Contents:
Recent news from the global community of cybersecurity researchers revealed a new type of .NET-based malware, dubbed Karkoff, part of the DNSpionage malware campaign. The worrisome reports on how this Karkoff malware operates highlight that the script is capable of adapting to security settings of its victims. This makes it particularly difficult to identify and remove from systems once it’s in. The malware campaign that Karkoff is a part of, dubbed DNSpionage because it’s capable of communicating with its C2 centers (command-and-control) via HTTP and DNS channels, has been investigated by researchers since November 2018. However, the new Karkoff strain of malware from within this DNSpionage family, and what it is capable of, has just been discovered and made public knowledge on the 23rd of April 2019. What is troublesome about the Karkoff malware strain is that it seems capable to intelligently scan a target’s computer for vulnerabilities and then adapt to it. For example, it will check if some well-known anti-malware solutions (for example Avast) are installed in the targeted system and then it will customize its own actions so it can bypass detection. This means that we truly reached an age in which anti-virus is not enough anymore, as a reactive defensive mechanism which only responds based on a list of known infected domains. The only solution which can stand a chance against new, adaptive malware strains such as Karkoff is a proactive traffic filtering solution, such as ourHeimdal™ Threat Prevention. This way, the safety of links and incoming traffic can be scanned and tested before your machine can actually connect to them and get infected.

The overall activities of the hacking group behind DNSpionage
Cybersecurity researchers (from Tallos) which focused exclusively on the activities of the DNSpionage campaign have pointed out that the hackers have been focusing on optimizing their activity for quite some time. Since last November, they noticed that the group was using the Mimikatz technology in order to deploy credential stuffing attacks, various off-the-shelf administration tools for allowing them to crack a full access into the processes of the victim’s computer, some open-source hacking tools customized for their operations, as well as the Putty program in order to be able to dig tunnels within the target network. Their ultimate goal is a multi-level approach to DNS hijacking attacks, so they can redirect victims’ traffic to their own servers. Since February this year, the DNSpionage campaign seems to have enhanced its range of tools with new malware strains and the Karkoff malware is the most dangerous of these.
How the Karkoff malware works
In the words of our colleagues from Bleeping Computer, this new Karkoff malware strain is capable of cherry-picking its victims in order to avoid getting caught, or in order to go for more high-gain, high-profile targets. According to intel provided by the researchers who have been watching the activities of DNSpionage, the campaign now performs a reconnaissance stage in which it automatically scans the target system for vulnerabilities. In the first phase, the malware drops a a.bat type of file (Windows batch format) and then executes a WMI command. This helps it obtain a list of all the running processes on the machine it is targeting. Next, the Karkoff malware runs a NetWkstaGetInfo() API request which gathers even more intel on the work environment of the targeted machine. This helps the malware completely fingerprint the machine and customize its next actions accordingly. 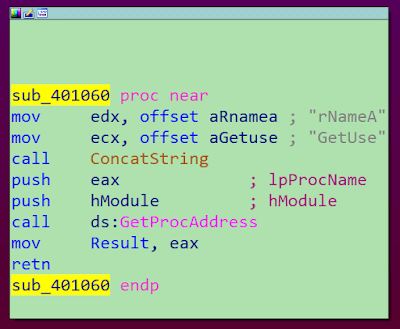 Example of split API call for Karkoff activity. Image source: Bleeping Computer. The hackers behind the Karkoff malware strained have also managed to split API calls, effectively breaking the Yara rules which are usually employed for detecting malicious activity based on previously identified strings. This means that yet again, this malware is capable of bypassing the standard detection provided by traditional anti-virus solutions.
Example of split API call for Karkoff activity. Image source: Bleeping Computer. The hackers behind the Karkoff malware strained have also managed to split API calls, effectively breaking the Yara rules which are usually employed for detecting malicious activity based on previously identified strings. This means that yet again, this malware is capable of bypassing the standard detection provided by traditional anti-virus solutions.
How to protect yourself from Karkoff
For now, there are no special steps to take in order to protect your system from Karkoff specifically, but we can recommend a few measures for advanced malware protection. As long as you follow these, you should also be safe from the Karkoff strain of malware as well.
#1. Start with a scan.
Run a complete scan of your computer to see if you Karkoff or any other malware deployed throughout your system. You can use our Endpoint Security Suite free trial; you have 30 days of free use so there’s plenty of time to secure your system before the trial expires. For now, data shows that the Karkoff malware is only capable of detecting and adapting to the Avast and Avira anti-virus solutions, so the multi-level approach from Endpoint Security Suite should be able to see it within your system if it’s infected.
#2. Keep software up to date
You probably heard us repeat it before, but it never hurts to say it again, just in case we have newcomers: outdated software poses a high-security risk. Very often, malware manages to gain an entry point into your system through software and apps which haven’t been updated in a while. To make sure you don’t get infected with a virus while trying to update your computer, manage your software patches with our Heimdal™ Free product (forever free). You can also get Heimdal™ Free as part of the Endpoint Security Suite products, so if you already have it or installed it following Step #1 advice, feel free to skip this. It automates all the updates you need and deploys them safely and silently in the background. No restarts, no interruptions.
#3. Keep learning about malware prevention strategies
Finally, the best thing you can do for your cybersecurity safety is to keep well-informed about the threat landscape, the latest threats and the social engineering techniques used by hackers to fool people. If you don’t know where to start, here are some of our free resources that will help:
- Cybersecurity course for beginners
- Cybersecurity glossary with important terms defined and explained
- Cybersecurity course for small business owners
- Our ultimate security guide for Windows 10
- The Daily Security Tip, a campaign where we send you a small nugget of info every day to help you become more knowledgeable in infosec topics.
Lastly, you should also subscribe to our blog. You’ll get a monthly digest of our best insights and guides for strengthening your knowledge of the current threat landscape and how to stay safe.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










