When it comes to cybersecurity incidents, your company’s endpoints are some of the most important IT assets you want to protect. Explore with me the critical differences in EPP vs. EDR and learn how they play a vital role in strengthening your company’s cybersecurity.
Key Takeaways:
- Understand the differences between EPP and EDR;
- Choose the right solution for your business;
- Explore EPP and EDR in Heimdal® Suite.
- EPP and EDR top features
EPP vs. EDR: Understanding the Differences
Grasping the distinction between EPP vs. EDR is essential. These are crucial tools for protecting your company’s endpoints, which have become important with the rise in remote work.
EPP solutions are proactive, whereas EDR solutions are reactive.
Let us note some other differences between them:
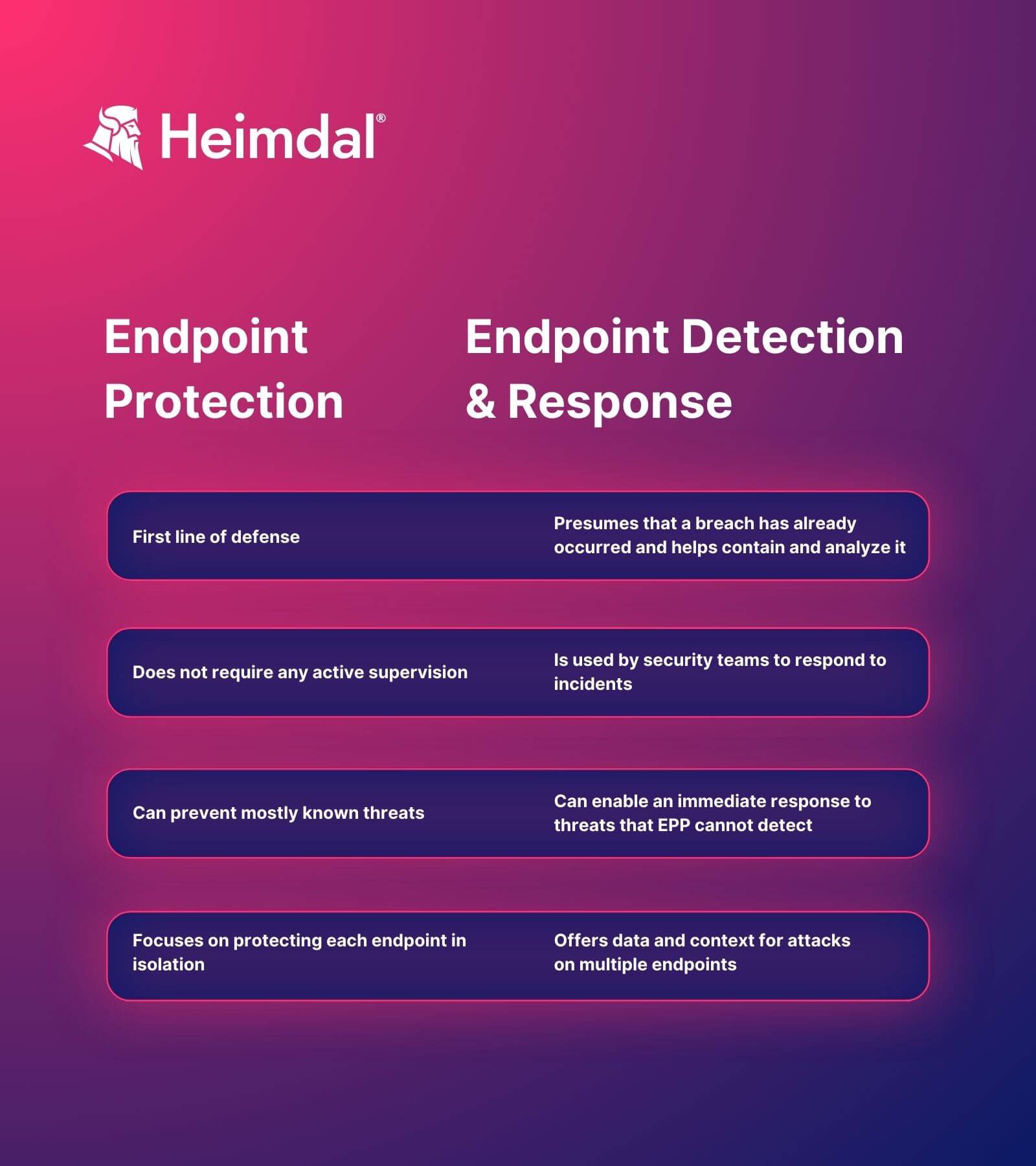
It’s also worth mentioning that EPP platforms are not designed for post-compromise security.
If attacks bypass your firewall and EPP, detecting them will be impossible without additional tools.
EPP vs. EDR: Which One to Choose?
Choosing between EPP and EDR depends on your needs. EPP works well with little oversight and is great for cloud-hosted systems. EDR, on the other hand, offers more detailed insights and helps find threats early. However, you need both for a good cybersecurity strategy.
EPP helps by keeping malware away from your devices. It quickly spots and removes known threats.
However, EPP alone isn’t enough because new and changing malware can still get through.
EDR steps in when a threat bypasses EPP. It quickly controls and removes these threats to keep them from spreading. EDR is more active.
It helps IT teams find and stop threats, and figure out where they started.
Together, EPP and EDR can “identify security incidents faster” and “simplify IT investigations”.
How Can Heimdal® Help with Endpoint Protection?
Heimdal® offers a strong Endpoint Detection and Response service. This service protects your devices and keeps an eye on cyber threats, responding quickly to them.
It uses DNS-based attack protection and updates your software to prevent attacks.
Here’s a product demo for you to check out:
Here’s how Heimdal®’s service works:
- Threat Prevention – a module that uses AI to predict and stop future threats. It finds suspicious activities and blocks attacks that regular firewalls might miss.
- Patch and Asset Management – that automatically updates your Windows and other software to fix security gaps.
- Next-Gen Antivirus – An advanced antivirus that uses AI. It has stages of scanning to detect and identify even the most advanced threats.
- Ransomware Encryption Protection – Protects your devices from ransomware attacks. It works with any antivirus and can handle even the most sophisticated attacks.
- Privileged Access Management and Application Control– our PAM solution can remove permanent rights and give rights when needed, for the period that they’re necessary; the rights granted can be revoked at any time, while all actions will be logged for a full audit trail.
See Heimdal in Action
In conclusion, it’s important to revisit the basic principles of EPP and EDR.
What Is EPP?
EPP portrays a proactive attitude and stands for Endpoint Protection Platform. EPP is represented by solutions that detect and block cybersecurity threats at the device level. It typically includes components like antivirus, anti-malware, data encryption, firewalls, intrusion prevention, and data loss prevention.
Most EPP approaches are signature-based – they prevent attacks by identifying threats based on known file signatures.
A file signature refers to “a unique identifying number located at the beginning of a file.
This number identifies the type of file, giving information about the data contained within the actual file.”
EPP tools today also offer dynamic fileless analysis and prevention, malicious static file detection, behavioral analysis, and Machine Learning model detection.
Learn what is the best 8 endpoint protection software at the moment and why.
Top Features of an EPP Solution
The most important capabilities of an EPP solution are:
- threat signatures;
- threat intelligence integration;
- static analysis for suspicious binary files;
- behavioral analysis;
- vulnerability management.
What Is EDR?
EDR, which stands for Endpoint Detection and Response, is the reactive part of the equation. EDR detects when something malicious has been executed on an endpoint and provides notifications, visibility, and remediation.
EDR platforms combine next-gen antivirus elements with additional tools, providing real-time anomaly detection and alerting, forensic analysis, and endpoint remediation.
They collect and analyze data from a network’s endpoints and use artificial intelligence, machine learning, and behavioral analysis to actively neutralize attacks.
EDR is essential for stopping attacks at the earliest signs of detection, even before a human admin finds out about the existence of a threat.
Moreover, EDR solutions also provide incident response capabilities to help security teams respond to cyberattacks faster and in a more efficient manner.
Top Features of an EDR Solution
The key capabilities of EDR solutions include:
- threat intelligence;
- threat detection and alerting;
- automation;
- forensic incident investigation;
- incident response;
- incident containment.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










