Contents:
Security specialists at Kaspersky have discovered a rare, large-scale Advanced Persistent Threat (APT) operation against users in Southeast Asia, especially in Myanmar and the Philippines.
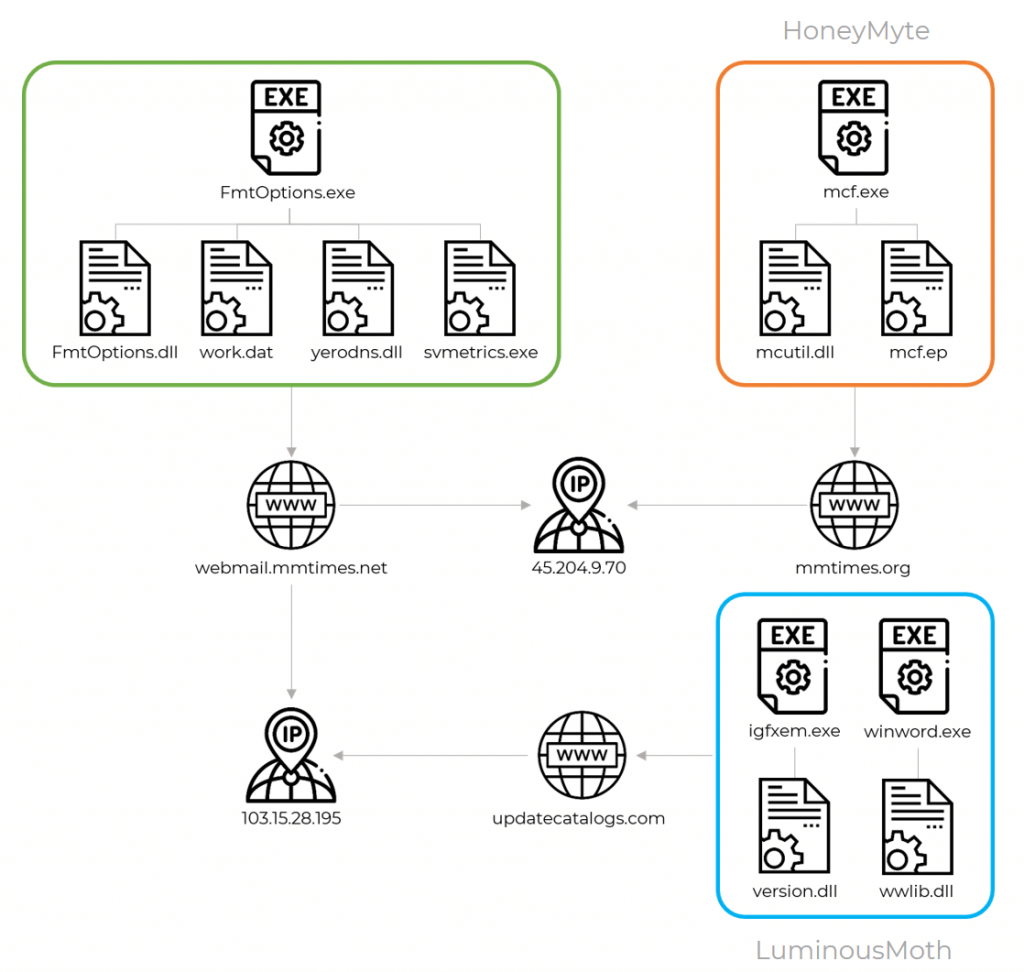
This cluster of APT activity, tracked as LuminousMoth by Kaspersky, has been associated with the HoneyMyte, a well-known, long-standing, Chinese-speaking threat actor, with medium to high confidence.
HoneyMyte is mainly interested in gathering geopolitical and economic intelligence in Asia and Africa.
The links they have discovered include network infrastructure connections such as command-and-control servers used by both HoneyMyte and LuminousMoth and almost identical strategies, methods, and procedures (TTPs) when deploying Cobalt Strike beacon payloads.
These groups are also known to initiate wide-scale attacks against significant numbers of targets with the ultimate goal of impacting just a small subset matching their interests.
In its report released on Wednesday, Kaspersky declared it identified approximately 100 victims in Myanmar and 1,400 in the Philippines, some of which were government organizations.
Kaspersky GReAT security researcher Aseel Kayal stated:
The massive scale of the attack is quite rare. It’s also interesting that we’ve seen far more attacks in the Philippines than in Myanmar.
This could be due to the use of USB drives as a spreading mechanism or there could be yet another infection vector that we’re not yet aware of being used in the Philippines.
The Malware Can Spread Through Removable USB Drives
The hackers usually gain an initial foothold in the system using spear-phishing emails with a Dropbox download link. Once clicked, this link downloads a RAR archive disguised as a Word document that contains the malicious payload.
After being executed on a victim’s computer, the malware attempts to infect other hosts by spreading via removable USB drives. If a drive is found, the malware creates concealed directories on the drive, where it then transfers all of the victim’s files, along with the malicious executables.
The malware also has two post-exploitation tools that can be used for later movement. One of them consists of a signed, fake version of the Zoom app and the other one steals cookies from the Chrome browser.
Once on the device, the hacker group starts to exfiltrate data to the command and control (C2) server. For the victims in Myanmar, these C2 servers were often domains that posed as known news outlets.
This new cluster of activity might once again point to a trend we’ve been witnessing over the course of this year: Chinese-speaking threat actors re-tooling and producing new and unknown malware implants.
In Kaspersky’s report, you can find further technical details and a list of indicators of compromise (IOCs), including malware hashes and C2 domains.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










