Contents:
We might feel that technology plays an enormous role in our lives, always with our eyes on our phones or turning on the TV right after we got home – maybe even consider, in a certain way, that electronic gadgets are a part of our family, like Mildred from Fahrenheit 451, Bradbury’s famous dystopia. We must not forget, though, that although technology has had a huge contribution to the evolution of human civilization, our devices can also be seen as a source of possible threats, especially if they are connected to the Internet. This happens because Wi-Fi routers, Smart TVs, smart cameras, smart locks, smart lights, voice assistants, some medical devices or Internet-connected cars fall under the category of the so-called Internet of Things, and may very easily become the target of cybercriminals.
What Is IoT Security?
The Internet of Things (IoT) describes the physical objects that are embedded with software, sensors and other technologies that allow them to connect and exchange data with other devices and systems over the Internet.
Consequently, IoT security refers to all the measures we can take to ensure the (cyber)security of this kind of devices, while also keeping in mind the various dangers that threaten them.
Both manufacturers and consumers prefer these devices. Consumers for the added functionality (it’s easier to watch Netflix if the TV already has Internet).
Manufacturers, however, like IoT devices because they allow them to silently collect information about how consumers use their products. As a result, they can then tailor future products around these usage patterns.
The Rise of IoT Devices
The emergence of IoT has been fostered by an impressive series of factors that include:
Connectivity. Hosts of network protocols for the Internet easily connect sensors to the cloud and “things”, streamlining data transfer.
Access to low-cost and low-power sensor technology. Nowadays, manufacturers use affordable and reliable sensors.
Cloud platforms. Cloud platforms’ increase in availability enables both businesses and consumers to benefit from their advantages, without having to manage them.
Machine learning and analytics. The advances in machine learning and analytics plus the vast amounts of data stored in the cloud allow companies to gather insights faster and more easily.
Rise of conversational artificial intelligence (AI). IoT devices (like the digital personal assistants Alexa, Cortana and Siri) can now benefit from natural-language processing due to advances in neural networks.
As i-SCOOP shows, “In 2020 the number of IoT endpoints is forecasted to reach 5.8 billion endpoints, as mentioned a 21% increase from 2019. […] The fastest-growing segments in terms of IoT endpoints installed base: building automation, automotive and healthcare. The second-largest user of IoT endpoints is physical security, says Peter Middleton. Here building intruder detection and indoor surveillance use cases will drive volume.” Other industries use this kind of technology as well, so this growth tendency only underscores the importance of IoT security for business.
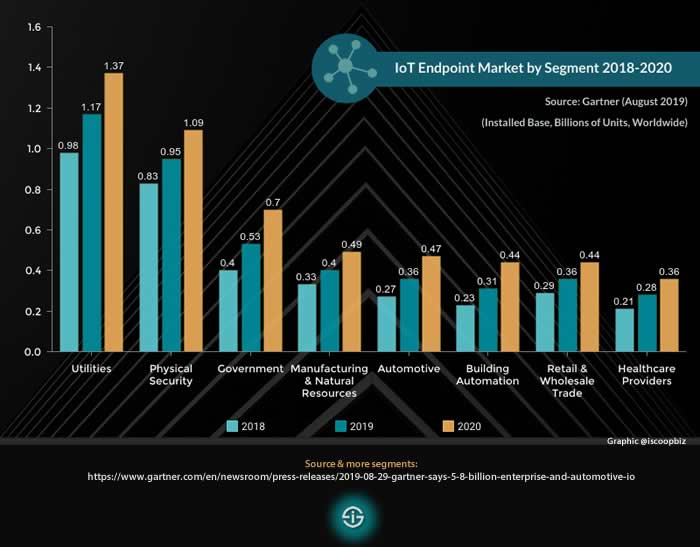
IoT endpoints 2018, 2019 & 2020 – selected segments (source and more information)
Benefits of IoT Devices
The major benefits of IoT secure devices for your business are the following:
- They increase the productivity and efficiency of business operations.
- They create new business models and revenue streams.
- They easily connect the physical business world to the digital world, which saves time and creates value.
The tricky part is, whether we use them as home consumers or in our workplace, they really are convenient – IoT devices allow us to turn lights on and off remotely, unlock the front door when we are not even in the building, or get Alexa or Siri to check our calendar for us.
As Peter Milley says, in his paper Privacy and the Internet of Things,
This convenience comes at a price. The unfortunate reality is the companies making these devices, although well steeped in the challenges of manufacturing physical products, are not as well versed in software development. […] Appliance makers create back-door access for support personnel or hard-coded passwords and encryption keys to simplify manufacturing and support with little regard for security. Furthermore, they rarely take into account the need for regular patch maintenance and rely too heavily on the end-user to make security changes to their products.
IoT Security Risks
Identity and access management
Identity and access management is typically related to end-users, but it also extends to devices and applications that require network and resource access. What they have access to and the legitimacy of their request in the first place must always be verified, because devices left exposed in various locations can be easily attacked and used by cybercriminals to infiltrate your organization.
Data Integrity
Data is crucial for IoT operations and it’s also critical that its integrity is wholesome. Take measures to assure that your data has not been manipulated, neither while at rest, in transit, or in use. Don’t forget about personal data either. This kind of information and any data generated by an IoT device must be protected through encryption, whether it’s in transit or at rest.
The great number of devices
Another aspect that threatens IoT security is the use of a great number of devices. To be precise, integrating new systems and devices provides more points of access for potential attackers, which raises the safety stakes exponentially.
The simplicity of the devices
Simplicity and ease of use are crucial principles within the IT and electronics industry. Every software and device out there is designed to be as easy to use as possible, so as to not confuse consumers and discourage them from using the product.
Unfortunately, this often means that some products cut corners, and don’t implement security features consumers might find “too clunky”.
IoT devices are being more and more used in various sectors, and even the most simple devices (like a fish-tank thermometer in a casino who can gather tens of GB of personal data and expose it to hackers, for example) can be potential gateways to private segments of a company’s network.
Poor software updates
What’s more, many Internet of Things creators don’t even patch or update the software that came on their devices. If your device has a software vulnerability (nearly 100% chance that it does), there’s little you can do to prevent an attacker from exploiting it without help from the manufacturer.
Insecure user interface
A device’s user interface is generally the first thing a malicious hacker will look into for any vulnerabilities. For instance, he might try to manipulate the “I forgot my password”, in order to reset it or at least find out your username or email.
A properly designed device should also lock out a user from attempting to log in too many times. This stops dictionary and brute force attacks that target passwords and greatly secures your device credentials.
In other cases, the password might be sent from the device to the central server in plain text, meaning it isn’t encrypted. Pretty bad if someone is listening in on the device and reading all of your data.
The physical protection and disposal of connected devices
Anyone with physical access to some products can extract the owner’s password from the plaintext, private keys, and root passwords. As companies adopt and upgrade IoT, it’s also important to think about the aspect of protection during the use and disposal of old or defective smart devices.
Malware on an industrial scale
Hackers are developing more and more dangerous sorts of malware, so companies must not forget to ensure the security of the industrial control systems that are connected and depending on IoT devices.
GDPR Compliance
Innovation always includes the possibility of opening potential loopholes for data protection. The fines levied for GDPR exposure show that the European Commission regulators are very serious when it comes to ensuring that personal data remains private. There are some new security laws on the horizon that promise to hold device manufacturers accountable for vulnerable entry points, yet companies need to take more responsibility for the imperfections within their own IT architecture.
Inertia
Inertia is, generally, one of the greatest cybersecurity threats of today. Technology constantly evolves, hackers elaborate more and more strategies to get what they desire, yet so many companies still rely on security tools developed decades ago.
Up to this point, the safety systems of a Saudi Arabian oil refinery have been targeted by the Triton industrial malware. Vast amounts of personal data have been accidentally exposed at the British Airways, Marriott Hotels, and various local authority organizations. A group of hackers got access to impressive amounts of a casino’s sensitive information by using an Internet-connected thermometer in an aquarium. Don’t let anything like this happen to your company!
Moreover, researchers have proven more than once that it’s possible to physically take control of a car by breaking into apps that control onboard software. For now, this has only been done in experimental situations, but as Internet-connected cars gain ground, it’s only a matter of time until it happens to someone, somewhere.
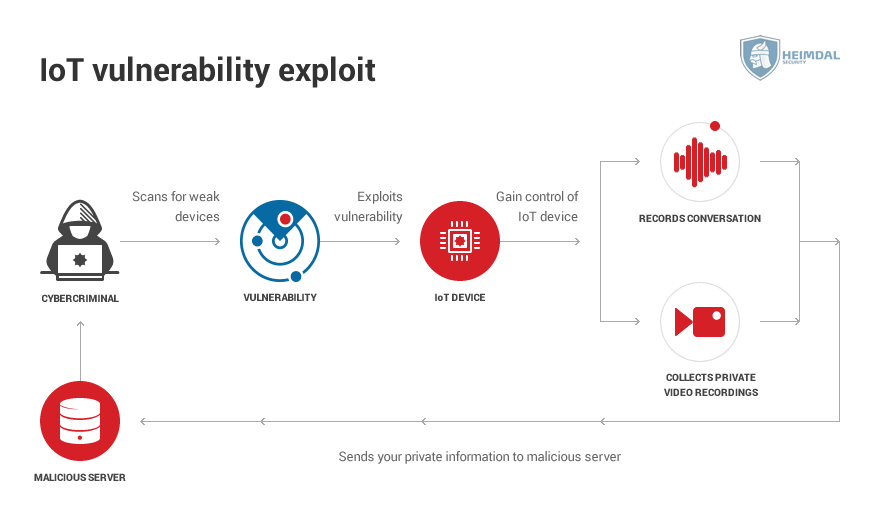
Smart devices can be hacked in a number of ways, depending on the type of vulnerability the attacker decides to take advantage of.
The main types of attacks against IoT devices are:
Vulnerability exploitation
Every software has its vulnerabilities. It’s nearly impossible not to. Depending on the sort of vulnerability, you can use them in multiple ways.
Buffer overflows. This happens when a device tries to store too much data in a temporary storage space. This excess data then spills over into other parts of the memory space, overwriting it. If malware is hidden in that data, it can end rewriting the code of the device itself.
Code injection. By exploiting a vulnerability within the software, the attacker is able to inject code into the device. Most often, this code is malicious in nature, and it can do a multitude of tasks, such as shutting down or taking control of the device.
Cross-Site Scripting. These work with IoT devices that interact with a web-based interface. Basically, the attacker infects the legitimate page with malware or malicious code, and then the page itself will infect the IoT device.
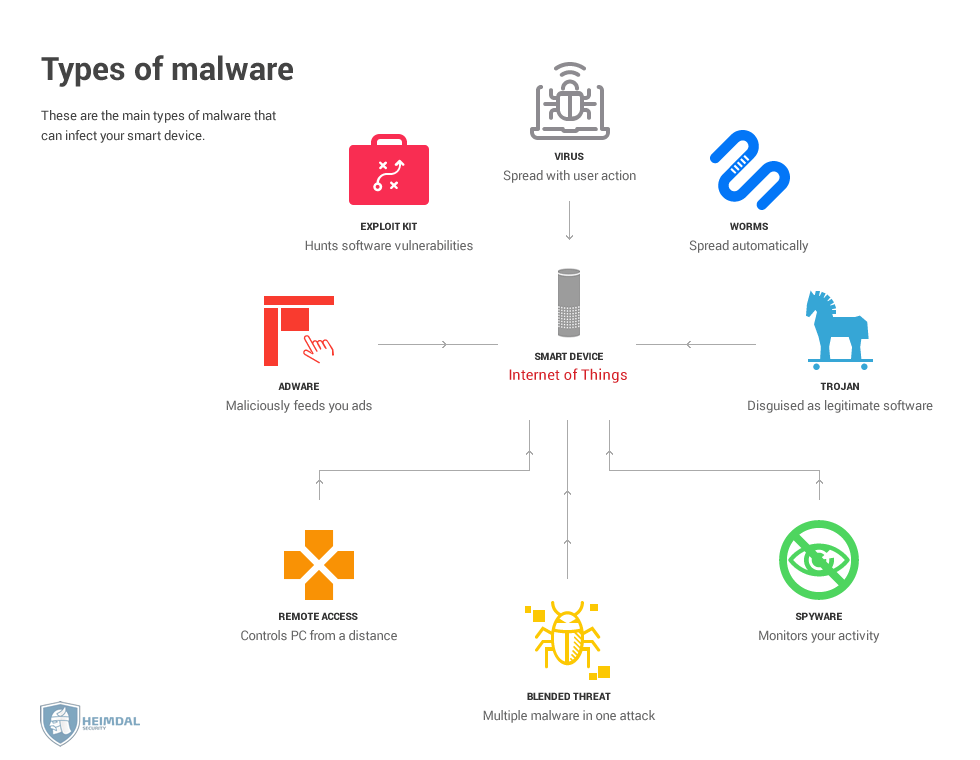
Malware attacks
The most frequent and well-known malware attacks on PCs target a device’s login credentials. But recently, other types of malware such as ransomware have made their way onto IoT devices.
Smart TVs and other similar gizmos are most exposed to this kind of threat, since users might accidentally click on malicious links or download infected apps.
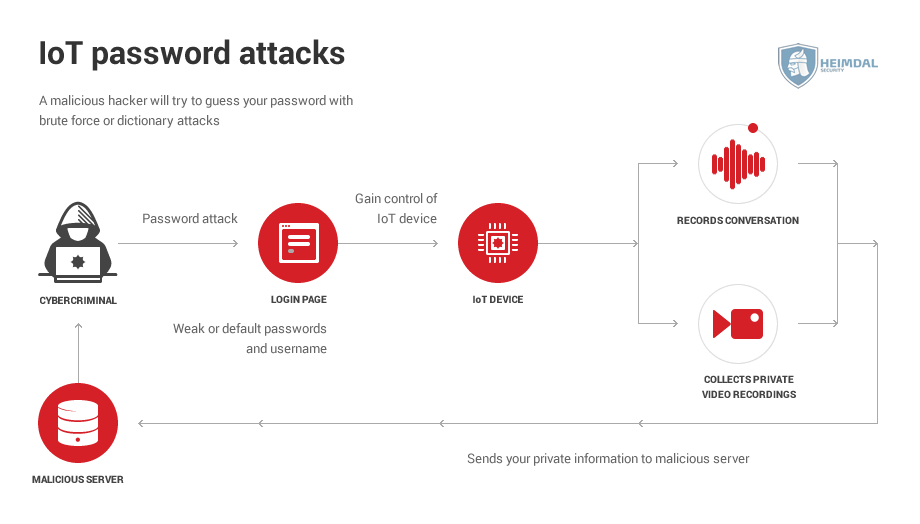
Password attacks
Password attacks such as dictionary or brute force target a device’s login information by bombarding it with countless password and username variations until it finds the proper one.
Since most of the people use an easy password, these attacks are fairly successful. Not only that, but according to one study, nearly 60% of users reuse the same password. So if an attacker gets access to one device, they get access to all devices.
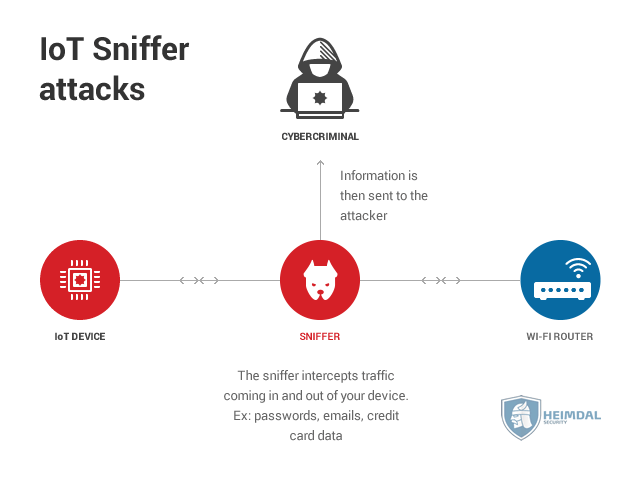
Sniffing / Man-in-the-middle attacks
In this attack, a malicious hacker intercepts the Internet traffic that goes into and out of a smart device.
The preferred target is a Wi-Fi router, since it contains all of the traffic data sent from the network, and can then be used to control each device connected to it, even PCs or smartphones.
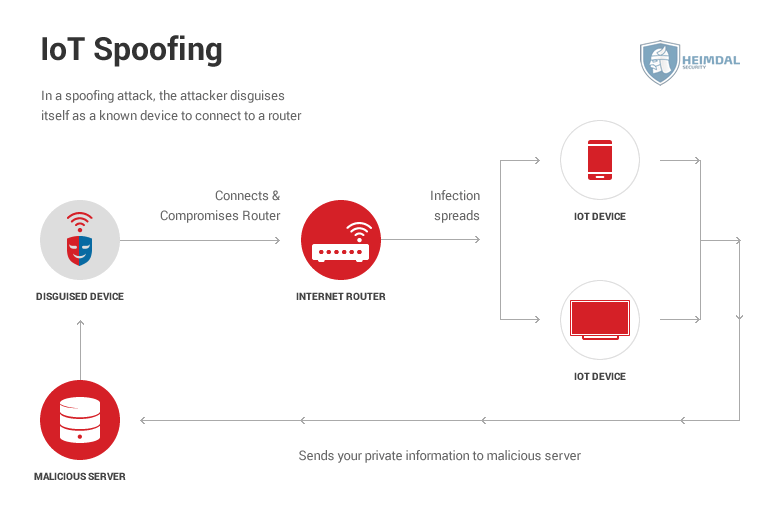
Spoofing
Spoofing works by disguising device A to look like device B. If device B has access to a wireless network, then a disguised device A will trick the router into allowing it on the network. Now that the disguised device A can communicate with the router, it can inject malware into it. This malware then spreads to all the other devices on the network.
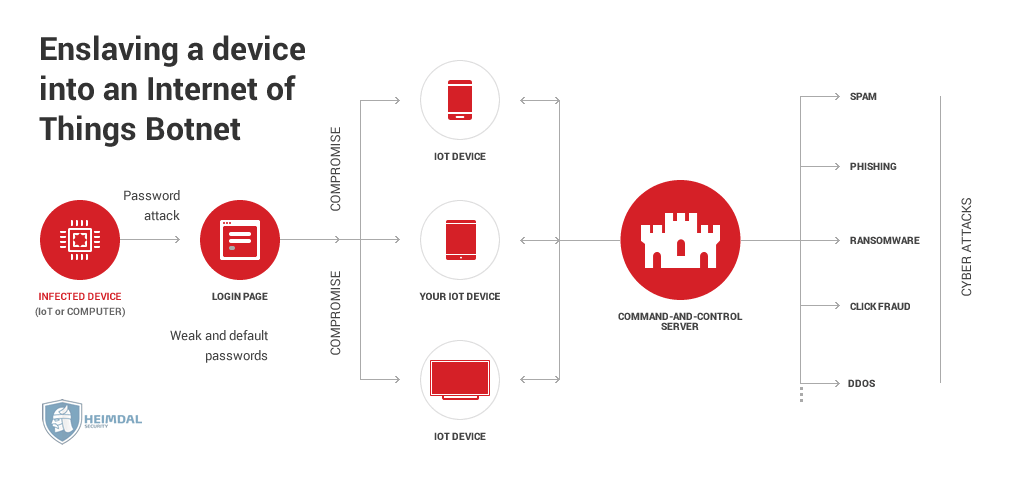
Botnet enslaving
Internet of Things devices are prime candidates for a botnet. They are both easier to hack and harder to diagnose if they’re compromised.
Once a device is enslaved, it can be used for a wide variety of cybercriminal activities, such as DDoS attacks, sending spam emails, performing click fraud (basically using the enslaved device to click an ad), and Bitcoin mining.
Mirai is the biggest IoT botnet we know about, and it was built on the backs of default passwords and usernames.
Remote access
Taking control of an IoT device doesn’t sound so menacing at first glance. After all, it’s not as if a malicious hacker could poison you if he hacked your coffee maker.
But things will quickly get serious if the attacker takes control of your car as you’re driving it. This isn’t even a hypothetical situation, it’s actually been done, albeit by cybersecurity researchers – whitehat hackers were able to hack into the car’s braking system and acceleration.
Some people now use smart locks to secure their homes, but ultimately they’re just software on hardware. At DEF CON 2016 (the biggest hacker conference in the world), researchers tested out 16 smart locks and proved how many of them used very simple security features such as plain text passwords. Others were vulnerable to device spoofing or replay attacks.
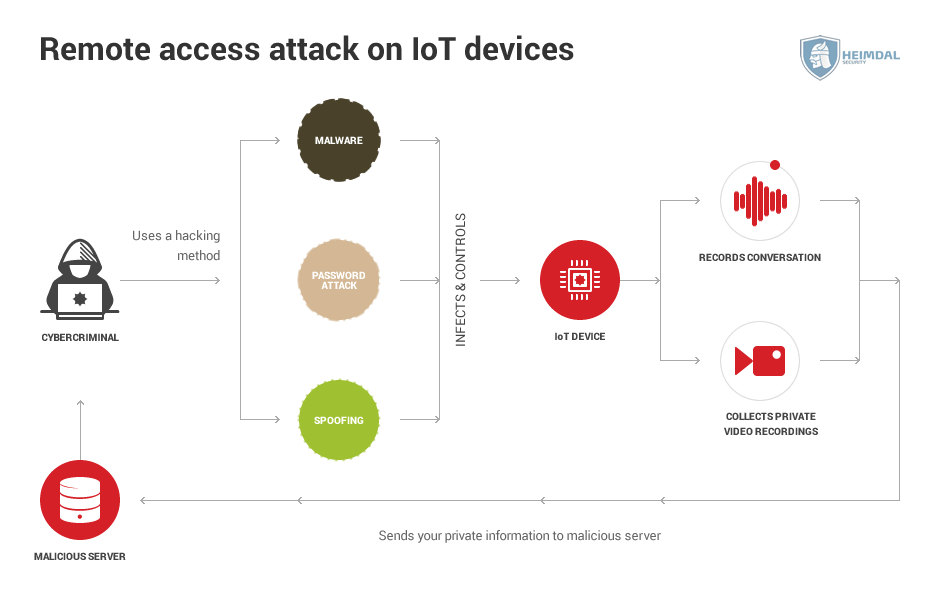
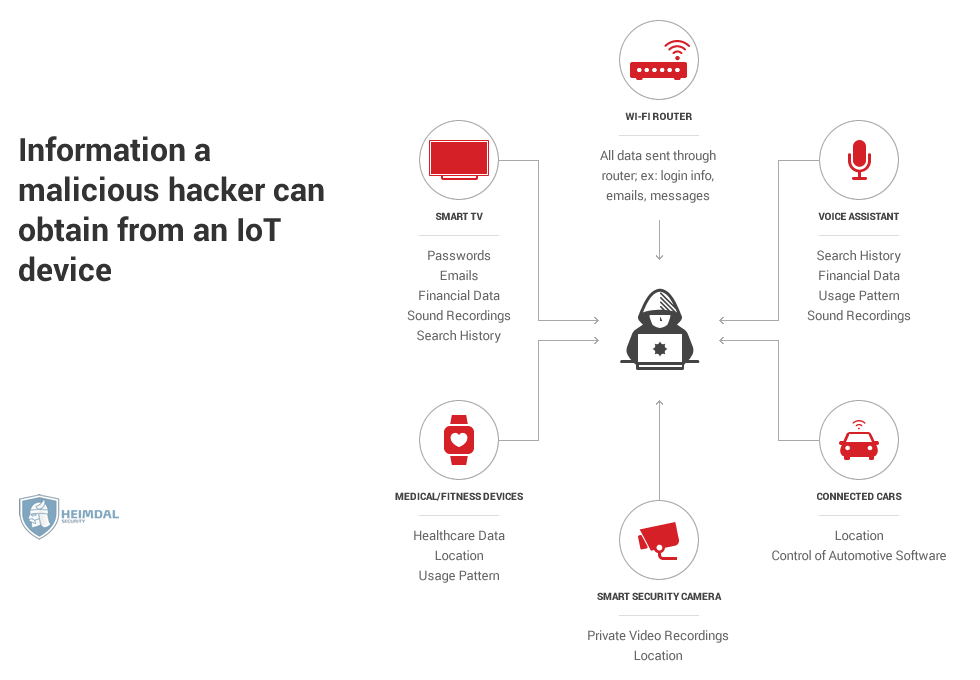
Data leakage
Smart devices process a lot of personal information, such as:
- medical data
- location data
- usage patterns
- search history
- financial information, etc.
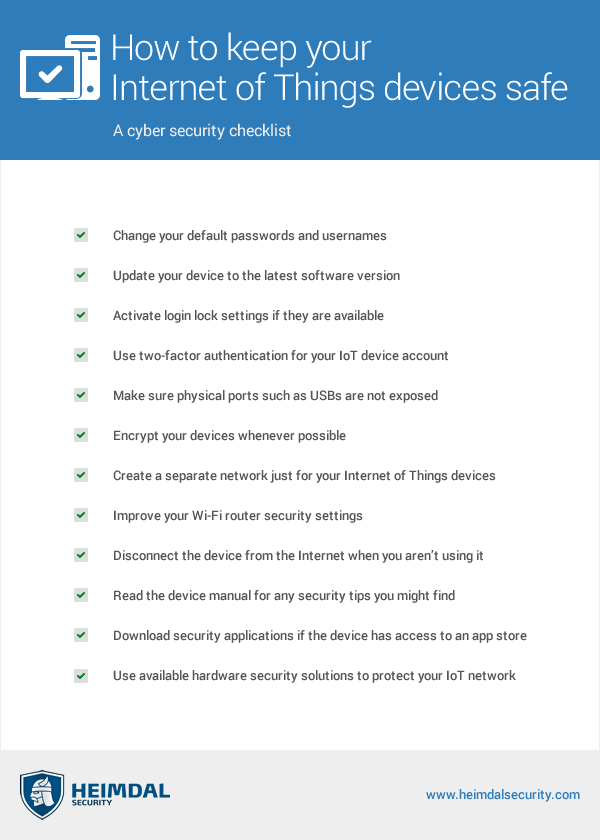
8 Tips for Flawless IoT Security:
Pay special attention when you choose the IoT devices providers
Make sure that you choose a well-known and reliable supplier, most likely one who will probably still be around for a long time. IoT devices require regular updates, especially when new security flaws appear, so you need a manufacturer that, over the years, provides patches and fixes any security bugs that may arise.
Invest in a network analysis tool
Monitor activity and quickly identify potential security issues by investing in a network analysis tool. This way you will not risk missing instances of information being accessed without permission or at unexpected hours – both signs that can point to a breach of your company’s IT system through IoT device.
Consider network management protocols a priority
IoT devices manufacturers often include an in-built protocol that allows the monitoring of internal activity. This usually isn’t enough if you want top security, so it’s crucial for your business to choose IoT devices that support Simple Network Management Protocols (SNMP). SNMP is a worldwide standard for network management, which allows them to be monitored by intrusion detection and prevention systems.
Consolidate your network’s security
It’s crucial to have an up-to-date router, with a firewall enabled because it can be the first point of attack. If the router is compromised, your entire network will be vulnerable.
Make sure your IoT devices get patched up
Security updates are often released by responsible manufacturers, but you must also make sure that your IoT devices are patched regularly, with the latest updates. If you happen to stumble upon a device that doesn’t receive updates, it’s best to think whether the benefits of the device surpass the potential impact of a potential attack in your company’s case.
Remove unsupported operating systems, applications and devices from the network
Improve your business’s IoT security by conducting an inventory to check which operating system a device might be running. If a certain operating system is not getting patches anymore, it shouldn’t be connected to the network.
Narrow down internal and external port communication on your firewalls
Companies should restrict outbound communication if that communication is not particularly necessary. As Cyber Security Services says,
Ports 80 and 443, typically associated with the internet, are common services that are open from the corporate network. But 80/443 might not be required for other VLANs associated with specific device types. These two ports are known to pose significant network threats since they allow web surfing, are rarely monitored and offer an entry path into the network. It is very common for malicious hackers and identity thieves to use those ports to exfiltrate data, as they are often left open in most organizations. This could allow a backdoor into the organization.
Last but not least, change default passwords!
This may seem commonsense, but you must ensure that the default passwords are changed for every IoT device on your network. The new passwords should also be changed over a period of time and stored in a password vault.
A few other strategies are synthesized in the image below:
Heimdal™ can also help you with IoT Security. Here’s how!
You can ensure your IoT devices’ security by choosing our Threat Prevention – Network solution, an Intrusion Prevention System that can actively protect your network and is delivered as SaaS. Threat Prevention Network can shield your organization from DNS queries to unwanted domains by stopping communication between infected devices and malicious servers, which guarantees that every device used in the perimeter of your company’s network will pose no danger to your business. Here we include any (possibly compromised) personal device that your employees or visitors use to connect to your corporate network.
Heimdal® Network DNS Security
Your organization’s protection can be also enhanced in the case of remote work with Heimdal’s Threat Prevention – Endpoint module, our proactive DNS security solution deployed at the endpoint level.
Wrapping Up
As i-SCOOP says, “despite challenges, different speeds and the fast evolutions which we will see until the first years of the next decade, the Internet of Things is here.” That, at the end of the day, the number of IoT security breaches is only going to grow is also a fact.
IoT is one of the biggest technological trends since the smartphone and promises to be just as impactful. Unfortunately, the promise and opportunity they offer are just as tempting for cybercriminals as they are for regular customers. Consequently, securing connected devices can no longer be treated as optional – it is mandatory.
Drop a line below if you have any comments, questions, or suggestions regarding IoT security – we are all ears and can’t wait to hear your opinion!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











