Contents:
While the demand for Wi-Fi access is increasing, more and more wireless Access Points (APs) are used in the network to ensure signal coverage in campuses, schools, or organization buildings, which makes the network operations & maintenance difficult for administrators.
Wireless Access Controllers (ACs) come into being to settle this bottleneck by running and administrating these multiple wireless access points. The wireless access point (AP) has lost the intelligent characteristic, while the wireless access controller turns into the new brain for WLAN.
In the case of the Wireless LAN network, also known as WLAN, you can use the WLC or Wireless LAN Controller, whose purpose is to centralize the control of Access Points (APs).
So that you can understand this better, let’s put it this way: what a wireless Access Point (AP) does for your network is similar to what an amplifier does for your home stereo. It takes the bandwidth coming from a router device and extends it so that multiple other devices can connect from farther distances away.
What Is a Wireless LAN Controller (WLC)?
A Wireless LAN Controller (WLC) is a centralized device in the network which is used in combination with the Lightweight Access Point Protocol (LWAPP) to manage lightweight access points in large quantities by the network administrator or network operations center.
Also called “fat” access points, these access points on the network are managed, operated, and configured independently. The WLC automatically handles the configuration of wireless access points.
Because of its centralized position and brainpower, the Wireless LAN Controller is aware of the wireless LAN environment. It provides services that can lower the price of deployment, ease the management process, and provide several layers of security.
Does My Company Need Wireless LAN Controller (WLC)?
The Wireless LAN Controller (WLC) – Lightweight Access Point (LWAP) setup is commonly utilized in the company environment to stretch an individual wireless network in a vast geographical region. This setup lets users stroll the office premise, campus, or building and still be connected to the network.
When deploying enterprise WLANs, every single wireless access point is initially created and managed separately from other APs on the same network. In other words, each AP must run individually, which makes centralized management difficult to realize.
Unfortunately, technical problems and unstable network conditions can be caused by the lack of communication between these Access Points (APs). The solution? Wireless LAN Controllers (WLC) meant to solve the mentioned problems above once for all. Accompanied by fit mode APs, Wireless LAN Controllers (WLC) can help to realize efficient and simplified network management.
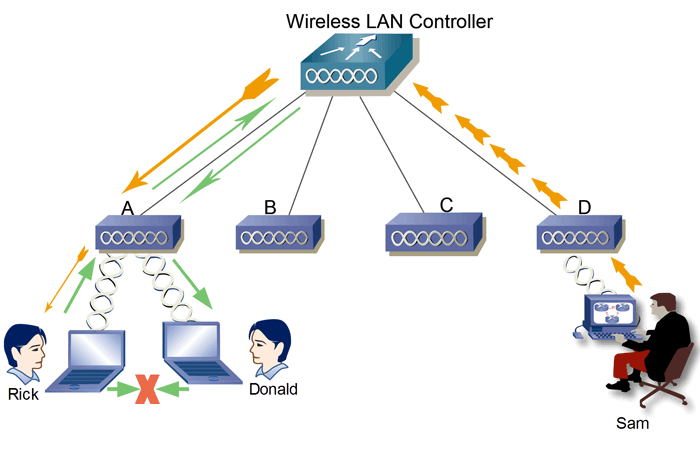
Source: FS Community
Functions of Wireless LAN Controller
As we said before, the major function of a wireless LAN controller (WLC) is to maintain the configuration of wireless Access Points (AP), but it carries out multiple other functionalities:
#1. Traffic aggregation and processing for wireless devices function
It is important to know that this function is not all the time performed inside the WLC, for this it will depend on the network architecture used. When all traffic from wireless devices is routed via the controller, you can use it to encode it or divide it so that is sent to different networks or to be filtered to prioritize it according to the established quality policies.
#2. Management and operation function
These two functions enable you to utilize and manage the wireless local network in a much simpler manner. This way you don’t have to repeat the same operations in every one of the APs within the local networks anymore. These tasks allow you to configure, observe and identify problems in the network and they also permit you to send and receive notifications when problems are noticed.
#3. Local wireless function
In the case of the radio features of wireless technology, it is preferable to utilize the coordination and protection mechanisms in the radio spectrum for more efficient use in a particular area.
The mechanisms aimed at optimizing the distribution of traffic between APs and wireless devices can recognize interference and by using radio triangulation mechanisms can locate geographically the devices.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;
Benefits of a Wireless LAN Controller
- It is secure. With all the daily news about hacking and data breaches, security is an essential factor to have in mind for any organization. Wireless LAN Controller (WLC) fights against all kinds of threats to your organization based on user ID and location thanks to built-in security characteristics.
- It is centralized. A centralized wireless controller provides malleability for deployment, which will lower the budget, planning instruments, and time spent organizing a wireless network in the business.
- It is simple. Having a Wireless LAN Controller (WLC) will help you to administer and supervise your access points in the centralized hub.
A Wireless LAN Controller (WLC) gives the network administrators the ability to see all the data and information linked to the network. They are able to observe on the device the hardware status, the situation of the physical ports, and a summary of the Access Points (APs) connected anytime they want.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










