Contents:
There is a vast array of antivirus and antimalware programs available, so it can be difficult to determine which one is best for your needs. Both will help you keep your computer and data safe, but they are different solutions to different problems.
Antiviruses guard against known threats like worms and viruses. Antimalware protects you from new exploits, like polymorphic malware and zero-days.
A successful cyberattack can cause data loss, financial issues, or disrupt operations. The best way to combat these online threats is to keep your system safe using antivirus software, antimalware software, or both.
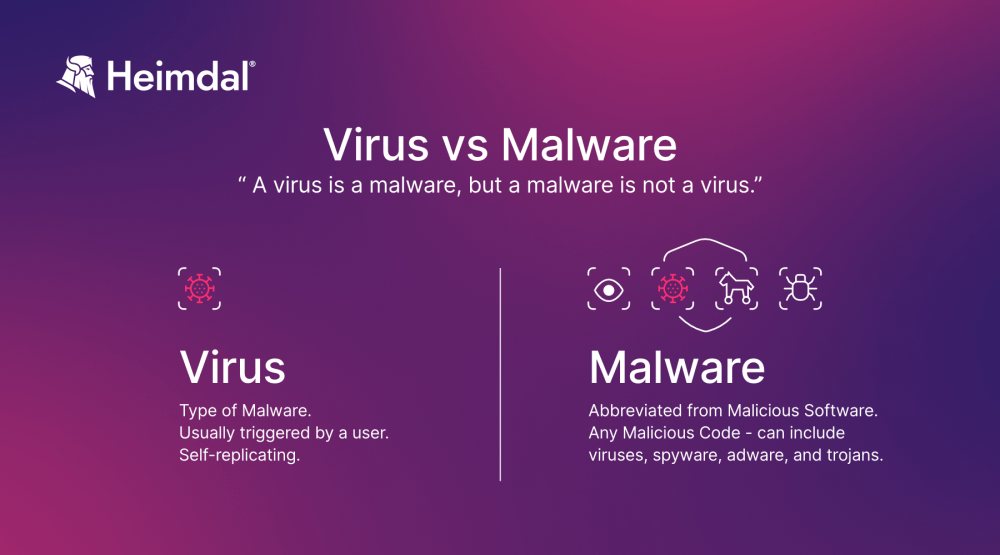
Virus vs Malware
When it comes to security software, many people are usually confused about the two terms – antivirus and antimalware. Before we jump into the waves of antivirus and antimalware, let’s see what the difference between virus and malware is:
Malware
Malware or malicious software is any program or file that is specifically created to harm a computer, network, server, or mobile device. It jeopardizes the user’s PC security and privacy by leaking and encrypting data, gaining unauthorized access to systems, and destroying information.
Malware comes in a variety of forms, including worms, trojans, spyware, keyloggers, etc.
Virus
Viruses are a type of malware that can replicate themselves and spread from one computer to another. A virus might attach itself to a program or file to execute when the program runs or the file opens. Viruses can delete files, corrupt data, or display unwanted or malicious advertising.
Although a virus is a form of malware, a malware is not always a virus.
Antivirus (AV): What It Is and How It Works
Antivirus software is a piece of software originally designed to offer protection against computer viruses. Given the proliferation of other kinds of malware, antivirus software started to protect from other cyberthreats too:
- trojans,
- keyloggers,
- rootkits,
- backdoors,
- phishing attacks,
- botnets.
However, it is limited to already known threats. Traditional antiviruses can`t detect new, unknown threats.
Antivirus is often called an antimalware program, as people tend to use both terms interchangeably. They think that antivirus programs can address all types of malware, but this is not the case. Traditional antiviruses can’t protect users against advanced forms of malware, like antimalware software does.
Choosing the right antivirus can make a difference and bolster protection for your endpoints.
Main features to look for in an antivirus program:
- Virus scanning happens in the background. The suspicious file or program will only open once the antivirus protection has finished scanning. Most antivirus programs offer real-time scanning, so they quickly detect if there`s a malicious file on your PC.
- Malicious script files blocking means that once the AV detects a malicious file, it immediately prevents it from running. Thus, it stops a potential malware infection.
- Heuristic analysis is a method that checks the files for code that behaves suspiciously. When it detects a potential threat, it flags it.
- Automatic updates are necessary to track and detect new threats. The list of existing threats the antivirus can recognize needs to be constantly updated.
- Malware removal is important because you want to eliminate a threat from the system as soon as possible. However, many free AV programs limit to detecting and blocking malware. Not all of them are able to remove malware from an infected computer. For that, you usually need to purchase a paid version of the antivirus, or a software program specialized in removing malware.
- Database of known malware which compares each scanned file to the contents of the database.
- Ransomware protection is a feature included in most of the paid versions of antivirus programs. Vendors usually offer it to premium users.
Antimalware: What It Is and How It Works
Antimalware abilities can cover broader software solutions, such as anti-spyware, anti-phishing, or anti-spam, and is more focused on advanced types of malware threats, such as zero-day malware, quietly exploited by cyber attackers and unknown by traditional antivirus products.
Main features to look for in antimalware software:
- Scan, detect, and remove known trojans, adware, spyware, and other advanced malware.
- Acts like a shield and offers second generation malware protection.
- Automatic software updates to easily identify new online threats.
- Traffic filtering for your Internet activity to secure your PC against cyber threats and blocking access to infected servers.
- Provide online banking security.
- Anti-phishing protection is a feature that is focused on detecting and blocking scams and phishing websites.
- Offer security against advanced exploit kits. Here’s a useful guide for non-technical people about the Angler exploit kit, which was one of the most notorious exploit kits used in attacks in the past years.
- Protect against websites involved in malware distribution.
- Provides a specialized malware database.
- The type of features you will find in antimalware products can be very different. Features are different, with more or less focus on proactive security, depending on what the products aim to offer.
Cybercriminals are constantly working on developing malicious software on a large scale. You can prevent infections by using a good and updated antimalware solution.
Antimalware programs can easily detect advanced forms of malware and provide specific protection from ransomware attacks. For example, they can spot, block, and remove adware and spyware threats that don’t act like regular computer viruses and might not be detected by the antivirus.
Antivirus vs Antimalware. Why Use Both?
Antimalware doesn’t try to replace users’ antivirus software but rather complements it. So, users can benefit from multiple layers of protection to combat the growing number of malware attacks.
Antivirus programs are more efficient and effective on the classic types of online threats: worms, viruses, trojans, keyloggers. On the other hand, antimalware detects and removes new and sophisticated malware strains and strengthens security.
Some antimalware programs work proactively to block ransomware before it has a chance to encrypt your data. They provide an extra layer of protection. This doesn’t mean the antivirus software is useless, it just can’t fight against advanced forms of malware, like antimalware does. For better protection and malware detection, you’ll need to use both of them.
Antivirus vs Antimalware. Pros and Cons
There are a few key differences between antivirus software and antimalware protection, and it’s important to understand them before deciding which type of protection is right for your endpoint.
Antivirus Pros:
- Antivirus software detect and remove viruses, which are one of the most common types of malicious software.
- Viruses can cause serious damage to your computer, including data loss and system crashes, so it’s important to have antivirus protection in place to prevent them from infecting your system.
- AV programs usually include additional features such as email protection and web filtering, which can further protect computers from malware.
Antivirus Cons:
- Antivirus software can sometimes flag legitimate files as malicious, which can lead to false positives.
- Usually, antivirus programs can also slow down machines due to the extra processing power required to scan for viruses.
Antimalware Pros:
- It focuses on proactive protection against malicious software.
- Filters these threats before they get to reach your system, but also during and after cyberattacks.
- Protects users from financial and data-stealing malware.
- Provides multi-layers of protection that users don’t get from a classic antivirus software.
- Offers real-time protection against the most dangerous forms of malware.
Antimalware Cons:
- The customized scan might slow the computer’s speed.
- Real-time protection could be available for premium versions of security software only.
- Doesn’t (necessarily) protect against common viruses as the antivirus does.
What Antivirus Software to Choose?
Key indicators of well-rounded antivirus software include:
- Real-time scanning: background scanning means the security software will detect threats as you encounter them.
- Automated updates: updates target any new forms of malicious software since installation.
- Threats removal: your software should remove malware, not just detect and block it.
Whether you need a free antivirus or a paid version, take your time and analyze your options.
To easily decide between a free or paid antivirus software, use specific tests. They will provide in-depth information that will help your buying decision. Expert reviews should also help in finding out which antivirus you should use.
My recommendation is to purchase an antivirus software, rather than use a free one. Free antiviruses are not enough to provide robust protection for a company. Read our guide on how you can better decide which antivirus program suits most to your needs.
What Antimalware Software Should I Choose?
Whether you find a separate antimalware software or purchase an antivirus with added capabilities, look for a program with the following:
- Sandboxing: this controlled environment allows the software to test suspected threats and determine whether or not they’re safe to use.
- Traffic filtering: this type of filtering protects your device by blocking access to suspicious servers and sites involved with malware distribution.
- Proactive security: your software should scan, detect, and remove known malware threats.
Attackers have been increasingly using zero-day vulnerabilities and sophisticated malware to get access to users’ personal data and encrypt them. And they won’t stop anytime soon.
Probably the most tech-savvy individuals know that antivirus keeps computers safe from online threats, but it’s just not enough. Antivirus can’t cope with the new wave of malware, and you need a layered approach to be more secure.
This is why choosing an antimalware program means an investment in more powerful technology aimed at destroying and preventing from advanced malware threats that classic antivirus programs can’t.
Does It Have the Right Price?
Pricing is an important factor to consider when you decide to purchase a security software – whether it’s antimalware or antivirus. In many cases, users can’t tell which is the right one, because they don’t have specific technical skills, nor do they know pricing criteria.
To better know if a security program is worth the price, users should estimate the real costs of a potential attack striking their devices by considering all case scenarios. For example, users who are being infected by ransomware attacks don’t recover their files.
Nowadays, most cyberattacks are more automated and increasingly sophisticated, which makes them harder to stop, unless there are specific algorithms designed for such attacks. That way, users can’t avoid them, even if you are using all the security measures needed.
“My device didn’t get infected” is not an excuse, as you can get the infection without noticing it. Malware has different behavior these days, as cybercriminals developing such attacks try to be silent and stay as hidden as possible.
Top 5 FAQs about Antivirus and Antimalware
Why do I need an antivirus program?
You need an antivirus program to scan your system and secure it from cyber threats. Since you can’t do that manually, you need a minimum layer of protection, and antivirus can provide you with that and detect suspicious websites and files containing malicious programs.
I have antivirus software. Do I need an antimalware program too?
Antivirus can’t detect every type of infection and don’t keep up with the cyber threats that are constantly evolving. You need an antimalware program to boost protection against newer types of malware.
I recommend reading this article on why traditional antivirus can’t detect second generation malware.
Can I run an antivirus and an antimalware program at the same time?
Yes, you can, because antimalware programs are complementary to antivirus systems and compatible with them, so they should run at the same time without any problem. If compatibility issues arise, they should be related to each product’s setup and specifications.
Does antimalware replace antivirus?
Theoretically, no, antimalware doesn’t replace antivirus. But it depends on the variety of features provided by software companies.
Am I 100% protected using both antivirus and antimalware software program?
There is no guarantee that by using both antivirus and antimalware programs on your computer, you’ll be fully protected. You need them both to stay safe and reduce the chances of malware infection.
How Can Heimdal® Help?
Heimdal`s Endpoint Detection and Response offers a complex cybersecurity software designed to protect endpoints and continuously monitor them for anomalies, as well as to respond to mitigate cybersecurity threats.
When threats arise, Heimdal’s EDR provides greater visibility into corporate endpoints. Also allows for faster response times, stopping an attack at its beginning.
Some of our most crucial modules are included in our EDR service: Threat Prevention, Patch and Asset Management, Next-Gen Antivirus, Ransomware Encryption Protection, Privileged Access Management, and Application Control. They ensure features such as automated detection and remediation, machine learning, threat intelligence, application control, patch and vulnerability management, privileged access management, intelligent alerting, and reporting.

- Next-gen Antivirus & Firewall which stops known threats;
- DNS traffic filter which stops unknown threats;
- Automatic patches for your software and apps with no interruptions;
- Privileged Access Management and Application Control, all in one unified dashboard
Conclusion
Although malware attacks continue to grow and put users’ online privacy at risk, antivirus programs remain an important tool to help keep cybercriminals out of your devices. They can offer security protection, but at a limited level, without offering maximum protection against advanced malware attacks. Antimalware gives your antivirus a boost and enhance protection for your devices.
While both types of programs protect your computer from malicious threats, each has its own strengths and weaknesses that you should consider when making this important choice.

If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









