Contents:
Key takeaways:
- What is a SOAR and what functionality does it offer?
- SOAR vs SIEM vs XDR: What are the main differences?
- Pros and cons of seven leading SOAR products
For almost a decade, businesses around the world have made security orchestration, automation, and response (SOAR) products a crucial part of their cybersecurity posture.
There are plenty of good reasons why. SOAR tools enable organizations to build automated policies that can respond to common security issues and prevent data breaches. This frees up security operations teams to focus on the most critical and anomalous alerts, creating a much more effective overall response.
But not all SOAR products are built the same. So what are the best options on the market? How do you decide which is right for you? And do you still need a traditional SOAR in 2025? We explain everything you need to know.
What is SOAR? Recapping the Basics
SOAR products have been on the market for several years now. Over that time, they’ve become an incredibly common part of enterprise security. In fact, the market was recently valued at $1.27 billion, a figure which is projected to grow to $3.48 billion by 2030.
Over that time, a standardized set of tools and functionality has emerged. The goal of these key features is to streamline security operations by enabling organizations to:
- Consolidate security information and data from several IT environments and security tools
- Build automated responses to common IT threats, like ‘new device/location login’
- Use out-of-the-box ‘playbooks’ to build common incident response policies, processes, and automation
- Analyze SIEM data to identify patterns and detect malicious activity
- Check security alerts against pre-defined rules to decide which threats are most critical. Then, the security team can respond to these alerts and let automation handle the low-risk issues
- Correlate event and other security data across on-premises, cloud, hybrid, and complex multi-cloud environments
But while most SOARs will offer this standard feature set, the devil is very much in the details. In particular, there is significant variation in how widespread the customization, playbook, and security automation features really are.
Therefore, it’s important to understand the unique requirements of your business to decide which tools are best suited for you.
SOAR vs SIEM vs XDR: What’s the Difference?
Until a few years ago, SOAR products were the only game in town when it came to automating repetitive tasks and vital security operations. Now, the situation is a bit more complex. But to understand why – it’s first helpful to explain the difference between SOARs, SIEMs, and XDRs:
- Security information and event management (SIEM): SIEM products traditionally focus on collecting, consolidating, and analyzing security information from around the IT environment. This is generally done through log management – an analysis of user behavior via log files.
- Security orchestration, automation, and response (SOAR): SOAR products are designed to take information from SIEMs and automate the response. SIEMs and SOARs have historically been designed to work together, and vendors generally offer both products under separate licenses.
- Extended detection and response (XDR): XDR is a much more recent innovation. It combines SIEM and SOAR functionality into one integrated dashboard and can also bring in a range of other security features, such as endpoint detection, threat intelligence management, and more.
Read more: XDR vs SIEM vs SOAR: A Comparison
Today, businesses are increasingly beginning to prioritize security tools that offer more functionality under fewer licenses. That means consolidated products like XDRs are quickly becoming the go-to standard for effective cybersecurity.
In practice, this means a SOAR product isn’t always the best way to get SOAR functionality. And while SIEMs and SOARs are traditionally quite distinct, the direction of the market means that there is now a substantial gray area between the two.
In 2025, it’s helpful to take these product categories with a pinch of salt, since the precise features on offer will be unique to each product. Nonetheless, an XDR will generally offer a more comprehensive, consolidated approach than a traditional SOAR.
Read more: SOAR vs XDR – What Type of Security Approach Benefits Your Organization?
The 7 Best SOAR Products: Pros, Cons, and Reviews
On this list, you’ll see that I didn’t limit myself to choosing traditional SOAR tools alone. My focus was on presenting solutions that solve the issues SOAR tools focus on and more.
-
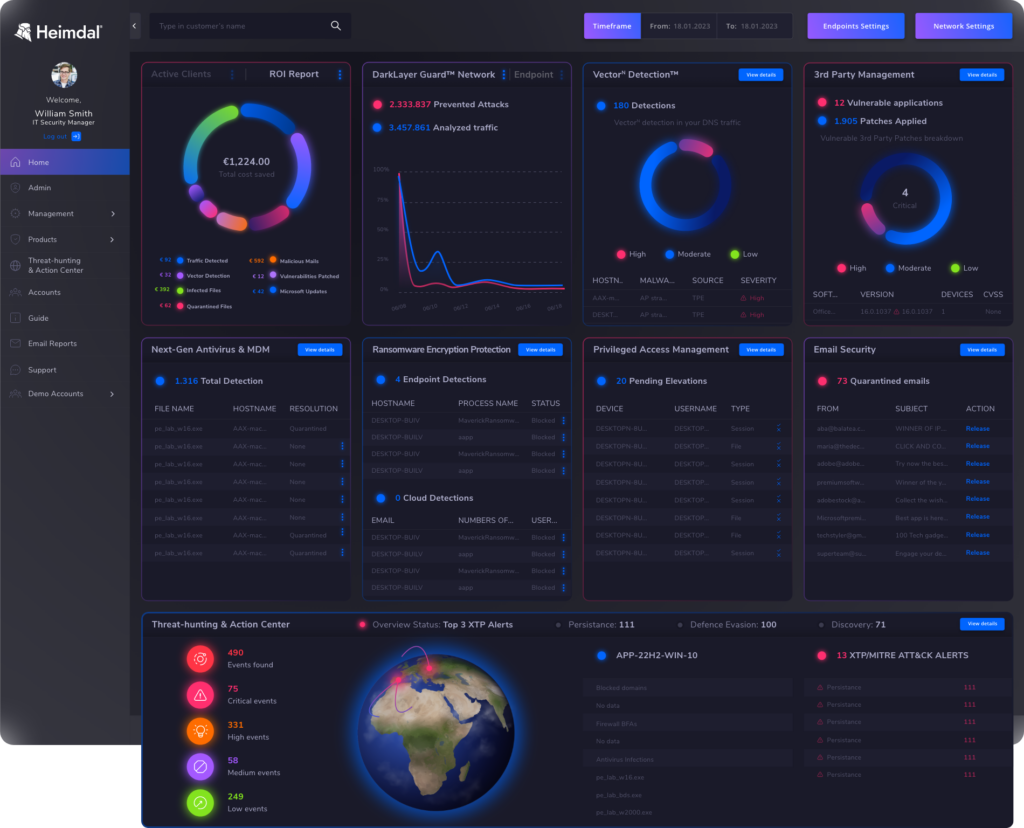
Heimdal
Heimdal’s XDR platform goes beyond any regular SOAR tool’s capabilities. Traditional SOAR tools focus primarily on automating security workflows and integrating various security tools. They need significant customization and may not offer the same level of integrated threat detection and response capabilities as Heimdal’s XDR does.
Read more: Extended detection and response: Download the full solution brief
Here’s what Heimdal brings to the table:
Integrated Security Suite
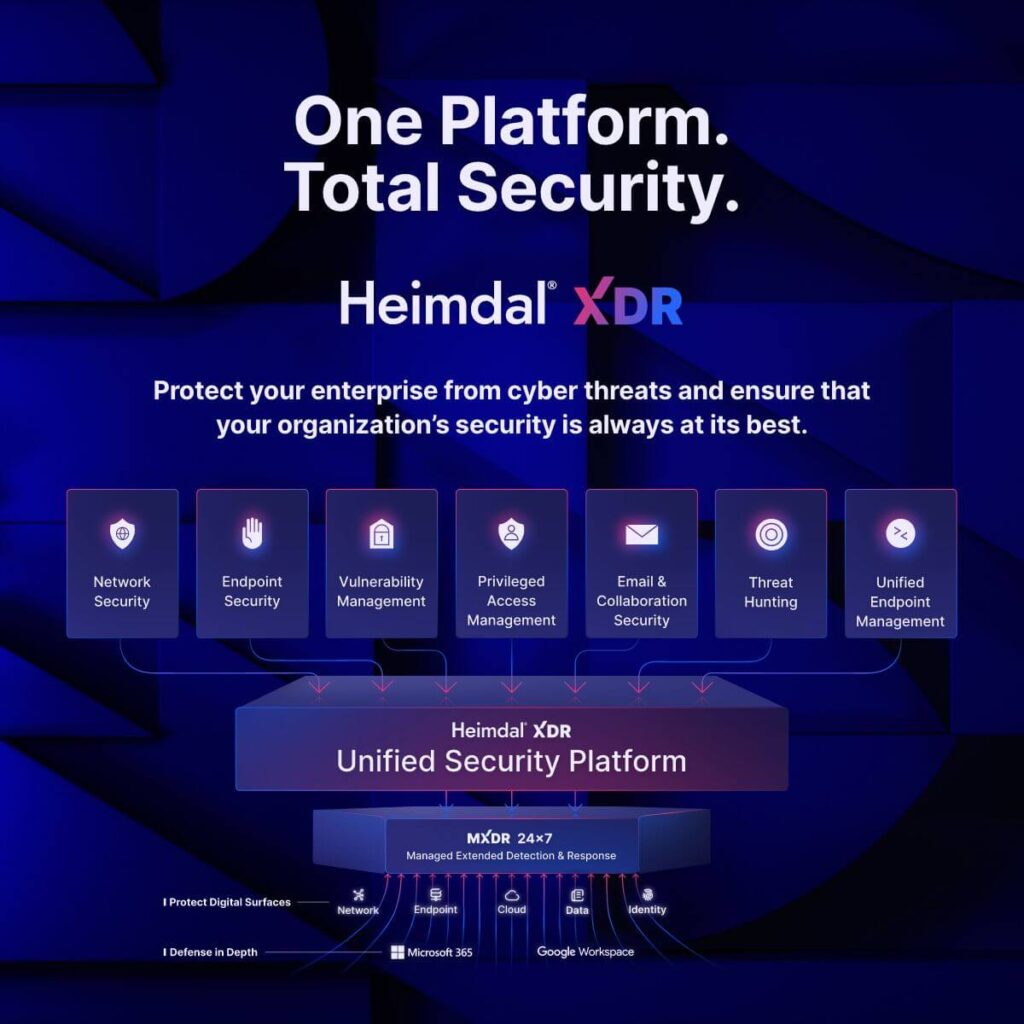
Heimdal XDR is more than just a leading security tool: It’s a comprehensive and integrated security platform, with the widest possible range of security tools available in a unified dashboard. This approach eliminates cybersecurity silos and agent fatigue.
Advanced Threat Detection
By using AI and machine learning, Heimdal XDR provides real-time threat detection across endpoints, networks, and cloud environments. Your threat hunting and incident response teams will be able to detect and rapidly respond to any threat.
Proactive Threat Hunting
Sometimes automated responses are not enough. That’s why Heimdal XDR empowers security teams with threat hunting capabilities. Its Extended Threat Protection (XTP) engine and native threat intelligence tools help discover hidden threats.
Automated Incident Response
If there’s a security incident, you want to move fast and stop the infection before it spreads. Sometimes, this means seconds. Heimdal XDR streamlines operations and incident response with automated custom workflows and guided remediation, enabling rapid and effective action to minimize the damage.
By adopting Heimdal’s XDR platform, organizations benefit from a comprehensive, adaptive, and user-friendly security solution that effectively addresses the complexities of today’s cyber threat landscape.
Pros:
- Easy to deploy and configure according to reviewers on Capterra
- Straightforward reporting for compliance
- Fast and effective technical support
It’s a fantastic tool. I recently (last 12 months) moved 2,000 endpoints from SentinelOne Complete to Heimdal and couldn’t be happier. The Heimdal SOC is highly communicative and extremely helpful, which was not my experience at all with Vigilance and SentinelOne.
Having all of the other Heimdal features is also a huge bonus. Their 3rd party patching module is the best I’ve seen so far.
– Heimdal user review, via Reddit
Cons:
Could seem pricey for smaller companies. Get a fast, custom price estimation for Heimdal’s XDR.
SOAR Without the Stress
Heimdal gives you the full range of security automation tools, seamlessly integrated into our complete security platform. Manage automations, threat detection, vulnerabilities, and more from the same integrated dashboard. Get in touch to find out more.
-
Microsoft Sentinel
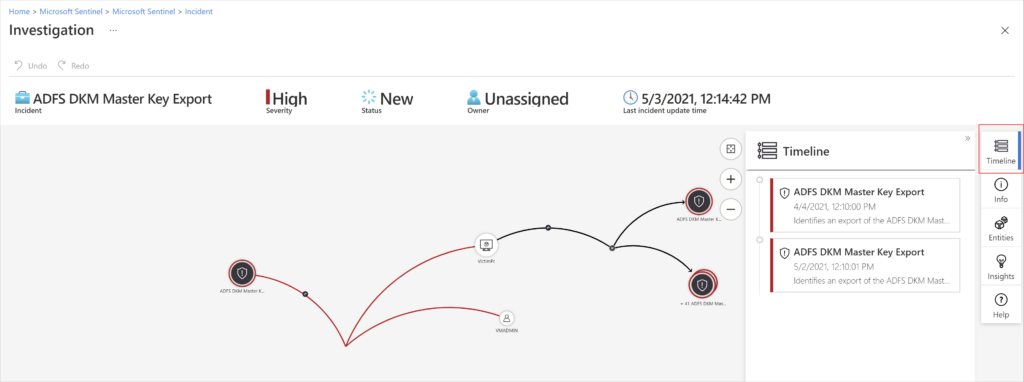
Microsoft certainly needs no introduction, and there’s a good chance you’re already familiar with their leading SOAR product: Sentinel.
Like many tools on this list, Sentinel isn’t a traditional SOAR. First and foremost, it’s a security information and event management (SIEM) platform, with extensive SOAR functionality, including a wide range of playbooks, connectors, and automation.
Like most Microsoft products, Sentinel has a broad feature set and advanced SIEM/SOAR capabilities. However, the price and complexity of these features mean they’re generally better suited to larger companies with established security teams.
Pros:
The threat detection and response capabilities via the playbooks are great. Threat intelligence signals also help by providing realtime data from global sources.
– Microsoft Sentinel user review, via Software Reviews
- Microsoft integration: Like all Microsoft products, the main benefit of Sentinel is its smooth integration with the wider Microsoft ecosystem.
- Advanced automation: Despite not being a SOAR product, Sentinel offers capabilities to automate your overall security operations.
- Playbooks: Many reviewers have praised Microsoft’s extensive playbooks, which allow you to plan an effective incident response.
Cons:
Some users find the user interface challenging to navigate, and understanding its features may take time. This comprehensive solution comes with a price tag.
– Microsoft Sentinel user review, via G2
- Complexity: Reviewers often describe Sentinel as a difficult tool to set up, customize, and manage. In particular, it can be difficult to integrate the platform with third-party products and configure custom reports.
- Pricing: Sentinel suffers from both high costs and confusing pricing. There are several different plans and the consumption-based pricing can make predicting costs uniquely difficult, particularly at scale.
- Support: Microsoft’s support is generally delivered through its partner network. This means the quality and responsiveness of support can hugely vary depending on the MSSP you’re using.
Reviews:
- G2: 4.4/5 stars (289 reviews total)
- Software Reviews: 8.3/10 stars (59 reviews total)
- Gartner: 4.6/5 stars (220 reviews total)
-
Palo Alto Networks: Cortex XSOAR
Palo Alto Networks has a long heritage in the cybersecurity space and is one of the most well-known XDR providers. Cortex XSOAR is just one of the many security products the company offers and is the first traditional SOAR we discuss.
Like most Palo Alto Networks tools, Cortex XSOAR is a comprehensive SOAR platform, aimed squarely at enterprise customers. This means its users get access to some of the widest and most customizable security functionality on the market.
In particular, the product is noted for its extensive playbooks and AI functionality. But it’s also one of the most expensive and complex platforms on this list, meaning it’s far from the right SOAR solution for everybody.
Pros:
Saves a lot of manual work on incident management. Our playbooks make it easier for the analysts to prioritize incidents based on incident score, which the playbooks update based on feeds from third-party CTI sources.
– Cortex XSOAR user review, via G2
- Playbooks: Cortex XSOAR features particularly extensive playbooks, with pre-defined responses to several cyber threats available.
- Integrations: There are also some 750 integrations available, among the most extensive in the market.
- Threat intelligence: The product also features a separate threat intelligence module, which can help lend vital context to alerts.
Cons:
While strong, Cortex XSOAR can be fairly complex to get set up, and there’s an assumption you know how existing work is done. It also provides substantial customization, which means the process is costly and can potentially delay full deployment and optimization in rapidly developing environments.
– Cortex XSOAR user review, via Software Reviews
- Price: Cortex XSOAR is among the most expensive products on the market. This means it’s generally better suited to enterprise clients.
- Complexity: Reviewers often note the size and complexity of the product. While good for experienced security teams, this can be prohibitive for smaller companies with fewer expert resources.
- Performance issues: The product is also generally more resource-intensive than competitors, particularly when handling a high volume of inputs.
Reviews:
- G2: 4.5/5 stars (19 reviews total)
- Software Reviews: 7.8/10 stars (26 reviews total)
- Gartner: 4.6/5 stars (65 reviews total)
-
Cisco XDR
If you want a security product built for the most complex enterprises, Cisco XDR is a popular place to start. And like many providers on the list, their SOAR functionality has now been rolled into a broader XDR product.
This combines advanced threat detection functionality with sophisticated tools to automate tasks and customize your security response.
The Cisco ecosystem certainly has its admirers – but their products are generally designed to work alongside other products from the same vendor.
Combined with the size and complexity of the product, this makes Cisco something of an ‘all-or-nothing’ option. If you’re not already bought into the vast security ecosystem, you may find other products on this list to be cheaper, simpler, and better adapted to your specific IT environment.
Pros:
Firstly, the ability to view all of the security information in a single pane is super important for our organization. It makes our lives easier and decision-making quicker. Secondly, the machine learning and AI capabilities are more robust than other competitors in the market today.
– Cisco XDR user review, via Gartner
- Integrated dashboard: As an XDR platform, this product can effectively centralize threat alerts from multiple security layers. This creates a more holistic security approach and requires fewer overlapping licenses.
- Advanced threat hunting: Cisco XDR offers advanced machine learning and AI capabilities, creating a robust and proactive response to emerging threats.
- Fast automations: Reviewers often praise Cisco XDR for its ability to quickly contain a wide range of known and unknown threats.
Cons:
The user interface is rich, however sometimes it feels cluttered and overwhelming. Realtime alerts occasionally generate false positives.
– Cisco XDR user review, via Gartner
- Complexity: Cisco XDR is a complex product with a steep learning curve. For that reason, it’s best suited to larger organizations with developed security teams.
- Cisco-specific: Like all Cisco products, XDR is primarily designed to work with other Cisco security products. This means some features are less effective when used alongside third-party tools.
- Alert fatigue: Many reviewers have also mentioned the high volume of alerts and false positives with this product. This can make it difficult to identify the genuine threats.
Reviews:
- G2: 4.8/5 stars (2 reviews total)
- Gartner: 4.4/5 stars (22 reviews total)
-
IBM Security: QRadar SOAR
IBM is another stalwart of the cybersecurity scene, and its QRadar platform is another example of a classic SOAR. It has existed in various forms for almost a decade, beginning with the acquisition of Resilient Systems in 2016. The product was then renamed to IBM Security SOAR in 2021 and became QRadar later that year.
QRadar takes a more traditional SOAR approach than many providers on this list, focusing specifically on automation. This means there are no additional monitoring, detection, or other security tools – unlike many of the XDRs on this list.
Though much of this extra functionality can be added through IBM’s QRadar SIEM, this will ultimately increase complexity and require more licenses.
Pros:
The platform allows us to build dynamic workflows to automate security processes. This approach helps us to create customized processes that meet our specific needs and SLAs. QRadar SOAR also has a user-friendly interface which makes it easy for us to understand the flow of security processes and track progress.
– QRadar SOAR user review, via Software Reviews
- Playbooks: QRadar SOAR offers extensive incident response playbooks, helping security teams plan their response to a wide range of potential security threats.
- Customization: The product’s dashboard also has wide customization options, making this an effective choice for more complex multi-tenant environments.
- Strong UI: Many users have praised the UI of the product, saying it’s intuitive and easy to use.
Cons:
While the interface is user-friendly, there is a learning curve associated with configuring and optimizing QRadar SOAR to suit your specific requirements. Adequate training and onboarding are essential to make the most out of the platform. As with any enterprise-grade security solutions, the cost may be a concern for smaller organizations.
– QRadar SOAR user review, via Gartner
- Pricing: Like most IBM products, QRadar is among the most expensive solutions on the market, aimed specifically at enterprise customers.
- Learning curve: The wide functionality on offer can also create a high learning curve for new users.
- SOAR only: Unlike many providers, QRadar SOAR is not an XDR product. This means alternative licenses (e.g. QRadar SIEM) will be needed to get the full scope of threat detection and response functionality.
Reviews:
- G2: 4/5 stars (2 reviews total)
- Software Reviews: 7.7/10 stars (29 reviews total)
- Gartner: 4.3/5 stars (11 reviews total)
-
Rapid7: InsightConnect
Rapid7 was founded in 2000 and is today headquartered in Boston, USA. Its SOAR product, InsightConnect, offers the classic feature set of orchestration and automation capabilities.
While this specific solution only offers SOAR functionality, Rapid7 packages it as part of the wider ‘Insight IDR platform’, which includes a much wider range of security protections.
Pros:
I really like the customization capabilities in the platform. You’re able to customize the workflows to make sure you’re getting the automation you need completed. These are multiple plugins you can tie into your workflows that will help with ensuring automation is smooth and efficient.
– InsightConnect user review, via Gartner
- Operations focus: The product is particularly praised for its ability to quickly integrate threat intelligence into your everyday workflows in order to improve security operations.
- Customization: InsightConnect is also highly customizable, with multiple plugins enabling a wide range of automations.
- Threat intelligence: Reviewers also regularly praise the quality and responsiveness of the threat intelligence platforms. InsightConnect offers real-time visibility into a wide range of contextual signals from across the cybersecurity community.
Cons:
The ease of use could be improved. Depending on how custom your workflows need to be, make sure you or someone on your team knows at least one scripting language well.
– InsightConnect user review, via Gartner
- Integrations: Many users have mentioned that the product has fewer out-of-the-box integrations when compared to other competitors.
- Complexity: The complexity and UI of the product is another common challenge, with many reviewers noting that it may require specialist security teams to monitor.
- Reporting: Some reviewers have noted that the reporting functionality could be more extensive.
Reviews:
- Gartner: 4.8/5 stars (14 reviews total)
- G2: 4/5 stars (5 reviews total)
-
Fortinet: FortiSOAR
Fortinet was founded in 2000 and is based in California. It’s a SOAR rather than an XDR, meaning the main focus is on automation rather than detection. Nonetheless, the automation and playbook functionality is more extensive than many providers.
Like most classic SOARs, FortiSOAR is designed to integrate with a wider suite of Fortinet products, including FortiGate, FortiAnalyzer, and FortiSIEM. Collectively, these offer comprehensive security coverage – but it will require numerous licenses to get the full feature set.
This is unlike the XDR products on this list, which generally consolidate SOAR, SIEM, and more into a single license.
Pros:
The playbook editor in FortiSOAR allows us to create tailor-made workflows to meet specific SOPs of the customer, which enhances our efficiency and consistency in incident response.
– FortiSOAR user review, via Gartner
- Integrations: FortiSOAR features over 350+ integrations, more than most SOAR products. Users particularly praise this wide compatibility with third-party tools.
- Playbooks: The product also offers some 160+ playbooks, which enable security teams to easily plan responses to common incidents, without the need for human intervention.
- Scalable approach: FortiSOAR is generally well suited to organizations of varying sizes, unlike many of the more enterprise-focused alternatives we discuss. This makes it a good choice for medium and large-sized businesses on an upward growth trajectory.
Cons:
It requires more dedication and quite a bit of time to learn the initial setup and customization and to develop expertise. It would be quite a learning curve to fully utilize the features provided, which could be quite time-extensive.
– FortiSOAR user review, via Gartner
- Customization: While the pre-built playbooks are effective, some users note that more advanced customization may be a challenge.
- Setup complexity: User reviews also mention that the product has a particularly steep learning curve, and that it may take some time for users to set up.
- SOAR-only: FortiSOAR does not offer threat detection and monitoring capabilities; these are covered in separate Fortinet products like FortiSIEM. This requires more products and licenses when compared with the more straightforward XDR products available.
Reviews:
- G2: 5/5 stars (3 reviews total)
- Software Reviews: 7.5 stars/10 stars (22 reviews total)
- Gartner: 4.9/5 stars (115 reviews total)
Soar higher with Heimdal
SOAR functionality is a crucial part of an effective cybersecurity posture. But on its own, these products aren’t enough to keep your organization safe. If you want a consolidated approach that combines classic SOAR features with threat intelligence, monitoring, and detection – the best approach is an XDR.
Read more: An Essential Guide to XDR Software
Ultimately, it is possible to get the same cybersecurity coverage as an XDR simply by combining SOARs, SIEMs, and other products. However, the resulting solution is going to be more complex, expensive, and difficult to manage than a straightforward XDR license.
But even the XDR products on this list aren’t all built the same. Most combine SOAR, SIEM, and threat intelligence functionality. But products like Heimdal take it even further. In fact, we combine this XDR feature set with a whole range of other tools, including network security, email security, vulnerability management, privileged access management, and more.
Taken together, these features offer the widest cybersecurity platform on the market. If you want a consolidated, focused, and low-cost approach – this is by far the best place to start.
Check out our XDR page to find out more.
FAQs: SOAR tools
What is the Difference Between SIEM and SOAR Tools?
SIEM and SOAR tools are designed to work together, but they traditionally have a different focus. SIEMs specialize in identifying suspicious activity across the IT network, usually through an analysis of user behavior via log files. SOARs, on the other hand, are designed to take the alerts that SIEMs generate and trigger automated responses, based on pre-defined rules and policies.
Can SOAR Replace SIEM?
SOARs and SIEMs are traditionally designed to do different jobs, so neither should replace the other. However, many vendors are now combining the functionality of both products into a single license and product – generally called an XDR. These products can replace both traditional SOARs and SIEMs, while reducing overall costs and confusion.
Is Microsoft Sentinel a SIEM or SOAR?
Microsoft Sentinel is fundamentally a SIEM product, but it also offers a wide range of SOAR functionality. Many organizations prefer this approach to having a separate SIEM and SOAR. Nonetheless, this is still more limited than the functionality available in an XDR.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security