Contents:
As the world becomes increasingly digital, cybersecurity threats continue to evolve and become more sophisticated. Traditional cybersecurity measures are no longer enough to protect organizations from malicious attacks. That’s where managed threat hunting comes in – a proactive approach that involves actively searching for potential threats before they can do any damage. But is it really better than traditional cybersecurity?
What Is Managed Threat Hunting?
When it comes to cybersecurity, managed threat hunting is a relatively new concept. Managed threat hunting is a service provided by a third-party that proactively searches for threats within an organization’s environment. This is in contrast to traditional cybersecurity approaches that focus on reactive measures, such as responding to alerts or incidents.
The hunts are conducted using a combination of human intelligence and cutting-edge technology, which allows for a more comprehensive search than what is possible with traditional approaches.
Managed threat hunting can provide peace of mind to organizations by taking a proactive approach to security. This means that organizations can feel confident that they are doing everything possible to protect their systems and data from cyberthreats.
On top of that, managed threat hunting can save organizations time and money. This is because it can help avoid costly breaches by identifying and remediating threats before they cause damage.
If your organization is considering switching to a managed threat hunting approach, there are a few things you should keep in mind. First, make sure to partner with a reputable and experienced provider. Second, consider your organization’s specific needs when selecting a provider. And finally, be prepared to invest both time and resources into making the switch.
How Does Managed Threat Hunting Work?
The managed threat hunting process combines advanced technologies with human expertise to detect, investigate, and mitigate potential threats. This process relies mainly on these four steps:

- Planning – This is the stage where the managed threat-hunting team works with the organization to identify the assets that need protection and the potential threats they may face. They also identify the tools and techniques that will be used to detect, investigate, and mitigate threats.
- Detection – In this stage, the team uses advanced threat detection tools and techniques to monitor the organization’s network and systems for suspicious activity. A variety of methods are used to identify potential threats, including behavioral analysis, artificial intelligence-based detection, and anomaly detection.
- Investigation – To determine the extent of the threat and the potential impact on the organization, the managed threat hunting team investigates the incident once it has been detected. The team uses techniques, such as memory and disk analysis, network forensics, and malware analysis, to gather data and evidence.
- Response – The managed threat hunting team then takes the necessary steps to mitigate the threat, such as isolating the affected systems, removing malware, and patching.
What is Traditional Cybersecurity?
Traditional cybersecurity is a preventive approach to security that relies on perimeter defenses, such as firewalls and intrusion detection systems, to keep attackers out. This approach has its merits, but it also has its limitations. For one thing, it assumes that attackers will always try to come in from the outside. But in reality, many attacks come from insiders or from compromised accounts that have already bypassed the perimeter defenses. Traditional cybersecurity also relies heavily on signature-based detection, which means it can only detect known threats. But new threats are constantly emerging, and traditional cybersecurity can’t always keep up.
Furthermore, traditional cybersecurity can be described as reactive rather than proactive. It can take weeks or even months to detect an attack and then mount a response. By contrast, managed threat hunting is a proactive approach that searches for signs of an attack. This means it can detect attacks much sooner and mount a more effective response.
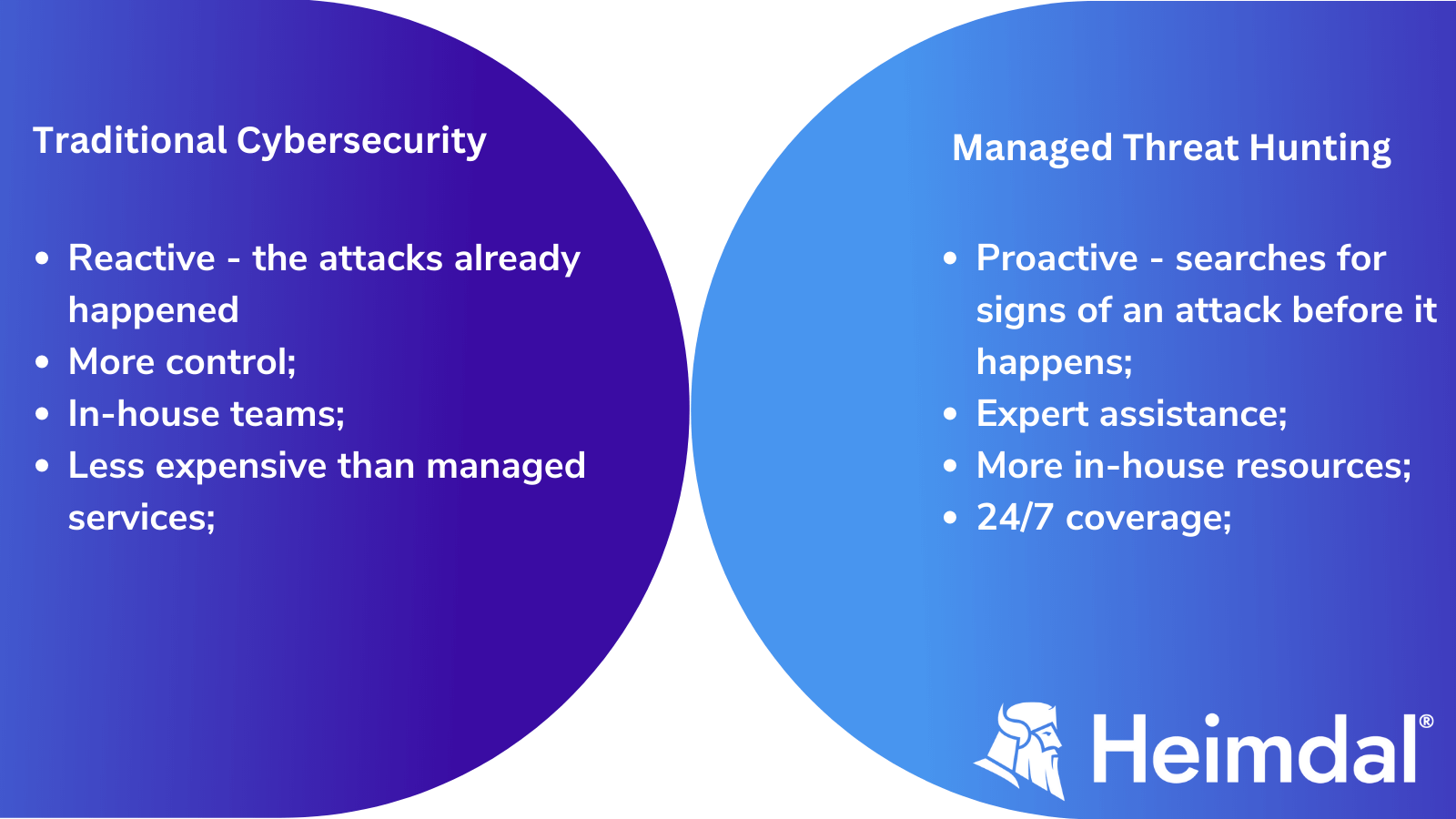
Pros and Cons of Managed Threat Hunting vs Traditional Cybersecurity
When it comes to cybersecurity, there are two schools of thought: managed threat hunting and traditional cybersecurity. So, which is better?
There are a few key distinctions between managed threat hunting and traditional cybersecurity that can make all the difference in your organization’s security posture. Here are some of the pros and cons to help you decide which is right for you:
Managed threat hunting:
Pros:
- You get expert assistance in identifying and remediating sophisticated threats that may have evaded your current security measures.
- Managed threat hunting services free up your in-house resources so they can focus on other tasks.
- These services provide comprehensive, 24/7 coverage and can scale quickly to meet changing needs.
Cons:
- Can be expensive, especially for smaller organizations.
- Requires sharing sensitive data with an external party.
- May require changes to your network infrastructure.
Traditional Cybersecurity:
Pros:
- More control over your organization’s security posture.
- In-house teams are typically more familiar with your organization’s specific needs and objectives.
- Can be less expensive than managed services, especially for larger organizations.
Cons:
- Takes up valuable time and resources that could be spent on other tasks.
- May not have the same level of expertise as a dedicated managed service provider.
- You are solely responsible for identifying and responding to threats.
The Benefits of Managed Threat Hunting
Managed threat hunting is a proactive approach to security that involves continuously searching for clues and indicators of compromise (IOCs) that could indicate an attempted or successful attack.
There are several benefits to using a managed threat hunting service:
- Increased visibility into your network: A managed threat hunting service can help you gain visibility into your network by identifying IOCs that may have been missed by your traditional security measures. This increased visibility can help you quickly identify and react to potential threats.
- Improved security posture: By proactively searching for IOCs, a managed threat hunting service can help you improve your overall security posture.
- Reduced false positives: A managed threat hunting service can also help reduce false positives, which can save you time and resources. False positives are often caused by traditional security measures, such as IDSes, that generate alerts for normal (benign) activity.
- Cost savings: A managed threat hunting service can also help you save money on your cybersecurity budget. This is because a managed service will often cost less than hiring in-house staff to do the same work.
Best Practices for Optimizing Your Cybersecurity Strategy
When it comes to cybersecurity, there is no one-size-fits-all solution. The best way to protect your organization is to have a comprehensive cybersecurity strategy that includes multiple layers of defense. However, even the most well-thought-out strategy can be ineffective if it’s not properly implemented or regularly updated.
To help you optimize your cybersecurity strategy, we’ve put together a list of best practices:
1. Understand your risks
The first step to protecting your organization is understanding the risks you face. This includes identifying what data and systems are most critical to your business and assessing the likelihood and impact of different types of attacks.
2. Implement layered security defenses
A good cybersecurity strategy will include multiple layers of defense, such as firewalls, intrusion detection/prevention systems, and anti-malware software. By using a combination of these technologies, you can better defend against a wider range of threats.
3. Educate employees on security risks and policies
Your employees are often the first line of defense against cyberattacks. It’s important to educate them on security risks and company policies so they can identify and report suspicious activity.
4. Keep your software up to date.
Regularly patching and updating software is crucial for keeping systems secure. Attackers often exploit known vulnerabilities in outdated software, so it’s important to keep all systems up to date with the latest security fixes.
In order for managed threat hunting to be successful, organizations need to have clear visibility into their environment and understand their normal behavior baseline. Additionally, it is important to have a team of experienced threat hunters who are able to identify and investigate anomalous activity.
Organizations should also consider implementing automation and orchestration capabilities to help with managed threat hunting efforts. Automation can help reduce the time needed to investigate potential threats, while orchestration can help simplify the investigation process by providing a centralized view of all relevant data.
Take the Heimdal® Approach
The Heimdal suite and Threat-Hunting and Action Centre enable you to envision, hunt, and act from a single unified and integrated platform. The platform eliminates the need for a multitude of solutions which create a slow and inefficient environment, by merging everything in one unified, integrated, and AI-driven tool that will change the way you look at cybersecurity forever.
For Managed Security Providers (MSPs), our solution makes it possible to manage more customers globally without any drain on efficiency or resources, all through a single-platform and real-time view of all customers in a single console.
Our platform brings a re-imagined SecOps toolkit under one roof, allowing you to swiftly zone in on threats using built-in knowledge base and forensics analytics.
Furthermore, the Heimdal Managed XDR solution allows a quick response to malicious incidents by blocking domains, quarantining malicious processes and e-mails, deploying critical vulnerability patches, and isolating compromised devices. Our teams report the findings, actions, and resolutions of incidents both while and after they occur. They also provide actionable strategies to avoid future attacks on the vulnerable routes.

- End-to-end consolidated cybersecurity;
- Powered by the Heimdal XDR, Unified Security Platform
- Comprehensive enterprise security without any additional integrations
- 24x7 monitoring & prompt response delivered by our security experts
Conclusion
Managed threat hunting and traditional cybersecurity both have their advantages and disadvantages. In the end, it is up to each company to decide which approach best suits their needs. If you are trying to reduce the risk of an attack or want a proactive approach to security, managed threat hunting might be the right choice for you. On the other hand, if you need a more cost-effective solution that covers all areas of your cybersecurity needs then traditional cybersecurity may be better suited for you. Weighing up these two approaches can help ensure that your business has the necessary protection from any potential cyber threats.
If you liked this article, follow us on LinkedIn, Twitter, Facebook and YouTube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









