Contents:
In one of my previous articles, I discussed AI and its critical role in today’s – and tomorrow’s – world, particularly in terms of cybersecurity. I’m certain that AI (and technology in general) is a tremendous evolution engine, providing us with more and more opportunities almost on a daily basis. Have a look, for instance, at how Heimdal™s malware hunting tools tip the scales in our customers’ favor!
Why Malware Hunting
Malware hunting is unquestionably one of the most important pillars of today’s cybersecurity. It is linked to threat hunting, which is the practice of finding and comprehending threat actors who may compromise a company’s infrastructure by focusing on repeated activities. Threat (or malware) hunting is a proactive cyber defense strategy based on the assumption of compromise, which allows you to concentrate on the risks that may have gone undiscovered in your network.
Because no system can be completely protected, all businesses require additional cyber defenses on top of the existing cybersecurity solutions on the market. Malware hunting combines methodology with advanced technology and top-notch threat intelligence to ensure a proactive and ever-evolving approach to detecting anomalies, strange patterns and various other indicators of compromise.
To better understand why you absolutely need threat / malware hunting, consider this: cybercriminals will always try to find (incredibly new and innovative) ways of hacking your systems (for a variety of reasons: financial gain, as a political statement, for revenge, fame and so on), so, even if you do apply all the necessary prevention strategies that you can think of, they will most likely get to you at some point. Threat hunting allows your IT teams to significantly reduce risks by always having the assumption of breach in mind.
Have organizations really shifted from what may be called passive detection to the more dynamic malware hunting? Fortunately yes. According to a report of the SANS Institute for 2020, “Sixty-five percent of respondents indicated that they already perform some form of threat hunting, and 29% plan to do so in the next 12 months. Only 2% of respondents claimed that they don’t run threat hunting operations and don’t intend to in the future.”
When it comes to market tendencies for malware hunting, many companies rely on automated tools for SIEM, IDS/IPS, EDR, internally developed search solutions, and third-party platforms that offer the threat intelligence that’s needed in malware hunting activities.
Interestingly enough, the respondents of the SANS Institute report, coming from organizations that range from small (less than 1000 employees) to large (more than 50 000 employees ), also shared their thoughts on how satisfied they were with the tools and technologies they used at the time:
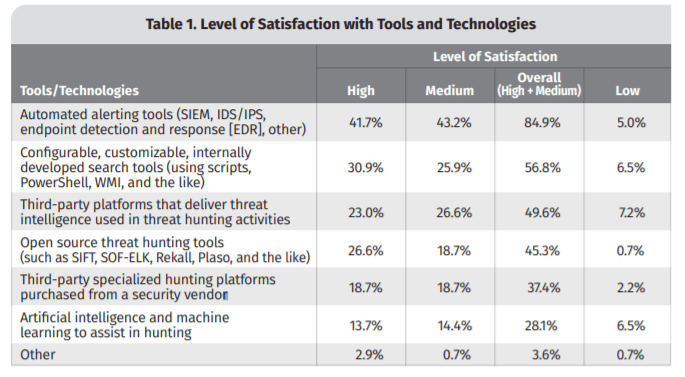
For 2021, automated tools for SIEM, EDR, internally developed tools, threat intelligence third-party platforms, and artificial intelligence and machine learning were the main technologies used. In terms of tools that most organizations plan to use, the top 3, according to SANS Institute, would be automated SIEM/EDR tools, open-source threat hunting tools, and third-party hunting platforms from cybersecurity vendors.
What about tomorrow?
I’m sure that, in the next period, the focus will move towards a greater use of artificial intelligence and machine learning, third-party hunting platforms developed by cybersecurity vendors, and even open-source threat hunting solutions. Third-party threat intelligence platforms and internally developed search solutions will probably remain valuable malware hunting assets as well.
Aligned with both the market tendencies and our vision of the future, the Heimdal™ products can be combined as SIEM and EDR, and they also have artificial intelligence at their core, which allows us to always be one step ahead of cybercriminals. Much more about this – below.
Malware Hunting in the Heimdal™ Suite
How does Heimdal™ tackle malware hunting? Well, we have, of course, a multi-layered approach, ensuring malware hunting through various modules of our suite: Threat Prevention, Next-Gen Antivirus, Ransomware Encryption Protection. We will soon add to these a standalone malware hunting sandbox and a malware hunting sandbox feature for the Email Security product.
Threat Prevention Intelligence
Heimdal™ Threat Prevention powers an AI-driven Predictive DNS module which, based on the origin and destination of DNS requests, proactively examines traffic and filters all network packages. Compatible with any existing Antivirus software, Heimdal™ Threat Prevention can block malicious domains and communications to and from C&C, and malicious servers.
Furthermore, by recognizing patterns of malicious domain requests, our award-winning system determines the endpoints that are most likely to have been affected by malicious scripts or malware. The system administrator will treat the identified computers as possibly infected, requiring additional investigation: hereafter, they will be inspected for threats either manually or automatically.
To give you an idea of what companies risk without DNS threat prevention, I’ll only mention that, during this year, our solution blocked 417 million malicious domains – out of which 414339 were newly created.
Next-Gen AV and REP For the Win
When talking about malware hunting, a good antivirus is, naturally, a must. Heimdal™‘s Next-Gen AV combines both classic and innovative approaches to identify threats like ransomware, hidden backdoors, rootkits, brute-force attacks, and undetectable malware. It can be used in conjunction with the Threat Prevention module to provide all-around security, thanks to TTPC, a feature that allows the AV to quarantine processes that Threat Prevention flags as malicious.
The product uses four stages of detection to ensure detection of even the most complex threats: during stage 1, the suspicious files are compared to a locally stored database and are then scanned in stage 2 with the help of some clever machine-learning algorithms.
Stages three and four imply hidden backdoor scanning, listening in for malicious Command & Control connections, but also the execution of the files that appear suspicious in Heimdal™’s sandbox environment.
Only this year, our Next-Gen AV flagged out 493627 infections and 54476 suspicious files – the most dangerous threats we encountered were viruses (154734), trojans (102484), and worms (92501).
REP (Ransomware Encryption Protection), on the other hand, is one of our latest additions to the Heimdal™ portfolio and a formidable ally in the fight against one of today’s biggest cyber threats – it has already detected and blocked 5518 malicious processes from the beginning of the year.
How does it work? 100% signature-free, REP protects devices from ransomware-related encryption attempts, expanding the capabilities of typical antivirus software. Actually, it can be used in addition to any antivirus on the market, allowing you to prevent and defend your endpoints from any ransomware strain – already known or newly discovered.
REP continuously scans active processes, mapping out each process event and looking for encryption patterns in the background, and gathers details about the process command line arguments, the network connections (IP Address and Port), read/write operation count at the moment of detection, as well as the process tree from the suspicious process with trace-back to the root process.
The Threat Prevention, Next-Gen AV and REP modules can be used separately or combined within Heimdal™‘s EPDR service, according to one of 2021’s most important cybersecurity market trends: unification.
A Standalone Sandbox for Increased Accuracy
This product is still in development, but I can already tell you that it will be a terrific tool for anyone looking for a comprehensive malware analysis. The sandbox will be a system that simulates a user’s PC, allowing you to run malware safely, in a secure environment.
It will have certain detection and interpretation capabilities, but it will function similarly to a virtual machine. When running a malware in the sandbox, you will get information related to statistics, spawned processes, HTTP/HTTPS connections and much more.
Enhanced Email Security
Email Security is a module that already assists our customers in proactively preventing even the most sophisticated email exploits that pose a threat to businesses by evading regular spam filters and antivirus solutions.
By acting as a man-in-the-middle between the Internet and a company’s email server (for inbound mail flow) or vice versa, Email Security safeguards both inbound and outbound mail flows and keeps all malicious emails out of our clients’ inbox, automatically removing attachments that contain malware, filtering emails coming from malicious IPs or domains, as well as those containing malicious URLs.
For example, from May until October, Email Security detected 5,609,641 spam emails, 203846 emails containing a virus, and 5946 emails with malicious attachments.
Very soon, our solution will be enhanced with a version of the sandbox I’ve mentioned above, that will act as an additional step in the malware hunting process. Email Security will automatically send the attachments in the mail flow to the sandbox, which will check for anything malicious.

- Granular telemetry across endpoints and networks.
- Equipped with built-in hunting and action capabilities.
- Pre-computed risk scores, indicators & detailed attack analysis.
- A single pane of glass for intelligence, hunting, and response.
What the Future Holds
Malware hunting is crucial for any company’s cybersecurity posture, and, thanks to the AI and ML technologies that gain more and more ground each day, will continue its evolution in what is already a fight against professionalized cybercriminals. Its benefits are simply undeniable: breaches and breach attempts decrease, smaller attack surface with limited attack vectors, swift incident response, increased accuracy and overall risk reduction.
If you’re still wondering whether threat / malware hunting would be a good addition to your company’s strategy or not, I’m only asking you this: would you go blindfolded to a battle? I certainly hope your answer is negative and I promise we’ll keep crafting our products so as to become your technology of choice in today’s – and tomorrow’s – ever-changing threatscape.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










