Contents:
Even the most inexperienced computer user knows about the dangers that lurk on the Internet – one slip of the click can turn your machine into a (very) expensive paperweight. The only way to stay safe while doing some online surfing is to buy or try out a cybersecurity product: antivirus, antimalware, email security suits, password vaults, etc.
Does that mean your business will be completely safe? Unfortunately, the answer is no. Threat actors constantly come up with new malicious software. Modern malware is more virulent, aggressive, easier to deploy, better at evading detection techniques, and takes less time to develop.
Additionally, thanks to the RaaS (Ransomware-as-a-Service) ”business” model, malware became infinitely cheaper. In theory, anyone can get a ransomware kit for the price of a large coffee these days. Also, some RaaS kits are plug-and-play, meaning that the operator doesn’t even need to know basic hacking stuff such as coding.
To make a long story short, modern problems require modern solutions and this is where cyber threat hunting comes into play. In this article, we’re going to delve into the basics of threat-hunting such as methodologies, techniques, and intelligence sources.
Why Threat Hunting Is Important?
Cyber Threat Hunting is a crucial part of security operations center services which focuses on proactive threat-seeking and/or remediation. As a technical resource, threat-hunting is very useful in identifying the tell-tale signs of an impending cyber-attack or even rooting out malware that employs advanced evasion techniques.
Threat Hunting Intelligence Sources
Before getting into any specifics, we should clear up a couple of things.
First of all, threat hunting is not something you just pick up randomly. As a threat-hunting specialist, you need to know what to look for, where to look, how to look, figure out scenarios (and outcomes), and, of course, act. So, data collection and analysis should be up on every threat hunter`s list.
Here below are some of the most important sources a security team goes to before launching a threat hunt.
- IOCs – stands for Indicators of Compromise, which is evidence signaling a network and/or endpoint compromise. IOCs are used in digital forensics analysis. Unusual DNS requests, abnormal network traffic patterns, DDoS attacks, abnormal logins, unusual database reading activity, file tampering, callbacks to the same file, etc. are a few examples.
- IOAs – stands for Indicators of Attack and carry intent and motivation. An IOA is an evident set pointing towards an active network/endpoint attack. It is crucial to coaching next-generation threat-mitigation engines and solutions (e.g., IDS, IPS, next-gen firewalls, etc.). Examples include covert communication between internet-facing public servers and individual hosts, communication over non-standard ports, spikes in SMTP traffic, post-infection inter-host chatter, connection attempts from different geographic regions, and a suboptimal malware removal rate.
- TTPs – In order to maximize your results, you should spend some time familiarizing yourself with the way threat actors do or might act. The best way to go about this is to hop on MITRE’s official page and start researching TTPs. TTP stands for Tactics, Techniques, and Procedures. Studying these will totally upgrade your threat-hunting abilities. Take a look at NIST’s framework while filling out the MITRE ‘paperwork’; NIST and MITRE are two sides of the same coin. While MITRE offers you insights into the attack, NIST provides defensive actions or strategies, regardless of the kill-chain index or trajectory.
Now that we`ve talked about the main intelligence sources for threat hunting, let’s talk about how to actually get the job done.
Common Threat Hunting Techniques
We`ve talked about the main information sources for threat hunting and we`ve also pinned the three methodologies. So, let`s move on to acknowledging four of the most common threat-hunting techniques:
Searching
To use this technique, the first step is to establish clear search criteria. Then you can go on and query data for specific artifacts. Beware that if the search criteria are too broadly defined, you might end up with a huge pile of results. Most of them will not necessarily prove useful but instead will take a lot of time to process. Extremely strict criteria are also not recommended. A too-specific search might not generate enough results to permit relevant conclusions.
Cluster analysis
This statistical threat-hunting technique refers to sorting out groups (clusters) of similar information based on specific characteristics, from a huge set of data. Threat hunters usually rely on machine learning for this. They use AI search techniques to process large assortments of data, like log files. The result is a report that uses the parameters that have been set out. For a human being, it would be exhausting and complicated to navigate and sort out all that amount of data. Clustering is very useful in outlier detection because it can precisely spot aggregate behaviors.
Grouping
First of all, grouping is not the same thing as clustering. This technique involves taking a set of unique artifacts and checking the circumstances under which multiple of them appear together, related to specific criteria. Grouping can be considered a step that derives from clustering, since it uses an implicit set of search criteria against a data set that is already marked as suspicious.
The grouping technique is a big help when you are looking for multiple, related instances of unique artifacts.
Stack counting
In this case, the threat hunter goes through a data set of similar or equal values trying to find similarities within the information. Detecting an outlier for a particular metric gives the hunter a clue as to what could be producing the result.
When processing large or diverse data sets, stack counting is not very effective. You`ll definitely need to use a program – Excel might do – to sort and process data for finding similarities and anomalies within the dataset. Using filters saves the day: choose endpoints that cover similar functions, for example.
Checking outgoing traffic on a specific port, executed from a certain hostname, is one of the things you can use stacking for.
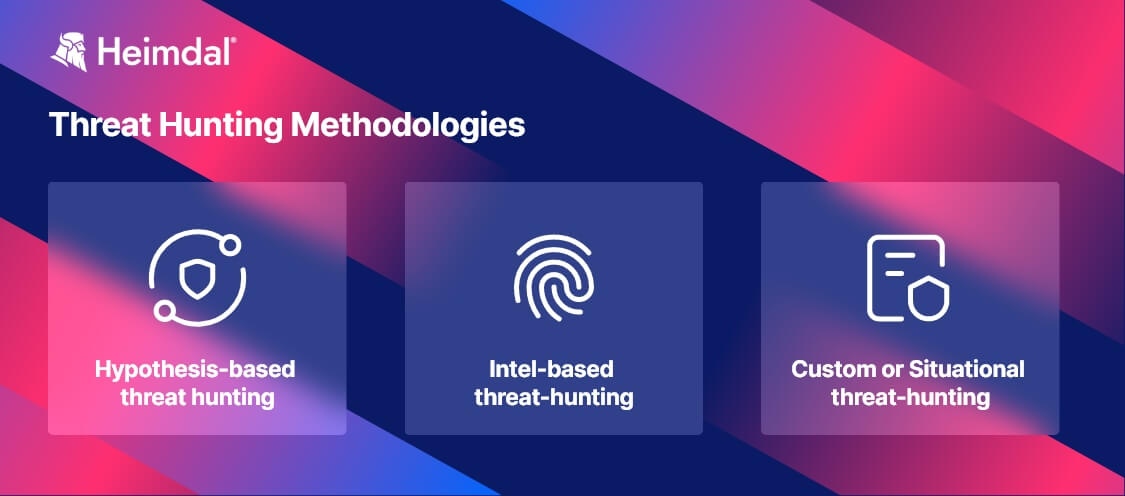
Threat Hunting Methodologies
According to the big book on threat-hunting, there are three major approaches: hypothesis-based, intelligence-based, and custom hunting.
Hypothesis-based threat hunting
This proactive methodology leverages a threat-hunting library and follows the MITRE ATT&CK framework. It starts as an educated opinion about the chances of a cyberattack to happen and serves as a trigger for the whole threat hunt process.
After the threat hunter elaborates on the hypothesis, the next step is to test it. This involves:
- collecting relevant data on security events, system logs, etc.
- analyzing the data to finally come up with a response strategy.
To come up with a hypothesis, threat hunters check recent threats and attack data, as well as insights into attackers’ tactics, techniques, and procedures (TTPs). Their goal is to find out whether such specific activities could be found across their company`s environment.
Intel-based threat-hunting
The Intel-based methodology analyzes threat intelligence sources and relies on using the Indicators of Compromise (IoCs) it finds. From then on, the search follows the guidelines provided by SIEM and threat intelligence. Once the team identifies an IoC-based issue, the threat hunter starts analyzing whatever malicious activities and data breaches that might have occurred. The Intel-based threat-hunting methodology is a reactive model. It also checks hash values, domain names, and IP addresses.
Custom or Situational threat-hunting
This threat-hunting methodology is impacted by situational awareness and industry specifics. The methods may vary depending on how the industry impacts the environment. The research team detects the anomalies using the SIEM and EDR tools.
Requirements received from customers, geopolitical issues, or targeted attacks are the foundation of custom threat-hunting. It has features from both intel- and hypothesis-based hunting methodologies and uses IoA and IoC data.
How Can Heimdal® Make Threat Hunting More Efficient
There is no doubt that the current hyperactive threatscape makes threat-hunting a critical task on any SOC team`s to-do list. Single-purpose, reactive products like antiviruses are no longer enough, no matter how performant they are. As a consequence, cybersecurity will switch more and more towards unification, both in terms of services and solutions.
Heimdal®’s unified platform takes threat-hunting to the very next level, by combining SOAR, SIEM, and XDR.
Designed to provide security professionals with an advanced threat-centric view of their IT landscape, the solution employs granular telemetry to enable swift decision-making. Built-in hunting, remediation, and actioning capabilities are all managed from the Heimdal Unified Security Platform.
The Heimdal® Threat-hunting and Action Center is a revolutionary unified platform that offers SecOps teams more clarity and speed of action. It helps reduce organizational risk and maintain compliance.
Besides, imagine being able to display security health in the boardroom with one dashboard!

- Granular telemetry across endpoints and networks.
- Equipped with built-in hunting and action capabilities.
- Pre-computed risk scores, indicators & detailed attack analysis.
- A single pane of glass for intelligence, hunting, and response.
Wrapping Up
Threat hunting is a both exciting and challenging component of cybersecurity and it can certainly no longer go overlooked.
A good threat hunter should have attention to details, creativity, lots of knowledge and experience in information technology and security best practices. All in one and at an extremely high speed.
The amount of data that need to be processed and the ever-growing list of new threats that malicious actors keep pushing are huge. Therefore, professional threat hunting without proper threat hunting tools is simply not effective.
So stand by your security team and bolster your environment`s defense with a smart and modern unified threat-hunting solution. Also, check the video below to find out what are 6 threat-hunting best practices.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







