Contents:
The ransomware operation known as BlackCat, also referred to as Alphv ransomware, has been utilized by members of the Alphv group since November 2021.
During the last few years, BlackCat has demonstrated a clear upward trajectory in its operations. Their recent attacks include targeting organizations in the healthcare, education, electricity, and natural gas, sectors.
In a FLASH report released by the FBI back in April 2022, they reveal that BlackCat/ALPHV ransomware as a service (RaaS) had compromised at least 60 entities worldwide by the end of March 2022.
How do They Operate?
BlackCat is written in Rust, considered to be a secure programming language, and supports Windows and Linux-based systems including Debian, and Ubuntu.

The BlackCat ransomware gang exploits previously compromised user credentials as a means to gain initial access to the targeted system. They use Windows Task Scheduler to configure malicious Group Policy Objects to deploy ransomware and steal victims’ data before executing it.
MITRE ATT&CK Tactics and Techniques Observed Across Recent Cases Associated with BlackCat Ransomware Group
Initial Access
Although evidence of the initial access vector may not always be accessible, the earliest signs of compromise strongly suggest that threat actors have utilized valid credentials.
Access Token Manipulation
BlackCat has the ability to modify access tokens
Command and Scripting Interpreter: Windows Command Shell
It can execute commands on a compromised network with the use of cmd.exe.
Modify Registry
It has the ability to add the following registry key on compromised networks to maintain persistence: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services \LanmanServer\Paramenters
System Owner/User Discovery
It can utilize net use commands to discover the user name on a compromised host.
Windows Management Instrumentation
Uses wmic.exe to delete shadow copies on compromised networks.
What are the Indicators of Compromise (IOC)?
Pipe
\\.\pipe\__rust_anonymous_pipe1__.<Process ID>.<Random number>
BlackCat Ransom Note
RECOVER-uhwuvzu-FILES.txt
Files created
checkpoints-<Filename>.uhwuvzu
RECOVER-uhwuvzu-FILES.txt.png
Processes spawned
cmd.exe /c “wmic csproduct get UUID”
cmd.exe /c “fsutil behavior set SymlinkEvaluation R2L:1”
cmd.exe /c “fsutil behavior set SymlinkEvaluation R2R:1”
cmd.exe /c “iisreset.exe /stop”
cmd.exe /c “vssadmin.exe Delete Shadows /all /quiet”
cmd.exe /c “wmic.exe Shadowcopy Delete”
cmd.exe /c “bcdedit /set {default}”
cmd.exe /c “bcdedit /set {default} recoveryenabled No”
cmd.exe /c for /F “tokens=*” %1 in (‘wevtutil.exe el’) DO wevtutil.exe cl %1
cmd.exe /c “reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters /v MaxMpxCt /d 65535 /t REG_DWORD /f”
cmd.exe /c “arp -a”
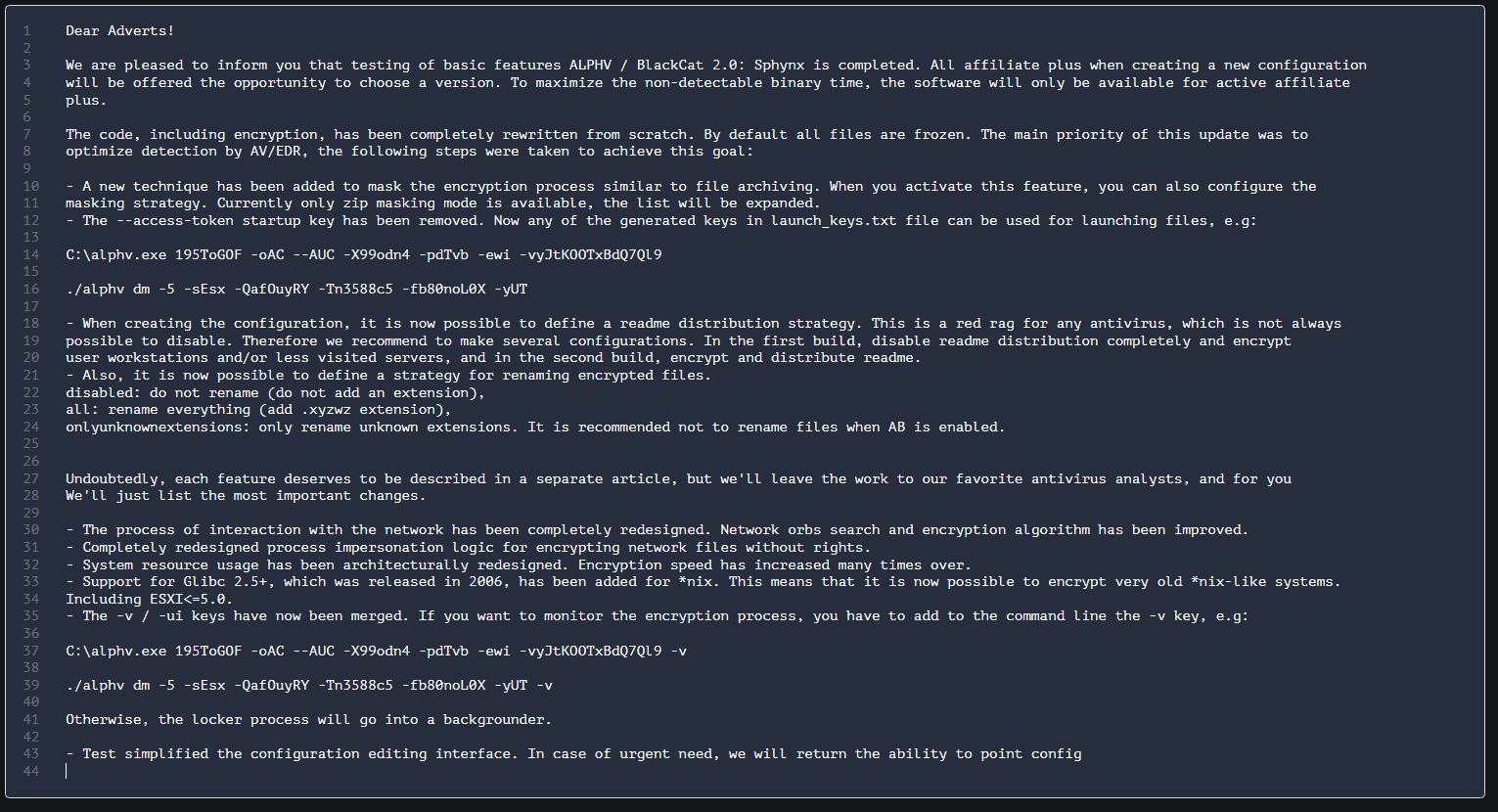
BlackCat Released a New Version of Ransomware
Sphynx differs from the previous variants in considerable ways, for example, the configuration data is not JSON formatted anymore, but raw structures, and also the process of interaction with the network has been completely redesigned.
The code, including encrytion has been rewritten from sctratch. By default, all files are frozen. The main priority of this update is was to optimize detection by AV/EDR
How Can Heimdal™ Help?
To combat ransomware, Heimdal™ Security is offering its customers an outstanding integrated cybersecurity suite including the Ransomware Encryption Protection module. This module is universally compatible with any antivirus solution and operates without relying on signatures, guaranteeing exceptional detection and remediation of all forms of ransomware, whether they are fileless or file-based.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security