Contents:
In the wrong hands, medical data can be used for a variety of crimes, such as patient identity theft, clinician identity theft, extortion, tax fraud, insurance fraud, and more.
Geopolitical agendas further complicate the threat landscape, as cyberattacks such as DDoS or cyberespionage have become part of the arsenal in geopolitical conflicts, such as the Russia-Ukraine conflict.
The pro-Russia hacktivist group KillNet, for example, has rapidly grown into a serious threat to the healthcare sector in just a few months since its inception in 2022.
In an analyst note, the Health Sector Cybersecurity Coordination Center revealed that in late January 2023, Killnet orchestrated over 90 coordinated DDoS attacks against healthcare systems, including some hospitals with Level I trauma centers that treat severely ill or injured patients, in retaliation for the delivery and assistance of tanks to Ukraine.
However, regardless of the motivation behind them and their increased complexity, the most common cyberattacks that target healthcare institutions remain:
1. Ransomware Attacks: Healthcare, the number one target
Ransomware is a type of malware that encrypts data and demands payment, usually in the form of cryptocurrency, for its release.
Healthcare institutions are often targeted in ransomware attacks due to the criticality of patient data and the potential disruption to patient care. These attacks can result in data loss, financial loss, reputational damage, operational disruption, and even delayed medical treatments.
Ransomware poses the greatest cyber risk in the industry, with profit serving as a primary motivation for these attacks. While sophisticated groups are often behind such incidents, the increasing prevalence and accessibility of ransomware-as-a-service (RaaS) means that anyone can initiate an attack.
Recent studies show that ransomware attacks need less than four days to encrypt systems, a 94% decrease from 2019 to 2021.
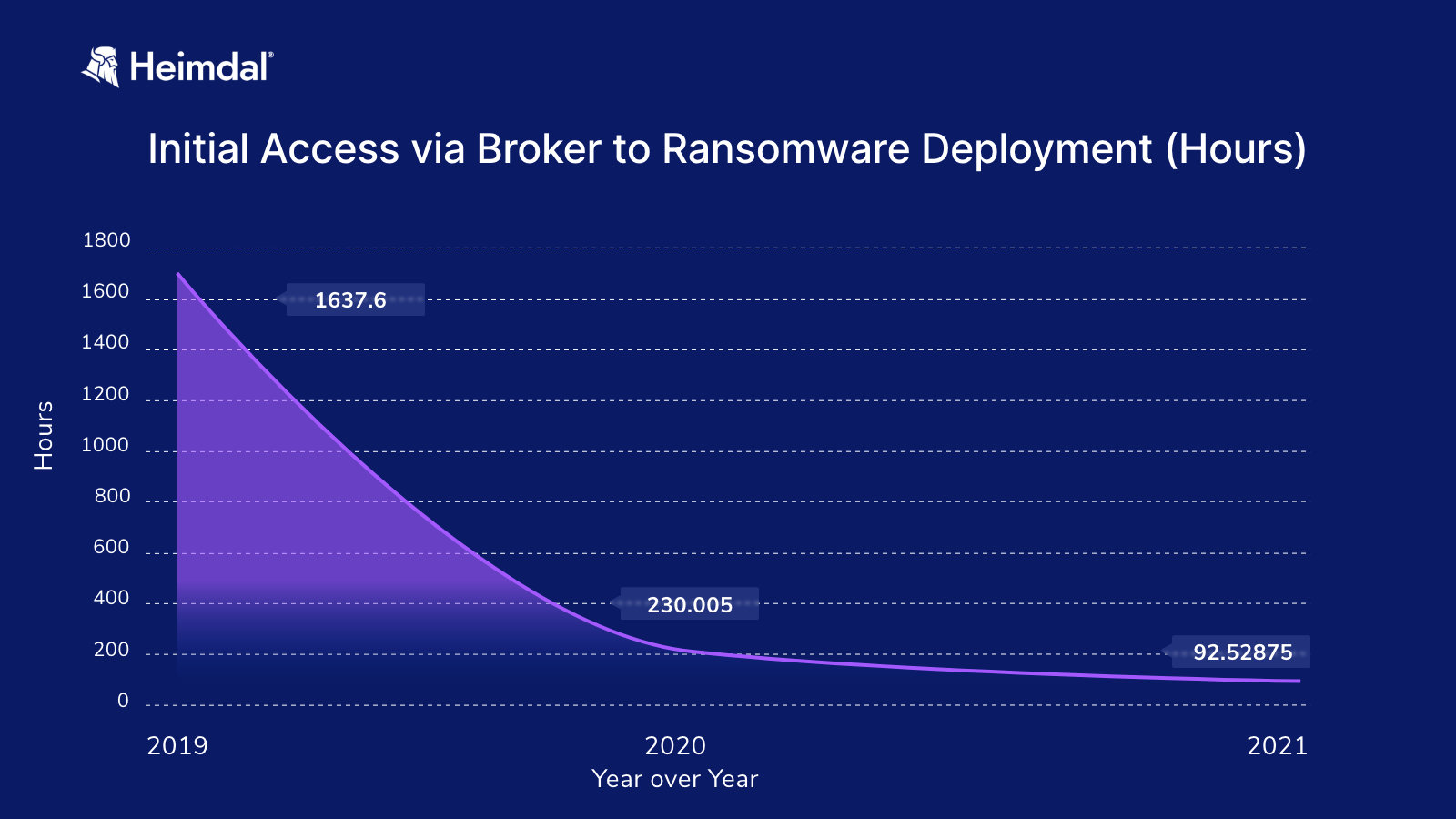
Initial Access via Broker to Ransomware Deployment (IBM Ransomware Study, 2022)
Moreover, the FBI’s most recent Internet Crime Report reveals that the Healthcare and Public Health sector is the most affected by ransomware.
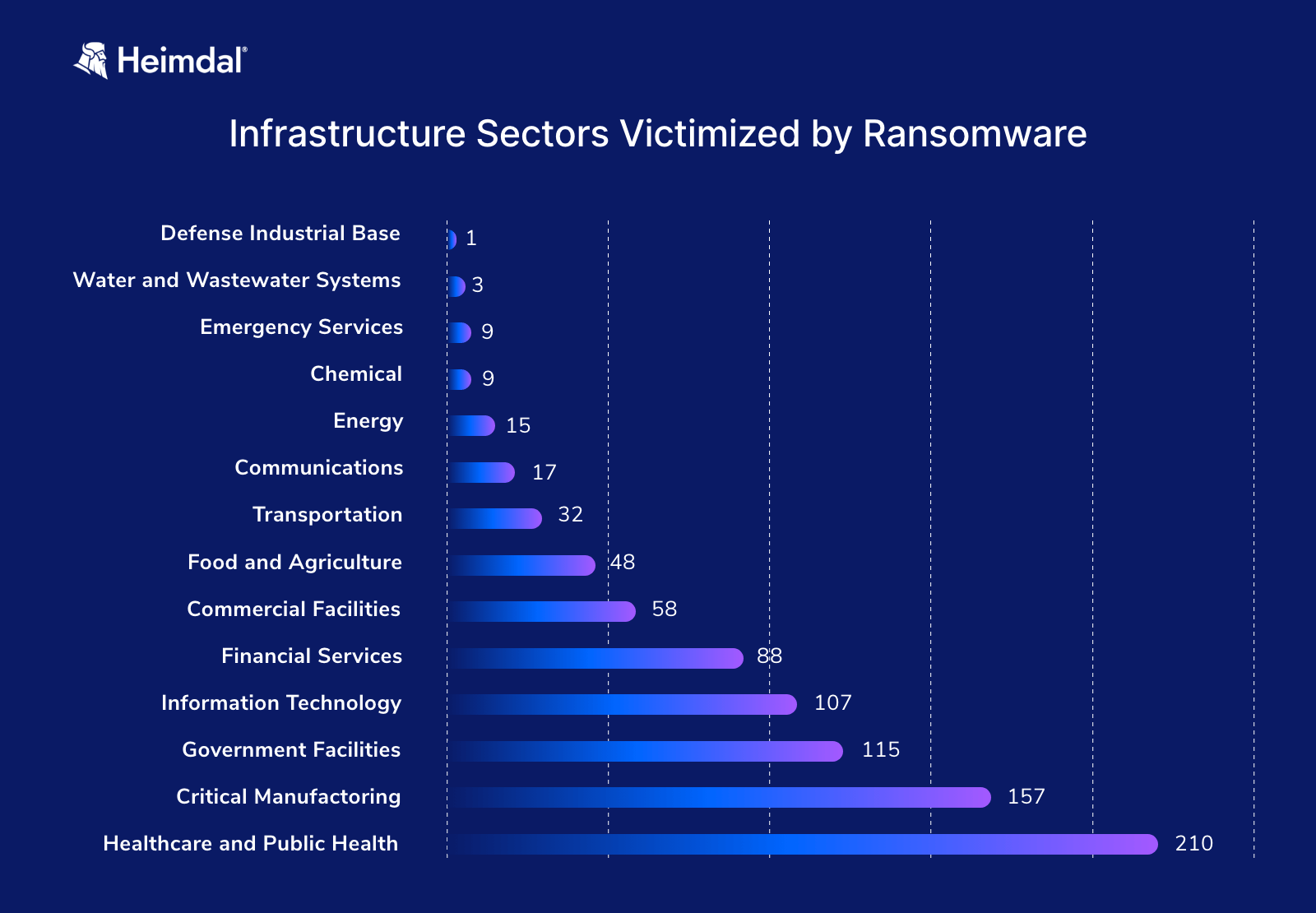
Infrastructure Sectors Victimized by Ransomware (FBI Internet Crime Report, 2022)
The same study shows that the top 3 ransomware variants that victimized critical infrastructures in 2022 were: Hive, ALPHV/Black Cat, and Lockbit.
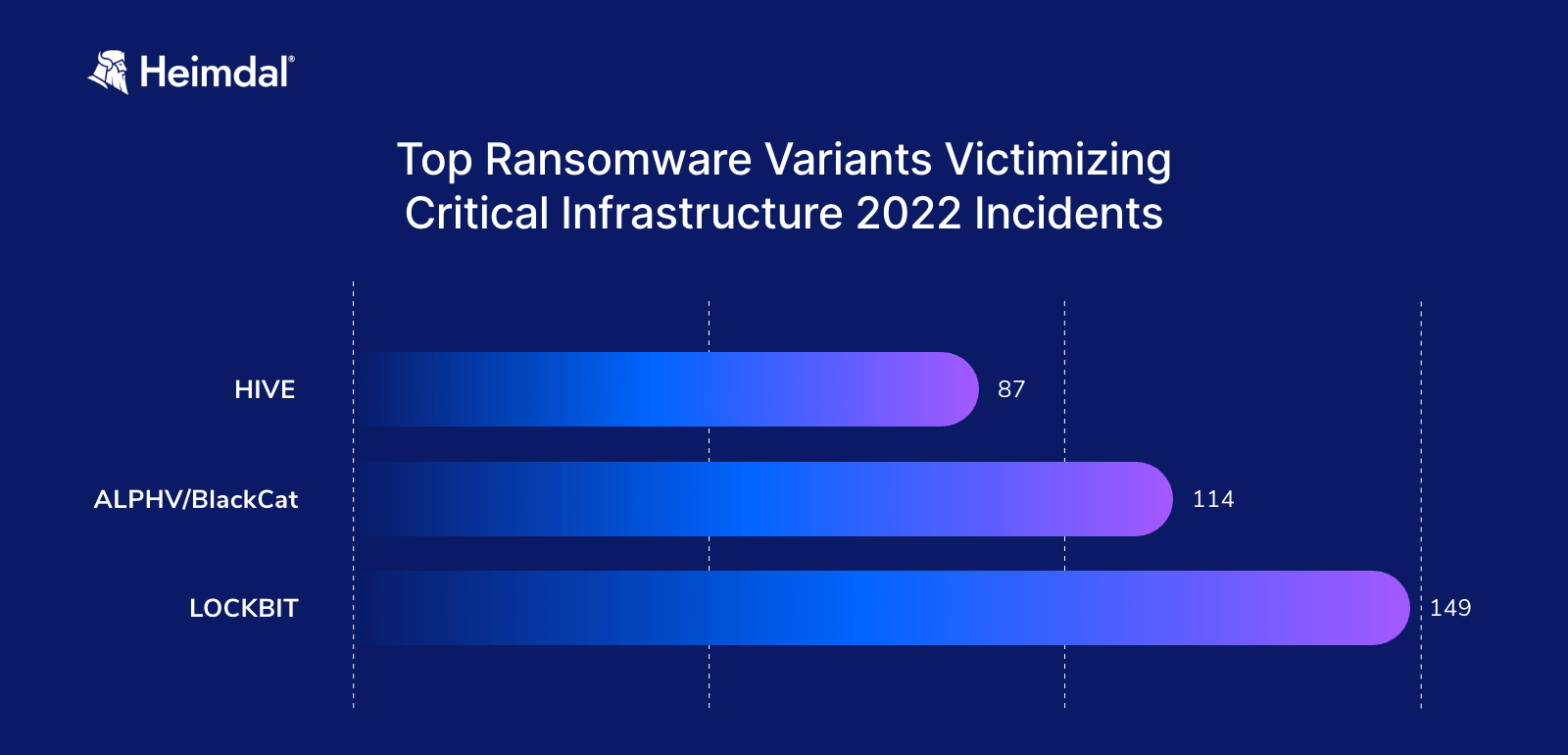
Top Ransomware Variants Victimizing Critical Infrastructure 2022 Incidents (FBI Internet Crime Report, 2022)
HIVE
Hive ransomware was first discovered in June 2021 and it’s an affiliate-based ransomware that cybercriminals use to target healthcare facilities, nonprofits, retailers, energy providers, and other sectors worldwide.
Although the FBI shut it down in January 2023, Hive has collected more than $100 million in ransom payments since it started its activity.
ALPHV/ BlackCat/ Noberus
ALPHV, also known as BlackCat or Noberus, is a ransomware-as-a-service that was initially detected in November 2021 and is designed to target organizations globally across various sectors, employing the triple-extortion technique.
In the “triple extortion” technique, the attackers first make a copy of the victim’s data before encrypting it on the victim’s machine.
BlackCat targets organizations in many industries around the world, but their most recent attacks targeted the healthcare, government, education, manufacturing, and hospitality sectors.
LockBit/ Abcd Virus
LockBit is a ransomware-as-a-service operation active since September 2019, when it was given the nickname “abcd virus.” The nickname was derived from the filename used to encrypt the data of the victim.
Lockbit typically uses the “double extortion” technique to coerce victims into paying twice: first, to regain access to their encrypted files, and then, to prevent their stolen data from being made public. LockBit usually targets mid-sized organizations.
Ransomware attacks can severely disrupt hospitals in particular because of the need for staff to resort to paper-based contingency measures in the absence of electronic health records and the need to reschedule surgeries.
According to a study by the United States Cybersecurity and Infrastructure Security Agency (CISA), hospitals in the United States that experienced a ransomware attack had significantly poorer health outcomes, including an increase in mortality rates.
2. Phishing Attacks
Phishing attacks are a type of social engineering attack where cybercriminals trick individuals into revealing sensitive information, such as usernames, passwords, and financial details, by posing as a trustworthy entity.
According to statistics, of the over 150 million phishing emails sent every day, 20 million arrive in inboxes, 10 million are opened, and 1 million are clicked, resulting in 100,000 people sharing their personal information each day.
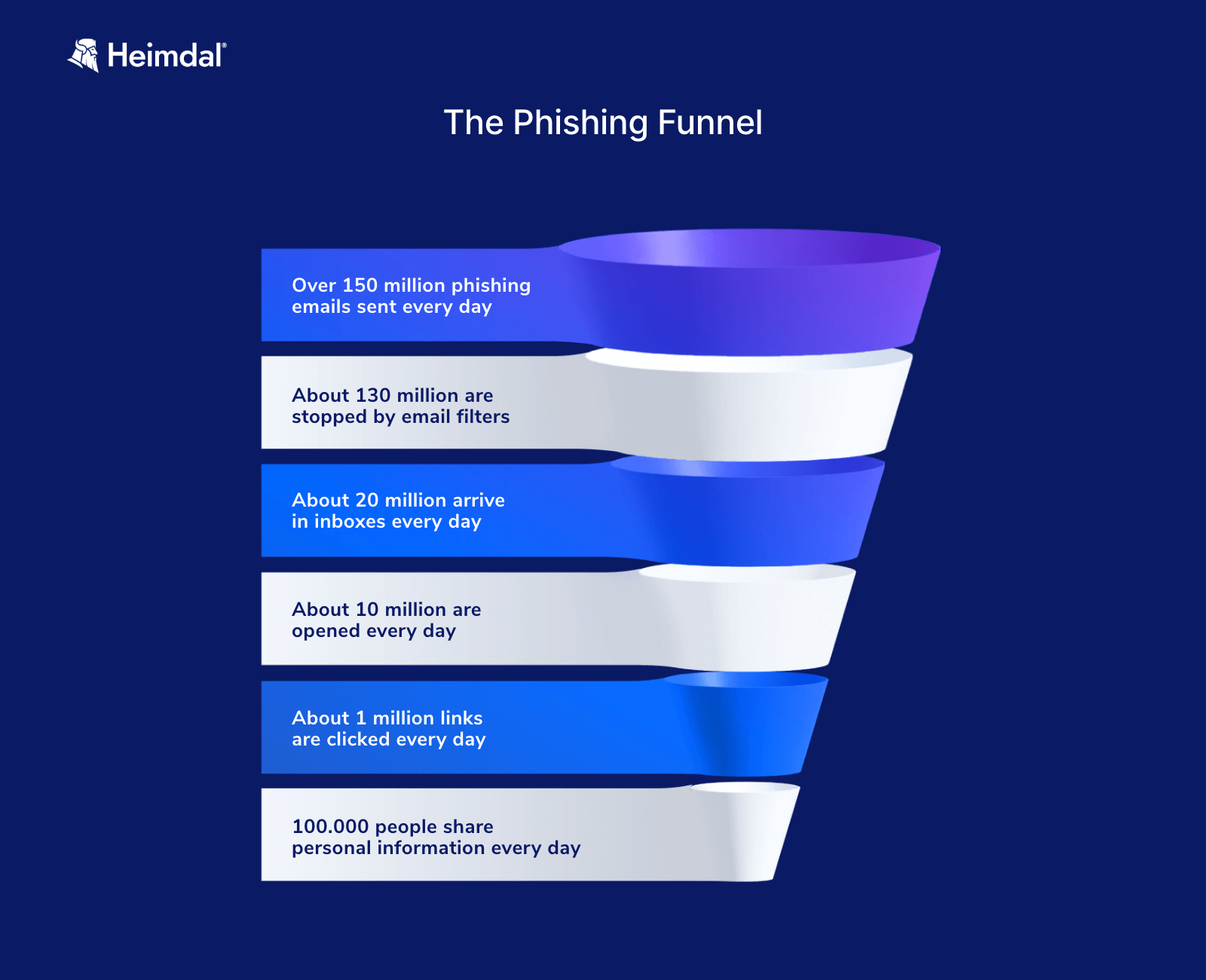
The Phishing Funnel (HIPAA Journal, 2018)
Phishing attacks on the healthcare industry primarily occur through email, though incidents via social media and malvertising (‘the use of online advertising to spread malware’) have been reported.
These attacks appear genuine and instruct employees to click on a link, leading to a webpage where they are prompted to perform an action that triggers malware download or disclose their login credentials.
The downloaded malware may not necessarily be ransomware; it could include surveillance software like adware or keystroke loggers, tracking employees’ online activities, and capturing usernames and passwords.
Other malicious software can establish remote gateways for threat actors to infiltrate an organization’s network. If a phishing attempt successfully acquires a username and password, the malicious actor gains immediate access to PHI (protected health information).
Also, an important subcategory of phishing is Business Email Compromise (BEC), in which the goal is to get access to legitimate email accounts and then use them to send convincing phishing emails. The FBI has labeled BEC attacks as the “$26 billion scam.”
3. Insider Threats
Insider threats refer to cybersecurity incidents caused by individuals with authorized access to systems or data, such as employees, contractors, or partners.
Insider threats can be unintentional (such as accidental data breaches), or malicious (where individuals intentionally misuse their access for personal gain or harm).
Regular cybersecurity training for employees is important to make them more alert and reduce potential risks. Additionally, some companies enforce strict consequences, such as warnings and job loss, for employees who fail to prioritize cybersecurity, underlining the seriousness and importance of maintaining a strong security culture within the organization.
Insider threats with negligent intent are more frequent, even though most businesses spend more money on insider threats with malicious intent. According to Ponemon’s 2022 Insider Threats Report, employee inadvertent or accidental behavior is the primary cause of 57% of data breaches involving an insider.
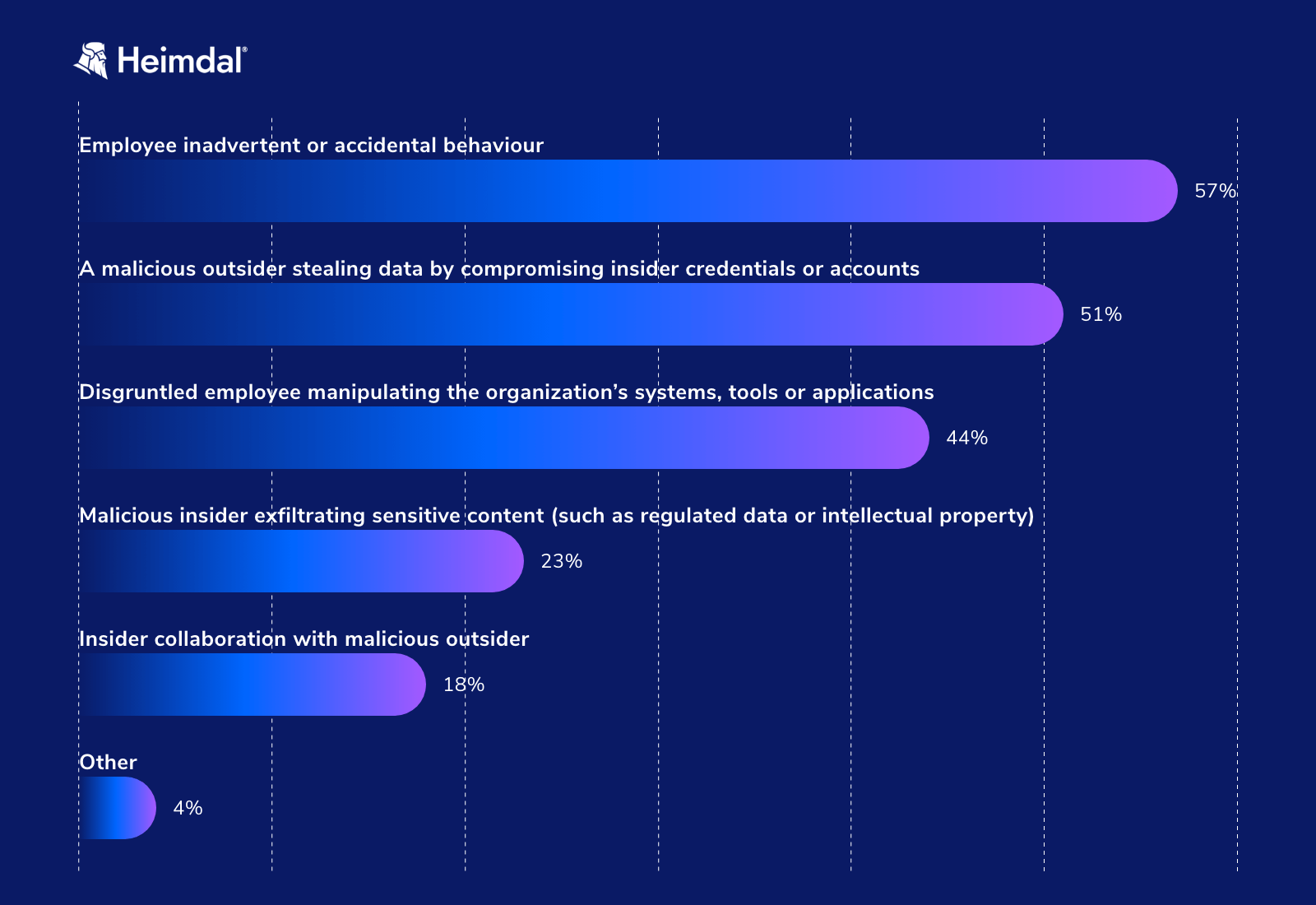
The Cost of Insider Threat (Ponemon Institute, 2022)
Factors such as human error, lack of awareness, and insufficient training in cybersecurity practices could be the cause of employee accidental behavior.
It’s important to understand this risk because employees have access to sensitive patient data and can inadvertently compromise it through actions like clicking on phishing emails, mishandling data, or falling victim to social engineering attacks.
By recognizing insider threats, healthcare organizations can implement training programs, policies, and technical safeguards to educate and empower employees, ultimately reducing the likelihood of breaches.
4. Distributed Denial of Service (DDoS) Attacks
DDoS attacks involve overwhelming a system or network with a flood of traffic, causing it to become unavailable or slow down. Healthcare institutions can be targeted with DDoS attacks, causing major issues: disrupting critical services, causing operational downtime, and affecting patient care.
Many DDoS attacks target victims for a social, political, ideological, or financial cause associated with a situation that enrages the cyber threat actors, though some are opportunistic or even unintentional.
In 2022, the notorious hacking group known as Killnet targeted healthcare, as well as Western government, education, and financial institutions. Killnet has been a vocal supporter of Russia’s war in Ukraine, using DDoS attacks as its primary weapon to cause havoc in Western countries.
Since February 2022, Killnet has frequently targeted both state-owned and private websites and networks in countries that have assisted Ukraine or supported sanctions against Russia.
The collective targeted both US and EU organizations such as various US government websites, the National Geospatial-Intelligence Agency, US tax resources, airports, a major US bank – JPMorgan Chase and the European Parliament, the Romanian Ministry of Defense, Border Police, the Italian State Police, and several Polish and German websites.
The Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) published an advisory to help governments and organizations respond effectively to DDoS attacks, particularly those launched by hacker groups like Killnet.
In an analyst note, The Health Sector Cybersecurity Coordination Center (HC3) also examined the cybergroup’s offensive from December 2022 to March 2023 and offered recommendations for how healthcare organizations can more effectively defend themselves.
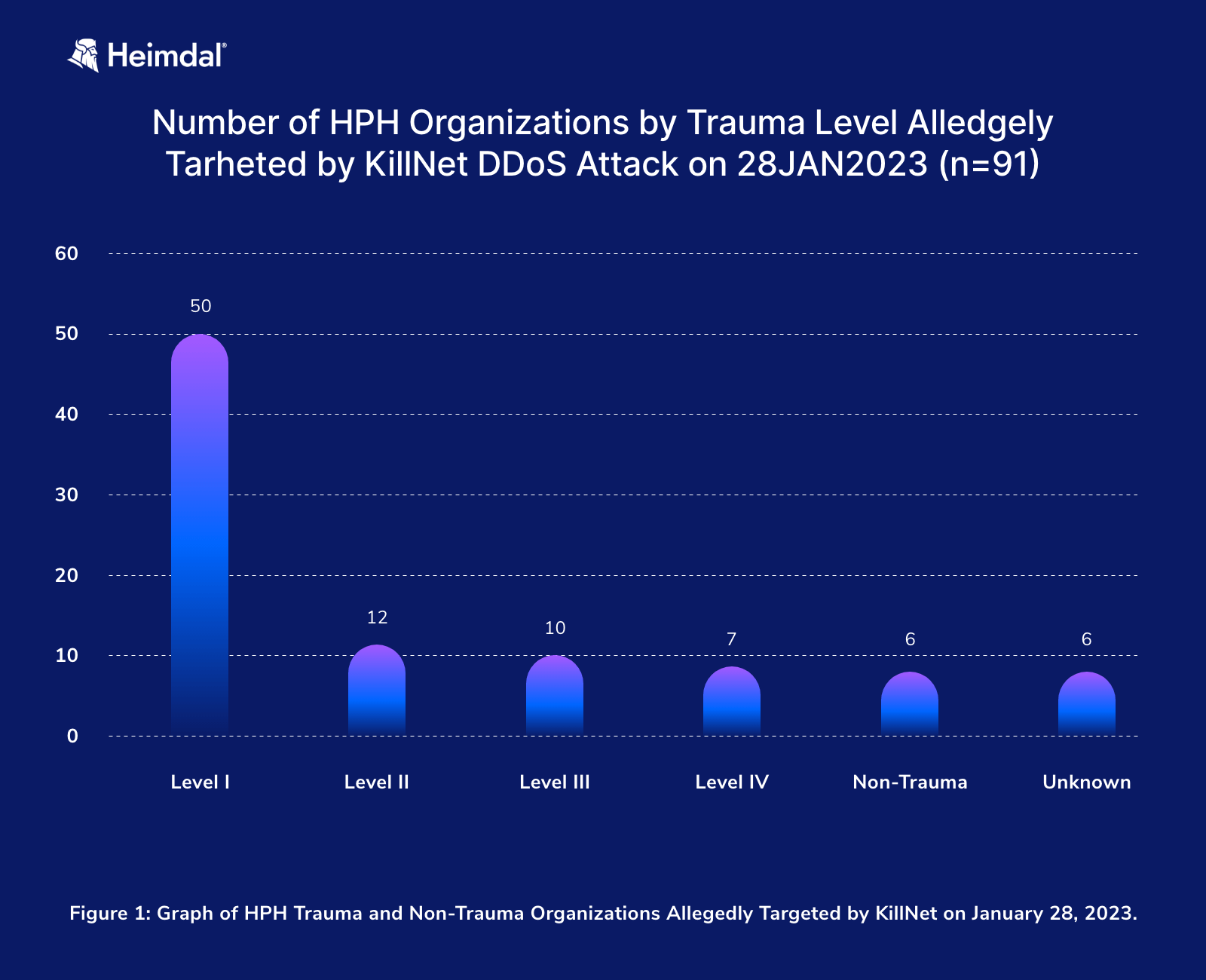
Figure 1 Graph of HPH Trauma and Non-Trauma Organizations Allegedly Targeted by KillNet on January 28, 2023 (HC3 Analyst Note, 2023)
In late January 2023 over 90 coordinated DDoS attacks targeted US healthcare systems, including multiple hospitals with Level I trauma centers, which offer comprehensive care to critically ill or injured patients.
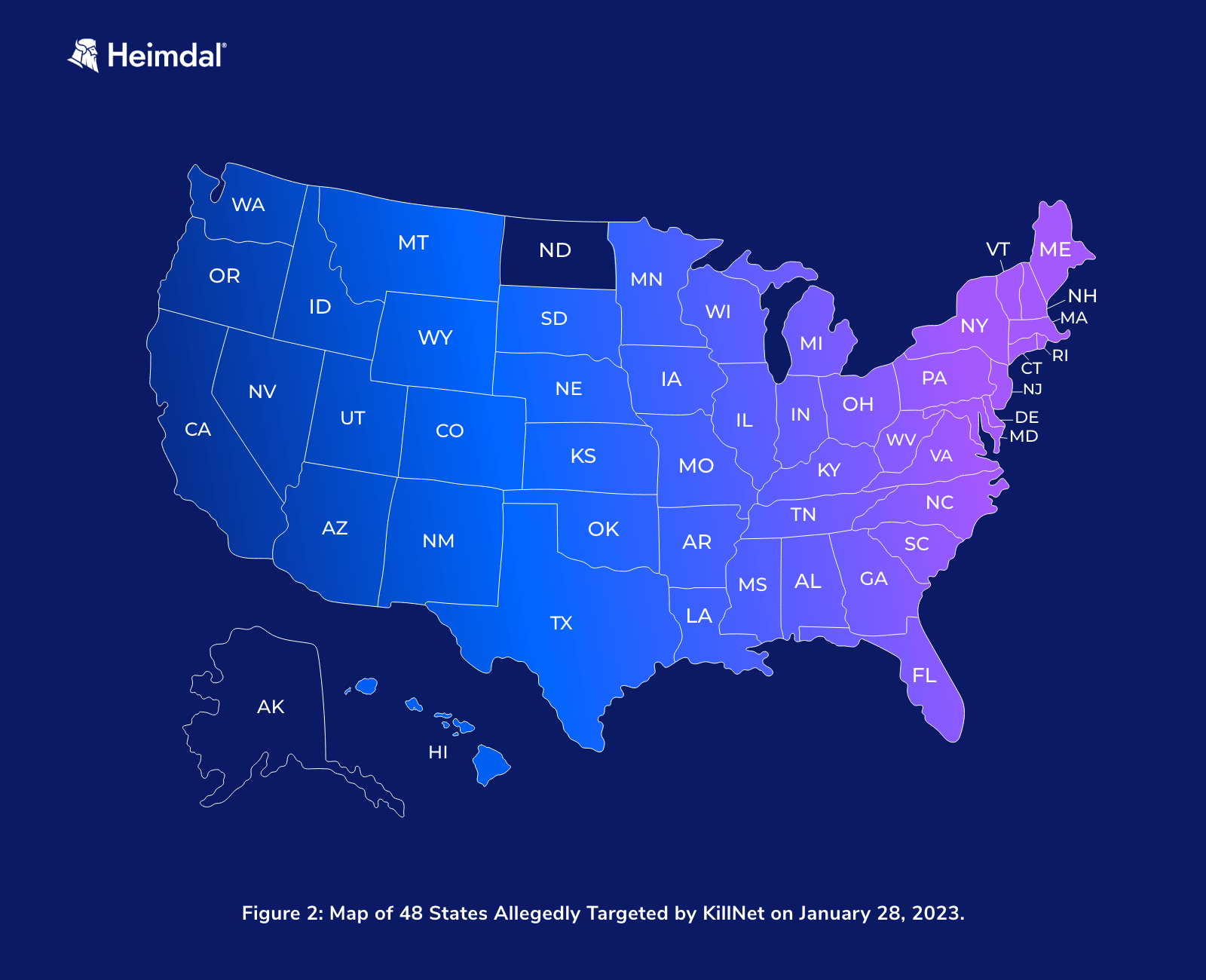
Figure 2 Map of 48 U.S. States Allegedly Targeted by KillNet on January 28, 2023 (HC3 Analyst Note, 2023)
As shown in the graph above, 48 out of 50 states were targeted by the Killnet in the January DDoS attacks.
Healthcare organizations can better prioritize the implementation of appropriate security measures, respond to potential operational disruptions, and protect patient care and data if they have a thorough understanding of DDoS attacks.
5. Malware attacks
Malware is a general term used to describe all kinds of malicious software. There are multiple types of malware like trojan horses, worms, keyloggers, adware, and spyware.
Many threat actors use malware to:
- monitor the victim’s online activity,
- destroy data,
- steal sensitive information,
- slow down a system,
- take control of a device,
- or cause internal errors.
According to Statista the worldwide number of malware attacks reached 5.5 billion in 2022, an increase of two percent compared to the preceding year.
Malware poses a significant threat to healthcare systems for several reasons:
Firstly, healthcare institutions store and handle vast amounts of sensitive patient data, including personal health information and financial records. Malware, such as info stealers, can be used to gain unauthorized access to these databases, leading to data breaches and the potential compromise of patient privacy. This can result in identity theft, fraud, and other forms of financial and personal harm to patients.
Secondly, malware can disrupt the operations of healthcare systems, leading to significant downtime and the potential for disruptions in patient care. For example, ransomware deploys malware to encrypt critical data and systems, rendering them inaccessible until a ransom is paid.
Moreover, systems often rely on interconnected devices and networks, creating opportunities for malware to spread rapidly. Once inside a network, malware can move laterally, infecting multiple devices and systems, and potentially impacting the entire infrastructure.
6. Supply Chain Attacks
In the last few years, supply chain attacks have become one of the biggest problems in cybersecurity. Gartner says 45% of global organizations will be affected by a supply chain attack by 2025.
Supply chain attacks involve exploiting vulnerabilities in third-party software or services used by healthcare institutions. Cybercriminals may target software vendors, equipment manufacturers, or other service providers to gain unauthorized access to healthcare systems or data.
Supply chain attacks can result in data breaches, malware infections, and operational disruption.
Since healthcare vendors are a much less secure part of the supply chain, cybercriminals have increasingly targeted them, and many of the largest healthcare data breaches reported in 2022 involved vendors.
In fact, according to a recent report by Black Kite Cyber Risk Intelligence, the healthcare industry was the most common victim of third-party breaches in 2022, accounting for nearly 35% of all incidents — up from 33% in 2021. Moreover, for the third year in a row, software publishers were the most common source of third-party breaches, accounting for 23% of all incidents.
Now more than ever, healthcare organizations need to be particularly vigilant in managing third-party risks and the ongoing challenge of securing software publishers, which continue to be a prominent source of data breaches.
How Can Heimdal® Help Prevent Cyberattacks?
Like many other organizations, healthcare organizations are struggling with limited budgets and resources during the 2023 global financial crisis. They must reduce cyber risks while maintaining costs to meet the best-case scenario of budget stability.
In most cases, healthcare businesses must do more with less. Healthcare institutions must use automation to boost cybersecurity and optimize IT Security operations while reducing security risks.
We help healthcare institutions worldwide with AI-enhanced, revolutionary endpoint security solutions that prevent, detect, hunt, and respond to the most sophisticated cyber threats.

- Next-gen Antivirus & Firewall which stops known threats;
- DNS traffic filter which stops unknown threats;
- Automatic patches for your software and apps with no interruptions;
- Privileged Access Management and Application Control, all in one unified dashboard
Wrap up
Cybersecurity in healthcare isn’t just a tech issue; it’s a patient safety matter. With threats like ransomware, phishing, and DDoS attacks becoming more common, healthcare organizations are in a constant scramble to guard against these digital threats.
As geopolitical strains add to the tension and hacking tools become more user-friendly, healthcare providers must be diligent and proactive. Now is the time to step up the game, putting in place stronger defenses to ensure that patient care and data remain safe.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










