Contents:
In today’s digital world, it is more important than ever to be able to identify and assess any potential threats to your business. That’s why User and Entity Behavior Analytics (UEBA) is becoming such an invaluable asset for businesses of all sizes. In this article, we will introduce you to UEBA and how it can be used to provide better security and insights into the data of your business.
What Is User and Entity Behavior Analytics (UEBA)?
User and Entity Behavior Analytics is a security strategy that focuses on monitoring and analyzing user behavior within an organization in order to identify malicious or unauthorized activity. UEBA can be used to supplement or replace traditional security methods, such as Intrusion Detection Systems (IDS), by providing a more comprehensive view of activity within an organization.
UEBA systems use machine learning algorithms to analyze data from various sources, then proceed to use said data to create models of normal user behavior, which can be used to identify anomalies and malicious activity.
Organizations can use UEBA to detect a variety of threats, including insider threats, advanced persistent threats (APT), and data breaches. UEBA can also be used to monitor compliance with internal policies and external regulations.
Benefits of using UEBA include improved detection of sophisticated attacks, reduced false positives, and the ability to proactively identify risks. UEBA can also help organizations save money by reducing the need for manual investigations of suspicious activity, but more on that later on.
How Does UEBA Work?
UEBA works by constantly monitoring and analyzing data about user behavior within an organization’s network. This data can come from a variety of sources, including system activity logs, application activity logs, and user activity data from security devices like firewalls and intrusion detection systems.
The learning algorithms used by UEBA are meant to identify patterns. These patterns could be things like unusually high levels of activity during normally inactive periods, or accessing sensitive data that the user typically doesn’t have access to. An example of unusual activity could mean a particular user that regularly downloads, let`s say between 10-20 MB of files daily, but all of a sudden begins downloading gigabytes of files. In this scenario, the system will detect the anomaly and alert you to the potential security threat. This allows organizations to quickly identify and respond to potential threats that might otherwise go unnoticed.
Benefits of Using UEBA
There are many benefits of using UEBA for businesses. Perhaps the most obvious benefit is that it can help enterprises to detect and prevent security threats, as well as improve their overall security posture. By identifying areas of risk, organizations can make changes to their security policies and procedures to better protect themselves from potential threats. Additionally, UEBA can help when it comes to compliance with industry regulations such as HIPAA and PCI DSS.
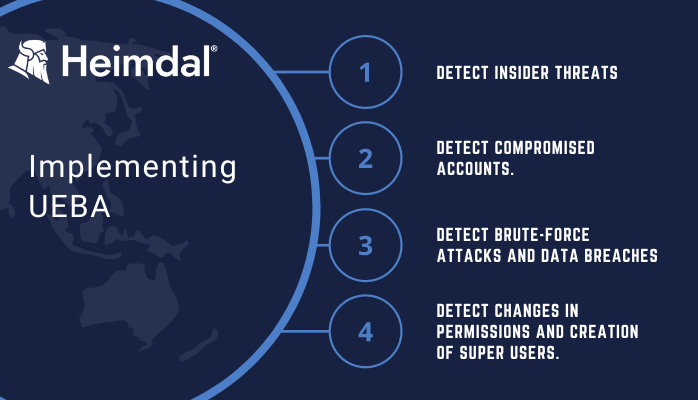
Further, UEBA allows you to:
1. Detect insider threats. The possibility of an employee, or perhaps a group of employees, going rogue and stealing your data may not seem so far-fetched. UEBA can help you detect data breaches, sabotage, privilege abuse, and policy violations.
2. Detect compromised accounts. There are times when user accounts are compromised. This could be due to a user installing malware on their computer, or it could be spoofed. With UEBA, you can weed out compromised and spoofed accounts before they can do any real damage.
3. Detect brute-force attacks. It is not uncommon for hackers to target your cloud-based entities and third-party authentication systems. With UEBA, you are able to detect brute force attempts and block access to these systems.
4. Detect changes in permissions and creation of super users. UEBA can detect when super users are created or if unauthorized permissions have been granted to accounts.
5. Detect breach of protected data. In order to keep protected data secure, you need to know when a user accesses it without a legitimate reason.
Finally, UEBA can also help businesses to improve their operational efficiency. By reducing false positives and identifying potential issues early, businesses can avoid costly disruptions down the line. Additionally, by automating some of the tasks associated with UEBA, businesses can free up resources that can be better spent on other tasks.
UEBA vs. UBA
User behavior analytics (UBA) involves the monitoring, collection and analysis of user data and activities. It works by examining historical data logs stored in log management and Security Information and Event Management (SIEM) systems. UBA and UEBA technologies detect patterns in traffic caused by user activity that can denote both normal and malicious behavior, thereby providing cybersecurity teams with valuable insights when irregular behavior is detected.
While UBA systems don’t take action based on their findings, can be configured to automatically adjust the difficulty of authenticating user accounts that show anomalous behavior or otherwise deviate from normal behavior based on their findings.
The primary differences between user behavior analytics and user and entity behavior analytics are the following:
- UEBA is newer. In 2015, analyst firm Gartner published a market guide for what it coined as user and entity behavior analytics.
- UEBA systems track more than just user activity. It tracks the activity of devices, applications, servers and data. Instead of analyzing only user behavior data, this technology combines user behavior data with behavior data from entities.
- UEBA systems may produce a higher volume of data and provide more complex reporting options than original UBA systems.
UBA and UEBA systems don’t flag every strange behavior as a risk. Instead, they rate the impact it may cause. For instance, anomalous behavior involving less sensitive assets gets a lower impact score, while accessing personal data would be graded more severely. This way security personnel can focus on the most pressing issues at hand and UBA will automatically restrict or complicate authentication for the user involved in the anomalous activity.
Other Comparisons
UEBA products are just one way to address threat detection, among others such as:
UEBA vs. SIEM
To identify potential threats and issue alerts, SIEM systems gather and aggregate data from multiple sources. SIEM systems are commonly used for detecting compliance issues and use statistical models to identify suspicious behavior patterns that are linked to cyberattacks. SIEM products can overwhelm information security teams with a large volume of alerts, many of which may be false positives.
A SIEM is a good security management tool, but it is less sophisticated when it comes to detecting and responding to more advanced threats. As a result, experienced threat actors do not engage in one-off threats but rather perform long-term attacks that can go undetected for several weeks or even months by traditional threat management tools.
However, UEBA solutions are capable of detecting more sophisticated threats, including those that might not be detected on a day-to-day basis but display surprising patterns over time. Malvertising is an example of this, a seemingly harmless advertising applet downloaded to a browser that collects data from the user or infects the endpoint.
UEBA and SIEM tools can be stacked together to better protect enterprises from a wide range of threats. As UEBA concentrates less on system events and more on specific user or entity activities, it builds a profile of employees and entities based on usage patterns and alerts users when unusual or suspicious behavior is observed.
UEBA vs. SOAR
By gathering rich event data and using automation to identify potential threats and anomalies, Security Orchestration Automation and Response (SOAR) systems outperform SIEM systems. It is still necessary for information security analysts to integrate SOAR systems with security data sources.
UEBA vs. NTA
All traffic and flow records on enterprise networks can be monitored and analyzed with Network Traffic Analysis (NTA) solutions using machine learning, advanced analytics, and rule-based detection.
A key benefit of NTA is that it allows companies to see all events across their entire network, not just logged ones. This includes everything that an attacker does. In addition, NTA can be deployed relatively easily, and it allows companies to profile both users and network devices, just as UEBA can.
It is likely that an organization with more sophisticated security needs will require both a UEBA and an NTA solution simultaneously, as is the case with SIEM. Unlike UEBA, NTA is unable to track local events, such as those from a device not connected to the network and is generally less capable of identifying more advanced security issues.
UEBA vs. XDR
UEBA capabilities are also convergent with XDR tools. Extended Detection and Response (XDR) systems are the latest generation of Endpoint Detection and Response (EDR) systems and Network Detection and Response (NDR) systems. EDR focuses on end-user computers and organizational servers, whereas NDR monitors network transmissions. XDR is an emerging technology that is converging with UBA and UEBA functions, as well as with SOAR and SIEM systems.
XDR combines all the capabilities of EDR, UEBA, NTA, next-generation antivirus and other tools into a single solution to deliver the best security. For companies to identify, hunt down, investigate, and respond to potential security threats, it provides comprehensive visibility and robust behavioral analytics across their entire infrastructure, including networks, clouds, and endpoints.
Because of the abundance of related technologies, threat detection tools are often overlapping. UBA and UEBA should be viewed as just one of many tools in the cybersecurity toolbox, just as other types of information security systems are. It is important for cybersecurity professionals to understand the organization’s use cases, despite the potential overlap between these systems.
How to Implement UEBA?
Organizations can implement UEBA in a number of ways, depending on their needs and resources. One approach is to use a UEBA platform that provides an out-of-the-box solution with preconfigured rules and models. This can be beneficial for organizations that want to get started with UEBA quickly and don’t have the resources to build their own solution.
Another option is to build a custom UEBA solution using open-source tools. This approach requires more technical expertise but gives organizations more flexibility to tailor the solution to their specific needs.
Once you’ve decided how you’re going to implement UEBA in your organization, there are a few key steps you need to take:
- Collect data from multiple data sources: In order to effectively detect anomalous behavior, it’s important to collect data from as many relevant sources as possible. This might include data from security devices such as firewalls, intrusion detection systems, and web proxies; data from user activity tracking systems; and data from application logs.
- Normalize and enrich the data: Once you have all of your data collected, it needs to be normalized so that it can be analyzed consistently. This step may also involve enrichment.
5 Tips for Utilizing UEBA Effectively
- Implement UEBA along with traditional security solutions such as firewalls and intrusion detection systems, not instead of them.
- Utilize UEBA to supplement your security team’s expertise by providing visibility into user and entity behavior.
- Configure UEBA to generate alerts when anomalous activity warrants further investigation by your security team.
- Make the most of UEBA`s ability to monitor the changes in user behavior in order to detect malicious insiders.
- Last but not least, UEBA can further be used to monitor for suspicious activity associated with new technologies or apps within the organization.
Pros and Cons of UEBA
Pros
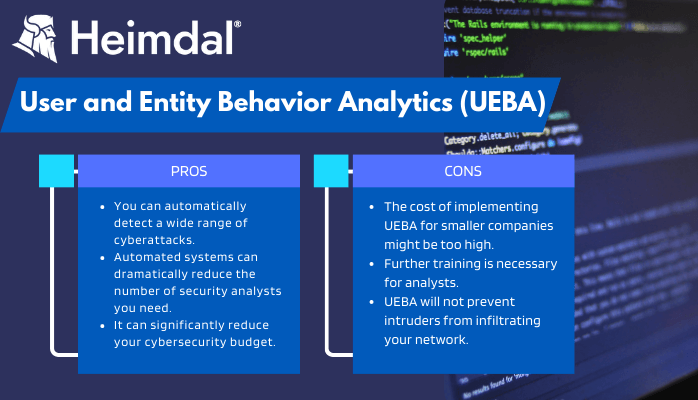
- The primary pro when using UEBA is that you can automatically detect a wide range of cyberattacks, including insider threats, compromised accounts, brute-force attacks, and the creation of new users.
- Automated systems can dramatically reduce the number of security analysts you need to employ. This leads us to ne next pro on the list:
- UEBA allows fewer security analysts to do more, it can also significantly reduce your cybersecurity budget.
Cons
There are also some drawbacks to UEBA, even when used alongside other cybersecurity tools.
- The cost of implementing UEBA can also present itself as a primary drawback. For larger companies, the investment will quickly pay off, but smaller companies might not need such a complex monitoring solution. UEBA might seem redundant to them because most dedicated hosting solutions already provide advanced user access controls for websites and web portals.
- Secondly, UEBA generates more complex data than more basic UBA systems. As a result, analysts without the necessary training may have difficulty understanding it.
- UEBA will help you spot unusual behavior, but it won’t prevent intruders from infiltrating your network. Keep in mind, UEBA is an addition, not a replacement for other cybersecurity systems.
How Can Heimdal® Help?
As we established so far, User and Entity Behavior Analytics works best when used together with other solutions, one of which is XDR. Extended Detection and Response oversees, gathers data from throughout your environment to predict cyberattacks and plots courses of action based on genuine, real-time data. Our Extended Detection and Response solution will continuously check your communications systems, servers, endpoints, and connected devices for indicators of a cyberattack.
Furthermore, Heimdal’s Endpoint Detection and Response also provides unrivaled prevention, threat-hunting, and remediation functionalities by incorporating six solutions in a single easy-to-deploy and compact agent that will not slow down your systems and will save you significant time.
And of course, the Network Detection and Response solution from Heimdal will provide A-Z protection regardless of device or operating system by utilizing machine learning on device-to-infrastructure interaction. Besides detecting and preventing attacks that firewalls cannot detect, it also blocks malicious web content, prevents data leakage, and filters traffic locally in any environment.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
In Conclusion
User and Entity Behavior Analytics (UEBA) can provide valuable insights into the behavior of users and entities in your system. By monitoring user activities and utilizing analytics to identify anomalies, UEBA can help you quickly detect potential threats or malicious activity within your network. With the right strategy, UEBA can be a powerful tool for improving security posture while also reducing operational overhead. So, if you’re looking to bolster your security efforts and stay ahead of emerging threats, look into incorporating User and Entity Behavior Analytics into your business operations today!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security