Contents:
SOC as a Service (SOCaaS) is a security solution based on the Cybersecurity-as-a-service (CSaaS) model. A managed SOC provider operates and maintains a fully-managed SOC team, offering this service to organizations for a subscription.
If you are planning on adopting a SOCaaS solution, keep reading this article.
What you’ll find in this article.
- What is SOC as a Service (SOCaaS)?
- Security Operations Center Roles & Tasks.
- SOC-as-a-Service (SOCaaS) Benefits in Enterprise data security.
- SOCaaS Challenges.
- In-house SOC vs Soc as a service.
What is SOC as a Service (SOCaaS)?
A Security Operations Center (SOC) is tasked with identifying, countering, investigating, and responding to threats.
A Socaas provider all of the security operations tasks carried out by in-house SOC, such as.
- Network monitoring.
- Log management.
- Threat detection and intelligence.
- Incident investigation and response.
- Reporting.
- Risk.
- Compliance.
- Reviewing security maturity.
Managed SOC providers should also cover the staff, tools, and processes necessary for 24/7 support.
SOC-as-a-Service (SOCaaS) Roles & Tasks
Usually, a security operation center or managed soc services includes the following roles.
SOC Manager
Is the leader of the Security Operations Center, overseeing all operations and security teams.
Security Analyst Tier 1
The main task of this role is triage: classify and security events for the tier 2 SOC analysts.
Security Analyst Tier 2
Security analysts that focus on incident response. This includes investigation of security information and mitigation in case of an attack, detection of the infected systems, establishing the scope of the attack and the threat.
Security Analyst Tier 3
SOC analysts who scan systems and files for threats, and identify vulnerabilities in enterprise data security that could potentially lead to data breaches.
Security Architect
Security engineers responsible for designing all the systems, processes, and security infrastructure. Also lessens integration with own security stack or those offered by 3rd party vendors .
Compliance Auditor
Supervises the organization’s compliance with all laws and regulations, both internal and external. Can also review the organization’s global security posture.
SOC Coordinator
This is the link between the Socaas provider and the client’s security experts.

SOC-as-a-Service (SOCaaS) Benefits
When compared to a conventional on-premises SOC, SOCaaS offers enterprises several significant advantages compared to internal SOC.
1. More Rapid Identification and Repair
SOCaaS solutions to faster recognize, classify, order, and address security incidents.
Speed is a major benefit in going through all the security alerts, ruling out the “false positives” and focusing on the real ones.
The big number of alerts can be overwhelming if it takes too long to respond to all of them, so time is of the essence.
2. Lowers the Security Risks
Having a SOCaaS solution decreases the risk of a security events.
24/7 monitoring, detection, and response capabilities help identify an intruder after the first machine is compromised.
Also, patching and updating software, as part of the security stack, can be a task for the managed SOAR solution.
By doing so, you free up time for your IT team and making sure that such an important job is never neglected.
3. Scalability
SOC-as-a-Service is a flexible and adaptable solution. The team and services are scalable up or down to respond to your organization’s needs or for a specific incident.
4. Increases Maturity
It is hard for companies to hire hyper-specialized security experts. It may be heavy on their budgets or they might need experts only from time to time.
So, having third-party experts enhances the level of maturity of a company’s security team.
5. Reduces Costs
Buying all the tools necessary for an efficient team can be expensive.
Only think about all the equipment, licenses, hardware, and software that you need.
Buying a SOCaaS subscription to have access to all these is much more convenient.
Additionally, a lot of SOCaaS pricing structures are consumption-based, which means that businesses only pay for the services they use.
6. Talent Optimization
Staffing shortage is a real problem for IT departments. So, instead of struggling to attract and retain talent, companies can employ help from a vendor.
This also can free up time for your in-house team, passing on a certain amount of workload to the SOCaaS team.
7. Keeping Your Security Up-to-date
Keeping up-to-date with all the security tools and practices can be difficult with your company’s resources. That is why you will benefit from your vendor’s capability to scale access to the latest security improvements.
SOCaaS Challenges
Although there are many advantages to outsourcing security operations, there may also be difficulties and restrictions. So, I think it’s important to take a look at the downside also:
Onboarding Process
Before the vendor starts providing its services, he must deploy and configurate the security solutions in the customer’s environment.
This process can be time-consuming and difficult, exposing your company to risks.
Data Sharing
To efficiently detect and respond to threats, a SOCaaS vendor will need access to your data. Sharing large amounts of sensitive data could lead to data exposure and higher security risks.
Data Storage
Your service provider will also need permission to store sensitive data. This will expose your organization to data leaks if the provider is compromised. There is also the challenge to keep track of that data if you decide to change vendors.
Vendor dependence
Transitioning away from a Soc as a Service provider can be complex and costly, especially if the organization has integrated its systems tightly with the provider’s platform.
Long Delivery Costs
Providers use data feeds and network taps from their customers’ networks to operate their cybersecurity solutions on-site.
So, the provider’s network and systems produce and store log files and other alert data. Gaining access to full-log data from a managed SOC provider can cost a company money.
Shared Security Team
Because some services could be shared across several customers, an external team might not be able to customize them, which could hurt efficiency.
Also, an external team will not know all the specifics of an organization, as an in-house team would. In this case, knowing the internal processes means being able to protect them better.
Compliance
Some compliance-related tasks are incompatible with a third-party provider. Therefore, putting into place security controls and policies to achieve and demonstrate compliance may still be an internal job.
Unable to Customize
Because they have multiple customers to satisfy, the level of customization of a SOCaaS solution is limited. This could decrease efficiency in protecting certain assets like endpoints or networks.
In-house SOC vs SOC as a service
Although SOCaaS normally offers classic SOC services at a cheaper cost, it may not be the right fit for your organization. You may still choose to maintain an on-premises SOC if the needs of your business are better tended this way.
Take a wise decision based on these lists of attributes.
Choose SOCaaS if you:
- Look for IT staff to handle highly specialized tasks or 24/7 monitoring.
- Don’t have a suitable physical space for a SOC team.
- Can’t or are not willing to invest in security technologies.
- Have low cybersecurity maturity and are looking for a fast solution.
- Experience variable security needs depending on the time of the year, the cycle of production, etc.
Choose SOC if you:
- Already invested in technology and employees and what to continue to do so.
- Have security maturity and a strong cybersecurity posture.
- Need a high-level granularity on your security practices.
- Maintain certain regulations that are hard to comply with by a third-party vendor.
How Can Heimdal® Help?
Heimdal offers the complete SOC toolkit under one roof, enabling you to quickly focus on threats utilizing the forensics analytics and built-in knowledge base.
Heimdal’s Extended Detection and Response solution will continuously check your communications systems, servers, endpoints, and connected devices for indicators of a cyberattack.
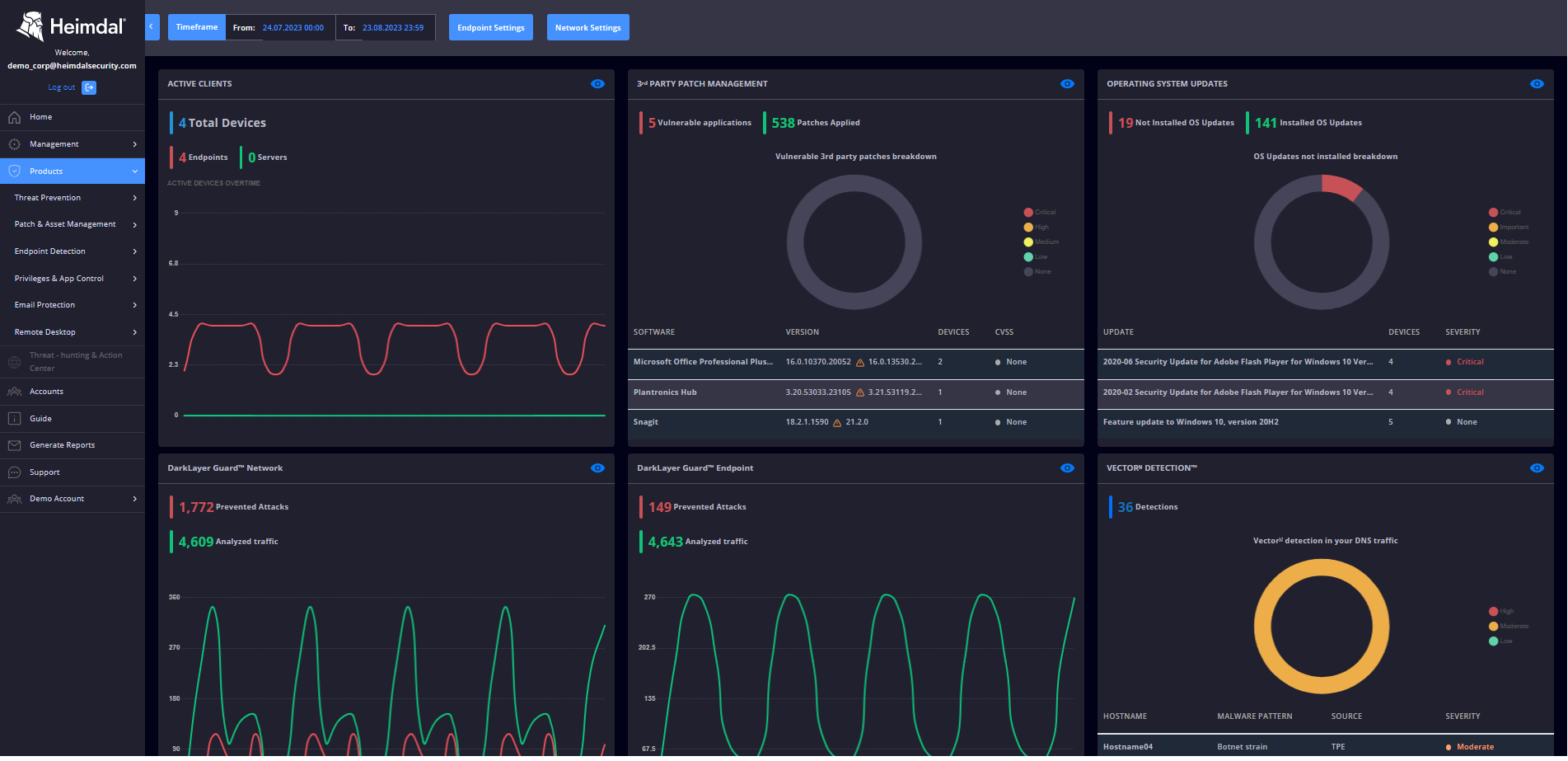
The Extended Detection and Response is powered SOC Service, which ensures:
- Constant monitoring, 24/7/365;
- Minimized response times and enhanced productivity;
- Complete network visibility;
- Real-time phone or email alerts in the event of an infection or attack;
- False-positive management, pre-incident assessment, “noise” reduction;
- Systemized, comprehensive reports on potential threats, malware, and vulnerabilities;
- Actionable advice on how to strengthen your security policies and procedures;
- Inspection of policy settings to ensure maximum compliance.
Also, the Heimdal Managed XDR solution allows a quick response to malicious incidents by
- blocking domains,
- quarantining malicious processes and e-mails,
- deploying critical vulnerability patches,
- and isolating compromised devices.
Our teams report the findings, actions, and resolutions of incidents both while and after they occur.

- End-to-end consolidated cybersecurity;
- Powered by the Heimdal XDR, Unified Security Platform
- Comprehensive enterprise security without any additional integrations
- 24x7 monitoring & prompt response delivered by our security experts
Wrapping Up…
A SOC as a Service (SOCaaS) offers a comprehensive security solution based on the Cybersecurity-as-a-Service (CSaaS) model, providing organizations with access to a fully-managed SOC team through subscription-based services.
By outsourcing security operations to SOCaaS providers, companies can benefit from rapid threat identification and response, lowered security risks, scalability, increased maturity, reduced costs, talent optimization, and up-to-date security measures.
However, there are challenges to consider, including the onboarding process, data sharing and storing concerns, long delivery costs, shared security teams, compliance issues, and limited customization.
Ultimately, the decision to adopt SOCaaS depends on the organization’s existing technological investments, cybersecurity posture, need for granular security practices, and regulatory requirements.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security