Contents:
Healthcare organizations are prime targets for cyber-attacks due to the sensitive nature of patient data.
Heimdal®’s ‘Cybersecurity in Healthcare’ playbook aims to provide a comprehensive guide to protect healthcare systems from potential threats.
In this guide, you’ll find:
- Detailed explanations: In-depth insights into the significance of cybersecurity in healthcare.
- Best practices: Step-by-step recommendations for securing healthcare systems.
- Advanced techniques: Information on the latest technologies and methodologies.
- Case studies: Real-world examples of successful cybersecurity implementations.
- Tools and resources: Practical tools and resources to enhance your cybersecurity posture.
Understanding Cybersecurity in Healthcare
Why is cybersecurity in healthcare important?
Cybersecurity in healthcare involves protecting patient data and healthcare systems from unauthorized access and damage. It is crucial for maintaining patient confidentiality, ensuring trust, and complying with regulations like HIPAA.
💡Learn more about HIPAA regulations: Unlocking HIPAA Compliance
Industry regulations mandate strict standards for data security and privacy. Non-compliance can result in substantial fines, legal repercussions, and damage to the organization’s reputation.
The stakes of cybersecurity in healthcare are underscored by the high incidence and impact of breaches.
For instance, in 2020 alone, healthcare breaches affected over 40 million. Such incidents don’t only compromise patient privacy but also impose heavy financial burdens on institutions due to fines, lawsuits, and the cost of remediation.
Given these factors, robust cybersecurity measures bring a series of benefits:
- unauthorized access prevention;
- early threat detection;
- swift incident response;
- fast recovery after a cyberattack;
This comprehensive approach helps protect not only the data but also the healthcare services that rely on digital technologies, ensuring continuity and reliability in patient care.
What are the main threats when it comes to cybersecurity in healthcare?
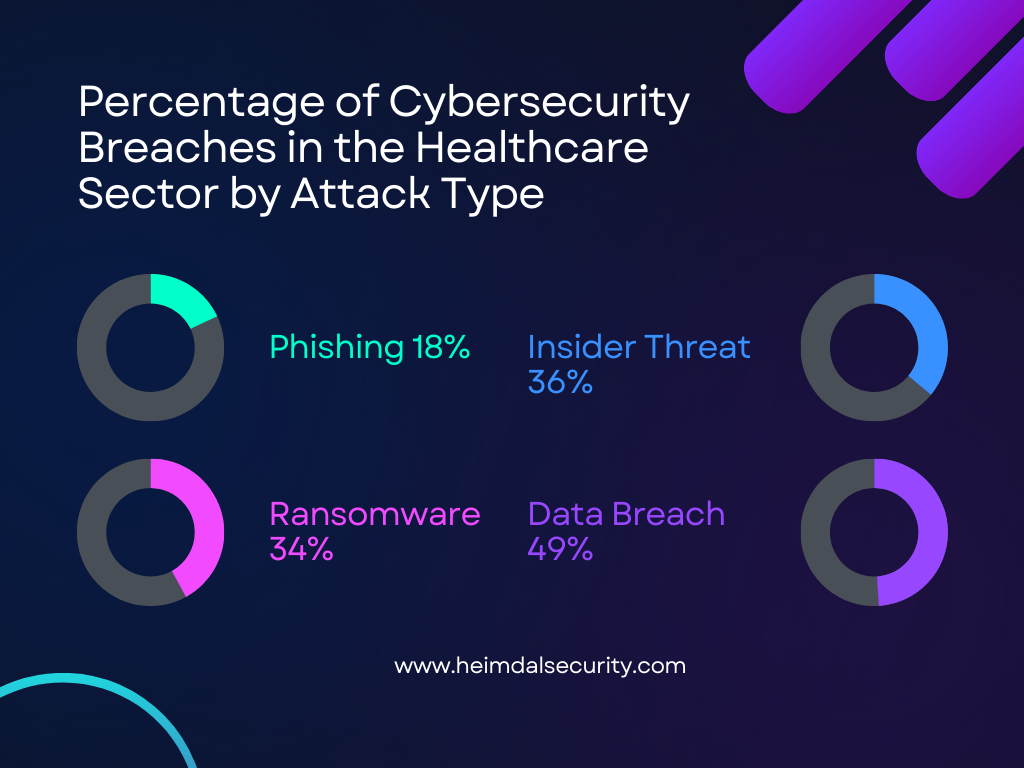
This type of malware locks systems and demands payment for access. In healthcare, ransomware can disrupt critical services, putting patient lives at risk. For example, the WannaCry ransomware attack in 2017 affected numerous healthcare facilities worldwide, leading to canceled surgeries and diverted ambulances.
💡Deep dive this topic:
- Massive Ransomware Attack Disrupts US Healthcare: Behind it, ALPHV/BlackCat
- Synnovis Ransomware Attack Disrupts NHS London Hospitals’ Activity
- Singing River Health System Ransomware Attack Affects Nearly 900,000
- Phishing
Phishing attacks trick users into revealing sensitive information through deceptive emails or websites. Healthcare employees are targeted to gain access to patient records and other confidential data.
A notable incident involved a phishing attack on a large hospital network that resulted in the compromise of over 10,000 patient records.
💡Deep dive this topic:
- What Is Phishing-as-a-Service (PhaaS) and How to Protect Against It
- Phishing attacks explained: How it works, Types, Prevention and Statistics
- How to Identify Phishing Emails and Prevent an Attack Using DNS Filtering
- Data Breaches
Unauthorized access to patient data can lead to significant financial and reputational damage. Breaches often result from unpatched vulnerabilities in the system or insider threats. In one case, a healthcare provider faced a breach due to unpatched software. The attack exposed the personal information of thousands of patients.
💡Deep dive this topic:
- 11 Million Patients` Data Stolen in HCA Healthcare Data Breach
- Major Healthcare Data Breach Impacts U.S. House Members
- What Is a Data Breach and How to Prevent It
- Insider Threats
Risks from within the organization, such as disgruntled employees or unintentional errors, can lead to data leaks and other security incidents. For instance, an insider threat incident at a major hospital involved an employee stealing patient data to sell it on the dark web.
💡Deep dive this topic:
- How to Mitigate Insider Threat – A Best Practices Guide for Organizations
- EU Healthcare: ENISA Reports that 54% of Cyber Threats Are Ransomware
- Internal Threats: A Major Risk to Any Business
What are the benefits of robust cybersecurity in healthcare?
Robust cybersecurity in healthcare brings several significant benefits given the sensitive nature of the data.
Here are the key advantages:

- Patient Safety: Ensures that patient data is secure, preventing identity theft and other malicious activities.
- Regulatory Compliance: Meets legal requirements, avoiding fines and other penalties.
- Operational Continuity: Keeps healthcare services running smoothly without disruptions caused by cyber-attacks.
- Reputation Management: Maintains trust with patients and partners by demonstrating a commitment to data security.
Methods and tools to improve cybersecurity in healthcare
In healthcare, data privacy and continuity of operations can be vital. Using effective methods and tools to bolster cybersecurity helps protect sensitive data and ensures workflow continuity. Here are the most important methods and tools to improve the cybersecurity posture:
Risk Assessment
Conducting regular risk assessments will help you identify vulnerabilities and prioritize security measures.
A risk assessment involves the following steps:
- Identify Assets: Catalog all hardware, software, data, and network components. This includes patient records, medical devices, and IT infrastructure.
- Evaluate Risks: Determine potential threats to each asset. This includes assessing the likelihood and impact of various threats, such as malware, phishing, and insider threats.
- Identify Vulnerabilities: Examine systems for vulnerabilities that could be exploited by threats. This includes outdated software, weak passwords, and insufficient access controls.
- Implement Controls: Apply appropriate security measures to mitigate identified risks. This may involve updating software, enhancing access controls, and providing employee training.
- Monitor and Review: Continuously monitor the effectiveness of security controls and update the risk assessment regularly to address new threats and vulnerabilities.
💡Deep dive this topic:
- [Free & Downloadable] Cybersecurity Risk Assessment Templates – 2024
- How to Conduct a Cybersecurity Risk Assessment (2024)
- How to Complete an IT Risk Assessment (2024)
Access Controls
Implement strict access controls to ensure that only authorized personnel can access sensitive information. This includes:
- Role-Based Access: Assign permissions based on job roles. For example, a nurse may have access to patient records, but not to financial data.
- Principle of Least Privilege: Ensure users have the minimum level of access necessary for their roles. This limits the potential damage from compromised accounts.
- Regular Access Reviews: Periodically review access permissions to ensure they remain appropriate as job roles change.
💡Deep dive this topic:
- [Free & Downloadable] Access Control Policy Template -2024
- Access Control-as-a-Service: What It Is and How Can Organizations Benefit from It?
- What Is Network Access Control (NAC)?
Employee Training
Regularly train employees on cybersecurity best practices, including recognizing phishing attempts and following secure protocols. Well-informed staff are the first line of defense against cyber threats.
Training should cover:
- Phishing Awareness: Educate employees on how to identify and report phishing attempts. Use simulated phishing exercises to reinforce learning.
- Password Security: Promote the use of strong, unique passwords and the importance of not sharing login credentials.
- Data Handling: Instruct employees on proper data handling procedures, including encryption and secure data transfer methods.
- Incident Reporting: Ensure employees know how to report security incidents promptly to minimize potential damage.
Incident Response Plan
Develop and maintain a comprehensive incident response plan. This plan should include steps for detecting, responding to, and recovering from cyber incidents.
Key components include:
- Detection: Implement monitoring tools to identify suspicious activity. Establish clear criteria for what constitutes a security incident.
- Response: Define roles and responsibilities for incident response. Ensure that there is a clear chain of command and that all team members know their tasks.
- Containment: Develop strategies for containing the impact of an incident, such as isolating affected systems.
- Eradication: Outline procedures for removing the threat from the environment. This may involve restoring systems from backups and applying security patches.
- Recovery: Plan for restoring normal operations and validating that the threat has been fully eradicated.
- Post-Incident Analysis: Conduct a thorough review of the incident to identify lessons learned and improve future response efforts.
💡Deep dive this topic:
- [Free & Downloadable] Cybersecurity Incident Response Plan Templates – 2024
- How to Create a Cybersecurity Incident Response Plan [2024]
- Incident Response – Everything You Need to Know
Advanced Security Measures
- AI and Machine Learning: Utilize AI and machine learning to detect and respond to threats in real-time. These technologies can identify patterns and anomalies that might indicate a cyber attack.
For instance, machine learning algorithms can analyze network traffic to detect unusual activity that may signal a breach.
- Encryption: Ensure that all sensitive data is encrypted, both in transit and at rest. Encryption adds an additional layer of security, making it more difficult for attackers to access the information.
Implementing end-to-end encryption for communications between healthcare providers and patients enhances data security.
- Regular Audits: Conduct regular security audits to identify and rectify vulnerabilities. Audits help in maintaining compliance and improving the overall security posture. Audits should include penetration testing, vulnerability assessments, and compliance checks.
- Multi-factor Authentication (MFA): Implement MFA to provide an additional layer of security. MFA requires users to verify their identity using two or more authentication methods, reducing the risk of unauthorized access.
For example, combining a password with a biometric factor like a fingerprint adds a significant security layer.
💡Deep dive this topic: What Is Multi-Factor Authentication (MFA)
How to integrate cybersecurity into healthcare operations?
Incorporating cybersecurity into healthcare operations is essential for maintaining the integrity, availability, and confidentiality of sensitive patient information and critical healthcare systems.
As the healthcare industry increasingly relies on digital solutions for patient care and operational efficiency, the need for a robust cybersecurity framework becomes more pressing.
Effective integration of cybersecurity measures enables healthcare providers to:
- deliver uninterrupted and safe care,
- protect patients` data,
- comply with regulatory standards.
Here’s how you can embed cybersecurity seamlessly into healthcare operations, fostering a culture of security awareness and resilience.
Collaboration
Foster collaboration between IT and healthcare professionals to develop comprehensive security strategies. A unified approach ensures that security measures are effectively integrated into healthcare operations. Regular cross-departmental meetings and training sessions enhance communication and collaboration.
Technology Upgrades
Regularly update and patch systems to protect against new vulnerabilities. Stay aware of the latest technology trends and assess critical vulnerabilities that could impact your infrastructure. . Using an automated patch management solution, like Heimdal’s, streamlines the process and ensure timely updates.
To ensure your healthcare organization remains ahead of cybersecurity threats, consider integrating Heimdal’s Patch and Asset Management into your security strategy. By automating the detection and deployment of updates across your software and hardware assets, it helps secure your systems against the latest threats without manual intervention.
This is especially critical in healthcare environments where IT resources are often stretched thin and system uptime is crucial.

Heimdal® Patch & Asset Management Software
- Schedule updates at your convenience;
- See any software assets in inventory;
- Global deployment and LAN P2P;
- And much more than we can fit in here...
Vendor Management
Ensure that third-party vendors comply with your cybersecurity standards. Vetting vendors and requiring them to adhere to your security protocols helps in safeguarding patient data. This includes conducting regular security assessments of vendors and requiring them to sign data protection agreements.
Patient Education
Educate patients on protecting their personal information. Provide resources and guidance on how they can avoid phishing scams and other threats. This can include informational brochures, online resources, and workshops. Encourage patients to use secure communication channels and strong passwords to enhance data security.
Case studies and real-world applications for cybersecurity in healthcare
Heimdal® Case Study: Mid Cheshire Hospitals NHS Foundation Trust (MCHFT)
Mid Cheshire Hospitals NHS Foundation Trust, serving Cheshire with comprehensive healthcare services, partnered with Heimdal® to enhance cybersecurity while ensuring operational continuity.
MCHFT faced two major challenges:
- a highly regulated healthcare environment
- resource optimization requirements
So, they needed a cost-effective solution that offered real-time updates to prevent operational disruptions.
After another NHS organization recommended it, MCHFT adopted Heimdal’s Application Control and Remote Desktop solutions. The recommendation highlighted the tools’ ease of implementation and effective expansion of cybersecurity capabilities.
Heimdal’s solutions provided immediate updates and proved cost-effective. This enabled MCHFT to maintain continuous operations and enhance its security posture without straining resources.
Heimdal’s Application Control was particularly noted for its seamless integration and minimal management effort, receiving high praise from Chris Thomas, Head of IT Infrastructure at MCHFT. The trust also benefits from regular, attentive support from Heimdal, ensuring the solutions continue to meet their needs effectively.

Conclusion: Heimdal’s cybersecurity solutions for healthcare providers have been pivotal in helping MCHFT protect patient privacy and care quality, demonstrating the effectiveness of Heimdal’s technology in a regulated and resource-conscious environment.
💡Deep dive this topic: Mid Cheshire Hospitals NHS Foundation Trust Consolidates Application Control with Heimdal
Conclusion
Cybersecurity is paramount in the healthcare sector, where the stakes are incredibly high.
By understanding the threats, implementing best practices, and integrating advanced security measures, healthcare organizations can protect their systems and patient data effectively.
Heimdal’s comprehensive guide provides the necessary tools and insights to enhance your cybersecurity posture and ensure the safety of your patients.
For further details and customized solutions, visit Heimdal’s website or contact our support team.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








