Contents:
Medibank, a health insurance company providing services for more than 3.9 million people in Australia, recently confirmed that a ransomware attack was the cause of last week’s cyberattack and interruption of online services.
The company issued an official statement apologizing for the temporary outage and confirming that a ransomware attack had occurred, and informed customers that business as usual had been resumed.
Our ongoing investigation continues to show no evidence that any customer data has been removed from our IT environment. We have resumed normal activity for our customers, after temporarily removing access to some of our customer systems as a precautionary measure last week. We’re sorry for the inconvenience and concern this may have caused.
A statement from Medibank’s CEO, David Koczkar (Source)
David Koczkar states that although the business was the victim of a ransomware attack, no systems were encrypted. Additionally, even though they are still looking into the incident, there is no proof that the attackers stole any customer data.
According to Bleeping Computer, on October 12th, the company discovered unusual activity on its network and immediately shut down some of its systems, including services geared toward customers, to minimize the risk of data loss in the event of a cyberattack.
On the 14th of October, about 2.8 million emails and SMS were sent out by Medibank to inform its clients of the security breach and to explain the reasons behind the outages.
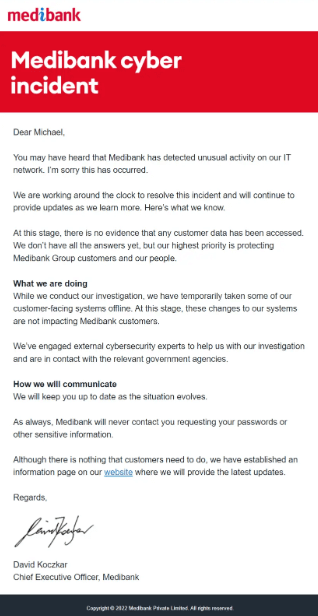
The notice emphasized that the investigation was still ongoing while offering guarantees regarding the security of private information.
Medibank also notes that they took additional measures of precaution across their network and they will continue their forensic investigation and cooperation with external cybersecurity professionals and the Australian Government’s lead cyber agency. The official statement is available here.
Australia was recently confronted with numerous high-profile cybersecurity incidents, including Optus security breach and Telstra data breach.
Update (October 27, 2022): Medibank Confirms that Hackers Accessed All Clients’ Personal Data
On the 26th of October, Medibank confirmed that hackers accessed all of its clients’ personal data and health claims data during the cyberattack.
The internal investigation revealed that threat actors had significantly more access to client data than previously assumed. The company confirmed, in an official statement, that the following data was compromised:
- All ahm customers’ personal data and significant amounts of health claims data;
- All international student customers’ personal data and significant amounts of health claims data;
- All Medibank customers’ personal data and significant amounts of health claims data.
Data access and data exfiltration are two different things, but Medibank found evidence that, in some cases, the cyber attackers were able to remove some of the accessed data. Therefore, customers should assume that all of this data was stolen.
As previously advised, we have evidence that the criminal has removed some of this data, and it is now likely that the criminal has stolen further personal and health claims data. As a result, we expect that the number of affected customers could grow substantially.
Initially, Medibank downplayed the significance of the security breach, but soon the ransomware gang contacted the company to extort it, delivering a sample of 100 stolen files from a claimed 200GB of data stolen during the attack, explains Bleeping Computer.
Because Medibank quickly concluded that the threat actors had exfiltrated client data, the internal investigation became more focused, finally exposing a full-scale data breach. Based on this progress, Medibank has announced a support package for affected customers that includes the following:
- Financial support for customers who are in a uniquely vulnerable position as a result of this crime;
- Free identity monitoring services for customers who have had their primary ID compromised;
- Reimbursement of fees for re-issue of identity documents that have been fully compromised in this crime;
- Specialist identity protection advice and resources from IDCARE;
- Medibank’s mental health and wellbeing support line.
Update (November 8, 2022): Medibank Will Not Pay the Ransom
On the 8th of November, Medibank announced in a press release that it turned down the attackers’ ransom demand, as advised by cybercrime experts.
Today, we’ve announced that no ransom payment will be made to the criminal responsible for this data theft. Based on the extensive advice we have received from cybercrime experts we believe there is only a limited chance paying a ransom would ensure the return of our customers’ data and prevent it from being published.
The company also added that “paying could have the opposite effect and encourage the criminal to directly extort our customers”, and there is a good probability that doing so will endanger more people by making Australia a bigger target.
Medibank stated that, based on their current investigation, the criminals may have gained access to the following data:
- Name, date of birth, address, phone number and email address for around 9.7 million current and former customers and some of their authorised representatives.
- Medicare numbers (but not expiry dates) for ahm customers;
- Passport numbers (but not expiry dates) and visa details for international student customers;
- Health claims data for around 160,000 Medibank customers, around 300,000 ahm customers and around 20,000 international customers. This includes service provider name and location, where customers received certain medical services, and codes associated with diagnosis and procedures administered.
- Health provider details, including names, provider numbers and addresses.
The company also noted that hackers did not get access to financial information (like credit card and bank details), primary identification documents (like driver’s licenses), or health claims data for extras services (like dental, physio, optical, and psychology).
Given the nature of this crime, unfortunately we now believe that all of the customer data accessed could have been taken by the criminal. Customers should remain vigilant as the criminal may publish customer data online or attempt to contact customers directly.
The official Medibank press release from 8th of November is available here.
BlogXX, A Relaunch of REvil Ransomware – Believed to Be Behind the Attack
The attack has been attributed to a group that some believe is a relaunch of REvil ransomware and others track as BlogXX. The ransomware group threatened to release data supposedly stolen from Medibank’s infrastructure within 24 hours in a new entry uploaded to their data leak website today, according to Bleeping Computer.
The original REvil ransomware group shut down in October 2021 after its Tor servers were stolen and members were arrested in Russia. In April 2022, the original Tor websites began diverting users to new websites known as the ‘BlogXX’ operation.
Due to website redirects and code similarities, some consider the new operation a relaunch of REvil, as do cybersecurity researchers from MalwareHunterTeam.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










