Contents:
What Is Spoofing?
Spoofing is a type of cyberattack that involves assuming a false identity and manipulating a victim into disclosing sensitive information or granting access to their device. Cybercriminals win a victim’s trust by claiming to be a trustworthy individual or company in order to steal their data or obtain access to their equipment.
They accomplish this by changing their caller ID or email address. As part of various types of spoofing, threat actors make replicas of legitimate websites, conceal their IP addresses, and even broadcast false GPS signals.
How Does Spoofing Work?
Spoofing attacks occur when an attacker successfully impersonates a system’s authorized user. They are distinct from counterfeiting and sniffing attacks, despite the fact that they are all falsification attacks. When an attacker forges RFID (Radio-Frequency Identification) tags that can be scanned by authorized readers, this is known as counterfeiting. Sniffing occurs when an attacker creates fake authorized readers that can read the approved tags and extract relevant data. The forging object of spoofing, on the other hand, is an authorized user of a system.
As Michael Gregg points out in “Hack the Stack”, there are two types of spoofing attacks. The first is local spoofing, which occurs when the attacker and the victim are on the same network. This is by far the easiest of the two sorts of spoofing attacks we’ll explore. The attacker has the ability to sniff network traffic and so gain access to essential pieces of information needed to carry out the attack. While some of the techniques used to launch this type of assault take place at the transport layer, it’s vital to remember that attackers will corrupt the data stream, spoof addresses, and try to inject sequence numbers into packets to acquire control of the communication session.
Blind spoofing is the second method through which this attack can be carried out. This is a far more advanced and sophisticated attack. The attacker is not on the same local subnet when the assault is initiated this way. This means that many of the bits of information needed by the attacker to succeed aren’t available. These crucial parameters must be estimated. Because most modern operating systems employ very random sequence numbers, this type of attack is difficult to carry out. The apex of these attacks has passed, yet they are still viable to launch.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
Types of Spoofing
Spoofing comes in a variety of forms, each with its own approach and aim.
DNS Spoofing
Domain spoofing involves impersonating the domain of a well-known website. Unfortunately, many businesses are unaware that it is a problem to be aware of, let alone recognize it when it occurs. Despite the fact that the number of domain spoofing assaults appears to be decreasing, there is no certainty that they will ever go away.
So, what happens when threat actors impersonate an organization’s domain? The company’s clients are duped into providing personal information on a fake website, putting their digital privacy and security at risk.
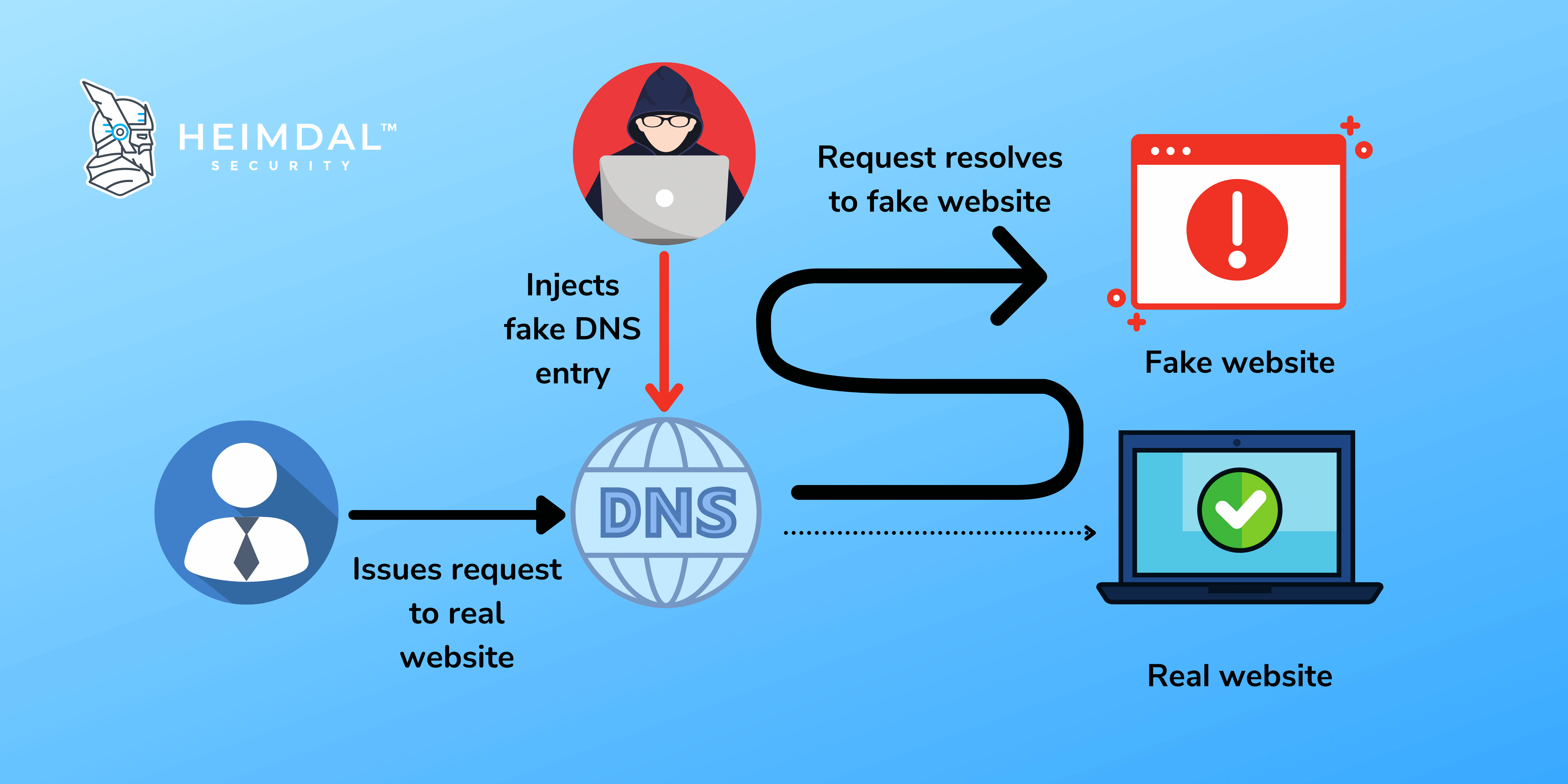
A DNS spoofing attack can be carried out in a variety of ways, including:
- Interception of communications between users and a DNS server in order to redirect users to a different/malicious IP address is known as Man-in-the-Middle (MITM).
- DNS server compromise – When a DNS server is configured to return a malicious IP address, it is directly hijacked.
A DNS filtering solution like our Heimdal™ Threat Prevention hunts, prevents, detects, and blocks threats at the traffic level. Traditional defenses don’t offer protection against DNS attacks. But thanks to its machine learning-driven DNS filtering system, Heimdal brings you full DNS protection and malware blocking.
Website Spoofing
This is a common type of spoofing attack that is generally used in conjunction with spoofed emails that provide links to the site. Designing a phony website that closely mimics a trusted or even well-known website is known as website spoofing. The majority of faked websites will have a login page where victims will be asked to submit their passwords or other sensitive data. Malware can also be distributed via spoofing websites. Spoofing a website can have serious ramifications for a company’s data privacy and integrity.
Email Spoofing
This is the most prevalent type of spoofing, in which victims are targeted by email. With an email address that closely resembles the original, the sender appears to be a reliable source. Adware, ransomware, Trojans, cryptojackers, and malware can all be distributed using spoof emails. While most users have refined their email usage to the point that they can spot a fake email address right away, faked emails are increasingly employing a variety of deceptive tactics. These could include closely resembling a well-known email domain or address with minor changes. Logos, iconography, and other trusted and recognized branding elements may also be used in the emails. Spoofed emails that are more targeted can include familiar messaging or an address that is directed to a particular person or a group of people.
There are rather obvious reasons for email spoofing. Typically, the threat actor has malicious intent, such as stealing a company’s proprietary data. The following are the most typical causes of malicious behavior:
- Phishing. Email spoofing is almost universally used as a phishing gateway. Impersonating someone the recipient knows is a trick to persuade them to click on dangerous links or give out personal information.
- Identity theft. Impersonating someone else can assist a threat actor in obtaining additional information about a victim (e.g. by asking for banking or medical information from the institutions concerned).
- Getting through spam filters. Spammers who swap email addresses frequently can escape being blacklisted.
- A phony email address is sometimes used to merely conceal the sender’s real identity.
Heimdal has created two email security products to combat both simple and sophisticated email threats: Heimdal Email Security, which detects and blocks malware, spam emails, malicious URLs, and phishing attacks, and Heimdal Email Fraud Prevention, a groundbreaking email protection system against employee impersonation, fraud attempts, and BEC in general.
IP Spoofing
IP Spoofing, which is commonly used in distributed denial of service (DDoS) attacks, is a pernicious attack that prevents malicious traffic from being removed while concealing the attacker’s location. Because the IP address of a device is frequently utilized in security systems to verify a user’s location, hackers can employ IP Spoofing to hide their identity and avoid detection even by advanced security systems.
Since IP spoofing is so difficult to detect, it is a serious threat to keep in mind. This is due to the fact that IP spoofing occurs prior to a hacker attempting to get access to a system or interacting with an unwitting victim.
Take into account the following consequences of this challenging detection:
- People are easily persuaded to give sensitive information to an unauthorized entity. While we’ve all been taught to search for phishing attack signs, an IP spoofing attack will display none of them. Instead, communications intended for a legitimate party will be forwarded to a hacker who has faked that person’s or device’s IP address.
- Allowing hackers to remain hidden for long periods of time. An attack on a protected system will typically raise a slew of alerts, and while the harm has already been done, security personnel can at least start to mitigate the effects. Because they are inside under the guise of a reputable source, IP spoofing enables hackers to gain access to systems without anybody noticing. As a result, they can do greater damage over a longer period of time before any form of repair is necessary.
- Shutting down systems by getting over firewalls and other barriers. On a bigger scale, IP spoofing allows several hackers to easily overcome firewalls and other security barriers in order to flood systems and create outages or completely shut down services. This strategy has the potential to cause massive devastation, especially given the large number of people involved.
ARP Spoofing
ARP (Address Resolution Protocol) is a collection of rules that links IP addresses to physical devices. ARP spoofing is the act of imitating this piece of data in order to get around security procedures such as antivirus software. Malicious actors can employ ARP Spoofing to link their computers to a genuine user’s IP address. If the user is an employee of an organization, attackers can acquire access to the network by obtaining his or her login credentials. Because the connection looks to be legal, the network’s security systems will be unable to detect the difference.
MAC Spoofing
Threat actors can alter or fake the MAC (Media Access Control) address by exploiting vulnerabilities in hardware drivers. This allows the attacker to make his device appear to be part of the target network, allowing him to evade all access restrictions. In essence, MAC Spoofing allows hackers to impersonate trustworthy users in order to commit frauds such as business email compromise (BEC), data compromise/theft, or malware distribution into previously safe environments.
Caller ID Spoofing
Have you ever received a call that you thought came from a reliable source but turned out to be spam? That’s exactly the definition of Caller ID Spoofing, a technique in which the phone call looks to come from a reliable source. Once you answer the phone, the attacker can utilize social engineering techniques, such as acting as a member of your bank’s customer service staff informing you of a crisis. The goal of Caller ID Spoofing attacks is usually to elicit important information from the user, such as financial information, passwords, Social Security numbers, and so on.
Mobile Spoofing
Mobile Spoofing is similar to Caller ID Spoofing in that threat actors send an SMS using someone else’s phone number or sender ID. The hacker is attempting to conceal his real identity by using an alphanumeric sender ID. The sender appears to be from a reputable/legitimate company or organization. Text Message spoofing is another term for mobile spoofing.
GPS Spoofing
Threat actors can use GPS spoofing to make it look as if they are at a specific area while they are actually somewhere else. Attackers frequently employ this type of spoofing to hide their true identity while committing more serious forms of cybercrime. GPS Spoofing can also be used to send commuters to the wrong locations by manipulating automobiles that use GPS input.
Spoofing Extensions
In this type of spoofing attack, the threat actor stores a file as an executable one that appears to be a simple text file to the untrained eye.
Malware that uses social engineering techniques is well-known for its ability to disguise itself as a non-obvious executable. Malicious attachments are provided in the form of specially created icons that look like legitimate document files. Furthermore, they frequently employ double extensions, such as “.pdf.exe” or “.doc.exe,” taking advantage of the fact that Windows hides the extension by default, making it difficult for users to tell which file is the one it claims to be.
They also use lesser-known executable format extensions, such as “.scr.”

Heimdal® Email Security
- Completely secure your infrastructure against email-delivered threats;
- Deep content scanning for malicious attachments and links;
- Block Phishing and man-in-the-email attacks;
- Complete email-based reporting for compliance & auditing requirements;
How to Stay Safe from Spoofing?
- Invest in cybersecurity software: Install anti-malware and anti-spam software to safeguard your device from dangerous threats and viruses.
- Only access websites that have a valid security certificate (https:// in the URL).
- Before you click on a URL, hover over it to make sure it’s going to a reliable source.
- To prevent fraudulent emails from reaching your inbox, use spam filters.
- Check the email sender’s email address for misspelled or otherwise inaccurate content before the email domain (the domain is the information following the @ symbol).
- Do not open attachments or click on links from unknown senders or unfamiliar domains. They generally contain malware or other infections that can seriously damage your device.
- When feasible, employ two-factor authentication with strong passwords.
- Update all apps, operating systems, browsers, network tools, and internal software on a regular basis to guarantee you have the most up-to-date and secure version.
- Use real-life examples to teach employees how to avoid becoming victims of social engineering.
You can file a complaint with the FCC’s Consumer Complaint Center if you believe you were a victim of a spoofing attack. If you’ve lost money due to spoofing, you can also inform your local police station. Check out our antivirus software to defend yourself from spoofing and secure your digital assets today.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










