Contents:
In recent years, healthcare institutions have become prime targets for cyberattacks. The year 2022 witnessed an alarming increase in the number of incidents where hospitals and other healthcare facilities were hacked, resulting in data breaches, system shutdowns, and compromised patient care.
In 2022 alone, the United States Department of Health and Human Services (HSS) reported 707 data breaches that exposed 500 or more records, affecting over 48 million individuals in the U.S.
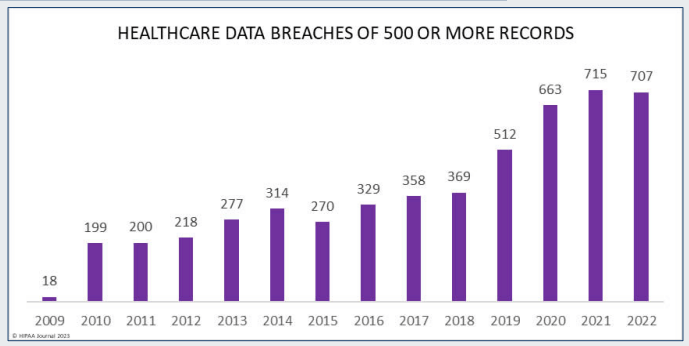
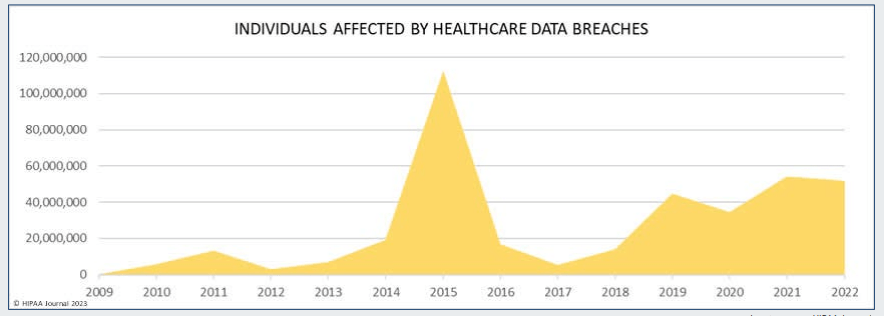
(HHS & HC3, 2022 Healthcare Cybersecurity Year in Review, and a 2023 Look-Ahead)
Not only in the U.S. but worldwide, cyberattacks have exposed sensitive patient information to unauthorized individuals, disrupted medical care, and caused significant financial losses.
Here are the top 10 largest attacks on healthcare institutions that occurred in 2022 and 2023, revealing the urgency for healthcare organizations to strengthen their cybersecurity measures:
1. Medibank: 9.7 million people impacted (Australia)
The Medibank breach, the largest healthcare breach worldwide in 2022, exposed the personal data of 9.7 million current and former clients, including 5.1 million Medibank customers, 2.8 million customers of Australian Health Management (AHM) – a privately held Australian company that offers and delivers health care plan, and 1.8 million international consumers.
The breach occurred after a cybercriminal obtained the login credentials of someone with high-level system access. After breaching the system, the attackers got access to sensitive client data and attempted to extort money from Medibank by holding the data for ransom.
The company refused to pay the ransom, and the 5GB of data was sold to a malicious actor on a Russian internet forum.
After the attack in October, Medibank’s shares dropped to $2.87, losing $1.8 billion in market capitalization in a day as investors comprehended the seriousness of the customers’ data stolen and the company’s possible liabilities.
The Medibank hack was one of the triggers that prompted the Australian government to increase the fines for repeated or serious data breaches from $2.2 million to $50 million.
2. Eye Care Leaders: 3.6 million people impacted (US)
The largest healthcare breach, but this time in the US, in 2022, affected Eye Care Leaders (ECL), a leading provider of eye care solutions. Patient notifications were staggered, with some providers waiting until November to inform individuals about the impact on their health data. ECL came under scrutiny after providers filed a lawsuit, accusing the vendor of concealing ransomware attacks and related outages.
ECL later acknowledged a separate ransomware attack in May, unrelated to the initial lawsuit, affecting Summit Eye Associates and Evergreen Health. The incident involved data deletion and potential access to patient information such as names, social security numbers, and medical records. ECL’s notification delays raised concerns, leading to additional patient-led lawsuits.
This complex situation involving the ECL ransomware attack had significant repercussions in the healthcare industry. The breach not only resulted in legal actions but also highlighted the need for prompt and transparent communication in the event of a cyber incident.
3. Advocate Aurora Health Care: 3 million people impacted (US)
Advocate Aurora Health, a prominent healthcare provider in the Midwest with 26 hospitals in Wisconsin and Illinois, faced a data exposure incident in July 2022. The misuse of a common website tracking tool, Meta Pixel, resulted in the compromise of 3 million patients’ data.
The tool utilizes JavaScript to track website visitors and improve user experience. However, Advocate Aurora Health’s implementation of Meta Pixel on patient portals unintentionally exposed Protected Health Information (PHI), particularly when users were logged into platforms such as Facebook or Google.
This incident shed light on the widespread use of Meta Pixel in the healthcare industry, leading to targeted ads and sparking a surge in class action lawsuits against Meta and healthcare providers.
4. OneTouchPoint: 2.6 million people impacted (US)
Fourth on the list is a ransomware attack on printing and mailing company OneTouchPoint that affected over 40 health plans and 2.6 million people.
The threat actor appears to have gained access to encrypted files on OneTouchPoint computers.
The subsequent investigation revealed that the actor gained unauthorized access to company servers in late April. It should be noted that company representatives initially admitted that they couldn’t tell which files on the network were accessed. However, the company later provided more details about the scope of access.
The malicious actors stole member IDs, names, information that patients gave to doctors and assistants at visits, and more. The good news is that none of the other highly sensitive information that is often stolen in online attacks, such as bank information or social security numbers, was lost.
At least 34 organizations were affected, including Matrix Medical Network, Blue Cross Blue Shield members Kaiser Permanente, Geisinger, Health First, UPMC Health Plan, Humana, Aetna ACE, Anthem Inc., and Blue Shield of California Promise Health Plan. At least one class action lawsuit has been launched against OneTouchPoint as a result of the data leak.
5. Connexin Software: 2.2 million people impacted (US)
Connexin Software also made the list, with a network hack and data theft incident that affected 119 provider offices and over 2.2 million patients. On August 26, 2022, Connexin discovered that a malicious actor had obtained access to its systems and encrypted files with ransomware.
The forensic investigation revealed that the actor responsible for the incident extracted files, including sensitive health information. The stolen data included names, addresses, dates of birth, social security numbers, health insurance information, medical and/or treatment information, invoicing, and claims information.
Connexin stated that its live EMR system and medical practice group systems were not hacked, but did not explain the lengthy delay in alerting patients and their relatives.
This led to the filing of a lawsuit against the company, because, as a HIPAA-regulated entity, Connexin is required to implement safeguards to ensure the privacy of protected health information and prevent unauthorized access, but failed to implement reasonable and appropriate cybersecurity measures such as data encryption.
The lawsuit asserts that the complaining parties now face a significant risk of being targeted in future phishing, data intrusion, and other illegal schemes, will incur out-of-pocket expenses protecting themselves against identity theft and fraud, and have or will suffer actual harm as a direct result of the data breach.
6. Professional Finance Company: 1.91 million people impacted (US)
The February ransomware attack on Professional Finance Company shows how one incident can affect hundreds of healthcare entities. The debt collection firm attack affected 657 healthcare and nearly two million patients.
The attack was discovered and stopped the same day, but not in time to prevent the disabling of some of its computer systems.
Although data theft and misuse were not ruled out by the investigation, no evidence of such activity was found. Names, addresses, A/R balances, payment history, and, in some cases, date of birth, social security numbers, health insurance, and medical treatment details were all among the types of information that could have been compromised in the attack.
The company had to wipe and rebuild all affected systems.
Moving on to 2023…
The situation does not look too good in 2023 either, because the number of people affected by healthcare data breaches in the first half of 2023 is almost equal to the number of people impacted throughout 2022.
In 2022, over 48 million individuals in the U.S. were the victims of healthcare data breaches. In the first five months of 2023, according to the most recent report by HIPAA Journal, over 36 million healthcare records were compromised.
If we also count the largest healthcare breach of 2023, HCA Healthcare, which occurred in July, is still being investigated, but affected about 11 million people, we sum up to an alarming 47 million people impacted by breaches in the first half of 2023 only.
The month of May was, in particular, one of the worst months ever in terms of the number of breached records, with a startling 19 million compromised records.
The largest data breaches in 2023 so far are:
7. HCA Healthcare: 11 million people impacted (US)
On the 10th of July, HCA Healthcare, one of the biggest healthcare providers in the U.S., reported a data breach affecting 11 million people and over 170 hospitals. The company claimed that 27 million rows of data were stolen from an “external storage location” but that it had not found “any malicious activity” on HCA’s networks or systems.
According to HCA, the stolen data included the names, addresses, birthdays, emails, phone numbers, and appointment times of patients. The data was posted for sale on a dark web forum. However, the company stated that the stolen data does not include details about healthcare conditions and treatment, credit card information, or social security numbers.
Lawsuits against HCA Healthcare were unavoidable. The first lawsuit, Silvers et al v. HCA Healthcare, claims HCA Healthcare violated HIPAA Rules and FTC guidelines, negligently failing to safeguard patients’ personal and protected health information. It alleges injuries such as lost private information value, identity theft costs, and emotional distress.
The lawsuit seeks monetary damages, legal fees, a jury trial, and injunctive relief, requiring HCA to implement data protection measures like encryption, data deletion, the implementation of threat management programs, and independent security audits.
8. Managed Care of North America, Inc. (MCNA): 8.9 million people impacted (US)
In May, Managed Care of North America (MCNA) reported a data breach impacting 8,923,662 individuals. The breach occurred between February 26 and March 7, 2023, when an unauthorized third party accessed MCNA’s IT network and stole personal and protected health information.
The compromised data included names, addresses, phone numbers, emails, birth dates, Social Security numbers, driver’s license numbers, health insurance details, and dental/orthodontic care information.
The forensic investigation confirmed that the network was compromised with malicious code, leading to the removal of personal and protected health information from its systems between February 26 and March 7, 2023.
LockBit ransomware group claimed the attack and leaked some data on the dark web, demanding a $10 million ransom to prevent publishing all stolen data. As the ransom wasn’t paid, the group released the files on April 7, 2023.
9. PharMerica: 5.8 million people impacted (US)
In March 2023, the Money Message ransomware group breached PharMerica, a major US pharmacy services provider with over 2,500 facilities and 3,100 programs, and its parent company BrightSpring Health Services, adding them to its data leak site. The group claims to have stolen 4.7 terabytes of data, including records of over 2 million individuals.
The investigation confirmed the unauthorized access to patient information and revealed that the data breach affected, in fact, 5.8 million individuals. The breach included names, addresses, birth dates, Social Security numbers, medication, and health insurance data.
Affected individuals received notifications and complimentary credit monitoring and identity theft protection for 12 months. Additional technical cybersecurity safeguards were implemented to prevent incidents like this from happening again.
10. Independent Living Systems: 4.2 million people impacted (US)
HIPAA Journal disclosed on March 15, 2023, that more than 4.2 million patients were affected by the largest healthcare data breach recorded so far this year.
Independent Living Systems, a third-party administrator for managed care organizations, reported on March 14, 2023, that between June and July 2022, a malicious actor seized data from its network and obtained files containing sensitive information.
Names, addresses, birth dates, state ID numbers, social security numbers, taxpayer ID numbers, financial account information, Medicare/Medicaid IDs, diagnosis codes/diagnosis information, admission/discharge dates, mental/physical conditions, treatment information, food delivery information, prescription information, billing/claims information, and health insurance information were among the information compromised.
The company, based in Florida, has been notifying affected individuals and has informed the Maine Attorney General’s office of the total number of patients affected. Florida Community Care and Florida Complete Care are two of its health insurance subsidiaries.
ILS stated that a preliminary notice was posted on its website on September 2, 2022, but that notification letters could not be sent until the review and validation procedure was finished.
While it ‘technically’ met with the HIPAA breach notification rule, the company did not proactively contact victims until eight months after the event occurred. Given the sensitivity of the material involved, regulators and law firms will, most likely, apply sanctions.
National Health Service (NHS): 2.5 million people (UK)
It’s also important to mention the case of NHS in July 2023, when the U.K.’s largest NHS trust, Barts Health, confirmed that they are investigating a ransomware incident amid a surge in cyberattacks on the public sector.
The ALPHV ransomware gang, also known as BlackCat, claimed to have stolen 70 terabytes of sensitive healthcare data, including employee identification documents and confidential internal emails. Barts Health serves over 2.5 million patients through its five London-based hospitals. The investigation is ongoing.
Wrap Up
These were the top 10 data breaches in healthcare in 2022 and 2023. The numbers show an increase, especially in terms of impact, reinforcing the idea that healthcare institutions must prioritize the security and integrity of their patients’ data.
If you want to learn more about the best security practices in healthcare, check out this article: Best Practices for Endpoint Security in Healthcare Institutions.
If you’re looking for a solution to protect your IT infrastructure against ransomware, you can try our Ransomware Encryption Protection. This product works in tandem with any antivirus by scanning the disk structure and detecting processes that quickly initiate file encryptions.
It automatically isolates infections and can be used to identify attacker origins and file connections, and it can run on endpoints, servers, and cloud workloads.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










