Contents:
Cyber Essentials is a practical, government-backed scheme that will assist you in protecting your UK-based organization, no matter how large or small, against a wide range of common cyber attacks.
It assists the UK’s most critical organizations, the wider public sector, industry, SMEs, and the general public. When incidents occur, they provide an effective incident response to minimize harm and aid recovery.
Cyber attacks come in various shapes and sizes, but the vast majority are straightforward and carried out by relatively unskilled individuals. Think of them like the digital equivalent of a thief checking to see if your front door is unlocked. Our advice is intended to keep these attacks from happening.
Cyber Essentials is basically a certificate that will allow your organization to demonstrate its credentials as trustworthy and secure in terms of cyber security. The certification defines a focused set of controls that provide clear guidance on basic cyber security for organizations of all sizes and provides a solid foundation of cyber security measures.
The scheme was launched with industry support, including the Federation of Small Businesses, the CBI, and several insurance companies that offer incentives to businesses.
Since then, one hundred twenty thousand certificates have been awarded to businesses, charities, educational institutions, and other organizations.
And now, let’s discuss the two Cyber Essentials certificates that you can achieve for your organization.
Cyber Essentials Certificates of Compliance
1.Cyber Essentials
Cyber Essentials is a foundation-level certification that provides a statement of the fundamental controls your organization should have to mitigate the risk of common cyber threats.
The Cyber Essentials certification demonstrates to customers, investors, insurers, and others that you have taken the bare minimum of security precautions to protect your organization from cyber threats.
This certification assures you that your defenses will protect you against the vast majority of common cyber attacks simply because these attacks seek targets that do not have the Cyber Essentials technical controls in place.
2.Cyber Essentials Plus
The Cyber Essentials Plus certification is the highest level of certification available under the Cyber Essentials scheme. It is a more rigorous test of your organization’s cyber security systems. In addition, our cyber security experts perform vulnerability tests to ensure your organization is safe from hacking and phishing attacks.
Note: You must meet the same Cyber Essentials requirements for both certifications.
What Is the Difference Between Cyber Essentials and Cyber Essentials Plus?
The basic Cyber Essentials package includes the following:
- Access to the online self-assessment questionnaire.
- Cyber Essentials branding for your business (to have on your website, emails, and so on).
- A 12-month Cyber Essentials certification upon successful application.
This is £300 plus VAT.
Cyber Essentials Plus provides comprehensive assistance throughout the Cyber Essentials application process. In addition to the Cyber Essentials certification, valid for a year, and the branding for promotional purposes, your organization will receive dedicated helpdesk support, on-site assessment at your company headquarters, and no resubmission fees.
Cyber Essentials Plus costs £2500 plus VAT.
The Cyber Essentials readiness toolkit is also available. Your responses to the toolkit’s questions aid in developing a personal action plan to assist you in meeting the Cyber Essentials requirements.
What Are the Benefits of Being Cyber Essentials Compliant?
The Cyber Essentials certification indicates that your organization is proactive in its response to malicious cyber attacks. Furthermore, it provides a mechanism for demonstrating to customers, investors, insurers, and others that you have taken the bare minimum of precautions to protect your organization from cyber threats.
The scheme can benefit your organization in a number of ways:
- Assure customers that you are working to protect your IT from cyber attacks.
- Attract new businesses by promising to implement cyber security measures.
- It shows that you have a clear picture of your organization’s level of cyber security;
- Cyber Essentials certification is required for some government contracts as well.
What Does the Cyber Essentials Compliance Scheme Cover?
Cyber Essentials covers the following cybersecurity areas:
- Firewalls.
- Secure Configuration.
- User Access Control.
- Malware Protection.
- Patch Management.
Let’s take them one by one:
1.Firewalls
Where a user connects to the Internet, firewalls and gateways provide a basic level of protection. While antivirus software protects the system from malicious programs, a firewall prevents attackers or external threats from gaining access to the system in the first place.
You can use this component to create a barrier between your IT network and other networks to determine whether incoming traffic should be allowed on your network.
2.Secure Configuration
Secure configuration refers to security measures implemented during the construction and installation of computers and network devices to reduce unnecessary cyber vulnerabilities.
Security flaws are one of the most common vulnerabilities that criminal hackers seek to exploit. The Cyber Essentials certification to the Secure Configuration scheme provides numerous benefits, including increased investor and customer confidence, and the ability to tender for business where Cyber Essentials certification is required.
3.User Access Control
Protecting user accounts and preventing privileged account misuse is critical for any cyber-secure system or network. Therefore, user accounts, particularly those with special access privileges (e.g., administrative charges), should be assigned only to authorized individuals, effectively managed, and provide the bare minimum of access to applications, computers, and networks.
Access control requires strict policy enforcement to be effective. This can be challenging because most organizations operate in hybrid environments where data is mobile and moves from on-premises servers to the Cloud, offices, and beyond.
Organizations must choose the best access control model to use based on the type and sensitivity of the data being processed.
3.Malware Protection
Malware Protection is one of the scheme’s five controls. This can aid in limiting the execution of known malware and untrusted software, preventing malicious code from causing damage or accessing sensitive data.
Protecting against a wide range of malware (including computer viruses, spyware, botnet software, and ransomware) and including virus removal options will keep your computer, privacy, and important documents safe.
4.Patch Management
Patch management is keeping software on computers and network devices up to date and resistant to low-level cyber attacks.
The thing is, any software is vulnerable to technical flaws. Once discovered and shared publicly, cybercriminals can quickly exploit them. Criminal hackers can exploit these vulnerabilities if operating systems and third-party applications are not properly patched or updated.
Patch management is a critical requirement of the Cyber Essentials scheme. It will assist you in ensuring that your devices and software are not vulnerable to known security issues for which fixes are available.
To keep itself safe, your company should routinely ensure that software is:
- Licensed and supported;
- Removed from devices when no longer supported;
- Patched within 14 days of an update being released in cases where the patch fixes a vulnerability with a severity described by the vendor as ‘critical’ or ‘high risk.’
How Can Heimdal® Help Your Organization Achieve Cyber Essentials Compliance?
Heimdal’s comprehensive cybersecurity solutions can facilitate your UK-based organization in not just achieving Cyber Essentials compliance quickly and efficiently but also staying compliant in the long run.
Below is a comparison table that we put together to show you how our services and solutions align with the CE components:
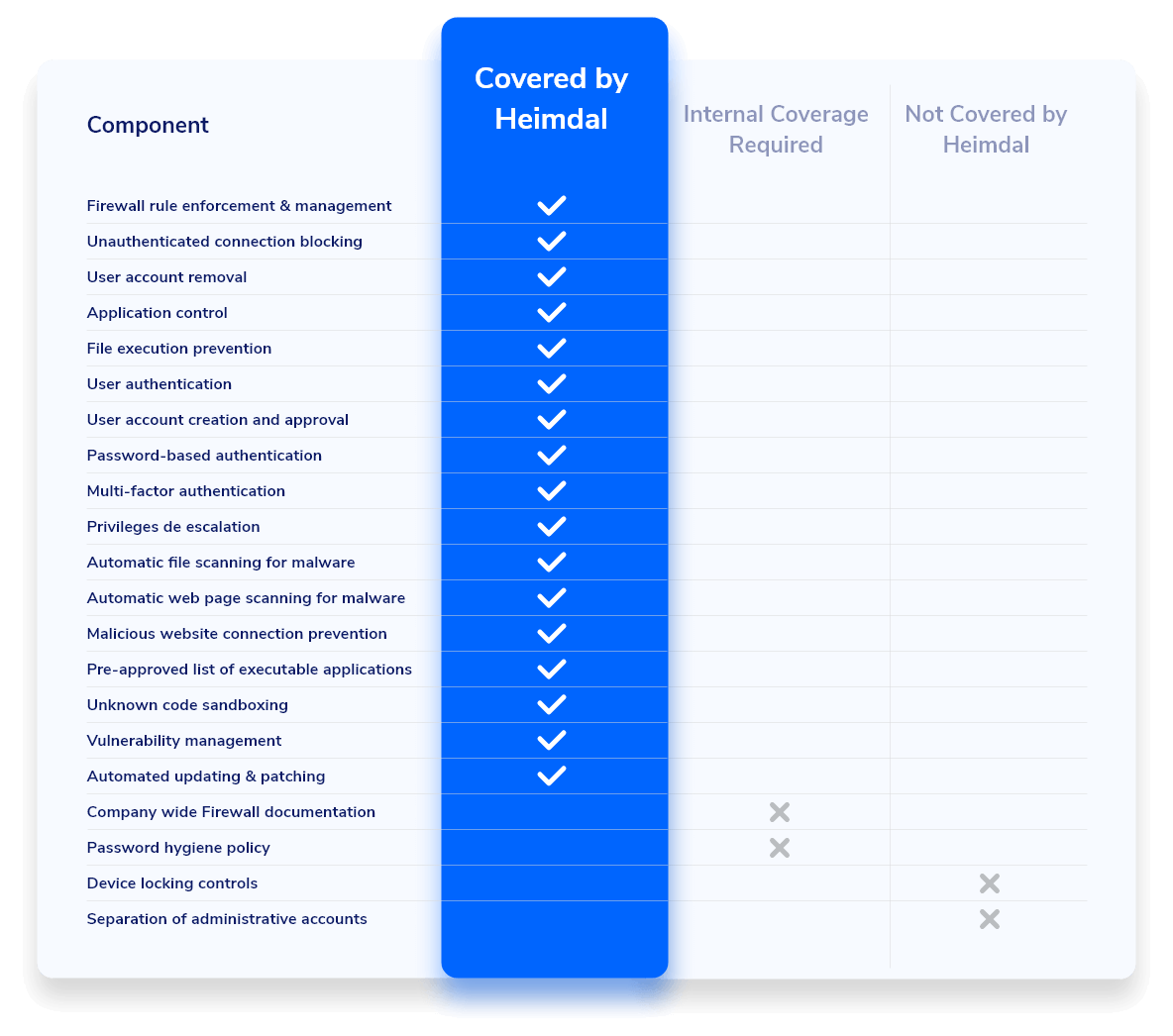
As you can see, we provide a comprehensive range of Cyber Essentials component coverage to help you achieve the compliance you require for your organization and stay compliant after each renewal.
Our four-layer Next-Gen Endpoint Antivirus detects sophisticated online threats like ransomware, hidden backdoors, rootkits, brute-force attacks, and undetectable malware.
Feel free to request a demo and take for a spin.
In addition, Heimdal provides the most powerful Patch & Asset Management software, allowing you to deploy and patch any Microsoft and Linux operating system, third-party and proprietary software, on the fly, anywhere in the world, and on any schedule.

Heimdal® Patch & Asset Management Software
- Schedule updates at your convenience;
- See any software assets in inventory;
- Global deployment and LAN P2P;
- And much more than we can fit in here...
Over to You
To summarize what we discussed, the Cyber Essentials scheme is a set of baseline technical controls developed by the UK Government and industry to assist large and small public and private organizations in improving their defenses and demonstrating their commitment to cybersecurity.
To achieve compliance, you must meet the criteria mentioned above, which you can do as of today by implementing Heimdal’s unified cybersecurity solutions. Obtaining cyber compliance has never been easier than it is now.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










