Contents:
Remote work has become a highly popular and common practice around the world, especially now as companies allow a significant part of their employees to remain remote. However, while this practice increases flexibility, improves productivity, and enhances work-life balance, there’s a downside to it – remote work security risks.
In this new remote-working landscape created by the COVID-19 pandemic, cybersecurity became an even greater concern for businesses everywhere.
The necessity of more rigorous and powerful cybersecurity to protect employees working remotely means that organizations should start looking toward more advanced approaches, such as investing in a zero-trust model and identity-centric services, to provide a stronger approach to these frequent attacks.
Common Security Risks of Remote Working
By unknowingly following cybersecurity worst practices, employees can actually be the ones giving threat actors access to your network and your company’s private information. When company operations suddenly or temporarily change to remote work, employees can become confused about how to continue working securely.
Remote workers can become the biggest threat to your network’s security, putting your company’s data at risk. Working from home can potentially cause data breaches, identity theft, and a host of other negative results.
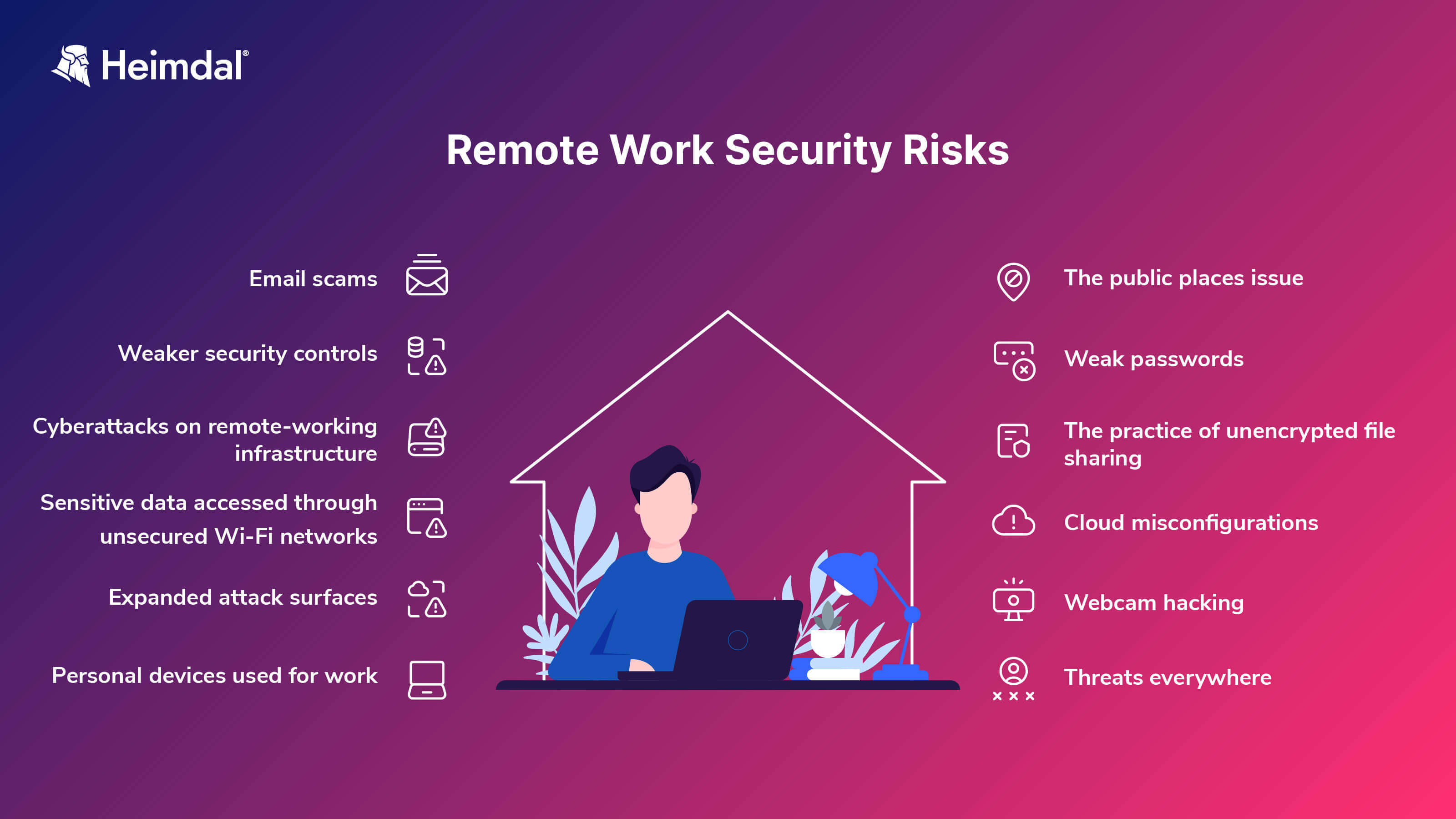
Let’s take a close look at some of the remote working security risks companies face:
1. Email scams
The most important cyber threat to remote employees is phishing strategies. Phishing schemes involve an individual or entity masquerading as a legitimate source, usually over email, to fool a victim into providing private login credentials or privileged information, which can then be employed to break into accounts, steal more confidential information, perform identity fraud, and much more.
Phishing emails have become so sophisticated that it is increasingly becoming more challenging for employees to notice them, especially when phishing emails make it past email filters straight to an employee’s main inbox.
2. Weaker security controls
The weakening of security controls goes far beyond relaxing firewall rules and email policy. Multiple existing layers of cyber protection will not apply to remote employees. Workers suddenly taking their work devices home with them will find themselves stripped of defense as they replace the office network with their home Wi-Fi.
No cybersecurity teams are monitoring what happens on the home networks of employees. Remote work, by definition, involves some system access, network traffic, and data that is moved outside the conventional perimeters of the enterprise technology environment. In general, organizations are unable to extend monitoring to all endpoints and across all networks that are now enabling remote work environments.
3. Cyberattacks on remote-working infrastructure
Apart from the weakening of existing controls, spinning up new infrastructure will generate new risks. Security teams should be on alert for brute force and server-side attacks. DDoS protection will also become essential.
For multiple organizations, this will be the first time that a DDoS attack could destroy their business by preventing remote workers from accessing services over the internet. Researchers expect to see a sharp increase in both of these forms of attack.
4. Sensitive data accessed through unsecured Wi-Fi networks
Your employees could be connecting to their home wireless network or accessing their corporate accounts using unsecured public Wi-Fi. This way, malicious actors nearby can easily spy on their connection and harvest confidential information. For instance, data sent in an unencrypted form in plain text might be intercepted and stolen by cybercriminals. For this reason, your employees should not be allowed to access any unknown Wi-Fi networks unless they are using a VPN connection.
5. Expanded attack surfaces
With more people working remotely, enterprises simply have more endpoints, networking, and software to protect, all of which significantly increase the volume of work for IT departments, which are frequently overburdened.
6. Personal devices used for work
A lot of employees transfer files between work and personal computers when working from home, which is a worrying practice. Also, a practice known as “Bring Your Own Device” or BYOD policy, which allows employees to use their own devices at work, has become popular in recent years.
You need to be fully aware of the issues involved when allowing your employees to use their personal devices for work-related matters. For instance, they may suddenly leave the company and hold on to the confidential information that has been stored on their device during their employment and you will not get the chance to erase it.
What’s more, they may not be keeping their software updated, which opens up security holes in your environment. We keep stressing the importance of applying software patches in a timely manner and for a good reason.
Consequently, we would advise against letting your employees use their personal devices at work since it would be difficult for you to control what happens on their endpoints.
7. The public places issue
Even if cybersecurity is our focus, we can’t completely leave physical security behind when it comes to your company’s sensitive information. For example, there are employees who may be talking loudly on the phone while working in public places, expose their laptop’s screen for the entire crowd inside a café to see or even leave their devices unattended.
Companies should teach their employees even the most basic security measures, even if they may seem like common sense at first glance. A friendly reminder for them not to expose the data of your business will always be of great benefit.
8. Weak passwords
Even if an organization uses VPNs, firewalls, and other cybersecurity solutions in order to keep safe your remote network, human error happens when employees attempt to protect their accounts with weak passwords. One of the easiest, yet frequently neglected, ways for your employees to protect themselves when working from home is to strengthen their passwords and make sure that they have strong password protection across all of their devices.
Unfortunately, cybercriminals are aware that human error is easier to exploit than trying to get past an advanced security solution, which is why they will attempt to crack account passwords in order to access private company data.
Attackers use a variety of measures to crack passwords. For instance, they will put together lists of frequently used passwords that can be used to easily access poorly protected accounts.
Repeat passwords are another usual insecure operation that cybercriminals use. Once they crack the password to one account, they will attempt to access other accounts with that same password. Workers who repeat passwords, especially across personal and business accounts, are at a higher risk of becoming victims of a cyberattack.
9. The practice of unencrypted file sharing
While organizations may think to encrypt information that’s stored on their network, they may not consider encrypting data when it’s in transit from one place to another.
Your employees share so much private data every day, from client account information to files and more, that your company cannot afford to not secure this information from being seized by a cybercriminal. If sensitive company information is intercepted, it can lead to identity fraud, ransomware attacks, theft, and more.
10. Cloud misconfigurations
The cloud is a crucial technology for remote work, although it also comes with risks. Misconfigurations, especially those related to access, pose one such risk. Companies may accidentally give users too much access or fail to implement access controls.
11. Webcam hacking
When employees work from home, they frequently participate in teleconferences and video calls that require them to use their webcam. Unfortunately, cunning cybercriminals can easily and illegally access their webcam, violating thei privacy. Even worse, if they have confidential documents lying around the office, intruders could be able to see them by hijacking their webcam.
12. Threats everywhere
There are remote work security risks everywhere! The shift to remote working is a blessing for malicious insiders. Sensitive information can now be easily stolen from a company device over USB within the privacy of their own home.
People around us may also represent a threat. Yes, you heard it right! Most of us think we live with people we can trust, but from a company point of view, their staff homes are zero-trust environments. Private discussions can now be heard, intellectual property can be seen on screens and monitors in living rooms everywhere in the world.
Remote Work Security Best Practices for Companies
Here are some fundamental practices that companies can use to strengthen security in a remote working environment:
1. Enforce Multi-factor authentication
Multi-factor authentication will act as an additional layer of security on top of your remote employees’ accounts. The more security layers in place, the little the risk of cyber-criminals gaining access to your sensitive systems.
2. Use Password managers
Besides multi-factor authentication, in regards to passwords, your employees should also be using a password manager. This way, they will not need to remember all of the different passwords that they need to set up for their work-related accounts.
3. Use internal VPN
VPN connections are crucial when your employees connect to unsecured networks, such as Wi-Fi hotspots, even when they work from home. It’s recommended for your employees to be using your company’s VPN. What this tool does is route the traffic through the internet from your organization’s private network, ensuring even more security. Basically, anyone who tries to intercept the encrypted data will not be able to read it. And this way, your employees will be able to connect to your company’s intranet, the private network designed to be used only by your company’s staff (in case you have one).
4. Deploy a Firewall
A firewall will prevent unauthorized access to and from the network, further strengthening the security of your employees’ devices. What firewalls do is monitor network traffic, at the same time finding and blocking unwanted traffic. So, firewalls are important tools that will protect your remote endpoints against various cyber threats.
5. Create a Work-from-home Security Policy
So, how do you protect your company’s private data when you can’t fully control the devices used to access your network? Where should you start to make sure your remote workforce is secure? How can you reduce the cybersecurity issues with remote work?
The first step is to create a security policy specifically designed for remote workers. A remote work security policy is a company’s written strategy that specifies all guidelines and practices for all the employees who carry out their responsibilities away from an organization’s physical office. These policies often include all important aspects of online security.
But let’s take a closer look at some of the essential security clauses that should be included in your remote work policy:
- Clearly define which positions are eligible for remote work
Be transparent towards your employees. Everyone should be aware which job functions are allowed to work remotely are which are not due to security reasons. Unfortunately, not every position is a good fit for remote work. If you don’t have a clear guide in place, chances are your work-from-home approvals will be judged as unfair. Specific security guidelines also must be created for employees from offshore locations, since these days companies hire remote developers in Latin America, remote marketers in India, etc.
- List the tools and platforms they should be using
Both your remote and on-site employees should be on the same page at all times and use the same approved tools, such as cloud storage platforms, communication/video conferencing tools, project management tools, etc.
- Provide employees with steps to follow at the first signs of account compromise
If they believe the company’s information has been compromised, they should have a clear guide to follow, such as where they should report the incident, be instructed to immediately change their passwords, etc. These steps should be included in their mandatory cybersecurity training, alongside other items such as how to create strong passwords.
6. Enhance Endpoint Security
Last but not least, system administrators should improve the security at the endpoint level and be able to see the exact details of your endpoints at all times. This is why it’s recommended you deploy a complete endpoint detection and response (EDR) solution, that will allow you to remotely prevent next-gen malware, data leakage, respond quickly to threats, and automatically manage software deployment and patching.

- Next-gen Antivirus & Firewall which stops known threats;
- DNS traffic filter which stops unknown threats;
- Automatic patches for your software and apps with no interruptions;
- Privileged Access Management and Application Control, all in one unified dashboard
Wrapping up
It’s crucial for you to remain innovative and competitive in the current business landscape and allowing your employees to work remotely is definitely a necessary step. Yet, remote work security risks should be addressed before you allow anyone to work from outside the office – no matter if we’re talking about permanent remote workers or the ones who do it just a few hours per month. However, only when you will correctly respond to this challenge, will you be capable of fully seizing this opportunity that increases talent retention, productivity, and improves your staff’s work-life balance.
This article was initially written by Bianca Soare in 2021, and later updated by Antonia Din in 2023.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








