Contents:
DHCP, or Dynamic Host Configuration Protocol, is a network protocol that allows devices on a network to be automatically assigned an IP address. DHCP is used extensively in both home and enterprise networks, as it simplifies the process of configuring IP addresses for new devices.
In this article, we will have a closer look at how DHCP works, what are its main components, its benefits, and we will also analyze some of the security concerns associated with it. Let’s begin!
What Is DHCP?
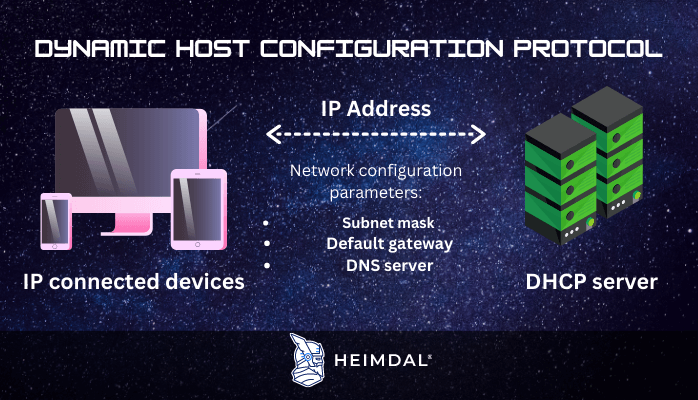
Dynamic Host Configuration Protocol (DHCP) is a network management protocol that is used to dynamically assign IP addresses and other information to each host on the network in order for them to communicate effectively.
DHCP automates and centrally administers IP address issuance, simplifying network administrators’ work. In addition to the IP address, DHCP assigns the subnet mask, default gateway, domain name server address, and other configurations to the host, making the network administrator’s job much easier.
What Is an IP Address?
An IP address is a unique number assigned to every computer and device on the Internet. IP addresses are used to uniquely identify computers and other networked devices. An IP address can be issued to a computer in two ways: either statically, or dynamically.
Assigning an IP address to a computer or other device manually, as was done in the early days of networking, is called using a static IP. Due to the complexity of this task, especially for large networks, a new way of assigning IP addresses emerged – the DHCP.
Assigning an IP address to a computer/device automatically and temporarily (is then replaced by a new one after its allocated time has passed), with the help of a server that supports the Dynamic Host Configuration Protocol – is called using a dynamic IP.
A DHCP server automatically assigns a computer with:
- An IP address;
- A subnet mask;
- Default gateway;
- And a DNS server.
A Brief History of DHCP
Dynamic Host Configuration Protocol (DHCP) was first defined in RFC 1531 (published in October 1993). The most recent version of the DHCP specification is RFC 2131 (published in March 1997). According to Javatpoint, DHCP is based on the Bootstrap Protocol (BOOTP), which was developed for diskless workstations. If there are any BOOTP clients on a network segment, DHCP servers can handle BOOTP client requests because DHCP is more advanced.
BOOTP introduced the idea of a relay agent that allowed BOOTP packets to be relayed across networks, using one central BOOTP server to serve hosts on numerous IP subnets. BOOTP, however, lacked a mechanism for reclaiming IP addresses no longer in use and required a manual process to add configuration details for each client.
Most home and small office routers support DHCP, and will automatically assign IP addresses to devices connected to the router’s LAN port(s). Many routers also have a “DHCP reservation” feature that allows you to statically assign an IP address to a specific device by its MAC address.
How Does DHCP Work?
DHCP works its ‘magic’ by automating the process of configuring devices on IP networks so that they can access network services including Domain Name System (DNS), Network Time Protocol (NTP), and any communication protocol based on UDP or TCP.
To facilitate communication between different IP networks, a DHCP server dynamically assigns an IP address and other network setup parameters (subnet mask, default gateway, DNS server) to each device on a network.
DHCP is a service that runs on a server. For instance, this could be a Microsoft or a Linux server, but it could also run on other routers such as a business router or a home router – each of these routers will have a DHCP service built into them.
The DHCP Process
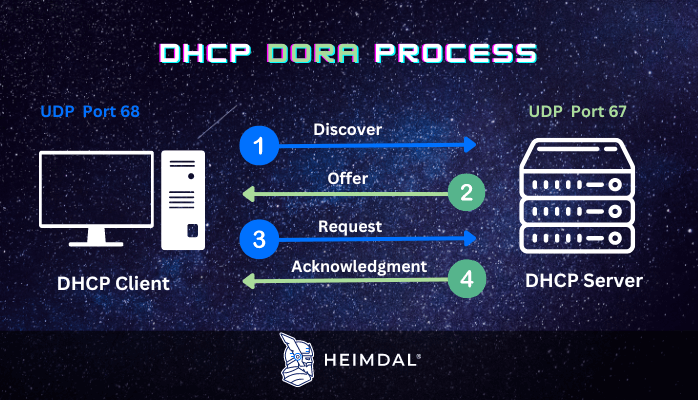
When a computer or device on a network wants to connect to and communicate with others, locally or over the Internet, it operates in a four-step process – also known as DORA process, which stands for:
- Discovery – The first message produced during server and client connection is known as the DHCP discovery request. To find out whether a network has any DHCP servers or servers at all, the client host generates this message. To locate the DHCP server, this message is broadcast to all connected devices in the network.
- Offer – When the server receives the request, it forwards it to its DHCP service. The DHCP service on the server checks the list of available IP addresses that have not already been claimed by other computers and devices. As soon as the DHCP server identifies a free IP address, it sends it to the computer or device that requested it. This step is referred to as a DHCP offer.
- Request – The PC or device receives the dynamically assigned IP address and sends a message back to the DHCP server confirming that it wants to use that IP address. This step is referred to as a DHCP request message because the client requests the offered IP address.
- Acknowledgment – When the DHCP server gets the message request, it sends a final message to the computer or device that started the whole process. This message is known as DHCP acknowledgment, and it has all the other configuration information, such as the gateway address and the addresses of the DNS servers, that is needed to give the computer or device access to the network. This configuration information also provides the time period for which the allocation is valid, known as a lease.
Lastly, the DHCP server or router marks the IP address as being used by the computer or device that requested it. This means that the computer or device can now interact with other devices on the local network and access the Internet.
DHCP Uses UPD Port Numbers 67 and 68
DHCP uses the User Datagram Protocol (UDP), a connectionless service model. It works with two UDP port numbers that are the same as the ones for the bootstrap protocol (BOOTP). The server listens on UDP port number 67, and the client listens on port number 68.
DHCP Lease Process
If a client is using dynamic DHCP, the IP address it receives is not its permanent address; rather, it is a temporary lease. A dynamic IP address requires a device to contact a DHCP server whenever it is turned on so that it can obtain a new IP address.
DHCP Components
For a better understanding of Dynamic Host Configuration Protocol (DHCP), let’s also take a closer look at its components:
- DHCP Server. A DHCP server is a networked device that runs the DCHP service and stores IP addresses and related configuration data. Typically, this is a server or a router, but it might be anything that operates as a host, such as an SD-WAN device.
- DHCP Client. The DHCP client is the endpoint that is configured using data sent from a DHCP server. Any network-capable gadget, such as a desktop, notebook, or endpoint for an Internet of Things (IoT) system, would qualify. By default, most gadgets are set up to get their IP address from a DHCP server.
- DHCP Relay. A DHCP relay is a host or router that scans the network for broadcast client messages and forwards them to a specified server. The relay agent subsequently provides responses to the client, who receives them from the server. Instead of having a server on each subnet, DHCP servers can be centrally managed via DHCP relay.
- IP Address Pool. The range of IP addresses that DHCP clients can use is called the IP address pool. IP addresses are normally assigned in descending order from lowest to highest.
- Subnet. The partitioned segments of IP networks are referred to as subnets. Subnets are used to organize networks and make maintenance easier.
- Lease. The lease is the amount of time that a DHCP client keeps the IP address information. When a client’s lease is up, they have to renew it.
DHCP Benefits
DHCP provides numerous benefits that make it an essential component of any successful network. Perhaps most importantly, DHCP can significantly reduce the amount of time and effort required to configure and manage network IP address settings. Other advantages are:
- Centralized IP Address Management: By using DHCP, a network administrator can automatically and centrally manage the IP addresses on their network. With all configuration data stored in a single location, the administrator can manage all IP addresses more efficiently.
- Dynamic host configuration: By automatically assigning IP addresses to devices on a network, DHCP can eliminate the need for manual configuration of these settings – saving valuable time and resources. DHCP also provides a way to automatically assign IP addresses to new devices that are added to a network, making it easier to expand the network without having to manually configure each new device.
- Flexibility: When using DHCP, the administrator has more flexibility because it is simple to switch IP configurations when the infrastructure changes – for example, when a client’s access point changes.
- IP Optimization: Addresses that are no longer in use are free to be reassigned to new network clients.
- Faster Connectivity for Users: One of the benefits of DHCP is that it provides faster connectivity for users. When a user connects to a network, they are assigned an IP address automatically. This eliminates the need for users to manually configure their IP addresses, which can be time-consuming and error-prone.
DHCP Security Concerns
When it comes to networking, DHCP is a core protocol that is responsible for assigning IP addresses to devices. But while DHCP can be incredibly useful, it also poses some security risks that need to be considered.
DoS Attacks
One of the biggest security risks of DHCP is the potential for denial of service (DoS) attacks. An attacker can launch a denial of service attack by sending fake DHCP requests to the server, leasing up all the available IP addresses and leaving no IPs for legitimate clients to use. Alternatively, an attacker could send fake requests and responses to trick clients into connecting to their machine rather than a legitimate DHCP server.
If an attacker is able to send malicious requests to a DHCP server, they can cause it to become overwhelmed and unable to respond to legitimate requests. This can result in network outages and disruptions.
Rogue DHCP Servers
Another risk that needs to be considered is the possibility of rogue DHCP servers. If an attacker is able to set up their own DHCP server on a network, they could assign addresses that conflict with those assigned by the legitimate DHCP server. This could cause problems with connectivity and lead to devices being unable to communicate with each other properly.
How Can Heimdal® Help?
It’s important to be aware of these risks above when using DHCP and take steps to mitigate them. For example, using access control lists (ACLs) on DHCP servers can help prevent unauthorized devices from making requests.
Additionally, monitoring network traffic for suspicious activity can help detect rogue DHCP servers or attempts at DoS attacks. For the latter, we have an excellent product that keeps your endpoints secure by filtering network traffic.
Heimdal Threat Prevention scans your users’ traffic in real-time, blocking infected domains and stopping communication with cybercriminal infrastructures. This gives administrators full confidence and allows users to browse the Internet safely, whether they are on-site or remote, with minimal system footprint.
Threat Prevention can detect malicious processes and URLs, as well as trace the attacker’s origins. Give your staff the right tools, and you’ll have comprehensive visibility and control over your endpoints and network. It works in tandem with any existing antivirus product to block harmful domains as well as communications to and from C2 centers and other malicious servers.
Heimdal® DNS Security Solution
Wrapping Up
DHCP is an important protocol for managing networks, but it also carries with it a number of potential security risks. By understanding what DHCP is, how it works, and the possible vulnerabilities associated with its use, users can better protect their systems from unwanted intrusions. With proper configuration and attention to security best practices, DHCP can be used safely and effectively in any network environment.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security