Contents:
Even though companies now understand the necessity of cybersecurity in the face of ransomware attacks, and started to take it more seriously, CISO Benchmark Survey named this malware number one in their list of initiatives for 2022.
Triple extortion ransomware represents an evolution in cybercriminal tactics, signaling an alarming escalation from previous ransomware strategies. This comprehensive update for 2024 delves into the mechanics, implications, and protective measures associated with this sophisticated threat.
What is Triple Extortion Ransomware?
After completing the encryption of data, the attacker presents their ransom demand to the victim. Initially, the organization could leverage the encrypted and stolen data to demand a ransom. However, attackers using triple extortion ransomware tactics increase their threats by introducing a third layer of extortion. This could involve:
- DDoS Attacks: In triple extortion scenarios, attackers might add a ransom demand specifically tied to distributed denial of service (DDoS) attacks. They threaten to either initiate or continue a DDoS attack unless a ransom is paid.
- Third-Party Attacks: Additionally, ransomware attackers might target third parties connected to the affected business, such as customers, stakeholders, or partners, demanding ransoms from them as well.
How Triple Extortion Ransomware Works
In addition to data encryption (the first layer), and the threat of leaking important data (the second layer), the cybercriminal can add another tactic of his choosing (the third layer).
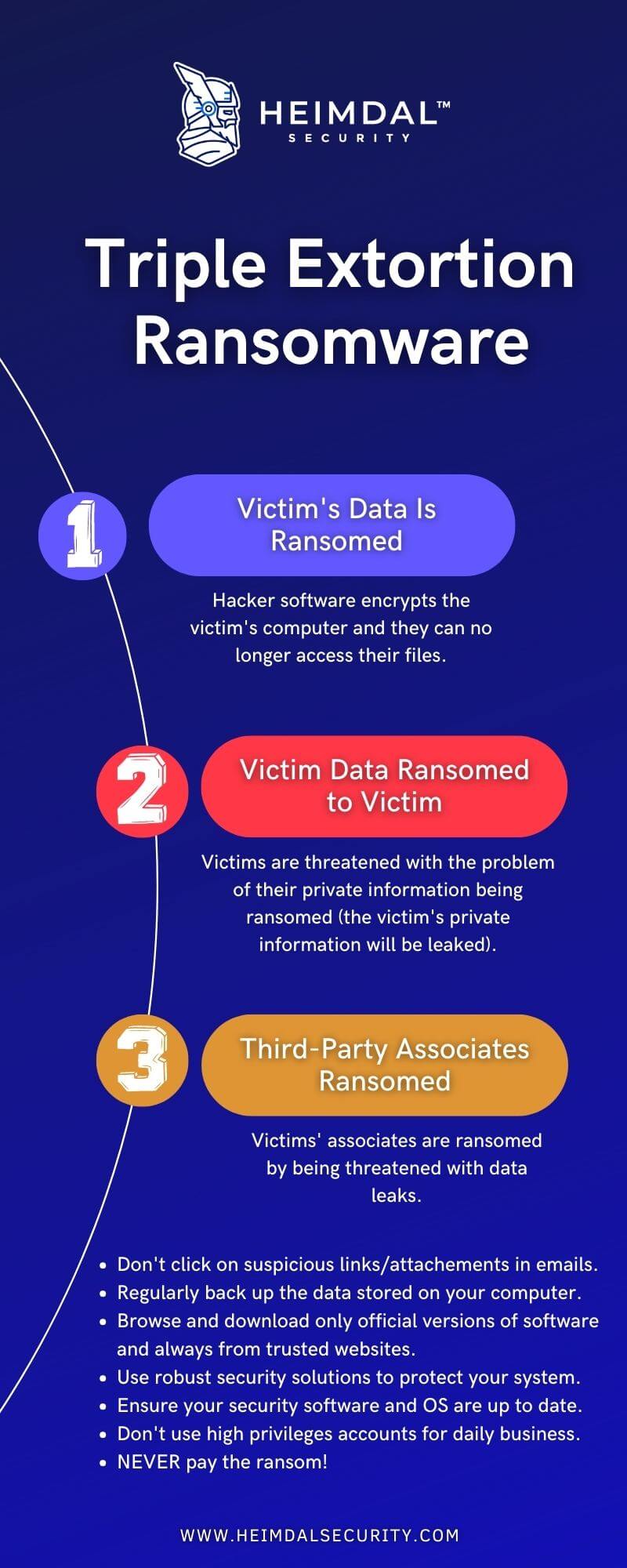
The most common tactics are going after the victim’s clients, partners, affiliates, patients, associates, suppliers, etc. with ransom demands so their data will not be leaked, launching an additional Distributed Denial of Service attack (DDoS) over the target, or making phone calls to persuade them.
But here is where the criminal inventiveness is free, and we even have records of a case in which a company’s printers were highjacked. The hacker then ceaselessly printed ransom notes as a strategy to make them pay.
The first triple extortion ransomware took place in October 2020, targeting Vastaamo, a Finnish psychotherapy clinic. After breaching the clinic’s network and encrypting data, the cybercriminals reached the patients with ransom demands. The patients were threatened that information about their therapy sessions would be made public if they fail to pay.
As ransomware technologies and strategies adapt and transform, modern attacks can become a ransomware chain that does not have to end, reaching further and further to a link of victims.
The Numbers Are Up
Researchers show that the number of ransomware attacks is increasing year after year.
Only in 2021, the number of breaches increased by 518% compared to 2020, and the value of ransom transactions rose by 82% in the same period of time, according to Unit 42.
This translates into the fact that the average ransom asked by malicious actors was $50m in 2021, but it reached this height from an average of $847,000 in 2020.
The average payment for a ransomware attack in 2021 was $570,000, compared to $312,000 in 2020, which was already 171% more than in 2019. This indicates that a trend is already emerging.
Who Are the Victims?
The most obvious targets for triple extortion ransomware are companies and organizations that hold important customer data. As the ransomware gangs are researching thoroughly a target before launching an attack, the possibility of further extending the siege to one’s clients is appealing to them.
In this category of favorite preys fall: healthcare organizations, government entities, and large private firms.
But any organization that can be in any way linked to a valuable victim is not safe and may get attacked. A good example is the REvil ransomware attack over Quanta, a Taiwanese manufacturer of electronics. When Quanta refused to pay the ransom, the cybercriminal gang turned its attention to one of the company’s clients, Apple, who was pressured to pay in order to avoid having leaked its confidential data.
And let’s also acknowledge the reputational damage that such an incident can cause to a company from any sector. A data breach converts a legitimate business into a dangerous partner.
How to Prevent Triple Extortion Ransomware Attacks
It is as important to have a plan in case of an attack, as it is to prevent one. Once the cybercriminal infiltrates your network, we know now that the extent of the attack, the tactics used, and the damage done to you and your partners can not be foreseen.
Businesses should not just focus on responding to breaches, but also take proactive measures to protect networks and endpoints.
Here are some measures you can adopt to stay safe in the case of a triple extortion ransomware attack, or other types of ransomware attacks:
- A regular backup of your data on a secure server will help you recover and resume activity a lot faster.
- Update your security tools and software so you can have the best protection offered by them.
- Use encryption in your favor. By encrypting sensitive information, exposed data will not be readable even if they are leaked.
- Don’t forget about the human factor and invest in educating your employees. With the majority of ransomware attacks using phishing, a well-prepared team can make the difference.
- The endpoint is where a large part of cyber incidents happen, so make sure you make endpoint protection a priority.
- Do regular scans for vulnerabilities in your network and patch them as soon as possible, as well as monitor your network for any unusual activity.
- Access to sensitive data should be very carefully granted only to certain users, and good password management should follow it.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
How Can Heimdal® Help?
Installing a good anti-ransomware solution could save you a lot of time and money. Heimdal® is offering its customers an outstanding integrated cybersecurity suite including the Ransomware Encryption Protection module, that is universally compatible with any antivirus solution, and is 100% signature-free, ensuring superior detection and remediation of any type of ransomware, whether fileless or file-based (including the most recent ones like LockFile).
There are a few easy steps we can take to prevent ransomware. Cybercriminals can affect your data and security to the extent that you allow them to.
For additional details on how to avoid ransomware, feel free to check out my colleague’s article on how to prevent ransomware.
Wrapping Up…
Losing money in the case of a successful ransomware attack is most likely, as any organization, even if it can recover its data from backup, fears having internal data and partners’ information exposed.
This makes this type of malware very profitable for cybercriminals who feel encouraged to invest in developing new features for their attacks.
In the face of continuous change and evolution of ransomware threats, prevention by implementing a series of measures and technologies is the best tactic.
If you liked this article, make sure you follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









