Contents:
APT stands for Advanced Persistent Threat. Behind an APT attack there usually are some highly skilled hackers that have very specific targets and a “low-and-slow” approach when it comes to directing and executing their misdemeanors. Read on to find out how an APT attack works, what are the clues that indicate your network might be compromised, and what you can do to avoid the danger.
What Is an Advanced Persistent Threat?
We call APT (advanced persistent threat) those complex cyberattacks that are long-term and multi-staged and usually planned by very well-organized criminal structures or even nation-state groups. The word was originally used to designate the groups responsible for these attacks, but it has since come to refer to the attack techniques used by these threat actors.
The primary targets of APT attacks are most of the time high-profile companies, and the cybercriminals aim to obtain classified information, intellectual property, personal information or databases, ongoing communication between high-value targets.
Stages of an APT Attack
The stages of an APT attack can be grouped into 4 or 5, with different terminology. Let us have a closer look.
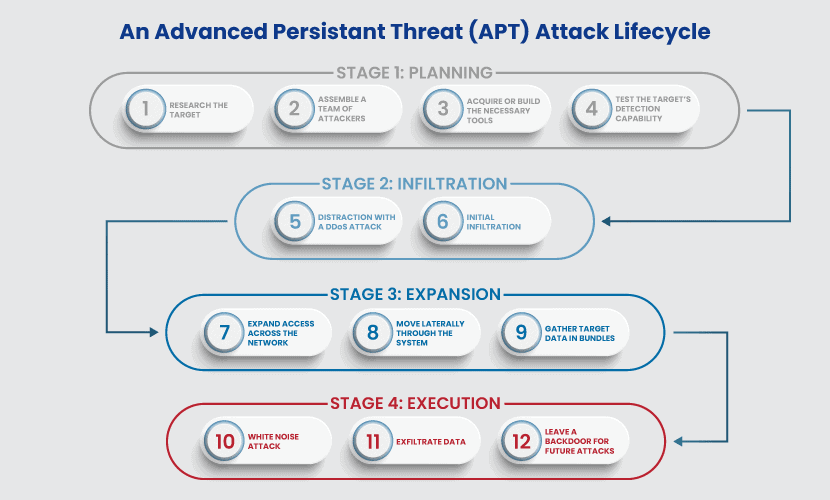
Source: phoenixNAP
- Initial compromise. In this initial stage, cybercriminals get access to their targets by using tactics like social engineering, spear-phishing, zero-day vulnerabilities, or malware.
- Establishing foothold. At this point, the remote administration software is planted in the network of the victim, creating backdoors for future access.
- Privileges escalation. In this stage, cybercriminals try to acquire administrator privileges by exploiting or cracking passwords
- Internal prospecting. This stage is dedicated to exploration and information collection.
- Lateral movement. At this point, cybercriminals “expand control to other workstations, servers and infrastructure elements and perform data harvesting on them.”
- Presence maintenance. In this stage, hackers make sure that they have continued control over the victim’s network and that they maintain the credentials acquired in the earlier stages.
- End of mission. In this final stage, cybercriminals exfiltrate the data they’ve stolen from the victim’s network.
APT Attack Indicators
Advanced persistent threat actors use sophisticated means to hide their presence, but there will still be some signs that can raise suspicions. Here are the indicators that may help you recognize an ATP attack:
Unexpected logins
If you detect an unexpected volume of logins outside working hours, an ATP attack might be ongoing. Attackers might have stolen credentials and use them in different time zones or during the night to avoid being noticed.

Source: Unsplash
Unexpected data transition
ATP attackers copy the data they want to steal to other locations in your network and they transfer it when they know they can do it undetected. Consequently, you might notice server to server, server to client, or network to network information flows.
Sophisticated spear-phishing emails
Spear-phishing attacks are directed against employees or organizations and are designed to “look like they’ve been sent by well-known market actors such as PayPal, Google, Spotify, Netflix, and even Apple Pay. In some cases, they even take the guise of in-house emails, asking the employee to fill in credential requests.”
ATP actors might send spear-phishing emails to high-management individuals, trying to get access to restricted data or their laptops.
Trojans
As defined in our Cybersecurity Glossary,
a Trojan Horse is a type of malware that acts according to the Greek legend: it camouflages itself as a legitimate file or program to trick unsuspecting users into installing it on their PCs. Upon doing this, users will unknowingly give unauthorized, remote access to the cyber attackers who created and run the Trojan. Trojans can be used to spy on a user’s activity (web browsing, computer activity, etc.), to collect and harvest sensitive data, to delete files, download more malware onto the PC and more.
CompariTech mentions that
APTs often install multiple Trojans in different parts of an organization’s network to make it easy to access various parts. They also use them as redundancies, just in case other forms of network access are blocked. If they only had one entry point, months of their work could be easily undone if the target’s security team comes across it.
Advanced Persistent Threat Examples
When it comes to ATP examples, CompariTech notes:
historically, the term advanced persistent threat has mainly been used for groups linked to nation-states. Few others had the necessary financial backing, the organizational capacity and the impunity of working on behalf of their government (and thus under its protection), except those linked to nation-states. The earliest named APTs were the Chinese state-backed groups PLA 61398 (APT 1) and PLA 61486 (APT 2). Their activities often focused on industrial espionage, targeting the likes of nuclear and aerospace firms. Groups linked to other countries were soon named as well, including Fancy Bear (APT 28), Helix Kitten (APT 34), the Lazarus Group (APT 38) and the Equation Group. These have ties to Russia, Iran, North Korea and the USA, respectively.
There are also advanced persistent threat actors that seem to act only for financial gain, without any state ties, like Silence or Carbanak Group.
Since PLA 61398 was mentioned, it might be interesting for you to know that one of their targets was, apparently, Coca-Cola:
Coca-Cola was in the midst of an acquisition bid for the China Huiyuan Juice Group, worth $2.4 billion. During the negotiation process, PLA Unit 61398 was rifling through the computers of Coca-Cola executives to try and find out the company’s strategy.
The attack started with a spearphishing attempt, which led one of Coca-Cola’s executives to click on a malicious link. This gave the group its entry point into Coca-Cola’s network. Once it was in, it managed to collect and send confidential files back to China each week, all without being noticed.
Moreover, some of the most notorious APT attacks happened in 2006 and 2010 – I’m talking about Sykipot Attacks and the Stuxnet Worm.
The 2006 Sykipot attacks took advantage of Adobe Reader and Acrobat vulnerabilities and were part of “a long-running series of cyberattack campaigns aimed primarily at U.S and U.K organizations including defense contractors, telecommunications companies and government departments. The attackers consistently used targeted emails containing either a link or malicious attachment containing zero-day exploits.”
The Stuxnet Worm was used against Iran in 2010. “Considered at the time to be one of the most sophisticated pieces of malware ever detected […]”, the worm targeted “systems that are traditionally not connected to the internet for security reasons. It instead infects Windows machines via USB keys and then propagates across the network […]”.
If you’re interested in learning more about how worms work, I recommend you to read one of our previous articles, Virus vs. Worm: What’s the Difference?
APT Security Measures
An APT attack is complex and might seem really startling, but, luckily, there are a few prevention strategies you can adopt to avoid it. So, always remember to:
Use a traffic filtering solution
Traffic filtering is essential for DNS and HTTP(S) security, playing a major-league part in keeping malware away from your systems.
Our Heimdal™ Threat Prevention works both at endpoint and perimeter-level and analyzes traffic and behavioral patterns using Machine-Learning algorithms specifically trained for threat hunting. HEIMDAL Threat Prevention will allow you to move beyond signature-based detection and block attacks that an antivirus cannot even recognize.
Patch all the software you use
Patching is as crucial as traffic filtering when it comes to avoiding malware and other cyberattacks that cybercriminals may use to perform an APT.
If you want to keep all the software you use up to date and do it automatically, saving time for other tasks, our Heimdal Patch & Asset Management is the ideal solution for you. It will deploy Windows, 3rd party, and custom software to your endpoints anywhere in the world according to your own schedule, without interruptions, creating inventory reports for accurate assessments and compliance demonstrations.
Use a privileged access management solution, as well as application control
Privileged access management is related to privileged accounts and protects data and information across organizations, together with Identity Access Management and Privileged Identity Management. A strong access control system can make it more difficult for APT attackers to successfully log into your company’s network.
You can try our very own Heimdal Privileged Access Management, which will show you all the admin requests in its centralized dashboard, allowing you to approve or deny user requests from anywhere or set up an automated flow.
Moreover, our Application Control module will only enhance your security. It can be combined with the PAM solution so that it will support both blacklisting and whitelisting, removing permanent rights, and allowing access to application execution when users need it.
Protect your email
Since APT actors are very fond of spear-phishing and other email threats, it’s clear that you need to properly protect your email accounts.
Our Heimdal Email Fraud Prevention will help you combat phishing, business email compromise, email-deployed malware, imposter threats, CEO fraud and criminal impersonation, Man-in-the-email, and spoofing attacks.
Install an antivirus & firewall
Antivirus solutions prevent a wide range of trojans, malware, and viruses that advanced persistent threat actors might use when trying to exploit your system. Firewalls are also essential.
If you would prefer a solution that enhances the traditional antivirus and firewall with other cybersecurity necessities, you’ve come to the right place. Our Endpoint Prevention, Detection and Response (EDR) Software merged EPP with EDR to offer you continuous protection by using a multi-layered approach: DNS-based traffic filtering, a next-gen Antivirus, automated patch management, and a component for automated admin rights escalation and de-escalation.
Wrapping Up
An APT attack is a very complex cybersecurity threat, usually orchestrated by well-organized criminal groups, but not impossible to prevent if you have the right information and allies. If you want to know more about which of our company products are best suited for your needs, don’t hesitate to contact us or get a demo to test our products.
Drop a line below if you have any comments, questions, or suggestions regarding the topic of advanced persistent threats – we are all ears and can’t wait to hear your opinion!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











