Contents:
A privilege escalation attack can have critical effects. Organizations must ensure that the security measures they implement are strong and regularly updated in order to prevent these types of cyberattacks.
In this article, we will help you prevent such attacks, teaching you what measures you should take now, so that your company can be safe from the lurking danger of privilege escalation.
Key Takeaways
- Implement Strong Password Policies: Use complex, unique passwords and eliminate default credentials to minimize entry points for attackers.
- Enforce Multi-Factor Authentication (MFA): Adds a second layer of security, preventing unauthorized access even if passwords are compromised.
- Use Automated Patch Management: Regularly update and patch software to close security gaps that could be exploited.
- Deploy Privileged Access Management (PAM): Automate and monitor privileged account activities to limit misuse.
- Conduct Regular Vulnerability Scans: Identify and fix potential weaknesses before they can be exploited.
How To Prevent Privilege Escalation Attacks
As cyber threats become more advanced, preventing privilege escalation attacks requires a multi-layered approach.
The following are some of the best practices for preventing privilege escalation attacks.
1. Set a Strong Password Policy
How many times did you come across passwords that were so simple that anyone could guess?
In your organization, you have to implement a well-defined password policy that everybody should follow.
Strong passwords should be long enough, have a mix of letters, numbers, and symbols that makes it hard to guess, and it’s not the employee’s birthday or the name of their pet.
Not to mention that default credentials on routers, printers, or IoT devices should not even exist.
Even if your applications and operating systems are well secured, a single overlooked router with default credentials could provide cybercriminals with the access they seek.
2. Use Multi-Factor Authentication (MFA)
Add an extra layer of security to user accounts, especially for lower-privilege ones, and such prevent unauthorized access through compromised credentials.
Broken authentication is one of the most common vulnerabilities that lead to user account compromise, ranking second on the list of OWASP Top 10 after injection attacks.
Typically, threat actors break authentication by obtaining access to web session data or acquiring login information through the brute force hacking method or social engineering attacks.
This emphasizes the importance of setting up complex and hard-to-guess passwords and protecting all accounts with Multi-Factor Authentication.
Although it may seem intuitive to allocate different levels of protection in accordance with user levels of rights, the secret to avoiding privilege escalation actually lies in the security of user accounts with lower privileges.
The inability to access lower-level accounts prevents privilege escalation from starting in the first place.
3. Provide Cybersecurity Training for Your Employees
To put it shortly, human error is often a weak link in security defenses, and the same can be said in the case of a privilege escalation attack.
Threat actors might target and trick your employees with phishing or spear-phishing attacks in order to click on a malicious link to provide their credentials and many more. Employees’ cybersecurity awareness should be a top priority for all organizations.
Educate your employees on identifying phishing and social engineering tactics, and the chances of a privilege escalation attack happening decrease.
4. Deploy Traffic Filtering Solutions
Domain name-level (DNS) threats are frequent in today’s cybersecurity landscape.
A high-quality traffic filtering tool is required to keep these away. And since today’s cyber world lives in the cloud, you will need a solution that can face cloud challenges like our Heimdal® Threat Prevention.
Combining machine learning, AI-based prevention, and cybercrime intelligence, it has the power to detect and stop both emergent and hidden cyber threats with 96% accuracy.
5. Automate Your Patch Management Process
Ensure all software is up-to-date by automating patch management, reducing the chances of attackers exploiting unpatched vulnerabilities.
This is one of the fastest and most efficient best practices you can implement!
As we mentioned before, a privilege escalation attack usually happens because hackers abuse a vulnerability in the OS or a software flaw. So, how to stay safe if your software is outdated?
You can prevent privilege escalation if you keep your software always patched with the latest released security updates.
The best way to thwart any type of cyberattack is to reduce the likelihood that an attacker will discover a vulnerability that can be exploited.
This will surely be a tiresome process if manually managed and even impossible to do it properly. And here comes into play an automated Patch Management solution like ours Heimdal® Patch and Asset Management, that will help you automate your vulnerability management.
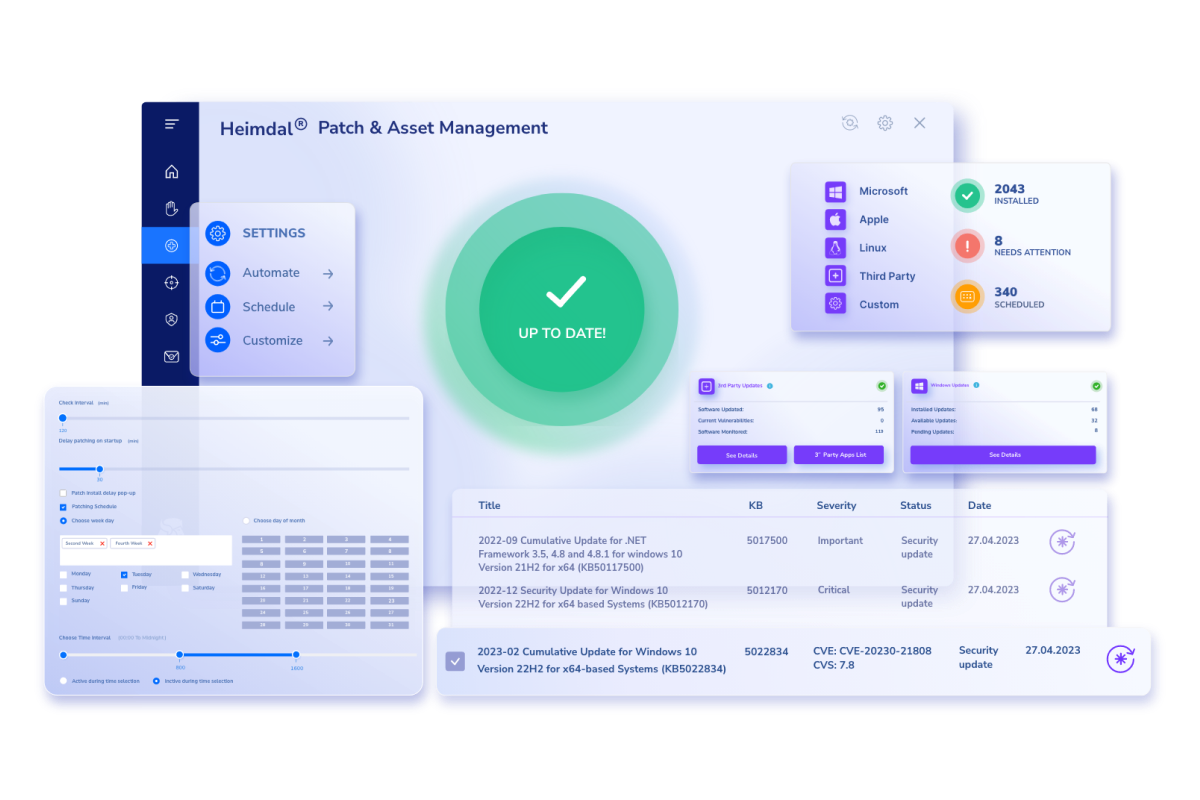
Our product will help you keep your Microsoft, macOS, Linux, third-party, and even proprietary apps updated. All with a single product, within a single dash.
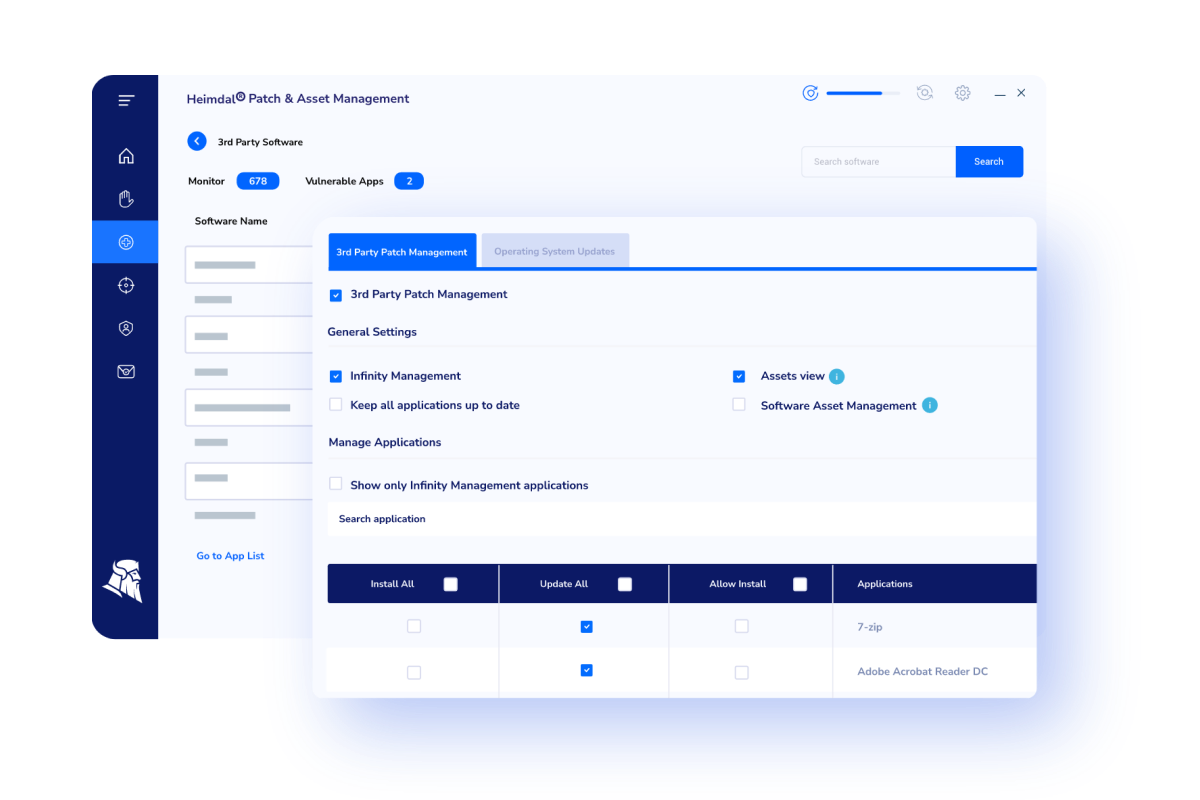
What’s even cooler with this solution is the end-user-vendor-waiting time, this meaning that in less than 4 hours every patch, hotfix, rollup, or update is uploaded in your Heimdal cloud already adware-cleaned, tested, and repackaged, and ready to be deployed.
6. Conduct Regular Vulnerability Scans
Identify and mitigate potential weak points in your infrastructure by performing consistent scans and addressing detected issues immediately.
It is significantly more difficult for an intruder to enter the network when all the IT infrastructure’s elements are regularly scanned for vulnerabilities.
Vulnerability scans detect misconfigurations, unauthorized modifications, unpatched or insecure operating systems, and apps, and other weaknesses before hackers do.
7. Use an Automated Privileged Access Management Solution
Implement an automated PAM solution to monitor, manage, and limit access to sensitive resources, enforcing the principle of least privilege.
A good counterattack method of privilege escalation starts always with a good privileged access management strategy.
This could only be truly efficient through an automated tool that will help you monitor and protect privileged accounts from either insider or external threats.
An automated PAM tool like Heimdal® Privileged Access Management will let you escalate and deescalate rights from anywhere in the world from your Heimdal® Dashboard and even from your phone.
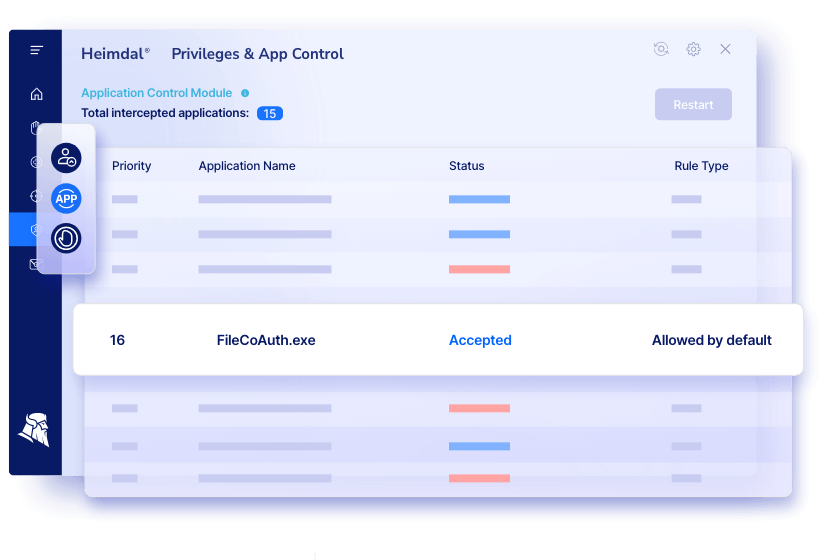
It also features detailed reports of an incident that will help you both with audit requirements and also with investigating what happened on a machine.
It is recommended to use it with Heimdal® Application Control which allows you to block or allow application execution in various ways: by file path, certificate, vendor name, publisher, MD5, and more.
Supporting a granular approach, Application Control combined with the PAM solution lets you customize admins sessions, this combo making for a shield against cyberattacks that target sensitive memory areas, a shield that won’t let hackers move laterally across the network, and also business assets will be well safeguarded.
Here’s a tip you might not want to miss: when used with Heimdal® Next-Gen Antivirus, the PAM tool will allow the automated de-escalation of rights if a threat is detected on the machine.
8. Enforce the Principle of Least Privilege
Restrict user permissions to only what is necessary for their roles, minimizing the risk of privilege escalation and limiting malware spread.
A PAM strategy should of course be always based on the principle of least privilege, meaning that users and applications or services should have restricted access, or better said, the minimum required access to organizational resources to complete a task.
This will also be efficient to not let the malware spread laterally across the network and infect other systems too.
By following these strategies, organizations can greatly reduce the risk of privilege escalation attacks and improve their overall security posture.
How to Detect Privilege Escalation?
In most cases, pattern recognition, looking for outliers, and observing unusual activities are involved when we talk about privilege elevation detection.
Unfortunately, due to its unpredictable nature, privilege escalation can be very difficult to identify. If a malicious actor enters the network successfully at any point, they can maintain ongoing access.
After obtaining credentials of any kind, the system recognizes them as authorized users.
Because privilege escalation incidents can take several weeks or even months, estimating the average time taken to spot an attack is challenging.
With a long dwell time, attackers can collect data, obtain credentials, and keep escalating privileges. Intruders typically cover their tracks (delete logs, mask IP addresses) before they are ready to complete their mission.
A Tool To Boost Your Security on All Plans: Heimdal® XDR
I hope you now know what to do to keep your networks safe from the dangers of privilege escalation attacks. In the articles, we recommended some tools, but did you know you can have them all within a single solution?
We created Heimdal® Extended Detection And Response (XDR), the widest cybersecurity platform currently available, to help companies like yours secure their endpoints and networks in the easiest way possible.
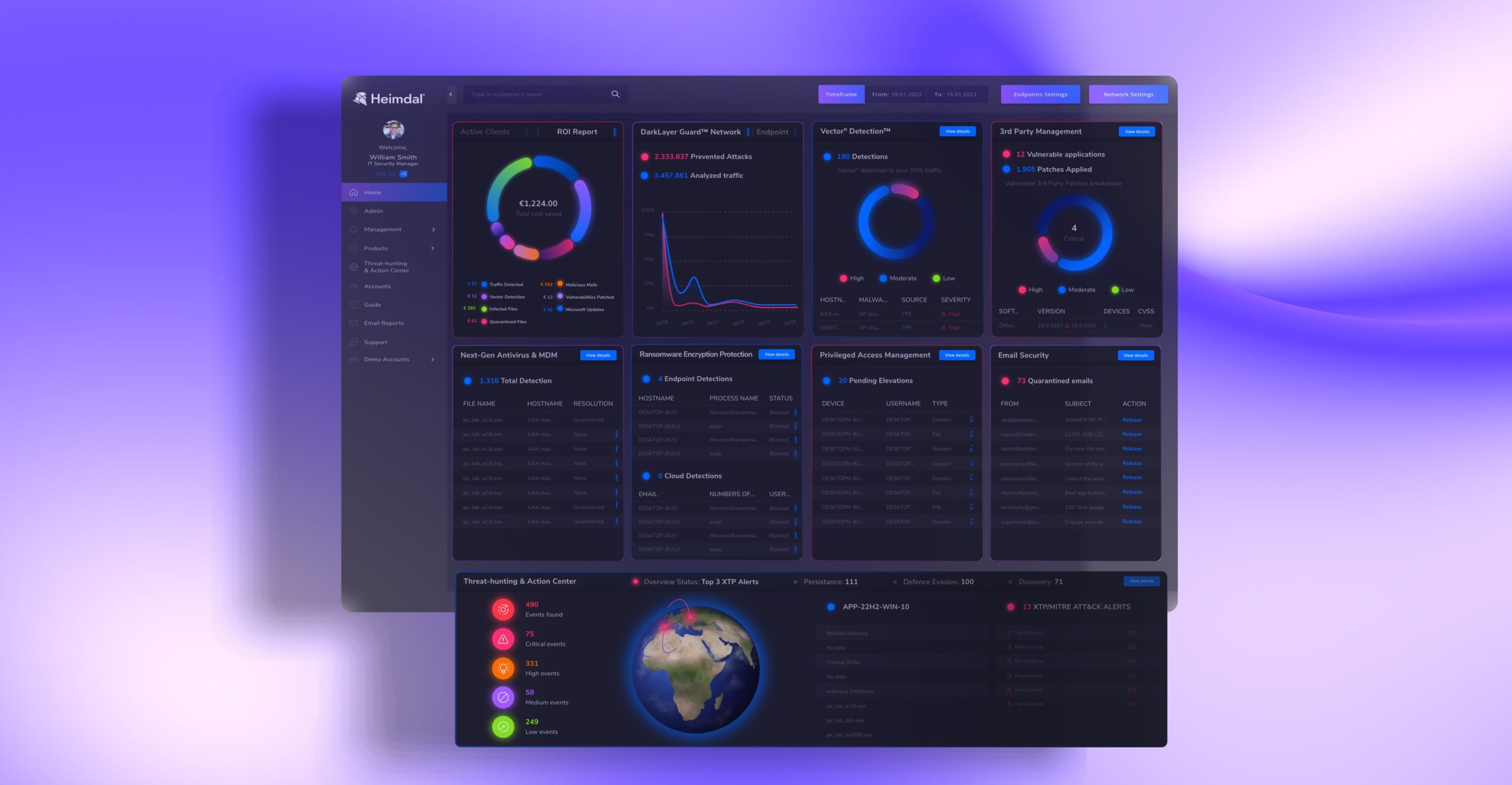
Here is a sneak peek into what our platform has to offer:
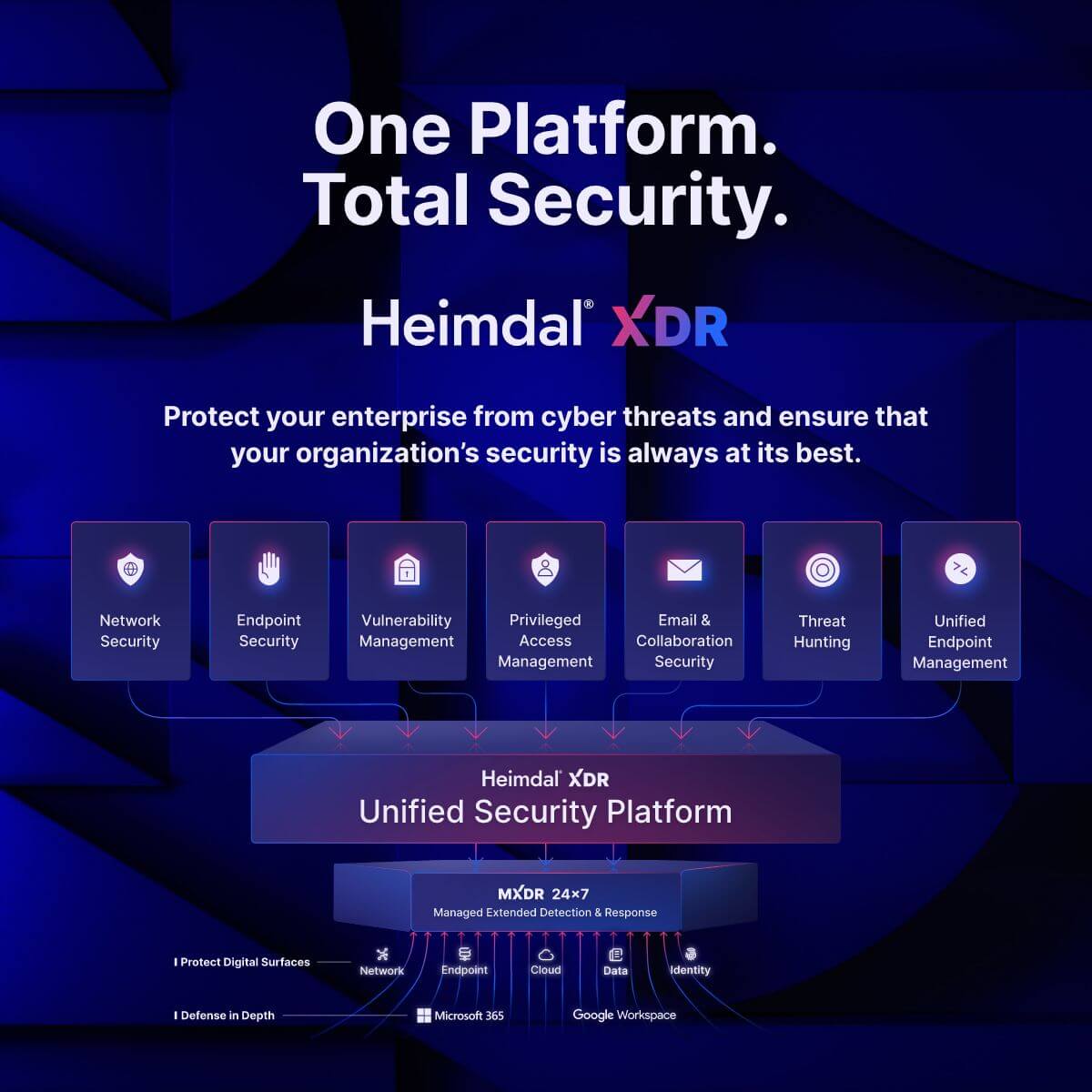
- Advanced Threat Hunting: Actively seek out hidden threats before they wreak havoc on your network.
- Automated Remediation: Let Heimdal handle the heavy lifting by automating responses to attacks, minimizing damage in real time.
- Multi-Layered Endpoint Detection: Protect every device with advanced endpoint protection that detects and neutralizes threats across your network.
- Threat Tracking Scans: Continuous scanning and tracking ensure no vulnerability goes unnoticed, keeping you a step ahead of attackers.
- Proactive Attack Prevention: Leverage predictive analytics to stop attacks before they even begin.
- Vulnerability Management: Identify and patch weak spots before they can be exploited.
- Patch Management: Streamline software updates and security patches to keep your infrastructure secure and up-to-date.
- Privileged Access Management: Safeguard your critical assets by controlling and monitoring access to sensitive systems.
- Email Security: Protect against phishing and malicious emails with powerful filtering and threat detection.
All of these tools accessible from one platform, customized for your company’s needs. If you’re interested into how it works, book a demo with one of our experts!
Wrapping Up
Given that privilege escalation attacks are among the most dangerous out there, having a solid incident response plan is essential.
In the event of a privilege escalation attack, the affected account needs to be isolated right away, the passwords changed, and then disabled.
The security team will then need to carry out a thorough investigation to determine the scope of the intrusion and identify the resources that were impacted.
A privilege escalation attack is a common threat to user data. This type of attack can cause data breaches, system crashes, and other damage. Make sure you stay safe and use the proper tools to safeguard your business’ critical assets.
Frequently Asked Questions (FAQ)
How Can Escalation of Privilege Be Prevented?
Preventing privilege escalation requires a multi-layered security approach that involves:
- Implementing the Principle of Least Privilege (PoLP): Limit user access rights to only what is required to perform their roles.
- Regular Patch Management: Continuously update and patch software to fix known vulnerabilities that could be exploited.
- Multi-Factor Authentication (MFA): Add an additional layer of security for privileged accounts to reduce the risk of credential-based attacks.
- Network Traffic Monitoring: Monitor for unusual activities and establish network segmentation to limit attackers’ lateral movement.
- Regular Vulnerability Scanning and Penetration Testing: Identify and fix misconfigurations or potential security gaps proactively.
- Employee Security Awareness Training: Train employees to recognize phishing and social engineering attempts, which are common methods for gaining initial access.
What Is the Best Defense Against Privilege Escalation?
The best defense against privilege escalation is to enforce the Principle of Least Privilege (PoLP) and combine it with comprehensive Privileged Access Management (PAM).
This ensures that users only have the minimum necessary permissions, reducing the impact of compromised accounts.
Additionally, using automated tools for real-time monitoring and auditing of privileged accounts helps detect suspicious activities before they lead to a breach.
What Is Privilege Escalation?
Privilege escalation is a type of cyber attack where an attacker gains elevated access to systems or resources beyond their initial permissions. There are two main types:
- Vertical Privilege Escalation: A low-level user (e.g., standard user) elevates their privileges to a higher level, such as an administrator or system account.
- Horizontal Privilege Escalation: A user accesses resources or data belonging to another user with the same privilege level, without elevating their own access rights.
Implementing robust access controls, regularly updating systems, and using PAM tools can significantly reduce the risk of such attacks.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security















