Contents:
HCA Healthcare, one of the largest health companies in the USA, announced on July 10th it was the target of a huge data breach.
The cyberattack impacted 1,038 hospitals and physician clinics across 20 states. All in all, 11 million patients in 20 states, including California, Florida, Georgia, and Texas had their personal data stolen. The incident is one of the largest healthcare breaches in history.
What Kind of Data Was Stolen?
The company discovered the data breach on July 5th. Until now, it seems that the hackers managed to exfiltrate:
- Full names, date of birth, and gender,
- Data regarding the city, state, and zip code,
- Contact data, like emails and telephone numbers,
- Patients` service date, location, and next appointment date.
The threat actor claimed to have 27.7 million records and has already released for sale, on a dark forum, nearly 1 million records. Initially, the hacker tried to obtain ransom from HCA Healthcare. Since the company did not respond to blackmail, the malicious actor put the full database for sale. He claims that the stolen records were created between 2021 and 2023.
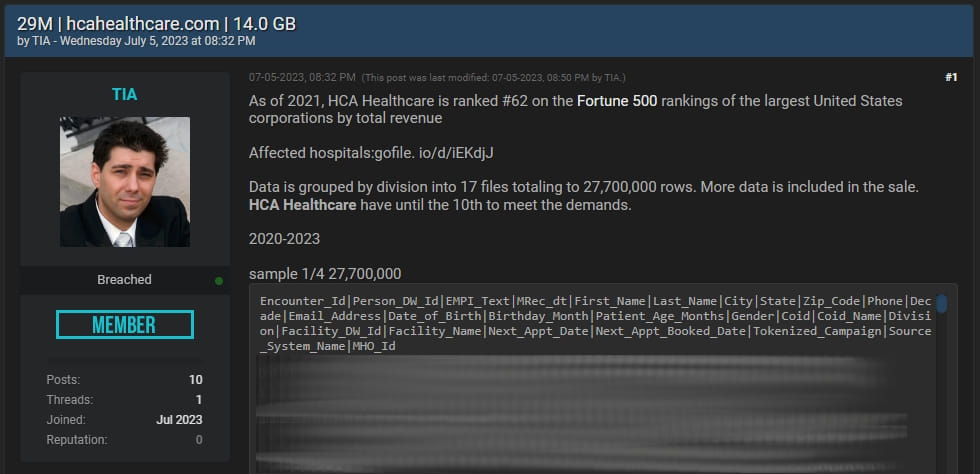
HCA Healthcare believes that the list contains approximately 27 million rows of data that may include information for approximately 11 million HCA Healthcare patients, explains an HCA Healthcare data breach notification.
HCA says that the data was stolen from an “external storage location” used to format patient email messages.
How to Prevent and Mitigate Data Breaches
Threat actors can use the leaked data for launching phishing attacks and social engineering. However, HCA Healthcare claims the stolen data does not include information about conditions, diagnosis, credit card and bank account numbers, passwords, or other extremely sensitive details.
The company has announced law enforcement and the investigation is now ongoing. In addition, the organization started to enforce additional security and data protection measures.
To prevent and mitigate data breaches and data losses, cybersecurity specialists recommend:
- Encrypt your data.
- Patch known vulnerabilities in a timely manner.
- Enforce endpoint security best practices.
- Check and enhance the safety of your Cloud Storage.
- Educate employees to use strong passwords and enforce a password policy.
- Use a DNS filtering solution to block all malicious communication, be it from the inside or outside. AI-powered filtering engines can predict with 96% accuracy if a domain is malicious. Detection works even if the domain is not on a blacklist. It stops communication to C2 servers thus making data exfiltration impossible.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
Do you work for an NHS Trust? Heimdal is giving you free ransomware licenses to combat growing cyber attacks.
Get your free ransomware protection here .


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









