Path management is a vital step to identifying and securing all coding gaps that could potentially be exploited.
In this article, we’re going to discuss the best patch management practices, and the risks associated with deploying a poor patch management program.
Why Is Patch Management Important?
Patching is important for several reasons.

Security
Patches are released to fix security vulnerabilities in software and systems.
Failure to patch these vulnerabilities leaves the company’s systems exposed to potential security breaches, data theft, and other cyberattacks.
Patch management helps to minimize these risks by ensuring that all software and systems are up-to-date with the latest security patches.
Compliance
Many regulatory and industry standards require companies to implement patch management as part of their cybersecurity program.
Failure to comply with these standards can result in hefty fines and legal consequences.
Stability
Patches also provide bug fixes and other updates that improve the stability and performance of software and systems.
Without patch management, companies risk facing system crashes, downtime, and other issues that can negatively impact their operations.
Reputation
A company’s reputation can be severely damaged by a security breach or downtime caused by unpatched vulnerabilities.
Customers may lose trust in the company and take their business elsewhere.
Patch management helps to prevent such incidents and maintains a positive reputation for the company.
The Risks of Poor Patch Management
Improper patch management practices can expose an organization to a number of significant risks.

Security breaches
If software vulnerabilities are left unpatched, cybercriminals can exploit them to gain unauthorized access to an organization’s systems and steal sensitive information or cause other forms of damage.
Data loss or corruption
Malicious attacks can also result in data loss or corruption, which can have significant financial and reputational consequences for the affected organization.
Non-compliance
Many industries and government regulations require organizations to maintain a certain level of security, and failure to patch vulnerabilities can result in non-compliance and potential legal action.
Increased downtime
Patching systems can take time and require temporary shutdowns, which can cause significant downtime and disruptions to business operations.
Damage to reputation
A breach resulting from an unpatched vulnerability can damage an organization’s reputation, leading to a loss of customer trust and potential revenue.
Increased costs
Addressing security breaches, downtime, and other consequences of improper patch management can result in significant costs for an organization.
Overall, organizations that fail to maintain proper patch management practices can experience a range of negative consequences, making it essential to prioritize this aspect of cybersecurity.
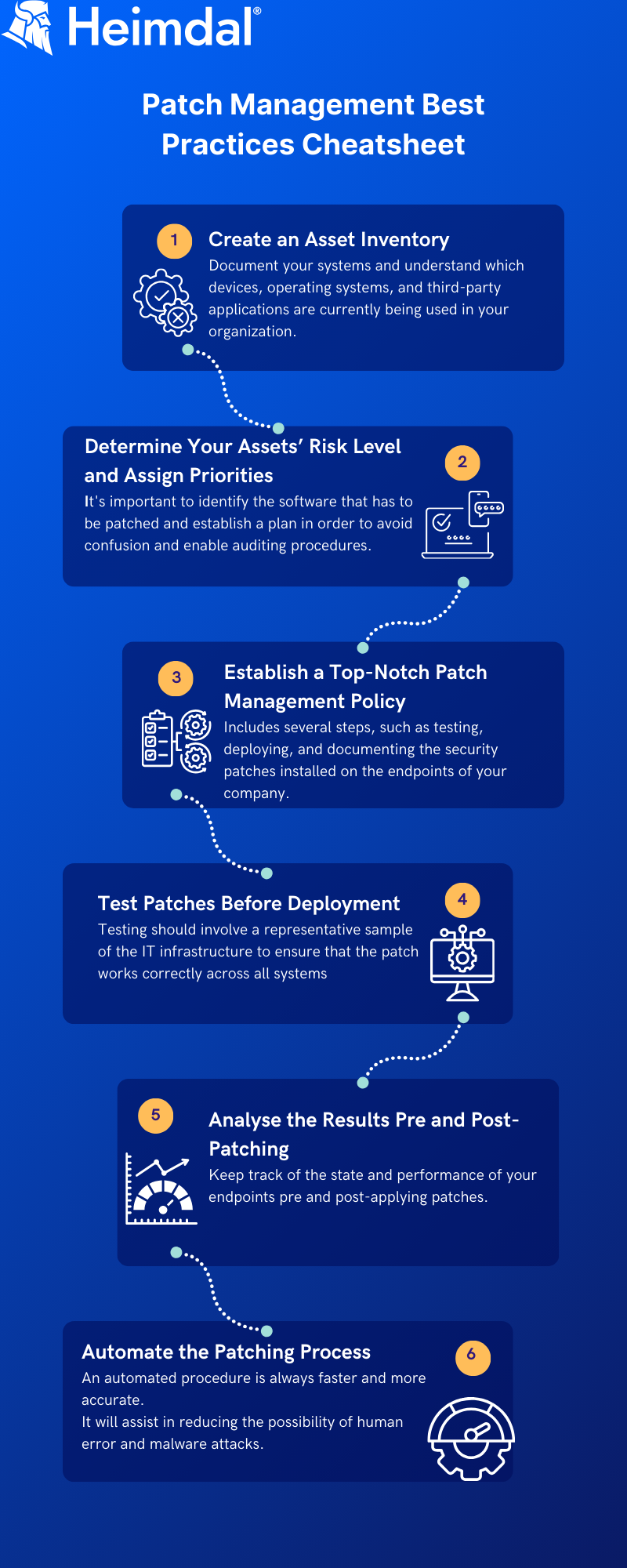
Patch Management: Best Practices to Follow (Cheat sheet)
Create an Asset Inventory
Before you start caring for vulnerabilities, you should start preparing.
This step may seem self-explanatory, but it is often overseen.
You should have a crystal-clear idea of what software and hardware your company is using, and know exactly how your environment currently stands.
Document your systems and understand which devices, operating systems, and third-party applications are currently being used in your organization.
Once you have a firm understanding of what you’re dealing with, it will be much easier for you to pay attention to vulnerabilities and discover available patches.
Determine Your Assets’ Risk Level and Assign Priorities
Not all assets are created equal.
You need to investigate which ones of your systems are non-compliant, and vulnerable and thus need patches faster.
It won’t help if correct identification and prioritization are not put in place.
Patching the wrong system won’t take you too far.
Setting priorities and identifying goals for patching are crucial steps in the patch management process.
It’s important to identify the software that has to be patched and establish a plan in order to avoid confusion and enable auditing procedures.
Also, make sure to prioritize the patches with high security risks, as they should be applied as soon as possible.
Establish a Top-Notch Patch Management Policy
A patch management policy outlines the standards and rules for handling vulnerabilities properly.
This process includes several steps, such as testing, deploying, and documenting the security patches installed on the endpoints of your company.
I have covered patch management policy previously, so I strongly suggest you read this article as well.
Test the Patches Before Deployment
Before deploying a patch, it is essential to test it in a controlled environment.
Testing patches allows businesses to identify any issues that may arise from the patch, such as compatibility issues with other software.
Testing should involve a representative sample of the IT infrastructure to ensure that the patch works correctly across all systems.
By testing patches before deployment, businesses can avoid potential system failures or security breaches.
Analyse the Results Pre and Post-Patching
Keep track of the state and performance of your endpoints pre and post-applying patches.
This practice is strongly related to the previous one, because sometimes, patches may actually slow down some processes.
This way, if problems begin to occur, it will be easier for you to determine if they can be attributed or not to an applied patch.
Bonus tip: make sure you have a rollback plan, so that in case of errors or conflicts, you can restore your software to the previous working version as soon as possible.
This should help you reduce downtime.
Automate the Patching Process
Despite the fact that patching can be done manually, an automated procedure is always faster and more accurate.
It will assist in reducing the possibility of human error and malware attacks.
By automating the patch management process, your system administrators will save time and be free to work on other security-related responsibilities.
Also, you will have complete access to your IT system and be rigorous about monitoring fixes and vulnerabilities.
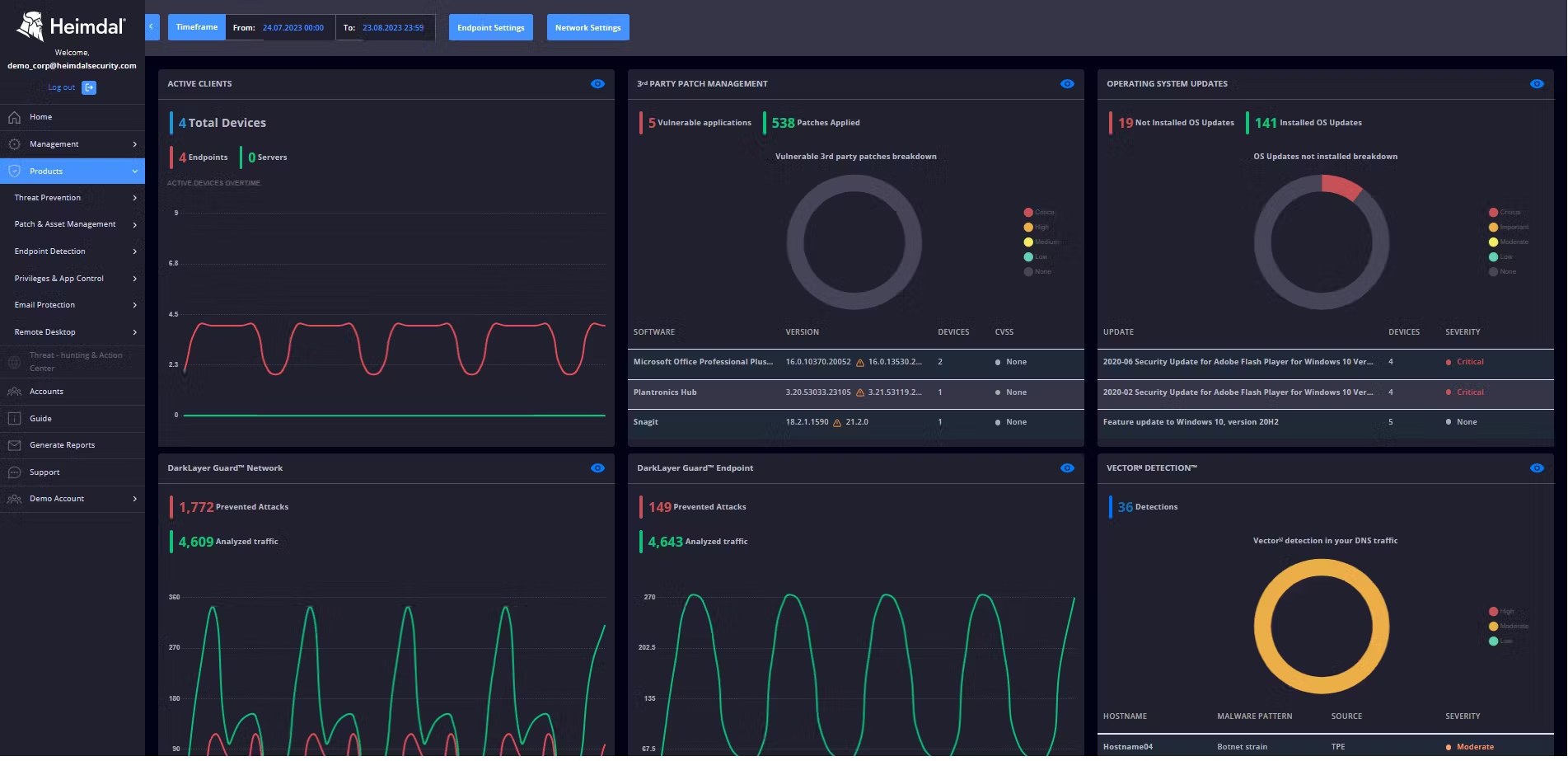
How can Heimdal® help?
Such a solution is our very own Heimdal® Patch & Asset Management Software, a hyper-automated solution that is guaranteed to keep your business secured in terms of patching, whether we’re talking about Windows, Linux, macOS, or third-party application patches.
Our solution is fully customizable, meaning that it can be configured to perfectly suit your organization’s needs.
Heimdal®’s software also works as set-and-forget, and will allow you to patch from anywhere in the world, anytime you want it.
Updates are delivered fully repackaged, ad-free, and tested from Heimdal® using encrypted packages inside encrypted HTTPS transfer to your endpoints locally.
Using local network P2P between your own machines only, to achieve world-leading bandwidth consumption.
Book a demo by using the form below and convince yourself of what our solution has to offer!
Automate your patch management routine.
Heimdal Patch & Asset Management Software
Conclusion
Patch management is an essential part of any business’s network security.
By implementing the right patch management practices, organizations can ensure their networks remain secure and compliant with industry standards.
From establishing a patching policy to automating processes and keeping up-to-date on patches, there are several strategies that businesses should consider in order to maximize the effectiveness of their patch management program.
With the proper knowledge and implementation tactics, companies can create a secure environment for their customers and employees alike.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










