Contents:
Each time I talk to my friends about cyber safety, I’m reminded that we still need to focus on the basics. We can comment on attacks led by nation-states and discuss securing the Internet of Things, but that’s not going to actually help my friends be safer on the Internet.
Before moving on the big stuff, we need to cover our basics. It’s not enough to read and (hopefully) remember what malware is. You also have to be able to know where it can come from.
For example, educating younger generations also entails explaining the impact of cyber threats to them. This is especially important for those who are growing up with digital devices (shoved in their faces from day 1).
What will you tell your kids when they ask: where does malware come from?
It may not be an uncomfortable a talk as the one about the birds and the bees, but it can get tricky if you don’t know the details yourself.
But you can elegantly avoid an awkward situation by going through the list below. I tried to gather all the forms in which malware can be flung at you from various sources, but, mind you, the list is work in progress.
Let’s get to it, shall we? Here’s where malware hides on the Internet, and sometimes even in your offline life.
In (Malicious) Email Attachments
This is one of the usual suspects. In spite of countless warnings from security specialists, people still download, open, click and enable malicious attachments to run on their computers.
Sometimes, in order to trigger malware hidden inside such a dangerous attachment, the user has to perform at least 3-4 actions. Even though the email comes from an unknown source and looks strange, many Internet users (more than you’d think) still can’t see it as a threat to their safety.
And the thing is that most of these infected attachments come in through spam emails, which people still open. Curiosity is usually to blame, but few realize what these seemingly innocuous clicks could lead to.
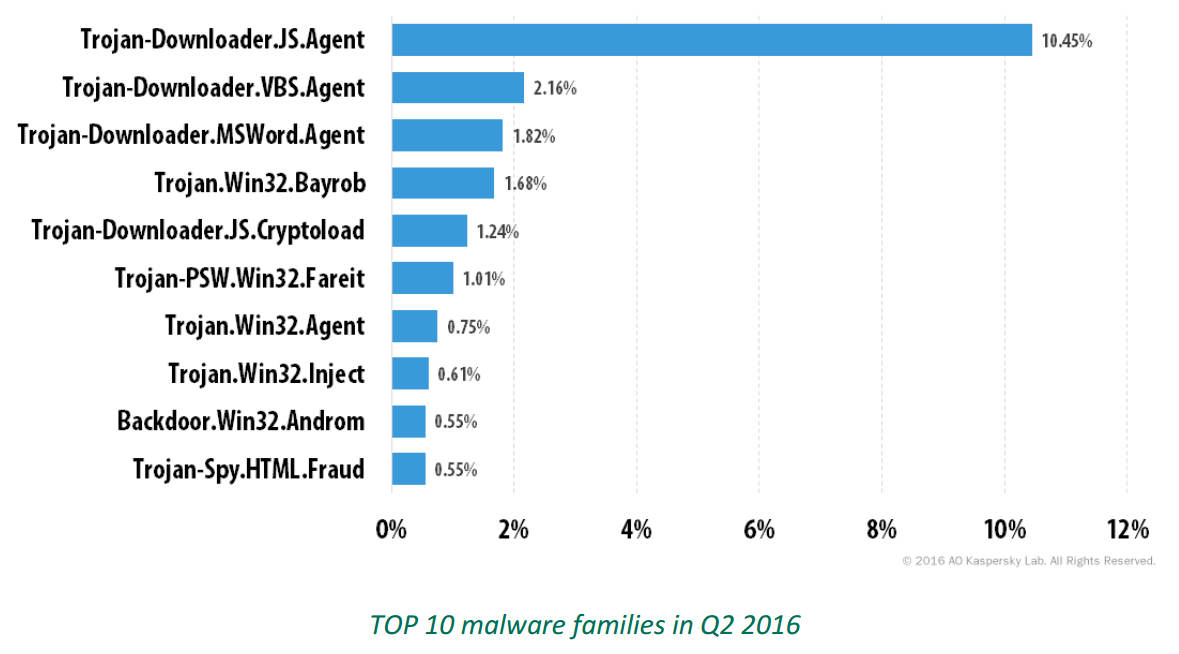
For example, here are the top 10 malware families that cybercriminals embedded into these infected files:
Source: Spam and Phishing in Q2 2016 by Kaspersky
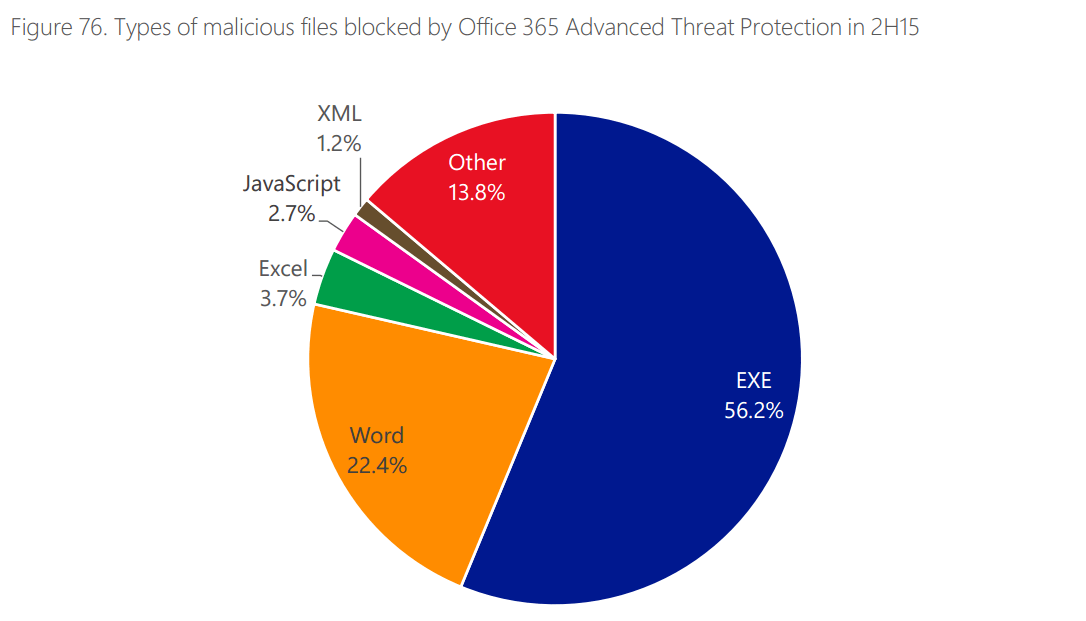
Email malware distribution is still one of the top ways cyber criminals use to spread their malicious software. The top 3 most frequent types of dangerous attachments include:
.EXE – this extension indicates that the file is an executable one, which means it can run code on your computer (including malicious code).
.DOC, .XLS, .PPT – the Microsoft Office suite is a common malware-mule because people trust this type of documents. I’ve added additional details about document malware below (so read on!).
Javascript – exploiting Javascript in cyber attacks is a new trend among cybercriminals, and a dangerous one at that.
Source: Microsoft Security Intelligence Report, Volume 20
In (Malicious) Links Sent in Emails
Clicking a link in an email is even more tempting for users than downloading a malicious attachment. It’s an instinctive reaction fueled by curiosity, boredom or simply by the power of habit.
The problem with mindless clicking is that cybercriminals know how to exploit this behavior. They know how to push all the right buttons to get you to click.
Malicious links in emails mainly work in two ways:
-
- they lead directly to a malware-infected page which will drop an exploit kit on your computer (the first step in a malware infection)
- or they include a mix of phishing and malicious software.
Phishing comes in many forms, from pharming to whaling. The cybercriminal tactic is evolving, both in terms of volume and in terms of sophistication.
The Anti-Phishing Working Group released a report earlier this year in which they showed that:
The number of phishing websites observed by APWG increased 250% from the last quarter of 2015 through the first quarter of 2016.
What’s more, the group’s Chairman, Dave Jevans, stated in a press release that:
Globally, attackers using phishing techniques have become more aggressive in 2016 with keyloggers that have sophisticated tracking components to target specific information and organizations such as retailers and financial institutions that top the list.
Asides from collecting data, phishing can also be used to distribute malware. And this type of combined threat is growing.
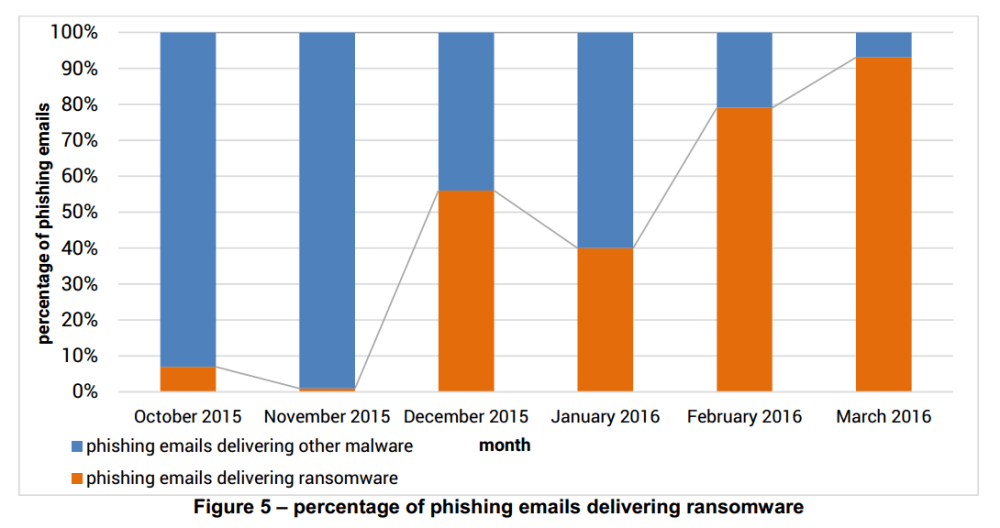
93%
This is how many phishing emails containing malware carried ransomware in Q1 2016, according to PhishMe’s Q1 2016 Malware Review.
And victims aren’t doing much to help themselves. For lack of basic cyber security education, they constantly fall for these tricks:
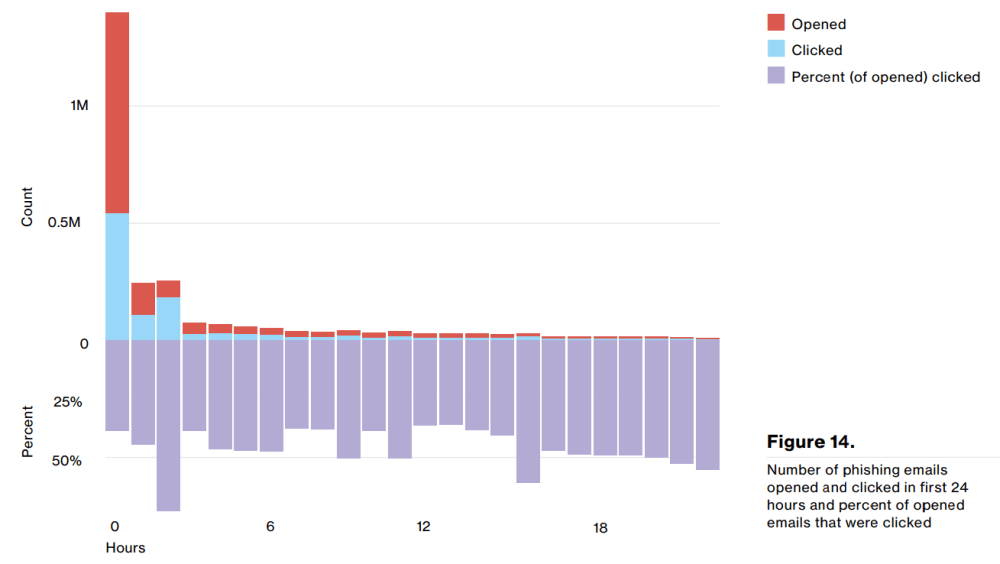
30% of phishing messages were opened by the target across all campaigns.
With all emails pouring into inboxes all over the world, you’d think that people don’t have the time to open everything they receive. However….
The median time for the first user of a phishing campaign to open the malicious email is 1 minute, 40 seconds.
Source: InfoSec Institute
And that is why malicious links in emails still work for distributing malware.
In Traffic Redirects
Another way that attackers try to infiltrate malware on your device is by redirecting your Internet traffic. This happens especially in the browser, which you should protect using everything you have.
Usually, traffic redirects are easily overlooked by users, because they either happen very fast or they’re actually “invisible” to the untrained eye.
As a result, people often land on web pages where malware is hidden in the code of the page or on the ads listed on the page (more on that later).
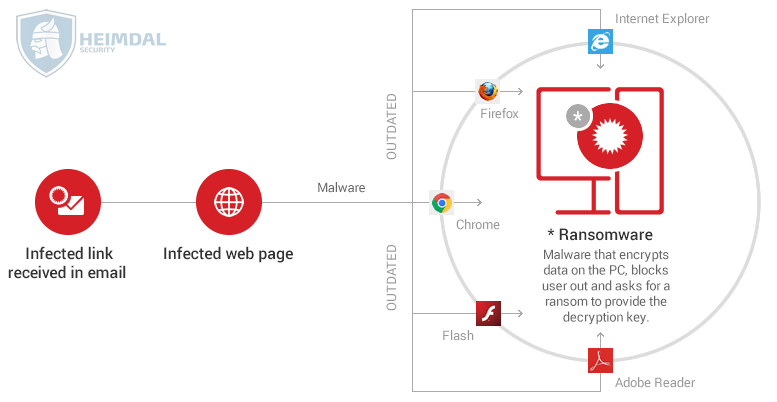
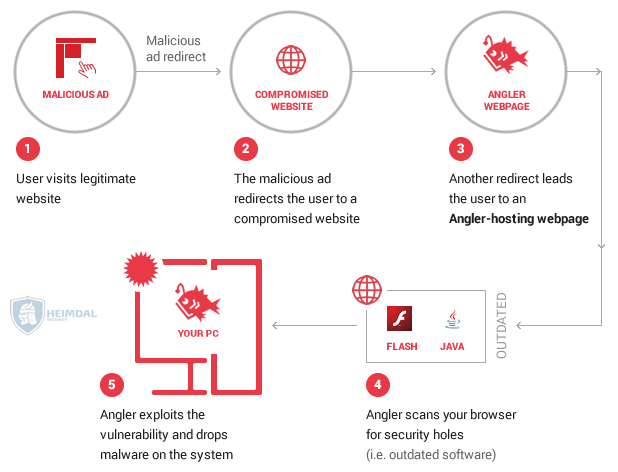
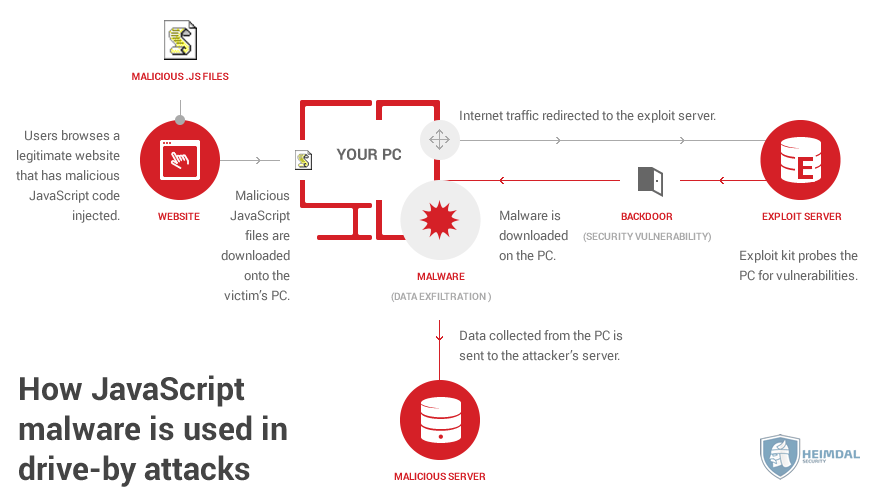
From here on, the infection chain unfolds in a similar way to the example below (depending on the type of infection, of course):
In Software Downloads
Malware often hides in seemingly harmless app downloads. Many of you might already have experienced this. Maybe you downloaded an app that changed the search bar in your browser. Maybe it slowed down your PC considerably.
It could have been just a PUA (Potentially Unwanted Application), but it could’ve been a type of malware as well. PUAs (or PUPs, as they’re also called), can become malicious, even if they didn’t start as such.
Malware hidden in software downloads affects both desktop and mobile devices. Software download websites are often plagued by questionable apps, especially when it comes to games.
As a rule of thumb, make sure to only download applications from official websites, which software makers tend to and keep secure. Otherwise, you might end up with a fake app (maybe even fake antivirus software) that’s actually malicious software and that can take over your PC in seconds. Rogueware falls into this category as well.
In Online Ads
Malvertising is a big issue on the web today. Cyber criminals often compromise networks that distribute online ads and, as a consequence, manage to spread their malware on legitimate and usually safe websites.
It happened to Spotify earlier this month, and they’re not the only platform affected. Answers.com was also impacted by the same issue at the end of September, exposing its 2 million daily visitors to potential malware infections.
Rarely do people think that malicious software can hide in an online ad, especially since they’re all over the place. (You’ve probably seen at least one website featuring over 6-8 ads on the same screen.) But that doesn’t make this threat less dangerous.
An especially insidious type of attack via infected online ads is the drive-by attack. I’d like to emphasize this because it’s a no-click-required malware infection. Just browsing the page that has injected malicious code is enough to trigger the hack.
On (Infected) Websites
I don’t mean to make you paranoid, but cybercriminals can use pretty much any website to hide their malicious code.
They compromise legitimate websites in various ways:
- by hacking their way into the content management system used (for example, WordPress, as it happened in this security alert);
- by breaking into the server on which the website is hosted (for example, in the case of an XSS attack);
- by injecting malicious code into the database that the website uses;
- through DNS hijacking.
And then there are those “one-day wonders”, websites or web pages that cybercriminals set up to not only to spread malware but also to “disguise botnet traffic.”
The best thing you can do in this case is to use the right security solutions for your needs (and budget). There’s no way to manually protect yourself from this type of cyber threat.
In Torrent Downloads
I’m sure that you already know that the files you download from torrent websites are dangerous. If not, this is the time to realize it.
Torrent poisoning is real, and I’ll back it up with an example.
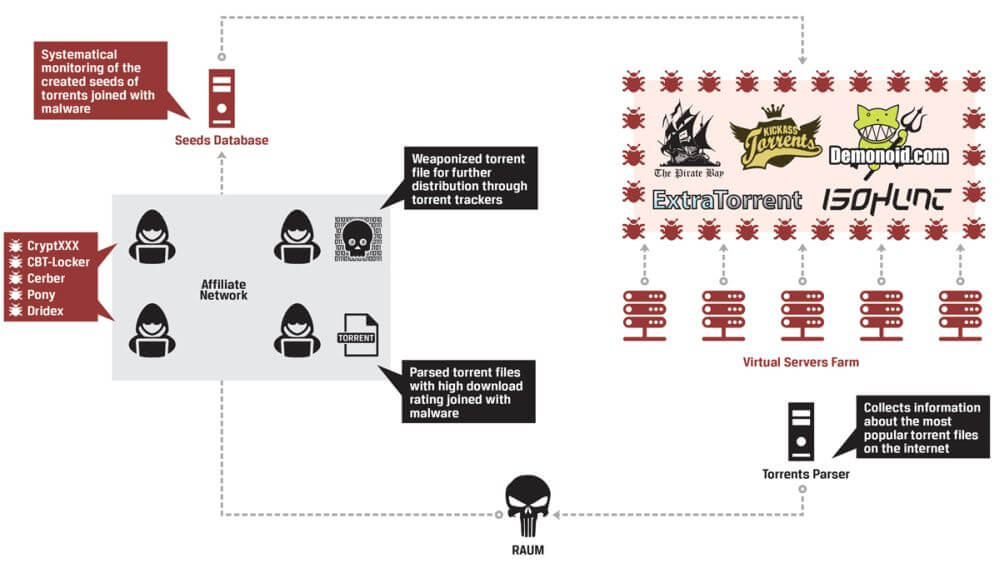
In September, InfoArmor released an analysis of how a group of cyber criminals used a special tool to distribute malicious software by packaging it into seemly trusted torrents.
Asides from disguising the malware as torrents, they also manipulated the internal rankings on some of the most important torrent websites on the web to give those malicious files the authority they need to be downloaded by thousands of users.
The infection chain is exemplified in this graphic they created:
I hope this is proof enough for you to stay as far away from torrent websites as possible from now on.
In Documents
Document malware is making a big comeback. Not that it ever left, but you may find this attack vector outdated. But, no matter what you or I think, the fact is that the method works.
Cybercriminals use macro viruses to run malicious code on your computer and trigger an infection that can spread further.
That’s why you should disable macros by default in all Office documents, no matter their extension: .doc/.docx/.xls/.xlsx/.ppt/.pptx.
Also, never, ever enable macros in documents you receive from unknown senders. They’ll most likely try to do some damage to your computer or steal your data.
In (Infected) Software Updates / Fake Update Prompts
This may sound strange to you, but it happens. Here’s an example of a case in which someone infected their computer with a fake Chrome update and it frequently happens for Java and Flash Player.
The solution to this issue is to either enable automatic updates in your apps (if they offer this feature) or use a tool that safely automates these updates for you.
Malware can take a myriad of forms, as you’ve seen until now. And we’re only about half-way through.
In Fake Free Wi-fi Hotspots
Public Wi-fi is a public safety hazard, as a great article put it. This may sound overly dramatic, but it’s not. Not by a long shot.
People have gotten so used to being connected to the Internet everywhere they do that they’ll connect to any available hotspot just to post that Instagram picture they just took. Of course, cybercriminals know this well and use it to their advantage (and to your major disadvantage).
They can not only use your FOMO to get you to connect to a fake hotspot, but they can also get your data (passwords, usernames, card details, etc.). And while they get your data, they’ll also drop a type of malware (or two) on your device (laptop, tablet, smartphone – you name it).
My recommendation is that you read this guide on public Wi-fi safety (maybe more than once) and actually apply the tips inside. You’ll thank yourself later.
In Pop-ups
Pop-ups are not only annoying, but they can also be dangerous. Not always, but oftentimes.
No matter how good an offer they make, don’t click on them. No matter how persistently they show up on your screen. Be smart, just avoid them.
This is especially true for torrent websites, software download websites and other crowded web pages that bundle tons of banners, ads and pop-ups.
If you develop your basic cyber security know-how, you’ll form a habit of avoiding these traps. Or just use an ad blocker and be done with all ads that can endanger your online safety.
In Social Media Posts & Messages
Social media is the perfect environment for cybercrime to thrive in. It’s fun, it’s fast and it lulls people into a false sense of security.
Everyone’s your friend, right?
Wrong!
Social media networks are also the place where scams flourish, so beware of links and attachments (rare, but existent) sent by random people. Refrain yourself from clicking on these, as they can camouflage malware.
As a collateral effect, the infection could also spread to your friends, by automatically propagating the malicious link/file in messages to them or posts on their Facebook walls.
Cyber security is everyone’s business, not just yours, and what you do for your own safety impacts others (people you love or don’t).
In Various Files
Malware can hide in a looooong list of files. The file extensions below are potentially dangerous because they can contain code or execute arbitrary commands.
No matter where these files come from, be wary of them and try to avoid clicking on them, unless you’re absolutely sure they’re safe.
Here are the most dangerous ones:
- .txt files – document file
- .pdf files – document file
- .jpg – image file
- .gif – image file
- .zip/.rar – archive files
- .mp3 – audio file
- .wav – video or audio file
- .mpg/.mpeg/.avi/.wmv/.mov/.ram – video files
- .exe – executable file
- .html – HyperText Markup Language file format used for web pages
- .msi – Microsoft installer file
- .jar – includes executable Java code
- .js – Javascript code that can run in browsers or individually
- .jse – encrypted JavaScript file
- .ws, .wsf – Windows script file
- .reg – Windows registry file
- .dll – Dynamic Link Library file
- .swf – ShockWaveFlash file.
Of course, the list could go on. What you should know is that cybercriminals often disguise their malicious code in these files, which they spread in various forms, as you’ve seen above.
Keep an eye out for them and exercise caution.
A great way to be safe from these is to enable “Viewing File Extensions” in Windows Explorer.
In Shortcuts
It can happen that you stumble upon some strange file extensions on your computer. These extensions can belong to shortcuts to various computer programs with specific abilities.
Here are 3 examples to watch out for:
- .SCF – this is a Windows Explorer command file. If programmed to do so, clicking on it could trigger Windows Explorer to perform malicious commands.
- .LNK – this shortcut is a link to a program on your computer. Clicking on it can activate dangerous actions that have preprogrammed by a cyber attacker.
- .INF – this is a type of text file used by the AutoRun option in Windows (which I highly recommend you turn off by default). If you click on this shortcut, you can potentially launch a malicious application that can trigger a malware infection on your computer.
Rule of thumb: if you find something on your PC that you didn’t download yourself, it’s time for a thorough cleanup and a deep scan with your antivirus and antimalware program of choice.
Infected browser add-ons and plugins
Browser add-ons and plugins can be more dangerous than you think. Since most of your Internet-related activity happens through your browser, anything that has access to it can pose serious security risks.
For example, last year we saw how Webpage Screenshot leaked private data for its 1,2 million users. Data it wasn’t supposed to collect in the first place.
To keep this cyber threat at bay, adjust the permissions for your web apps accordingly. You’ll feel much more comfortable with browsing the web all day long.
In Hacking Tools/Websites
If you’re looking to develop a career in cyber security, you’ll have to learn thing or two about ethical hacking. Of course, you’ll need to use the adequate tools for the job.
The issue is that, when you’re a beginner, you can easily fall prey to malware delivered through the very tools and websites that should teach you how to combat cyber attacks.
I recommend you search for advice and maybe start with some trustworthy courses to steadily build up your experience.
In (Infected) USB Sticks
While the biggest part of malware is distributed through web infection vectors, cybercriminals still use every trick at their disposal.
This includes sending out infected USB sticks… through the mail. In a recent example:
Police in the Australian state of Victoria are warning the public about cybercriminals’ latest tactic: randomly dropping unmarked USB sticks containing malware through letterboxes.
The worst part is that people think that scanning a USB stick with their antivirus (often a free one) is enough. A much-needed wake-up call is in order here: antivirus often doesn’t detect 2nd generation malware. This means you’ll probably persuade yourself into a malware infection without even knowing it.
Just don’t plug it in! USB sticks are so cheap nowadays that it’s not worth the risk to wipe one clean and reuse it.
To wrap things up…
I hope that, after reading this guide, you’ll have a better idea of how malware creators and other categories of cyber criminals try to slip malicious software into your software and onto your devices. The next step, you should follow is this malware removal guide, which will help you clean up an infected PC.
I’ve mentioned a few security guides already, but I highly recommend you browse our security guides category to see what best fits your current needs.
And, as always, I can’t emphasize enough how important it is to build your cybersecurity education. Nothing beats knowing what to do or what information to search for when it comes to online security issues.











 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security