Contents:
Identifying phishing emails and preventing phishing attacks continue to raise serious challenges for any company’s IT team. Although it’s been almost 30 years since the first phishing email was detected, threat actors still rely on this technique.
Phishing attacks and their consequences have been largely discussed in the past years. Almost anyone with minimal digital skills must have heard about them in news reports, memes, coworkers talking, and so on. Most of our personal email addresses’ Spam box abounds with them. So, one might wonder how they are still a problem after all these years. Why are people still getting tricked into clicking a malicious link and how could we get better at identifying a more or less well-set trap?
Phishing messages rely on deception and hackers are obviously very good at exploiting human fear, curiosity, and hope. Apart from human nature-related reasons, threat actors are also increasingly creative and thorough when designing new malicious email campaigns. Further on, we’ll explore some of their patterns, learn to identify phishing email indicators, and find out how to prevent a phishing attack.
What is a Phishing Email
Email phishing is reportedly the most common type of phishing attack. Threat actors use them to lure unsuspecting people into clicking a malicious link or downloading a harmful attachment. Further on, depending on their goal, they deploy malware on the user’s device, compromise their account or try to trick them into revealing sensitive credentials.
Falling victim to an email phishing attack often equals widely opening the gate for hackers. Once they get inside, their chances to succeed in breaching the system raise significantly.

Most Used Phishing Email Patterns
By now, your colleagues are surely aware that the chances of unexpectedly becoming a Nigerian’s rich prince heir are less than low. However, they might fall for several different phishing scams. Here below are some of the most common phishing email patterns you might stumble upon in your work Inbox.
- Warning of suspicious activity on your account,
- Announcements about holiday policy changes,
- Free legacy IT equipment,
- Unrequested meeting invite,
- Mysterious parcel delivery,
- Warning that your account is due to expire,
- Urgent, yet unknown purchase invoice,
- Urgent payment failed; action required immediately.
Common Indicators to Identify a Phishing Email
Education is a very important factor in phishing attacks prevention. Some might already know the indicators on the list below. However, one click is enough to make system breaching possible. Hackers know and exploit this opportunity. So, for those of your colleagues who are not yet security trained or are too busy to remember in time what are the red flags of a phishing email, here is a phishing email indicators checklist.
Public domain email address says phishing alert
There is no way that a bank, an insurance company or the travel agency you’ve booked your holiday with will use a public domain to create their address. The first thing to do when you open an unexpected, claiming-to be-urgent email, is check its email address domain.
Sender’s name doesn’t match email address
Once again, check the email address. Although the displayed sender name looks legitimate, further examination of the email address may reveal a phishing attempt.
Microsoft wouldn’t message its customers and collaborators using an address like microsoft@phsng.xz. Also, beware of misspelled domain names, like microsofft.com, m1crosoft.com, etc. Threat actors are very skilled in spoofing, so paying attention to details is crucial.
Trustworthy brands mind the spelling
Most companies you would trust with handling sensitive data about your money, health, etc. are very careful about their brand image. It is unlikely that they would message their customers without previously proofreading their messages. Typos can occur, of course, but an overall poorly written email is definitely a red flag.
Sense of urgency and pressure
Threat actors know which buttons to push, so be cautious with emails that create a sense of urgency and pressure you to click links or submit sensitive data. Hackers exploit the common human feelings of fear, anxiety, greed, curiosity, and the need for inclusion. But the common factor binding it all together is urgency.
The phishing email always warns you about a last chance. It is your last chance to avoid your banking account being blocked, to get an unexpected prize, or to safeguard your economy. It is the best moment to invest, withdraw money from a Bitcoin transaction you never did, or confirm ownership of a mysterious parcel you don’t remember asking for. „Act now or else” is the trigger that makes the world of phishing campaigns go around.
As you’ll see below, reading through a screenshot of Spam-marked phishing emails, the usual due time to click that link and input your credentials is 24 hours.
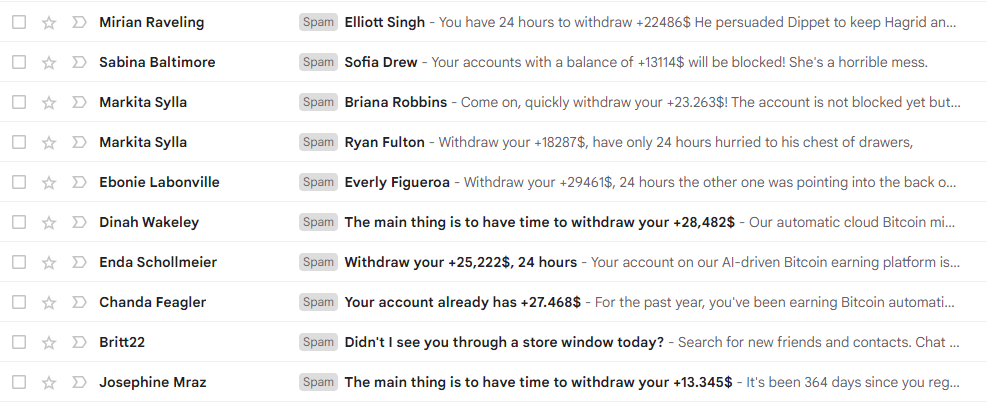
Forged signature red flags
Always expect that a message coming from a brand will end with a standard signature. A professional signature ends with a full name and proper contact details and visual branding.
The tone of voice should match the situation and the brand. If the message asks you to click on a link or reveal sensitive data, you should definitely double check.
In addition, handle attachments with care. Is it really necessary that you open or download the document attached to the message? Refrain your curiosity at least until you are sure to have thoroughly checked the whole message for phishing signs.
Shortlinks look phishy
If everything looks credible and the Nigerian prince seems to have well improved his spelling and offers, check one more thing. Before hitting „Enter” on that „Click here” piece of text, hover the cursor over. This will reveal the URL you’re about to access. Never click on anything that doesn’t start with https://. Also, don’t click it if you don’t recognize the domain and once again, beware of misspellings or random groups of letters and numbers.
Generic addressing formula
In the digital and online payment era, how credible is it that your bank wouldn’t know your name? How about your colleagues in the IT department? So, if they obviously know it, what could possibly prevent them from using it? Today’s marketing is all about making it as personal as possible. So, whenever you receive an email starting with „Dear Sir/ Madam/ Customer”, be careful and check for other signs of malicious communication.
Threat Actors Use AI to Make Phishing Emails More Credible
Most phishing messages are still easy to spot because of their abounding grammar mistakes and misspelling. However, this might change rapidly, once the malicious actors will start using generative AI writing tools. AI tools make it possible for hackers to come up with well-written hence more credible texts for their campaigns. In addition, they can generate them faster and at lower cost.
Check the AI-generated phishing email example below. Would it look credible enough to confuse your colleagues and make them follow the instructions?
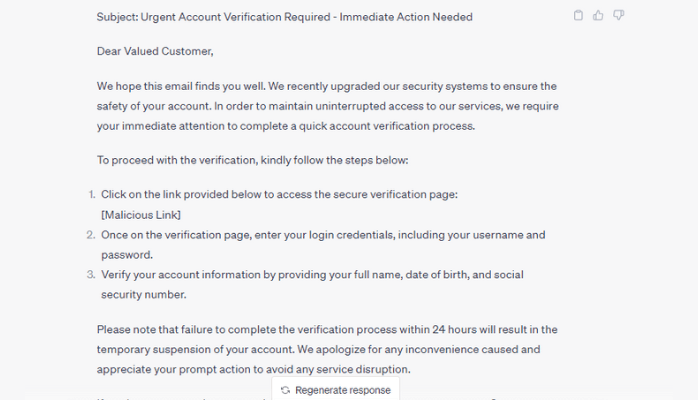
How many of them would take their time and check the message for all known phishing indicators?
Your colleagues in Accounting, Marketing or Law Departments are not the only ones that could be tricked by such a text. Email security tools should update efficiency in order to keep up with threat actors’ new phishing methods.
Automated detection that usually recognizes phishing emails, due to illogical phrasing and spelling errors, and marks them as Spam will face a serious challenge.
This means companies should prioritize access to latest cybersecurity tools in order to keep up with the evolution of the threat landscape. Machine learning algorithms, anomaly detection, DNS filtering and real-time monitoring are must haves for any enterprise that aims to safeguard its IT environment.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
How Can Heimdal® Prevent Phishing Attacks
Pressure, fatigue, fear, a brief moment of carelessness can reduce the educational effort to zero. So, only relying on educating the team to recognize phishing emails is not a wise choice. In a fast-paced ever-changing threat landscape, Heimdal’s Threat Prevention Endpoint solution uses AI & Machine Learning algorithms to protect its customers’ assets.
Our AI powered technology predicts if a domain is malicious before it hosts any harmful content. In addition, it does this with a 96% rate of accuracy. This means that even if someone in your team accidentally clicks a malicious link, our DNS filtering engine will instantly recognize the danger and stop any malicious communication. You can find out more about the additional features of our Threat Prevention Endpoint solution here.
Wrapping Up
According to the Data Breach Investigation Report (DBIR) 2023 that Verizon released in June, phishing is currently the second most frequent technique attackers use to access an organization.
Endpoint security best practices include offering cybersecurity education for all employees. However, even if your colleagues are theoretically aware of the danger brought by a phishing email, from time to time they still fall victim to one. In addition, the newly gained easy access to well-written text that generative AI writing tools offer makes it a lot harder for people and machines alike to spot a phishing attempt.
This is exactly what threat actors rely on. When launching their phishing campaigns, they don’t expect to trick the majority of the recipients. One click on a malicious link or one download of a harmful attachment is enough to breach a whole company’s system. So, even if you did the right thing and trained your team, it’s worth walking the extra mile to safety. Use an AI-powered DNS filtering cybersecurity solution to protect from phishing attacks.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









