Contents:
Transmission Control Protocol (TCP) is a fundamental communication protocol, used in computer networks, that does exactly what its name says: it controls how data is transmitted between two systems – the client and the server, and it makes sure this is achieved successfully.
Because it has been widely used on the Internet since its inception, in the 1970s, it’s now become an essential component of modern networks. From a cybersecurity point of view, understanding Transmission Control Protocol (TCP) is an essential step toward keeping your networks secure, because as you might have guessed, TCP was not built with security in mind.
So, if you’ve ever wondered what lies at the heart of your network communications, you’re in luck! In this article, we’ll look at what TCP is, how it works, and provide some tips on how to tackle its potential vulnerabilities. We’ll also compare TCP/IP versus OSI models as well as explore the most common attacks against TCP and how to prevent them. So let’s dive in!
What’s the Purpose of TCP?
TCP is one of the core protocols of the Internet Protocol suite and is used by many of the most common internet applications, such as email, file transfers, and online gaming. The combination of TCP and IP provides a complete solution for transmitting data over a network and is essential for the functioning of the internet.
In simple terms, TCP is a protocol that provides a reliable and secure means of transmitting data over computer networks. It is an important component of data communication in networks and ensures the stability and reliability of the network as a whole.
A Short History
It was the US Department of Defense that first defined how the data will be transferred from one system to another, in an end-to-end communication, to make sure it gets sent successfully. Transmission Control Protocol (TCP) was developed in the 1970s as part of the ARPANET project, which was the precursor to the modern internet.
TCP was created by Vint Cerf and Bob Kahn as a reliable and secure means of transmitting data over computer networks. It was first standardized as an Internet standard in 1980 and has undergone several revisions and updates since then to improve its performance and security. Today, TCP is a critical component of the internet and is used by billions of devices worldwide for communication and data transmission.
TCP and Computer Networking
Before getting into details on how TCP works, let’s first establish a few important distinctions.
Now, you might have heard about the TCP/IP (Transmission Control Protocol/Internet Protocol) suite or model and of course, the OSI (Open Systems Interconnection) model. But what’s the difference between them and what’s TCP’s role in all this? Let’s clarify.
TCP/IP versus OSI
Similarities: Both OSI and TCP/IP are models used to understand the communication of data between devices in computer networks.
Differences: The main difference between TCP/IP and the OSI model is applicability. OSI is a theoretical model but it was never actually implemented, it is just conceptual and often as a reference and educational tool in the field of computer networking. TCP/IP, on the other hand, is a real-world implementation of communication protocols and it is widely used in practice.
The OSI model has seven layers, while the TCP/IP model has 4 layers. The OSI model provides a general understanding of the different layers involved in communication, while TCP/IP provides the specific details of how data is transmitted between devices.
While both models are important in understanding how data communication works, most practitioners find that it is easier to think in terms of the TCP/IP model because it closely mirrors how data communication actually happens.
Note: if you want to learn more about the OSI model, my colleague Vladimir wrote a dedicated piece on this subject: OSI Layers Explained – The “What”, “Where”, and “Why” of the OSI Model.
TCP versus TCP/IP
This one is easy: TCP/IP is a suite of protocols that provide communication and data transmission services for the internet and other computer networks, while TCP is a specific protocol that operates at the Transport Layer of the TCP/IP suite and provides reliable, in-order delivery of data between applications running on different devices.
The TCP/IP protocol suite includes TCP, as well as other protocols that provide a range of communication and data transmission services.
For a better understanding of these models, as well as how to recognize TCP in the vast pool of protocols, check out the table below:
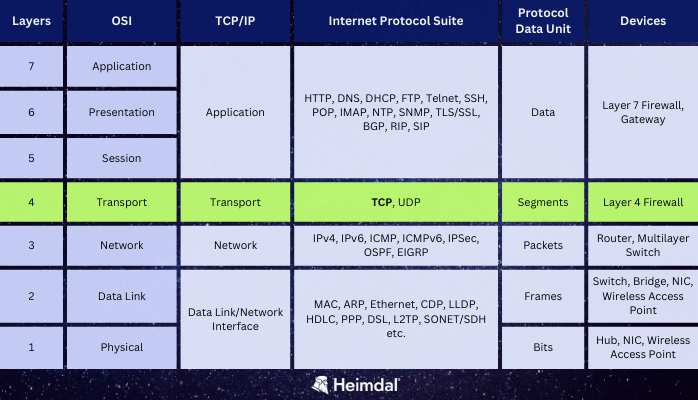
How Does TCP Work?
Now that we’ve established what TCP is and its place in the networking picture, let’s see how it does its job.
Transmission Control Protocol (TCP) works by dividing the data to be transmitted into small segments and then transmitting each segment individually over the network. The segments are reassembled at the destination to form the original data. This process helps ensure the reliability and security of the data transmission.
In addition, the protocol also provides mechanisms for flow control and congestion control to ensure that the network is not overwhelmed with too much data.
Here is a general overview of how TCP works:
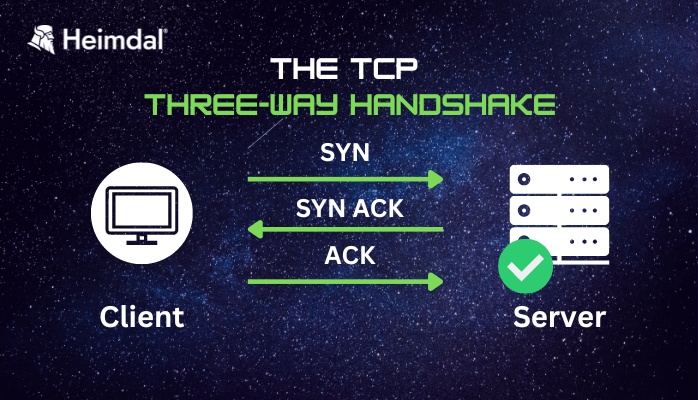
- Connection Establishment: Before any data can be transmitted, a TCP connection must be established between the two devices. This is accomplished through a three-way handshake between the devices.
- Segmentation: Once the connection is established, the data to be transmitted is divided into small segments. Each segment is then given a sequence number to help ensure that the segments are reassembled in the correct order at the destination.
- Transmission: The segments are transmitted over the network and received by the destination device.
- Acknowledgement: The destination device sends an acknowledgement (ACK) back to the source device to indicate that it has received the segment successfully. The source device keeps track of which segments have been acknowledged and which have not.
- Flow Control: TCP uses a mechanism called flow control to ensure that the receiving device does not become overwhelmed by too much data. The receiving device sends back a window size in its ACK message, which specifies the number of segments it is prepared to receive. The source device adjusts its transmission rate based on the window size received from the destination device.
- Congestion Control: TCP uses congestion control to ensure that the network does not become congested with too much data. The protocol adjusts the transmission rate based on network conditions, such as the amount of data in the network and the number of lost segments.
- Connection Termination: When the data transmission is complete, the TCP connection is terminated through another three-way handshake.
Is TCP Secure?
The short answer is: not really. While TCP provides a reliable and efficient way to transmit data, it does not provide any encryption or authentication mechanisms to secure the data. As a result, transmitted data can be intercepted and read by unauthorized users, and its authenticity cannot be verified.
Therefore, to secure communication over TCP, additional security measures, such as encryption and authentication, must be implemented on top of TCP. Common security protocols used in combination with TCP include SSL/TLS, SSH, and IPSec.
Most Common TCP Attacks
The most common attacks that could target TCP (Transmission Control Protocol) are:
SYN Flood
A SYN flood attack is a type of denial-of-service (DoS) attack that exploits the three-way handshake used by TCP to establish a connection. The attacker sends a large number of SYN requests to the target server, overwhelming its ability to process them and causing the server to become unavailable.
TCP Reset Attack
The TCP reset attack, also known as a “forged TCP reset” or “spoofed TCP reset,” is a method for terminating a TCP connection by transmitting a faked TCP reset packet. This method of tampering can be utilized by a firewall or abused by an adversary to disrupt Internet connections. Example: The Great Firewall of China and Iranian Internet censors use TCP reset attacks to interfere with and block connections, as a primary tool for implementing Internet censorship.
TCP Session Hijacking
TCP session hijacking is a type of attack in which an attacker intercepts and takes over an existing TCP session. The attacker can use this to eavesdrop on communications, inject false data into the session, or disrupt the session altogether. This type of attack is possible due to the fact that authentication is often performed only at the beginning of a TCP session.
A man-in-the-middle attack is another sort of session hijacking in which the attacker, employing a sniffer, can observe the communication between devices and seize the transferred data.
TCP Sequence Prediction
In this attack, a threat actor tries to predict the sequence number used by TCP to establish a connection. The attacker can then use this information to inject false data into the connection, disrupt the connection, or steal sensitive information.
TCP Spoofing
In TCP Spoofing, the attacker sends false data, or “spoofs” the source address of the data, to a target system. This can allow them to gain unauthorized access to the target system or to disrupt its normal operations. Spoofing attacks can be difficult to detect and prevent, so it’s important to have strong security measures in place.
How to Prevent TCP Attacks?
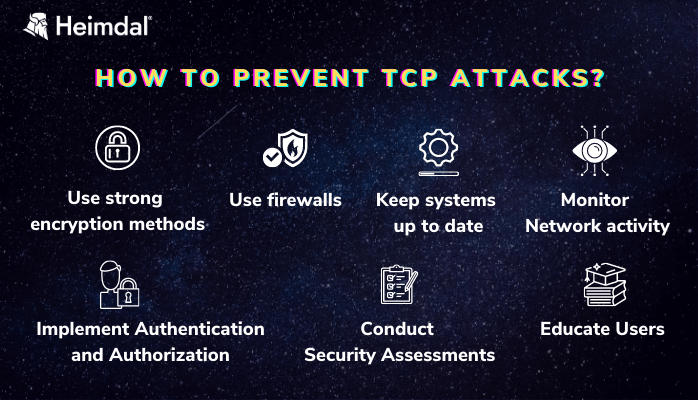
To protect TCP (Transmission Control Protocol) against attacks, businesses can take the following measures:
- Use strong encryption methods: Encrypting data that is transmitted over TCP is one of the best ways to prevent eavesdropping and tampering. Strong encryption methods such as SSL/TLS can make it much more difficult for attackers to intercept and exploit data.
- Use firewalls: Firewalls can be used to restrict incoming and outgoing traffic to and from a network, reducing the risk of exploitation.
- Monitor network activity: By monitoring network traffic, it is possible to detect suspicious activity and take appropriate action. Monitoring tools such as intrusion detection systems can be used to identify potential threats and take steps to mitigate them.
- Keep systems up to date: Regularly patching and updating systems can help to close any security holes that may exist. Keeping systems up to date with the latest security fixes is an important part of preventing attacks.
- Implement Authentication and Authorization: Implementing authentication and authorization mechanisms, such as passwords and access controls, can help prevent unauthorized access to network resources.
- Conduct Regular Security Assessments: Regular security assessments can help identify and remediate potential security weaknesses in a network.
- Educate Users: Educating users about safe computing practices, such as avoiding phishing scams and using strong passwords, can help reduce the risk of exploitation.
How Can Heimdal® Help?
The ones above are just a few of the many measures that businesses can take to protect against TCP attacks. It’s important to remember that no single measure will provide complete protection, so businesses should use a multi-layered approach that incorporates a variety of security measures.
A great addition to your cybersecurity posture would be Heimdal Threat Prevention, our award-winning traffic-filtering solution, which actively checks the whole network for any signs of malware entry from malicious infrastructures. It detects emerging and hidden cyber threats, stops cyberattacks that go undetected by typical anti-virus software, and closes off data-leaking channels.
Using the Darklayer Guard™ endpoint engine, which works in tandem with VectorN Detection smart traffic pattern algorithms engine, Threat Prevention not only gives you the ability to stop active attacks, but it also speeds up your investigation process by using the unique intelligence gathered by blocking threats at the DNS, HTTP, and HTTPS level.
Heimdal® DNS Security Solution
Wrapping Up
The Transmission Control Protocol plays a vital role in transferring data from one system to another. By understanding what it is, how it works, and how to keep it secure, you can ensure that your business’s data remains confidential while also enjoying a reliable connection.
TCP security is important to enterprises because it helps protect confidential information, maintain continuity, comply with regulations, protect reputation, and even enhance customer trust. The good news is that by implementing strong TCP security measures as part of a multi-layered cybersecurity strategy, businesses can maintain the security of their networked systems and ensure that their sensitive information is kept safe.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











