you end up on an infected website that hosts an exploit kit. But if you use a proactive security product, it can block the page as soon as you reach it, so the exploit kit can never reach the applications on your computer (in this case, the browser).
How?
By knowing that this compromised website is generated or connects to cybercriminal infrastructure. Attackers invest a lot in their infrastructure and rarely change it (because it takes time and a lot of money to do so). So this detection technique can be invaluable for your online security.
Level 3: blocking the payload delivery.
Once an exploit kit had identified a vulnerability in your system, it will connect to Command & Control servers to download the payload and place in your RAM memory.
But if you’re adequately protected and your security suite knows that the exploit kit is trying to connect to malicious servers, it will stop the payload download.
Once again, the fileless infection is blocked before it happens. Not even ransomware can get through!
Level 4: blocking the communication between your PC and the attackers’ servers.
Let’s say the payload does end up on your system via a Zero Day vulnerability (a flaw in software for which no update exists, because the software maker doesn’t know about it).
The next layer of protection insured by a proactive security product is to block the communication between your computer and the servers controlled by cybercriminals.
By doing this, the attackers won’t be able to retrieve the data collected from your PC, so data exfiltration attempts will be futile. Moreover, cyber criminals won’t be able to infect your system with additional malware.
[Tweet “This is how you can protect yourself against fileless #malware too (I just did):”]Your traditional antivirus products won’t be able to offer this protection, but there are solutions that can. Of course, you won’t find them for free, but having peace of mind and multi-layered security is invaluable. Any victim of a ransomware attack can tell you that.
FILELESS MALWARE TECHNICAL ANALYSES RESOURCES
If you’re technically inclined and would like to read more about fileless malware, there are some detailed analyses you can read.
We’ve made a selection of the best ones, which include:
- The evolution of the fileless click-fraud malware Poweliks
- Angler EK : now capable of “fileless” infection (memory malware)
- Fessleak: The Zero-Day Driven Advanced RansomWare Malvertising Campaign
- Triaging a System Infected with Poweliks
- Digging deep into Angler Fileless Exploit delivery
Conclusion
As using a computer became essential to our lives, we strongly believe that so will cybersecurity. Not because we’re part of this industry, but because technology is increasingly complex and errors – in the form of vulnerabilities – are unavoidable.
Those who gain online security literacy will have the upper hand when it comes to keeping their devices safe and protecting their data, which is increasingly stored and managed online. And I don’t mean cybersecurity specialists, but those who master the very basics of Internet security.
You can do it too! And the fact that you read this article all the way through is proof!



 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security